A secondary authentication method based on out-of-band verification and enhanced otp mechanism
A secondary authentication and mechanism technology, applied in the fields of identity authentication and information security, it can solve the problems of password theft, hacker deciphering, fund theft, etc., achieve safe and convenient two-factor authentication, and eliminate the threat of phishing and man-in-the-middle attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
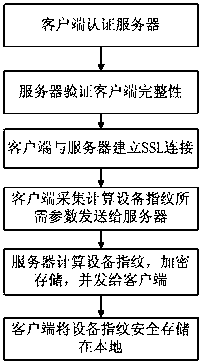
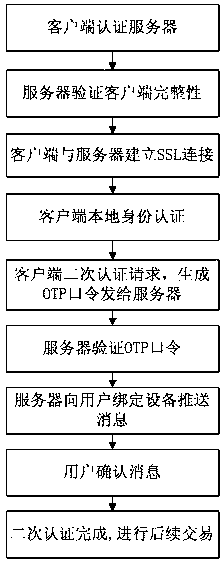
[0040] The present invention aims at the phishing problem and man-in-the-middle attack problem existing in the existing OTP token authentication, proposes an enhanced OTP mechanism, and combines out-of-band security communication, proposes a new type based on out-of-band verification and enhanced OTP mechanism Multi-factor authentication method, and its realization method is given at the same time. In order to more clearly illustrate the new identity authentication scheme and implementation method in the present invention, the present invention will be described in detail below in conjunction with the accompanying drawings and embodiments. Other feasible equivalent variations can be obtained from these figures.
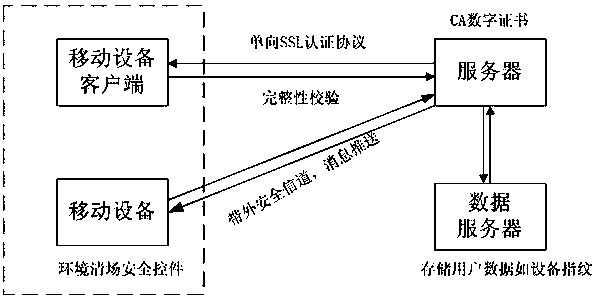
[0041] Such as figure 1As shown, it is a block diagram of the secondary authentication system based on the out-of-band verification and enhanced OTP mechanism of the present invention, and the system mainly involves the client, the server, the data server, and the mo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com