Malicious clicking behavior detection method and device
A malicious click and detection method technology, applied in the Internet field, can solve the problems of poor real-time performance and poor user experience, and achieve the effect of good real-time detection and good user experience.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
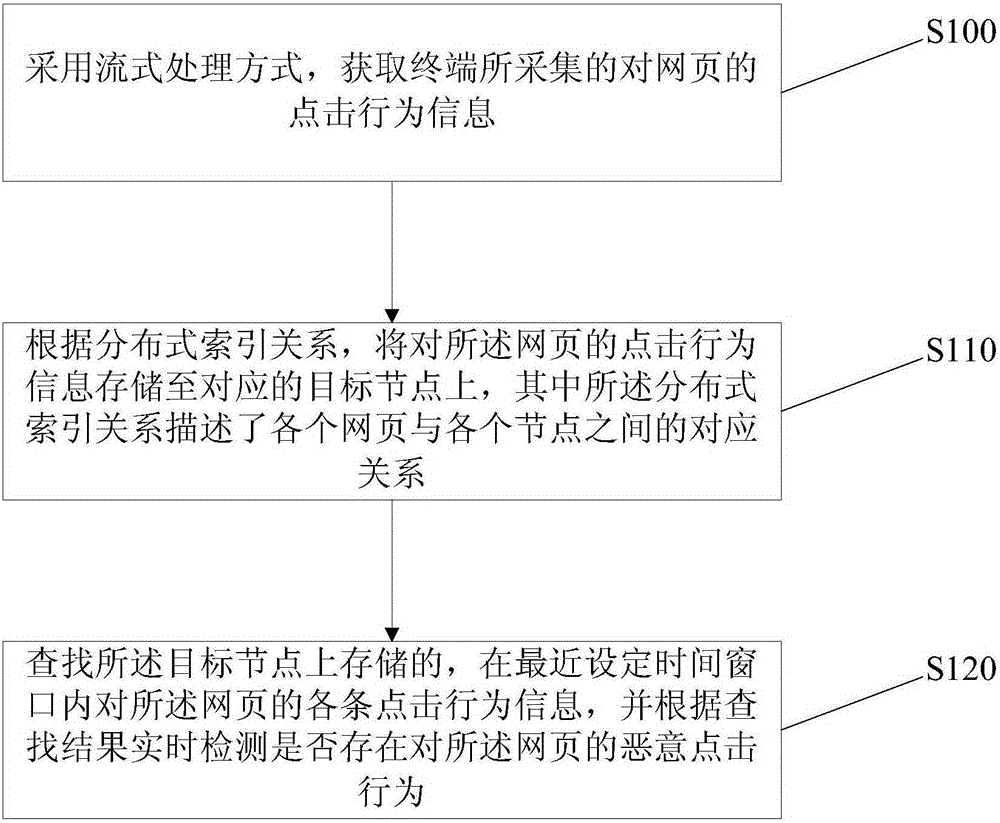
[0024] figure 1 It is a schematic flow chart of a method for real-time detection of malicious click behavior provided by Embodiment 1 of the present invention. The method can be executed by a device for real-time detection of malicious click behavior. The device is implemented by software, and the device can be built into the Internet SEM ( On a physical device (such as a server) in the SearchEngineMarketing (search engine marketing) system, or built into the physical device that the merchant provides website services to customers. see figure 1 , a method for real-time detection of malicious click behavior provided in this embodiment, specifically includes the following operations:
[0025] Operation S100, adopting a stream processing method to acquire click behavior information on webpages collected by the terminal.
[0026] Each time the terminal monitors a click behavior on a web page, it will generate a corresponding piece of click behavior information and upload it in a...
Embodiment 2
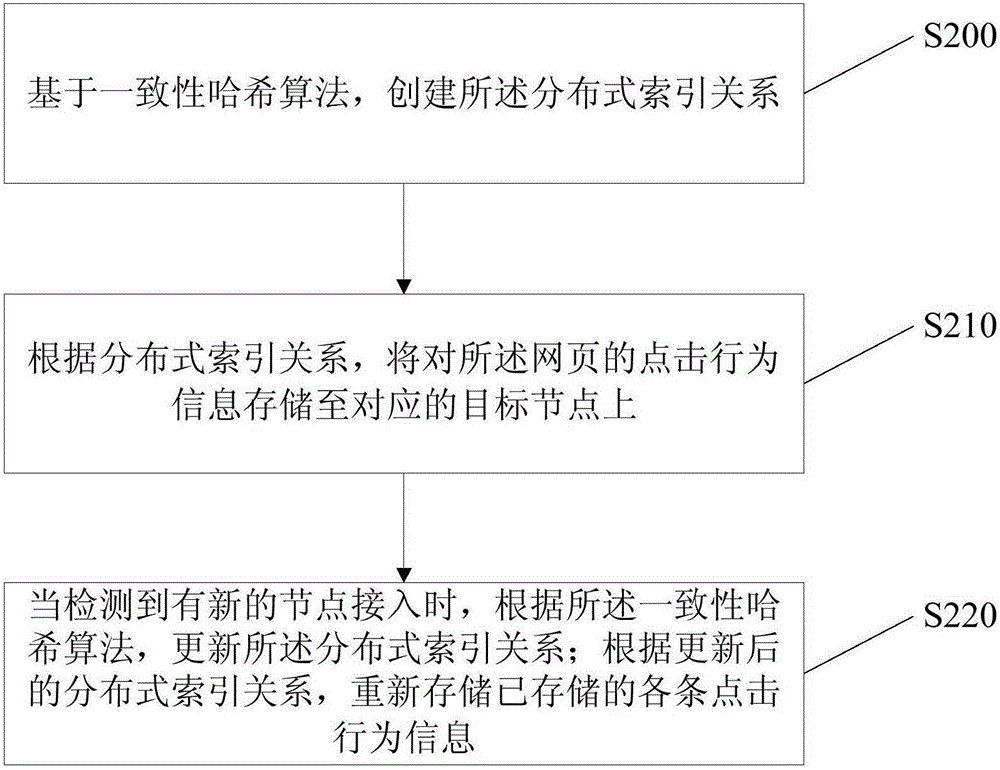
[0035] figure 2 It is a flow chart of updating the distributed index relationship operation in the real-time detection method for malicious click behavior provided by Embodiment 2 of the present invention. On the basis of Embodiment 1, this embodiment further adds: based on the consistent hash algorithm, create The distributed index relationship;
[0036] The method further adds: when a new node access is detected, the distributed index relationship is updated according to the consistent hash algorithm; the stored index relationship is re-stored according to the updated distributed index relationship. Individual click behavior information.
[0037] refer to figure 2 As shown, the method for real-time detection of malicious click behavior includes the following operations:
[0038] Operation S200: Create the distributed index relationship based on a consistent hash algorithm.
[0039] Monitor the click behavior information of a single website within a set time window (whi...
Embodiment 3
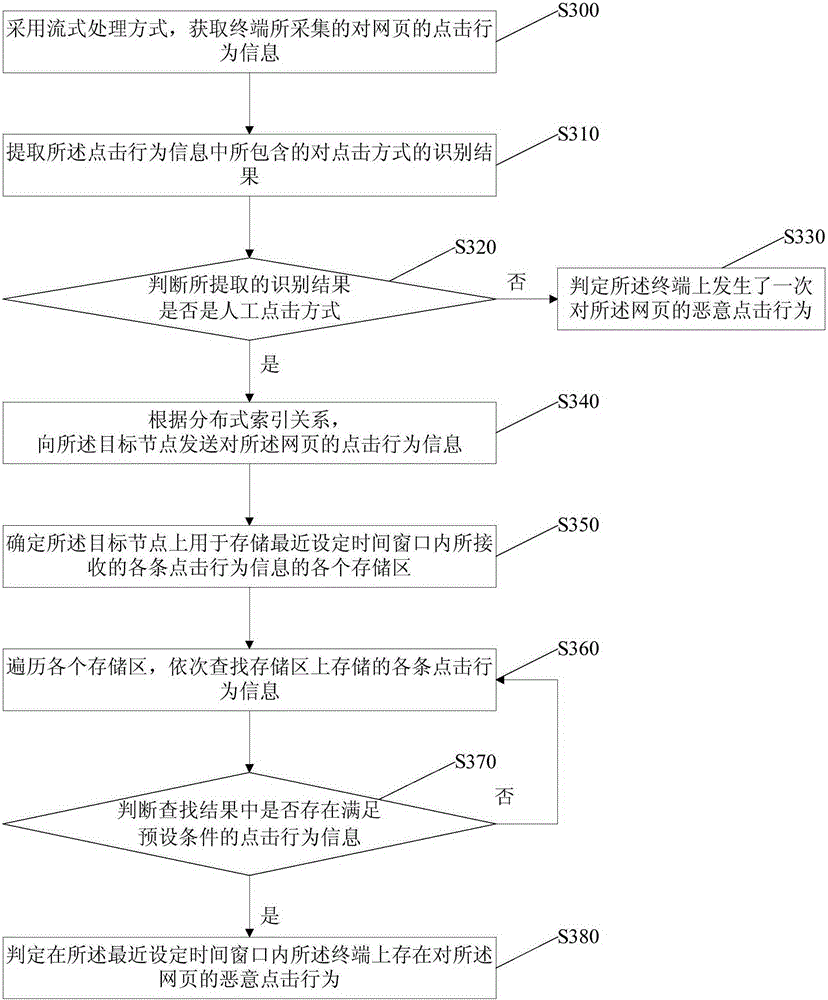
[0046] image 3 It is a flow chart of a real-time detection method for malicious click behavior provided by Embodiment 3 of the present invention. On the basis of the above embodiment, this embodiment further stores the click behavior information on the web page on the corresponding target node The specific optimization is: send the click behavior information on the webpage to the target node, so that the target node stores the click behavior on the webpage according to the pre-created sub-index relationship and the time sequence of receiving the click behavior information information, wherein the sub-index relationship describes the corresponding relationship between each time period when the target node receives click behavior information and each storage area.
[0047] Searching for each piece of click behavior information stored on the target node within the latest set time window is specifically optimized as follows: according to the sub-index relationship, determine that...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com