Security evaluating and detecting method used for cloud infrastructure
A technology of infrastructure and evaluation methods, applied in the field of information security, can solve the problems of lack of information security evaluation devices and methods, interference of analysis and processing work, waste of resources, etc., so as to speed up the execution of evaluation activities, reduce the extension of evaluation time, and reduce unnecessary occupied effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
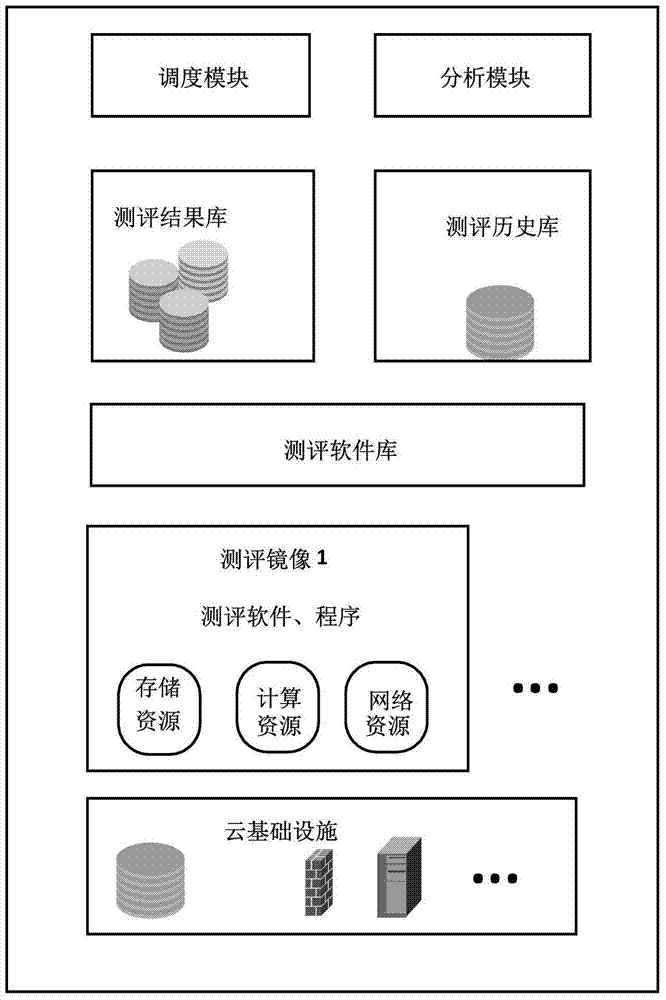
[0063] See figure 1 As shown, the device for security evaluation of cloud infrastructure in the present invention is composed of scheduling module, evaluation software library, evaluation image, evaluation configuration library, evaluation result library, analysis module, evaluation requirement book, evaluation report and other modules.
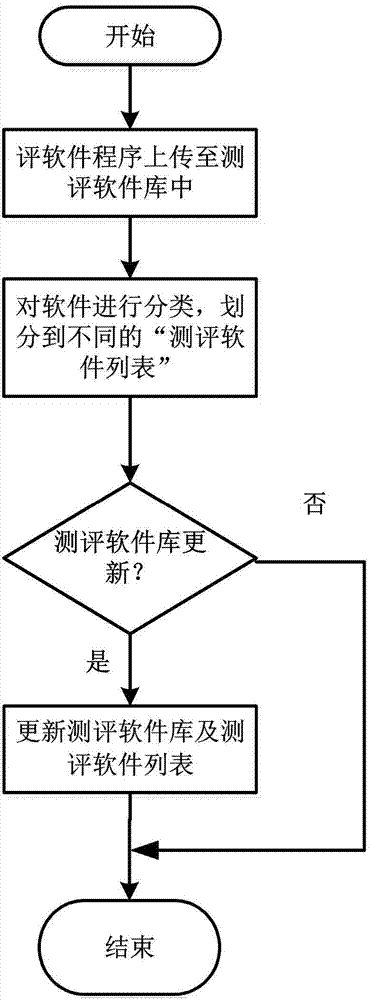
[0064] Before the evaluation, the user has to configure the evaluation software library in advance; for the specific process, see figure 2 shown. Upload the existing cloud infrastructure security evaluation software and self-written evaluation software programs to the evaluation software library. According to the usual classification: system security, network security, data security, behavioral security, etc., these software are classified and divided into different "evaluation software lists". The evaluation software library can be continuously updated to ensure the advancement and maturity of the evaluation software.
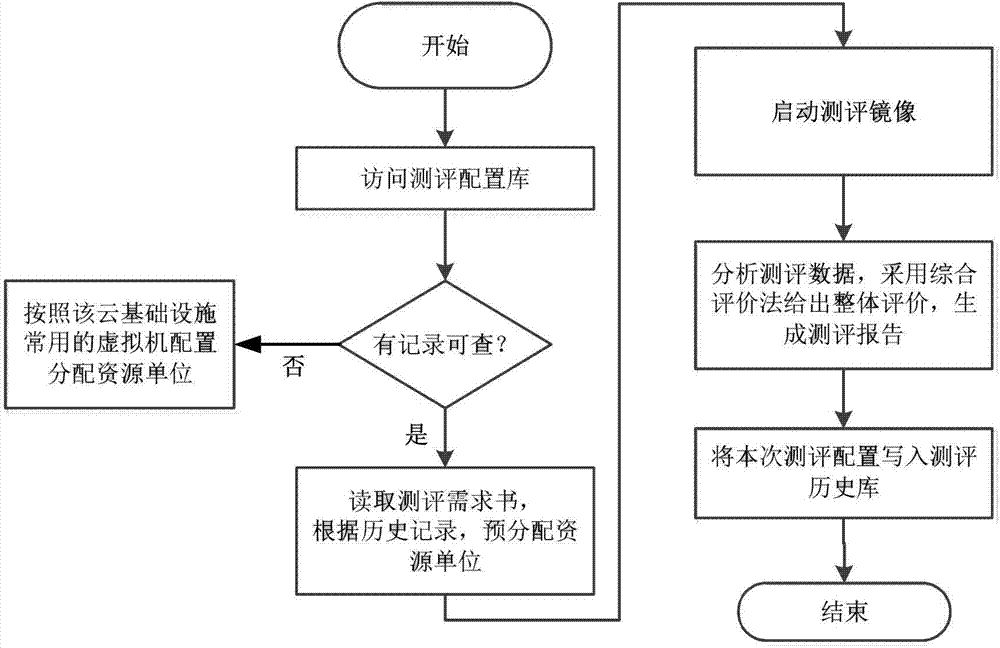
[0065] The comple...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com