U disc capable of being encrypted and encryption method thereof
An encryption method and data encryption technology, applied in digital data protection, internal/peripheral computer component protection, preventing unauthorized use of memory, etc., can solve computer host infection, password theft, and illegal reading of encrypted files in U disks and other issues, to achieve the effect of eliminating cumbersome steps and potential safety hazards
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
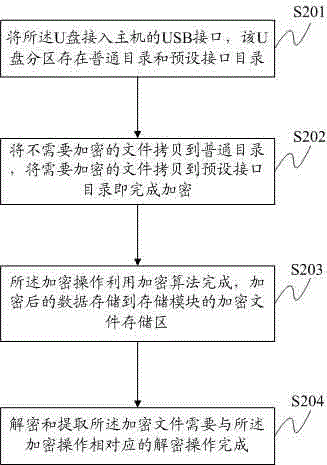
[0031] The present invention provides a specific embodiment of an encryptable U disk and its encryption method, in order to enable those skilled in the art to better understand the technical solutions in the embodiments of the present invention, and to make the above-mentioned purposes, features and methods of the present invention The advantages can be more obvious and easy to understand, and the technical solution in the present invention will be further described in detail below in conjunction with the accompanying drawings:
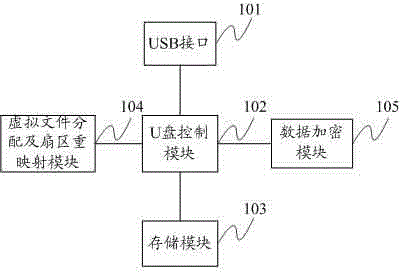
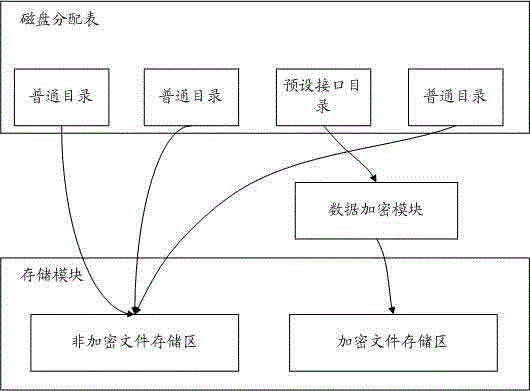
[0032] The present invention firstly provides a kind of encryptable U disk, such as figure 1 As shown, it includes: USB interface 101, U disk control module 102, storage module 103, virtual file allocation and sector remapping module 104 and data encryption module 105:
[0033] The U disk control module 102 is used for data monitoring and processing of the virtual file distribution and sector remapping module 104 and the data encryption module 105, ac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com