A vulnerability management system and method
A vulnerability management and vulnerability technology, applied in the field of vulnerability management system, can solve problems such as low work efficiency, difficulty in sharing hardening experience, and difficulty in accurately evaluating the health and security threats of the network management network, so as to achieve the effect of improving quality and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
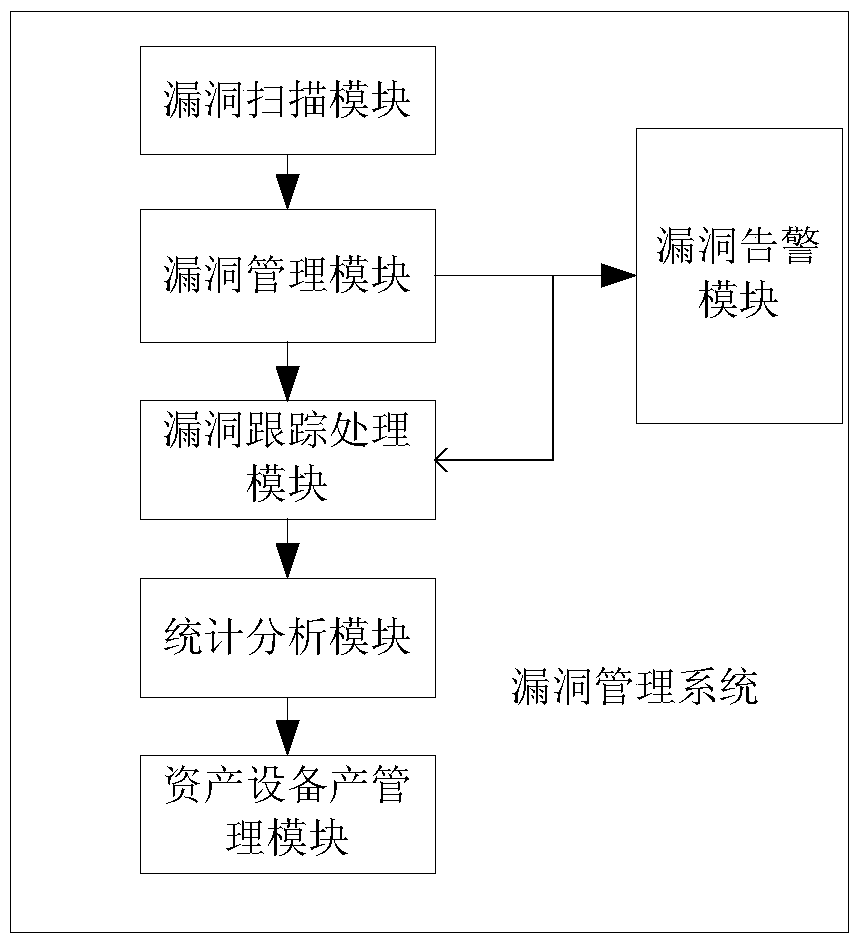
[0036] like figure 1 As shown, this embodiment discloses a vulnerability management system, including
[0037] The vulnerability scanning module is used to scan the vulnerabilities in the system and generate a vulnerability scanning report;
[0038] The vulnerability management module is used to import the vulnerability scanning report, manage the vulnerability through the analysis of the vulnerability scanning report, format and present the related information of the leakage, and record the business system and the scanning batch of the vulnerability information for subsequent use Comparative analysis; used to provide automatic update of vulnerability processing status, information display and vulnerability repair reference solutions, where the vulnerability repair reference solution is selected from the vulnerability repair solution library, and the relevant reference solutions and technical points are extracted from the vulnerability repair solution library. Managers can ar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com