Data diagram detection method for industrial control system malicious data attack
A technology for industrial control systems and malicious data attacks. It is applied in the fields of electrical digital data processing, instruments, and platform integrity maintenance. It can solve problems such as the inability to meet the "Stuxnet" virus injection attack, complex models, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be further described below in conjunction with the accompanying drawings.
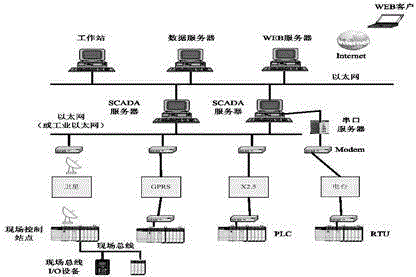
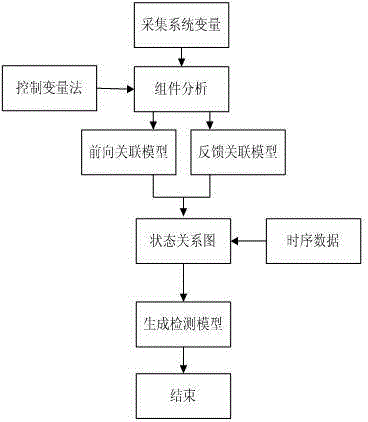
[0038] Such as figure 1 As shown, this is a schematic diagram of the SCADA system, giving the main components and conventional configuration of the SCADA system. The control center includes SCADA server (MTU) and communication router, also includes HMI, engineer station and data logging server, these devices communicate through LAN connection. The invention allows users to customize the subset of system variables, and also provides another way to automatically extract independent component information from the SCADA system. Collect a set of such system variables using the above method to A total of 6 different variables are represented. The detection process of the present invention is as figure 2 shown.
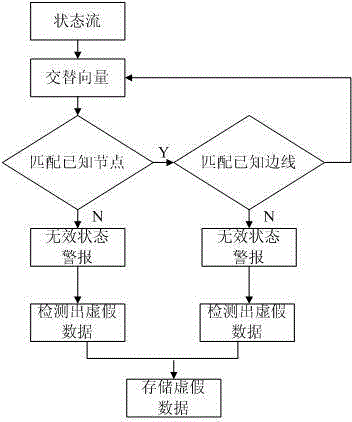
[0039] The next step is to process the data, that is, to find out the internal relationship of the data. According to the relationship between variables at dif...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com