Internet of Things equipment capable of avoiding data tampering, and data secure transmission method and system
A technology of Internet of Things equipment and data tampering, applied in digital transmission systems, transmission systems, security communication devices, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
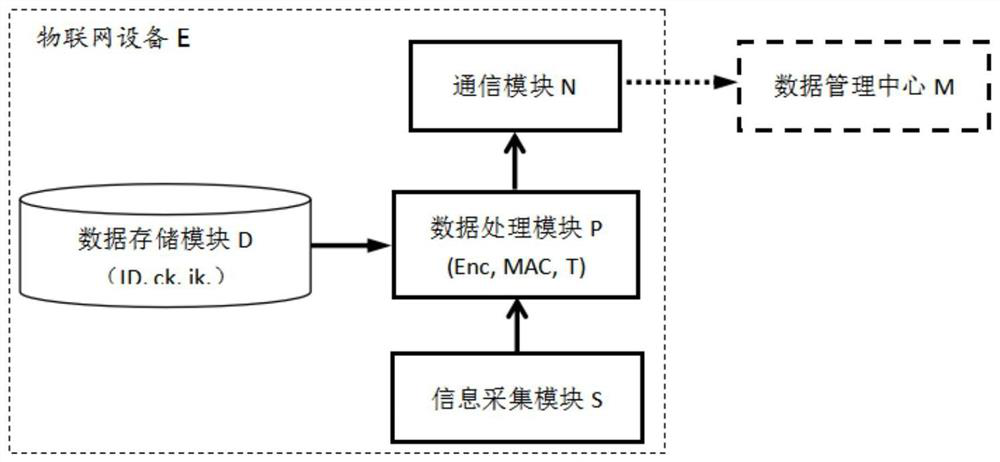
[0078] An Internet of Things device for avoiding data tampering, characterized in that said Internet of Things device includes:
[0079] The data collection module S is used to obtain environmental detection data;
[0080] The data processing module P is used to perform certain calculation processing on the data;
[0081] The data storage module D is used to store key parameters of the device;
[0082] The communication module N is used to connect to the remote data platform, send data to the data management center, or receive relevant instructions;
[0083] The working process of the described IoT device is as follows:
[0084] (1) The information collection module S transmits the environmental detection data data to the data processing module P;
[0085] (2) The data processing module P reads the device's identity ID, encryption key ck and integrity protection key ik from the data storage module D;
[0086] (3) The data processing module P reads the system clock data T, ...
Embodiment 2
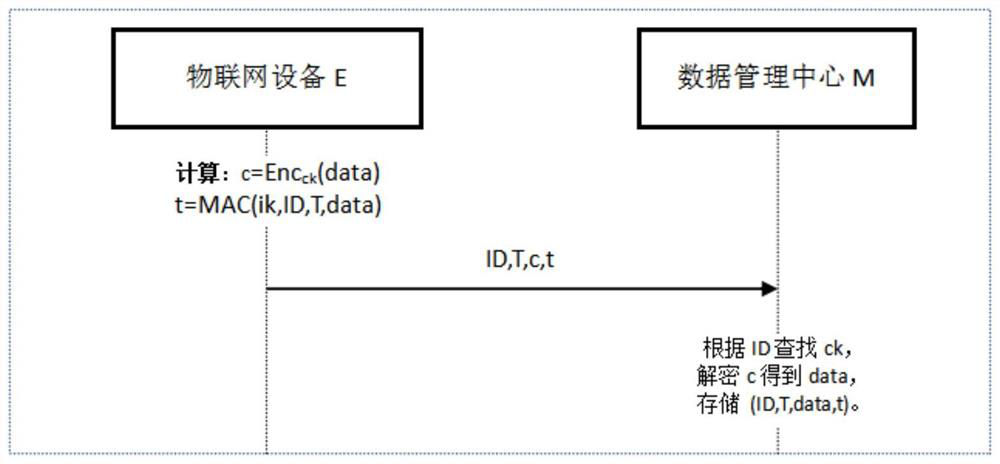
[0088] The present invention also provides an Internet of Things data security transmission system that avoids data tampering, including an Internet of Things device E, and a data management center M, and the Internet of Things device E sends data to the data management center M, so The above-mentioned data management center M carries out corresponding processing, and its processing process comprises the following steps:
[0089] 1) The IoT device E uses the encryption algorithm Enc and the encryption key ck to calculate c=Enc ck (data), using the MAC algorithm and the data integrity protection key ik to calculate the data integrity protection label t=MAC(ik, ID, T, data);
[0090] 2) The IoT device E sends data (ID, T, c, t) to the data management center M;
[0091] 3) After the data management center M receives the data (ID, T, c, t) in step 2), it searches for the key ck according to the ID, and decrypts c using the key ck and the decryption algorithm corresponding to Enc ...
Embodiment 3
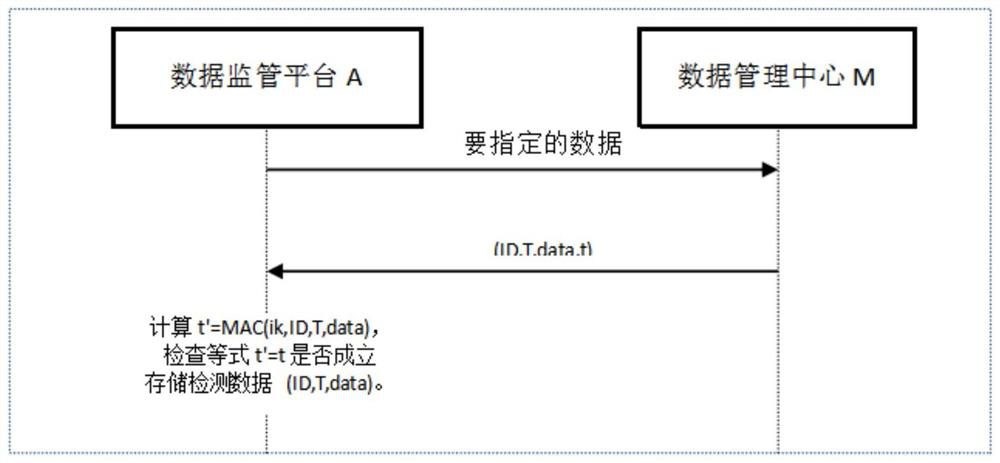
[0115] The present invention provides a method for secure transmission of IoT data that avoids data tampering. The method for secure transmission of IoT data is to add a data header h to the data sent by the IoT device E to the data management center M ; The data management center M performs the following steps after receiving the data sent by the data management center M:
[0116] 1) Determine how to operate according to the data header h: if the value of h indicates that the data has not been encrypted, then use the original system method for processing; if the value of h indicates that the data has been encrypted, then according to the value of h Judging the encryption result of which data the ciphertext c is;
[0117] 2) According to the value of h, execute the entire operation process of step 3) in the data transmission and processing steps between the IoT device E and the data management center M.
[0118] Wherein, when calculating the data integrity protection label t,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com