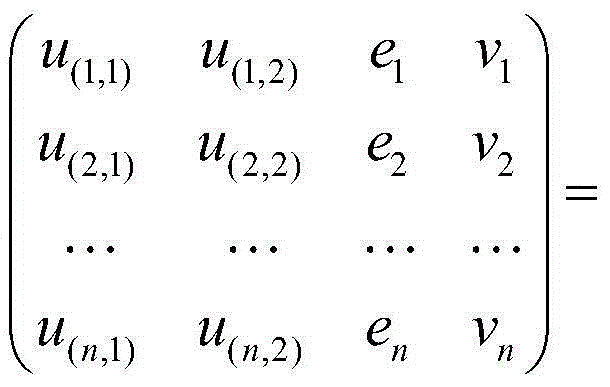Batch Cramer-Shoup cryptosystem based on batch processing exponential operation product
A batch processing and exponential technology, applied in the field of cryptography in information security, can solve the problems that mobile devices cannot bear the consumption and the amount of calculation is huge.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
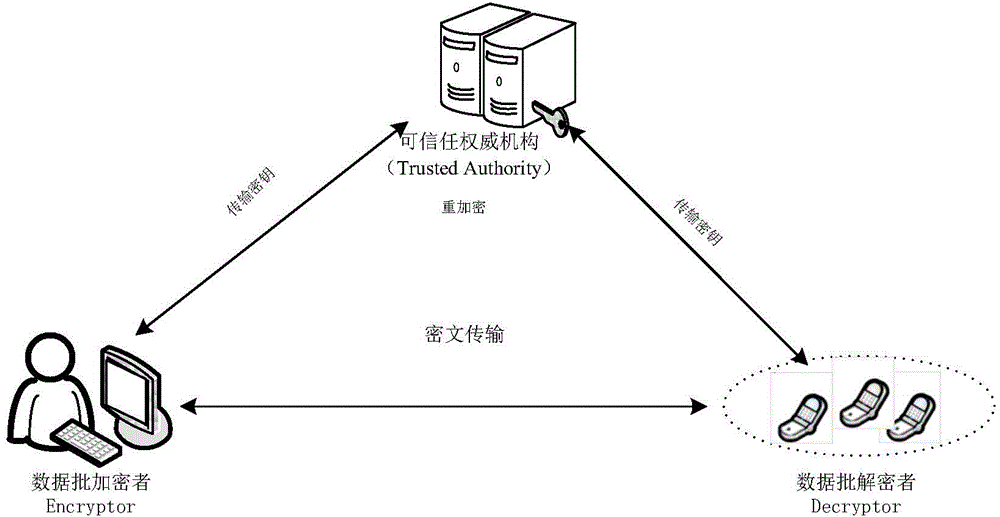
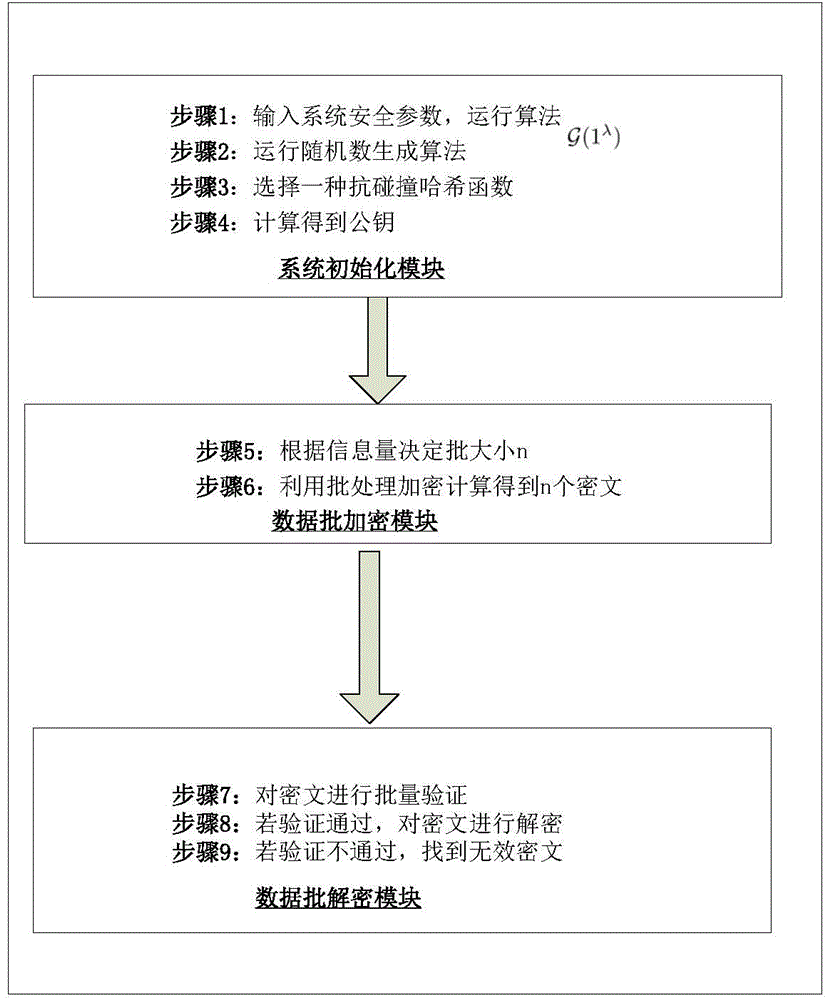
[0041] The invention is a batch Cramer-Shoup encryption system based on batch processing exponential operation product, and the method is realized by three modules: a system initialization module, a data batch encryption module and a data batch decryption module. figure 1 It is a system architecture diagram of the method of the present invention. The system flow of the batch Cramer-Shoup cryptosystem operation based on the batch exponential operation product figure 2 , combined with the flow chart, the specific implementation steps of the method are introduced as follows:
[0042] Module 1: The system initialization module can trust the authority (TA) to call the initialization algorithm, select security parameters and anti-collision hash functions, and generate public and private keys.
[0043] Step 1: TA inputs the system security parameter λ, and runs the initialization algorithm g(1 λ ), output a group whose order is a prime number q
[0044] Step 2: TA then runs the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com