A Method of Monitoring Router Selection Based on Mutual Information
A technology of mutual information and routers, applied in the field of communication networks, can solve problems such as inability to complete router monitoring tasks, large resource consumption, network performance degradation, etc., to reduce system monitoring overhead, avoid resource consumption, and achieve high information reliability. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] An embodiment of the present invention will be further described below in conjunction with the accompanying drawings.
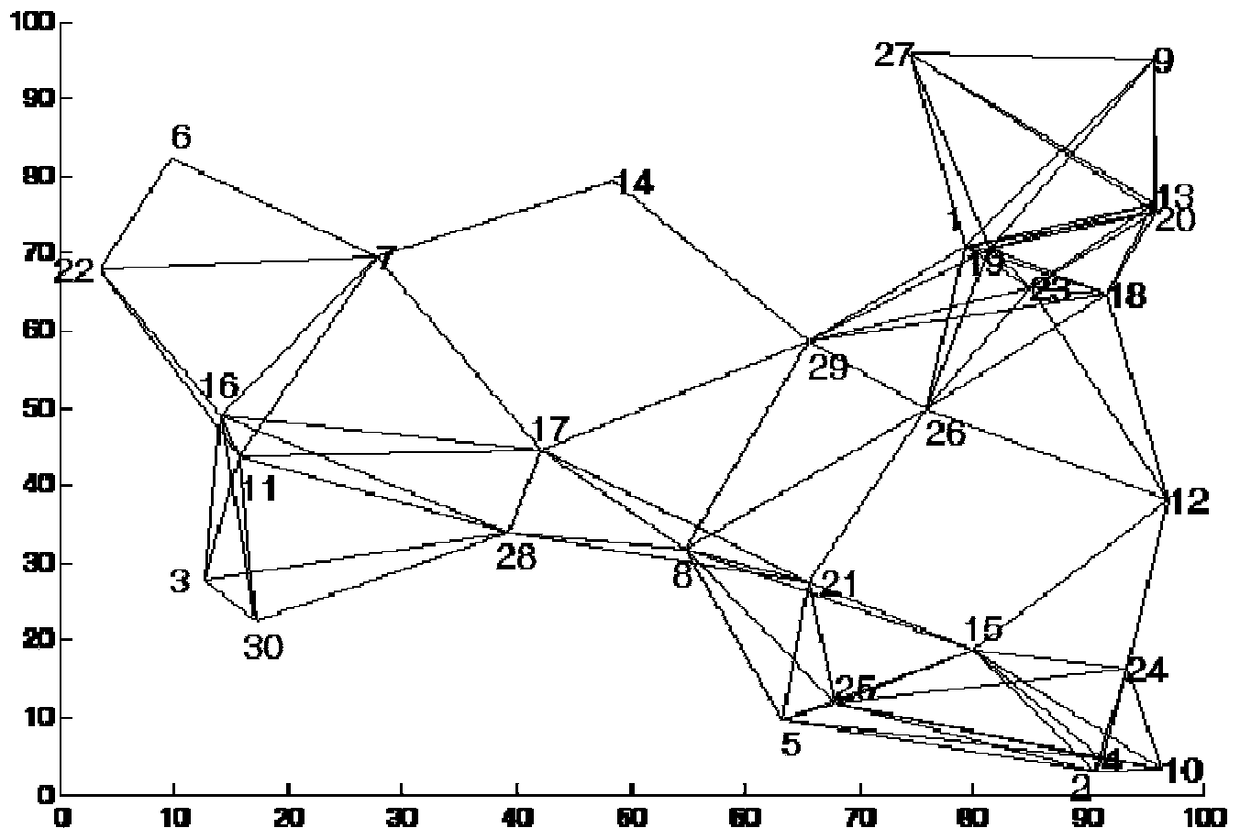
[0031] In the embodiment of the present invention, the number of randomly generated routers is 30 wireless Mesh networks, and the schematic diagram of the network topology is as follows figure 1 As shown, the 30 routers in the topology are all wireless routers, the wireless routers are single radio frequency, and the wireless links do not interfere with each other;
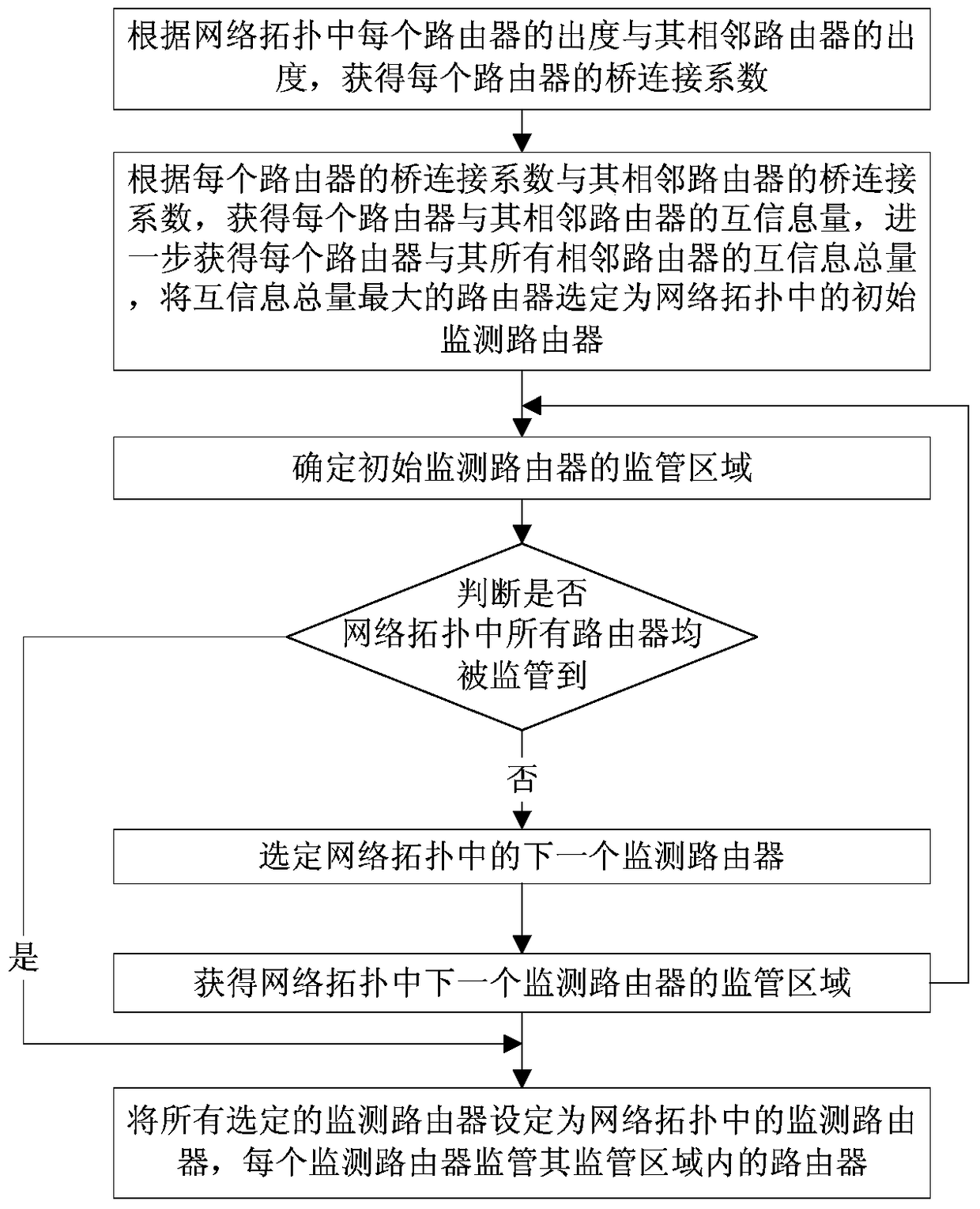
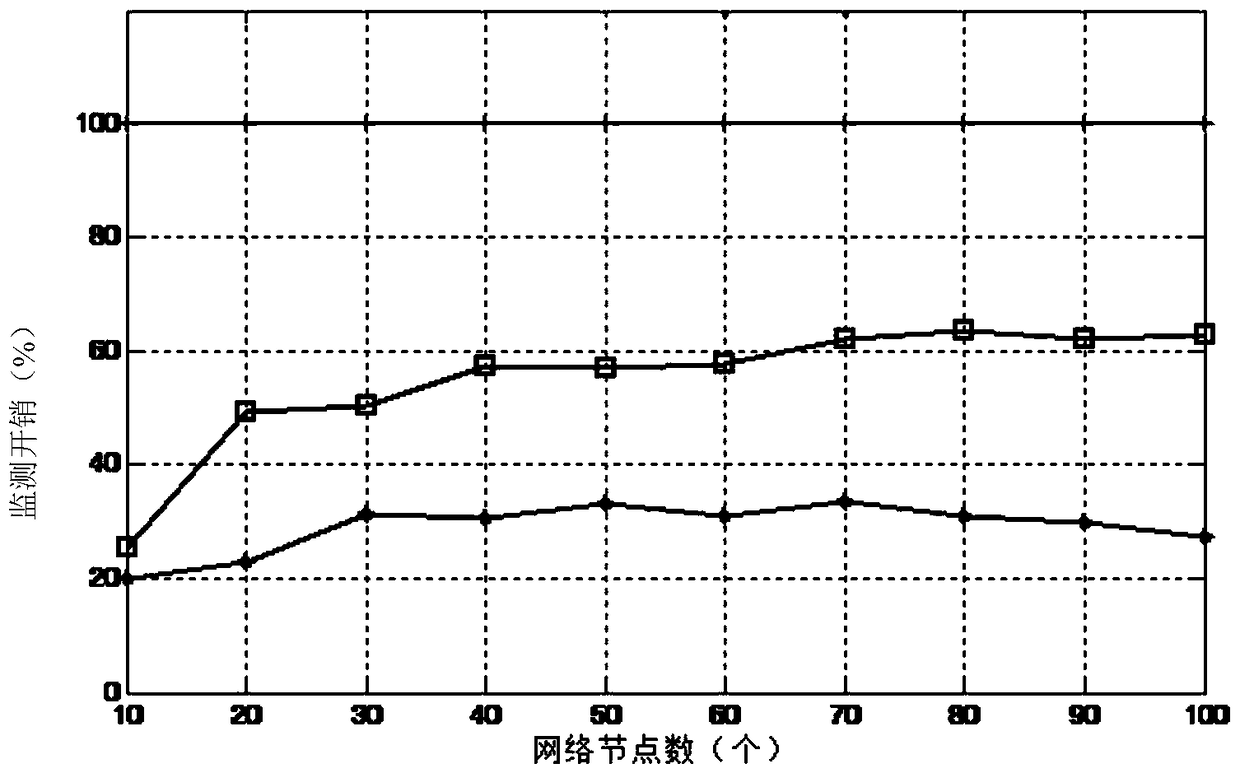
[0032] In the embodiment of the present invention, a monitoring router selection method based on mutual information, the method flow chart is as follows figure 2 shown, including the following steps:
[0033] Step 1. Obtain the bridge connection coefficient of each router according to the out-degree of each router in the network topology and the out-degree of its adjacent routers;
[0034] In the embodiment of the present invention, the described bridge connection coefficient of obtaini...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com