A method and device for protecting an Android application program based on code fragmentation
An application and application package technology, applied in the direction of program/content distribution protection, digital data protection, computer security devices, etc., can solve problems such as memory theft, reduce the possibility, balance protection strength and performance overhead, and protection strength high effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
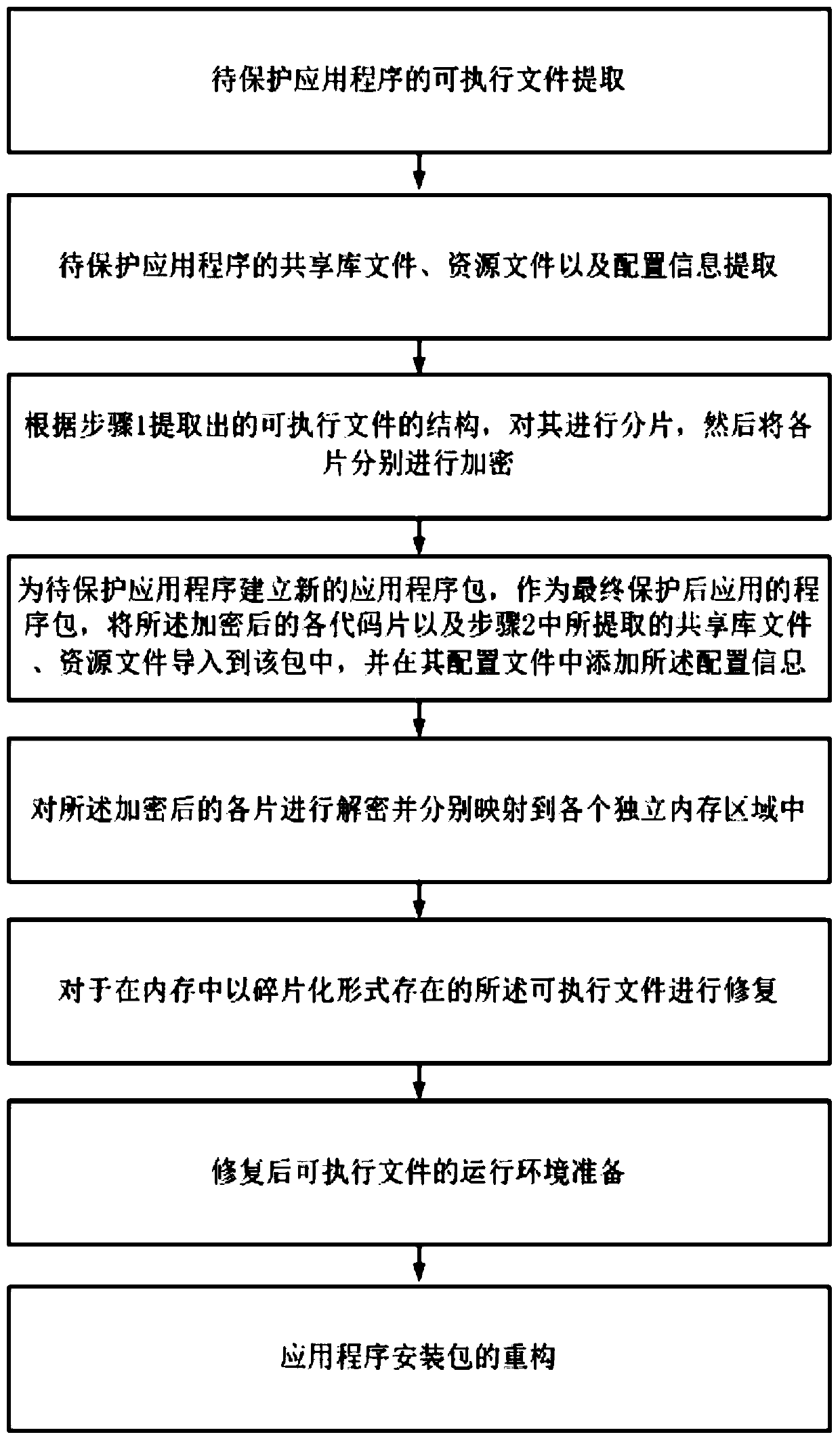
[0042] Such as figure 1 Shown, the Android application packing protection method based on code fragmentation of the present invention comprises the following steps:
[0043] Step 1, extract executable files from the Android application program to be protected;
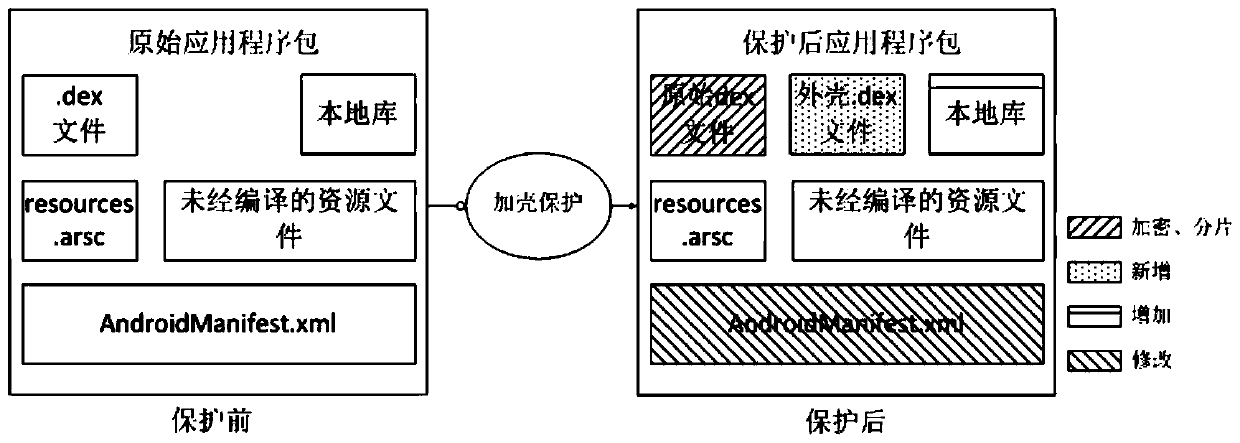
[0044] The Android application program is a compressed package in ZIP format. For an Android application program to be protected, it first needs to be decompressed, and then the executable file in it needs to be obtained. In the present invention, the executable file of the application refers to the executable file running on the Android Dalvik virtual machine, that is, the dex file.
[0045] Step 2, extract shared library file, resource file and configuration information from the Android application program to be protected; Concrete steps include:
[0046] Step 2.1, extract all shared library files from the decompressed Android application package;
[0047] In step 2.2, resource files include image files, layout fi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com