Secured logon method for variable secret key encryption under HTTP
A technology of secure login and key encryption, which is applied in the field of secure login with variable key encryption, can solve the problems of counterfeit security and easy leakage of passwords, and achieve the effect of security guarantee
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0023] In the present embodiment, the secure login method of variable key encryption under the HTTP protocol comprises the following steps:
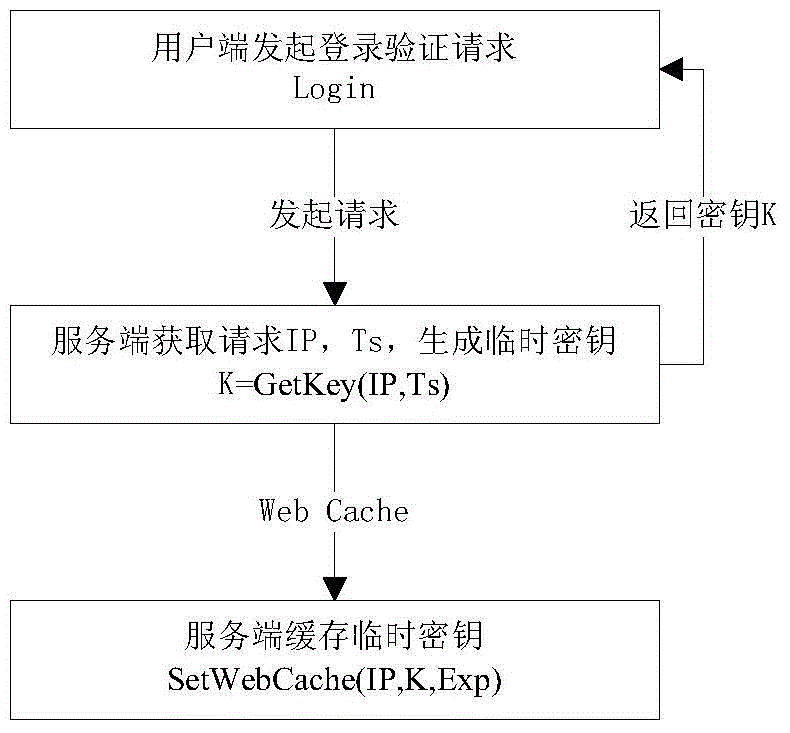
[0024] 1) For the login verification request initiated by the client, the server generates a temporary key according to the login verification request, sends the temporary key back to the client, and caches the temporary key in the server cache with the client IP address as the key value.
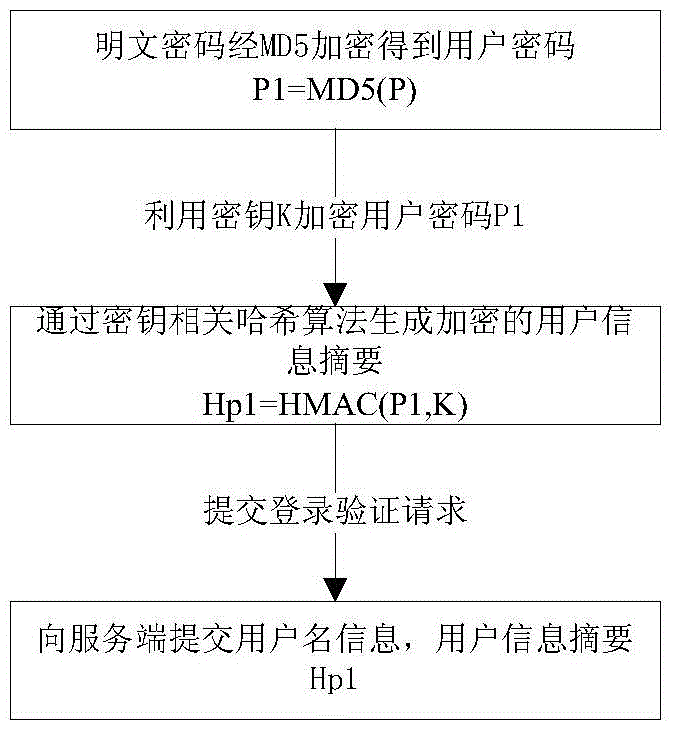
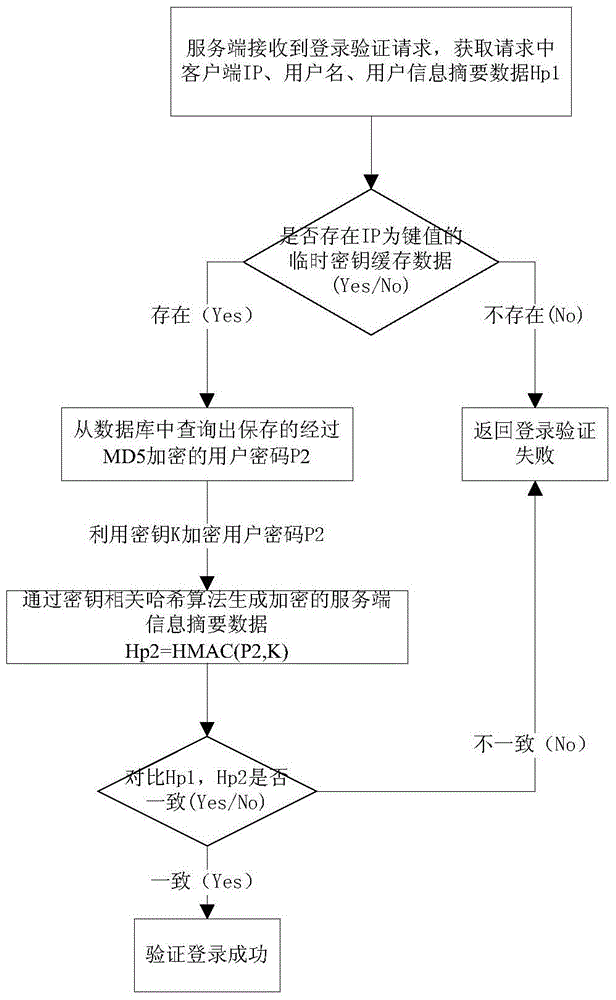
[0025] see figure 1 , when the client initiates a login verification request, the server receives the request and obtains the IP address (IP) of the client that initiated the current login verification request session as the first parameter for generating the temporary key, and at the same time obtains the current login verification request Timestamp data (Ts) at that time, as the second parameter to generate the temporary key, through the key generation algorithm K=GetKey(IP,Ts), get a temporary key K processed by base64 encoding, and then the tempor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com