Route origin and path two-factor authentication method
A double verification, routing source technology, applied in the network field, can solve the problems of high network performance pressure of network equipment, and achieve the effect of reducing the verification process and improving the processing flow and efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
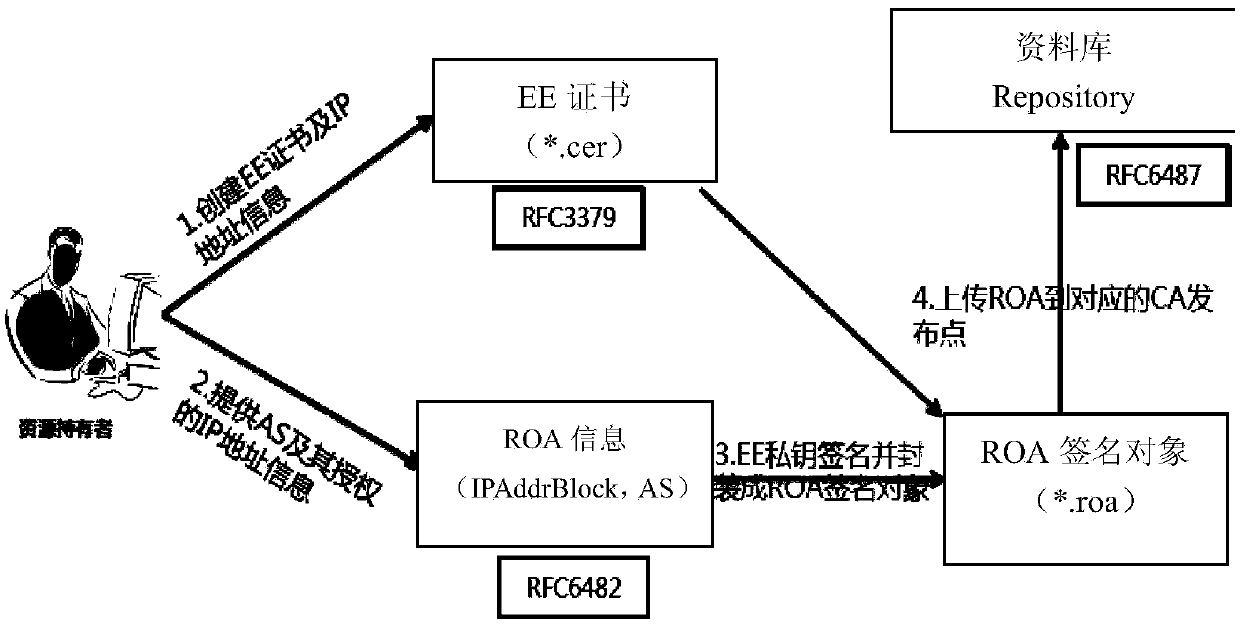
[0074] Embodiment 1: The value of ROA can be embedded into the path attribute.
Embodiment 2
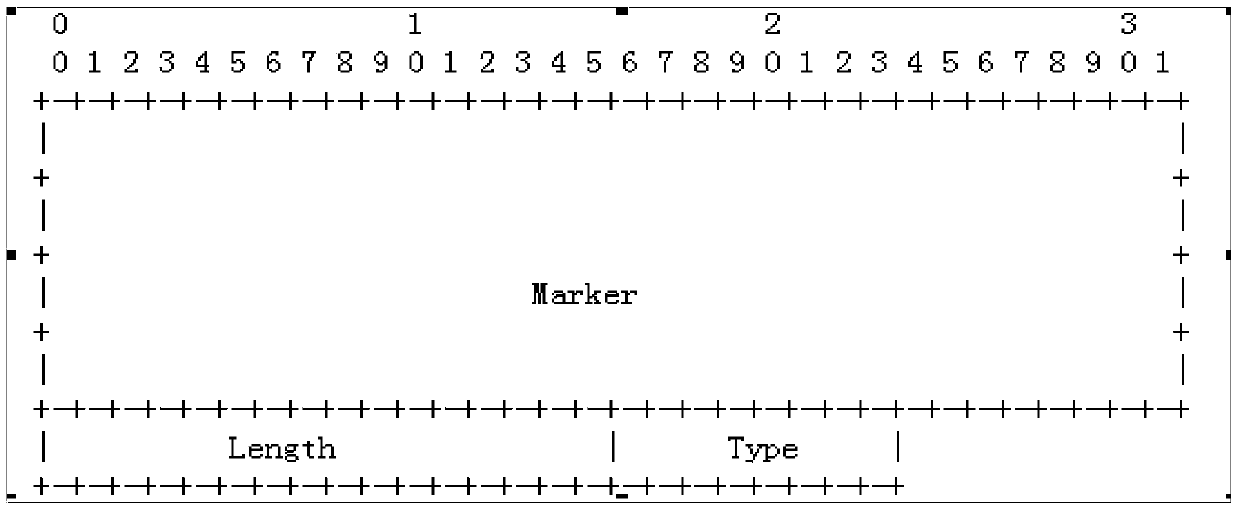
[0075] Embodiment 2: The BGP message can be extended, and a new option is added behind the network layer reachability information, which is used to store the value of ROA. The specific format is as follows:
[0076]
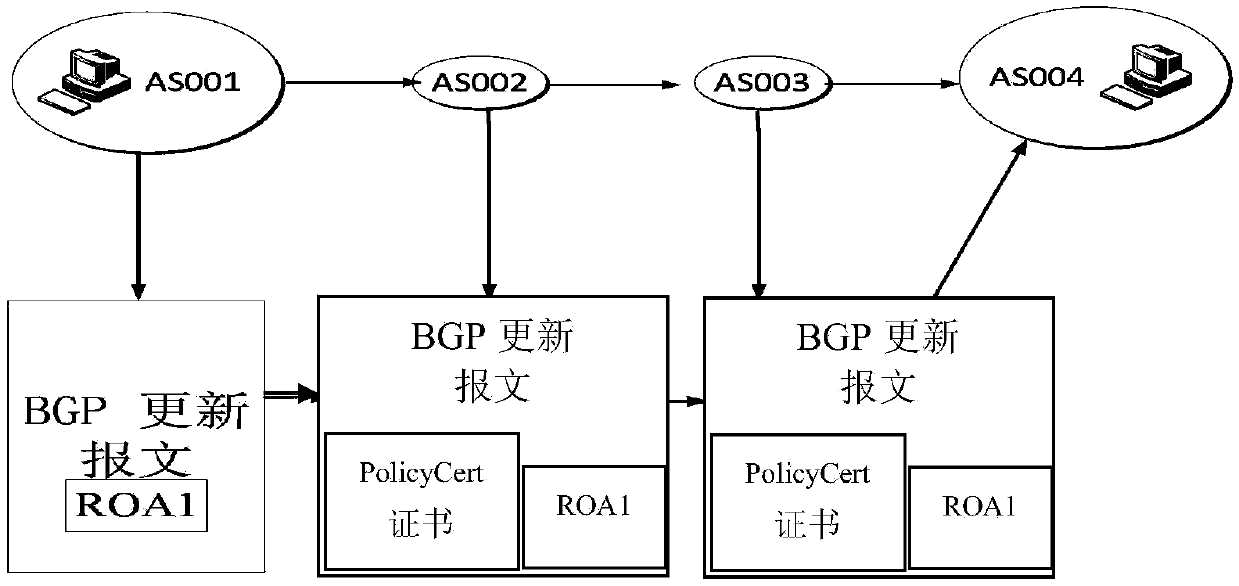
[0077] 1) The originating router sends update+roa;
[0078] 2) The second hop uses ROA to verify UPDATE;
[0079] Y: Forward update, no ROA is required, plus policycert;
[0080] N: Discard;
[0081] 3) The next-hop router directly trusts the previous hop;
[0082] Path validation is based on policycert.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com