Trusted verifying method and equipment used in running process of virtual machine
A verification method and virtual machine technology, applied in the direction of digital data authentication, software simulation/interpretation/simulation, program control devices, etc. And other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
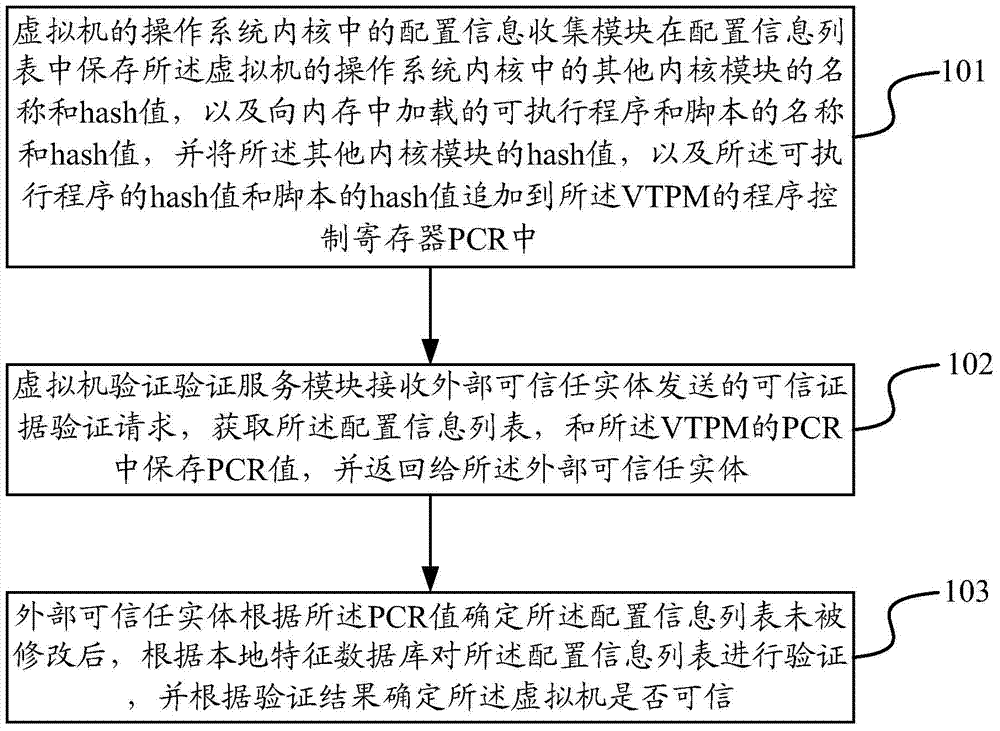
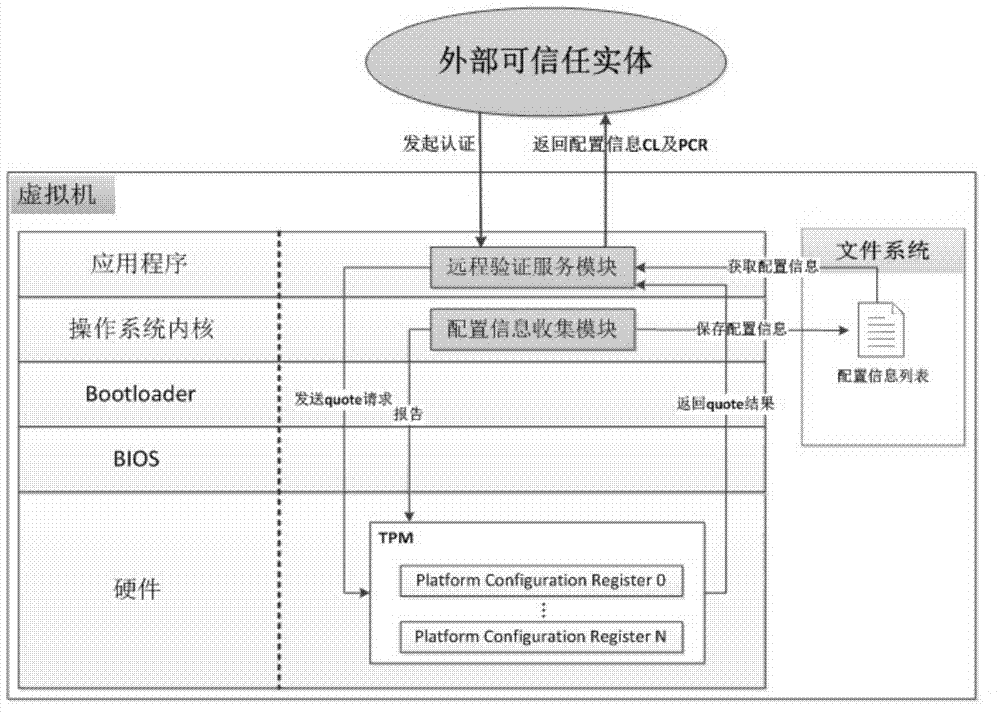
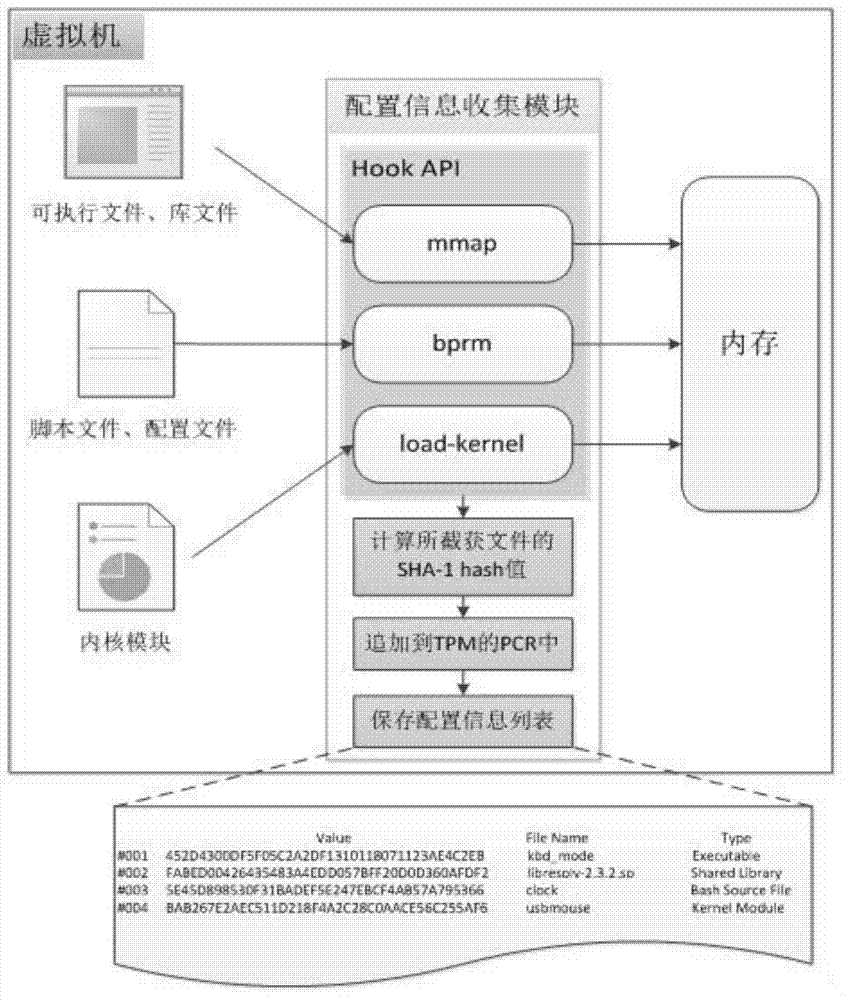
[0035] Aiming at the above-mentioned technical problems in the prior art, an embodiment of the present invention provides a technical solution for trusted verification when a virtual machine is running, which is applied to a system including a virtual machine and an external trusted entity. In this technical solution, the virtual machine includes a configuration information collection module, a remote verification service module, and a VTPM; the configuration information collection module in the operating system kernel of the virtual machine saves in the configuration information list in the operating system kernel of the virtual machine The name and hash value of other kernel modules, as well as the name and hash value of the executable program and script loaded into the memory, and the hash value of the other kernel module, as well as the hash value of the executable program and the hash value of the script Added to the PCR (Program Control Register) of the VTPM; when the rem...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com