Software security flaw discovering system
A software security and defect technology, which is applied in the field of software security defect discovery system, can solve problems such as difficult to understand format, difficulty, and high learning cost of defect reports, and achieve the effects of improving the detection range, reducing the difficulty of use, and improving detection efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be described in detail below with reference to the accompanying drawings and examples.
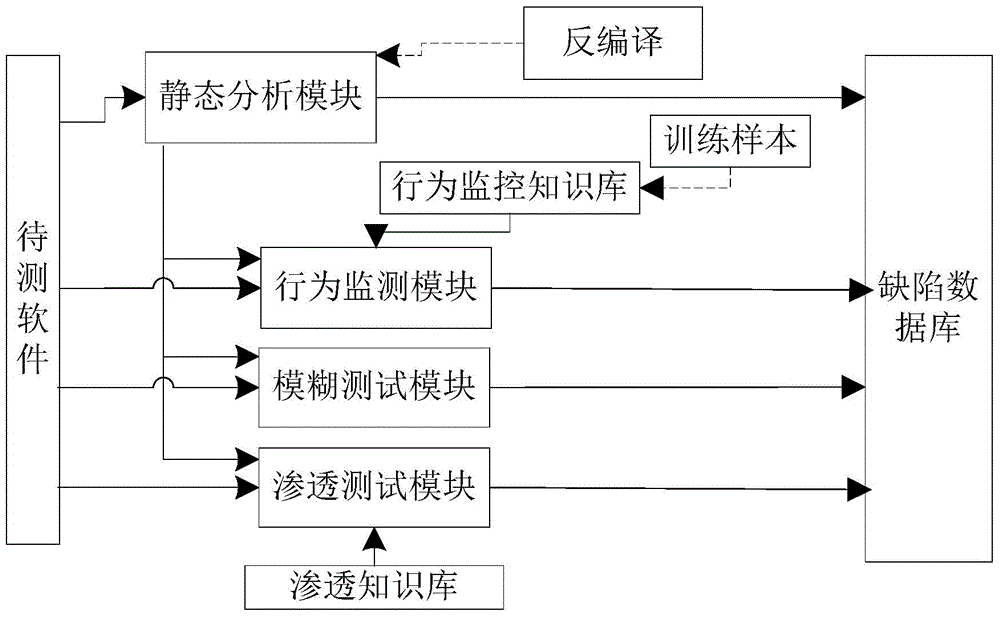
[0026] The present invention provides a software security defect discovery system (hereinafter referred to as the system), such as figure 1 As shown, it includes behavior static testing module, behavior monitoring module, fuzz testing module, penetration testing module, knowledge base and defect database; where, the knowledge base includes behavior monitoring knowledge base and penetration knowledge base, and the behavior monitoring knowledge base is used to store behavior The sequence call sequence segment generated by the software training of the monitoring module is used as a reference call sequence, and the penetration knowledge base is used to store penetration test cases for penetration testing; the defect database is used to store sorted and formatted defect data.
[0027] The security detection of the software to be tested is completed by the monit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com