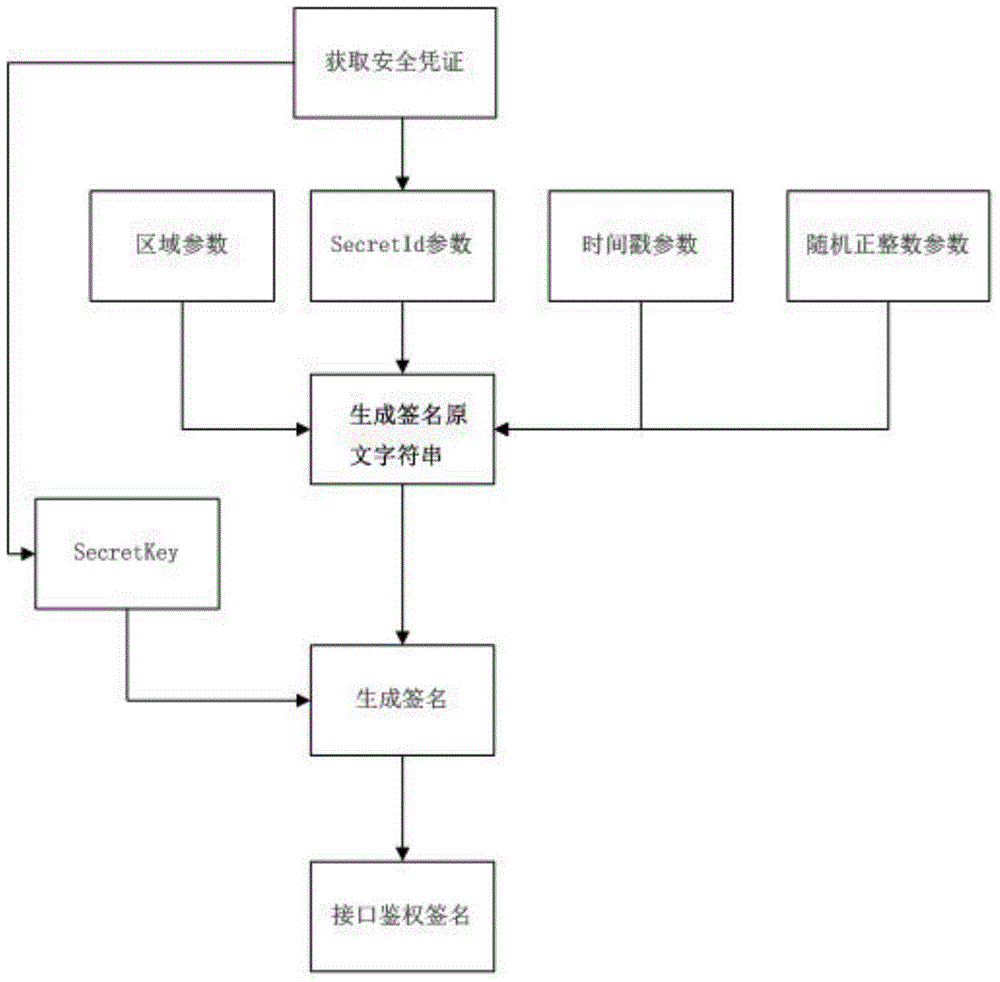
Interface authentication signature method facing cloud platform
A cloud platform and interface technology, applied in the direction of digital transmission system, electrical components, transmission system, etc., can solve the problems that the interface authentication extension cannot be unified, and the requirements for safe and convenient interface access are not met, so as to overcome the singleness and Low efficiency, guaranteed non-interference, wide application effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The prior art used in the present invention mainly relates to the following aspects:
[0030] 1. Spring Security
[0031] Spring Security is a security framework that can provide declarative security access control solutions for Spring-based enterprise application systems. It provides a set of beans that can be configured in the Spring application context, making full use of the Spring Inversion of Control technology (Inversion of Control), Dependency Injection (Dependency Injection) and aspect-oriented programming technology functions to provide declarative security for the application system Access control functions.
[0032] 2. Hibernate Validator
[0033] Data validation is a function that any application will use, whether it is the display layer or the persistence layer. The same verification logic will be scattered in each layer. Developers often write these verification logic directly in the domain model, but this mixes the domain model code and verification c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com