Source coding method based on polar codes
A technology of source coding and polar code, which is applied in the direction of adjusting source coding, transmission modification based on link quality, and error detection by signal space coding, and can solve the problem of not finding a source coding method based on polar code etc. to achieve excellent coding performance, good promotion and application prospects, and low computational complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to make the purpose, technical solution and advantages of the present invention clearer, the implementation process and performance analysis of the present invention will be further described in detail below in conjunction with the accompanying drawings and simulation examples.
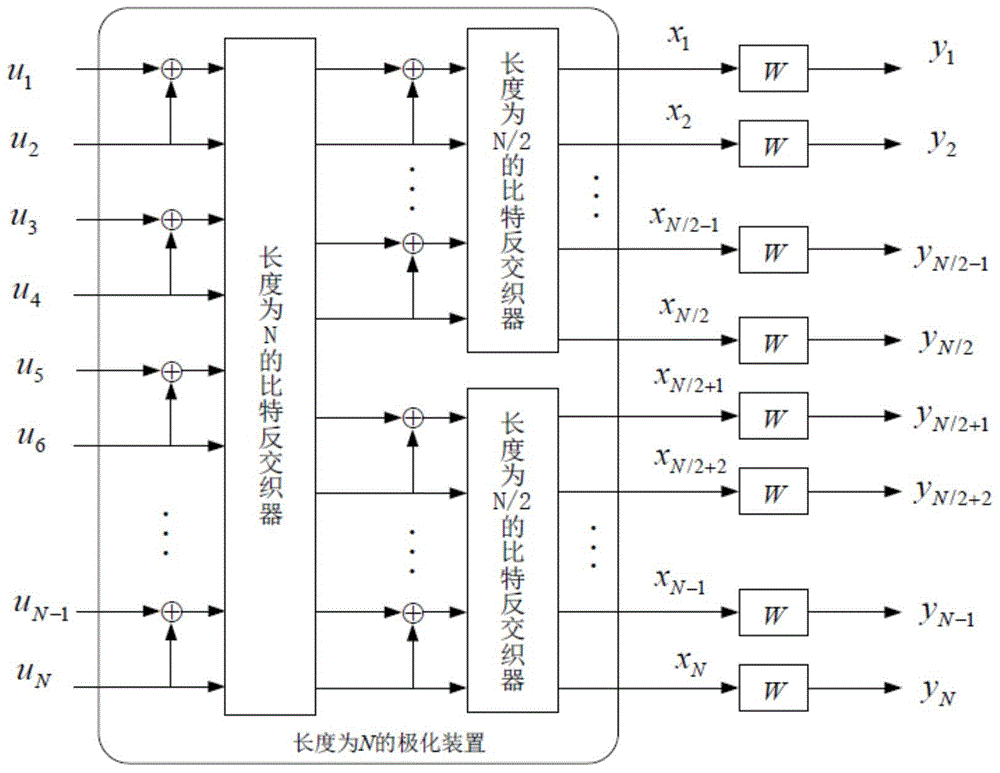
[0030] see Figure 4 , introduce the source coding method based on the polar code of the present invention:
[0031] First determine the symbol value set of the source recovery signal, and then use the best symbol-to-bit mapping rule to serially map the source symbol sequence into a bit soft information sequence, and polarize the bit soft information sequence The serial offset coding is to find the coding path with the largest reliability value and the bit sequence corresponding to the coding path, and finally select the most important bits from the bit sequence as the coding result through the reliable bit set.
[0032] see Figure 5 , specifically introduce the following steps of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com