Key extraction method of palm print-palm vein double-source fuzzy vault
A fuzzy safe and key extraction technology, which is applied in the field of identity authentication, can solve the problems of threatening FV security, leaking, fingerprint FV is difficult to resist brute force attacks, etc., and achieves the effect of ensuring privacy and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention adopts the following scheme, a key extraction method for palmprint and palm vein dual-source fuzzy safe, characterized in that the method steps are as follows:
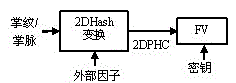
[0027] (1) Extend 2DPHC-based FV from palm print to palm vein. Palmprint or palm vein features and external factors generate 2DPHC through 2DHash transformation (Reference: LuLeng, AndrewTeoh, MingLi, MuhammadKhurramKhan.Analysisofcorrelationof2DPalmHashCodeandorientationrangesuitablefortransposition[J].Neurocomputing,2014,131:377-387), and then use 2DPHC as the protected palmprint Or palm vein template to construct FV, which constitutes a hybrid scheme.
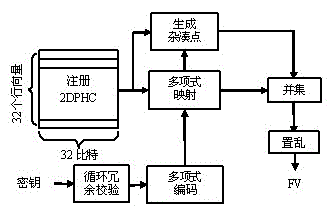
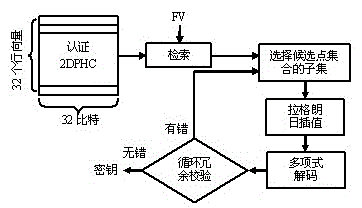
[0028] (2) During single-source registration, lock palmprint or palm vein FV. Convert the set key and its cyclic redundancy code into real numbers after segmentation, and construct n Order polynomial coefficients. The point set in FV is unordered, while 2DPHC is an ordered matrix. Due to the dislocation between the 2DPHC templates, m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com