Method and device for preventing synchronous packet attack
A technology of synchronous packets and synchronous data packets, which is applied in the field of communication, can solve problems such as poor performance of the host device, loss of user data, occupation, etc., and achieve the effect of ensuring network paralysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0034] figure 1 It is a schematic flowchart of the method for preventing synchronous packet attacks provided by the present invention. Such as figure 1 Shown, method of the present invention comprises:
[0035] Step 101, pre-registering a hook (HOOK) function in the kernel, creating a tracking and monitoring linked list and a blacklist linked list, and setting a SYN packet threshold parameter and a recheck interval time parameter.
[0036] The present invention is based on the netfilter architecture. Netfilter is a Linux kernel firewall framework, which is concise and flexible, and can implement many functions in security policy applications, such as packet filtering, packet processing, address masquerade, transparent proxy, dynamic network address translation (NAT, NetworkAddressTranslation), and Based on user and media access control (MAC, MediaAccessControl) address filtering and state-based filtering, packet rate limit, etc.
[0037] Specifically, netfilter places some...
Embodiment 2
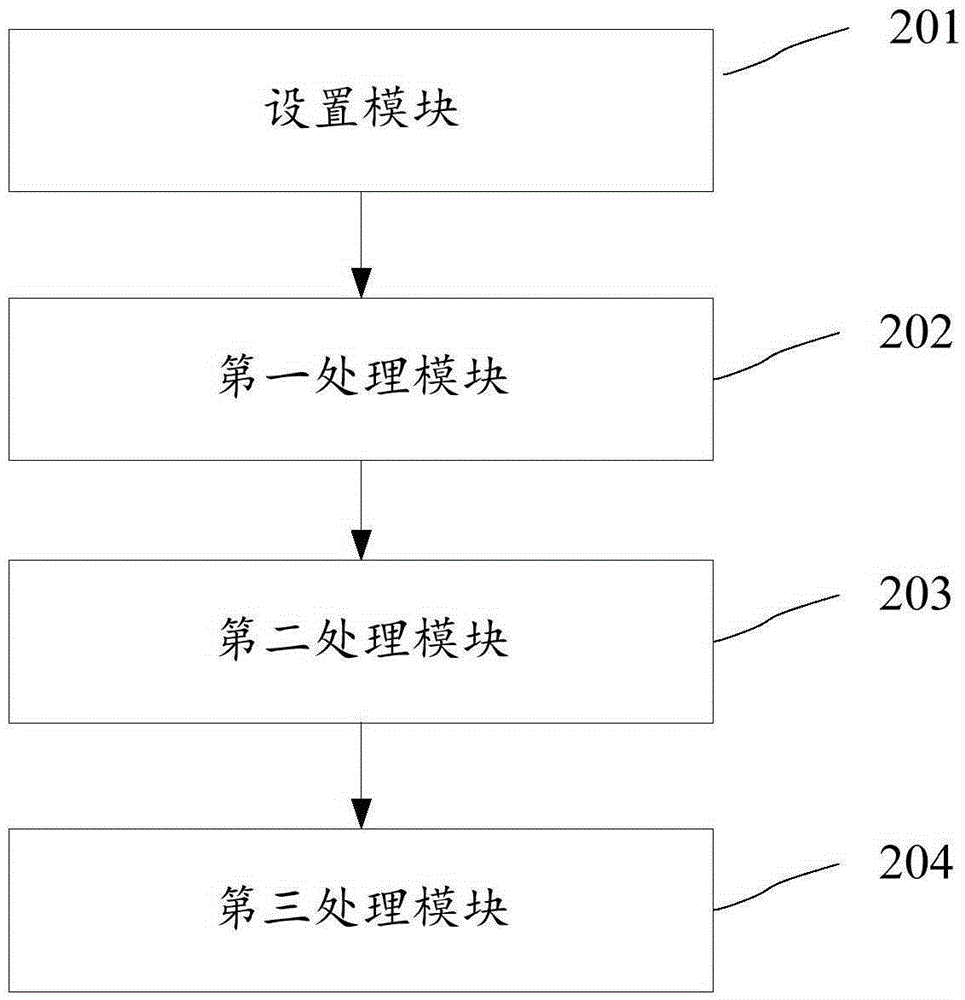
[0060] The present invention also provides a device for preventing synchronous packet attacks, such as figure 2 As shown, it includes: a setting module 201, a first processing module 202, a second processing module 203 and a third processing module 204, wherein,
[0061] The setting module 201 is used to pre-register the hook function in the kernel, create a tracking monitoring linked list and a blacklist linked list, and set the synchronization packet threshold and recheck interval time;
[0062] Specifically, the tracking and monitoring linked list includes an IP address field and a TCP connection data packet field; the length of the tracking and monitoring linked list is the number of IP addresses to be tracked and detected.
[0063] The blacklist linked list includes an IP address field and a blacklist flag field; when the blacklist flag is the first value, it means that the IP address is permanently added to the blacklist linked list, and the TCP connection packet sent b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com