A key-value storage method based on log-structure merged tree
A log and key-value technology, applied in the input/output process of data processing, instruments, input/output to record carriers, etc., can solve the problems of speeding up writing, writing amplification, reducing the frequency of sorting and merging, and avoiding I/O O operation, reduce write amplification problems, and improve the effect of throughput
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
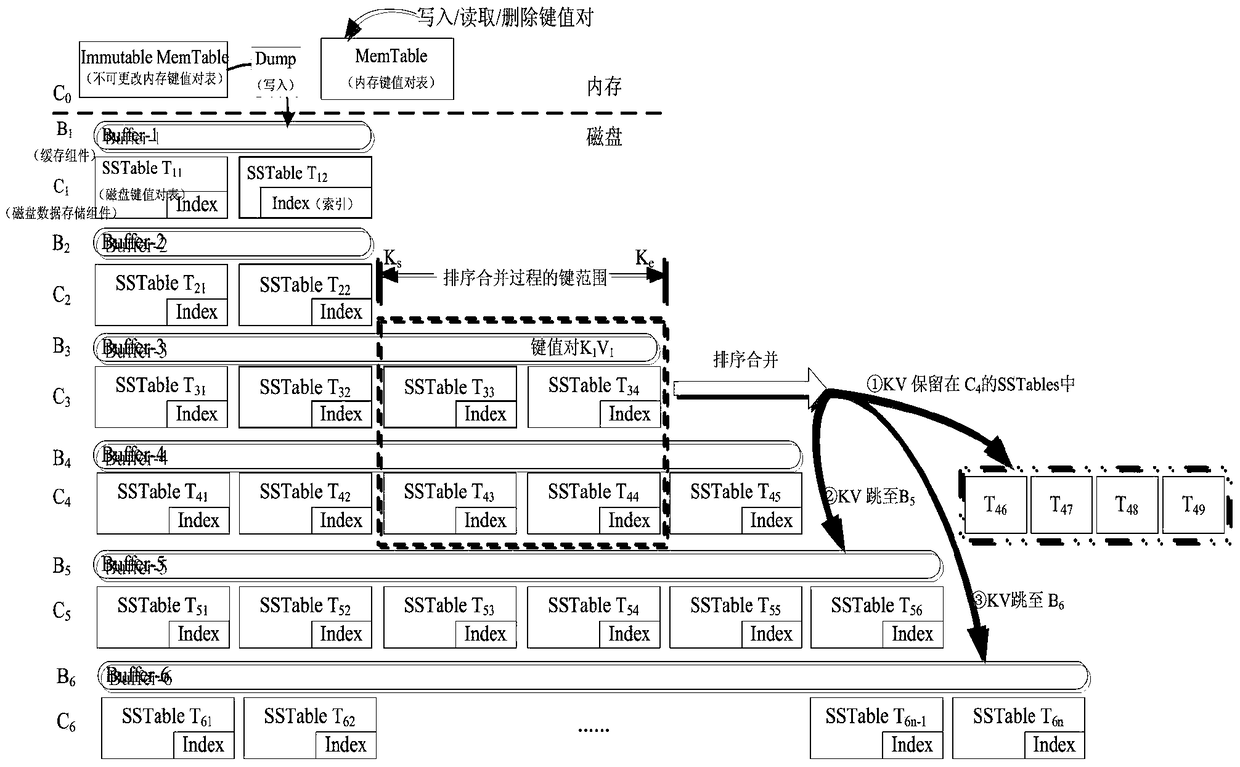
[0034] Example 1 Key-value storage system based on log structure merge tree
[0035] 1) Judging the existence of key-value pair version based on Bloom Filter (BF)
[0036] In this method, if a specific key-value pair (kv) is to be jumped down, the first thing to ensure is that the skipped data storage component does not have any version of the key-value pair corresponding to the kv.
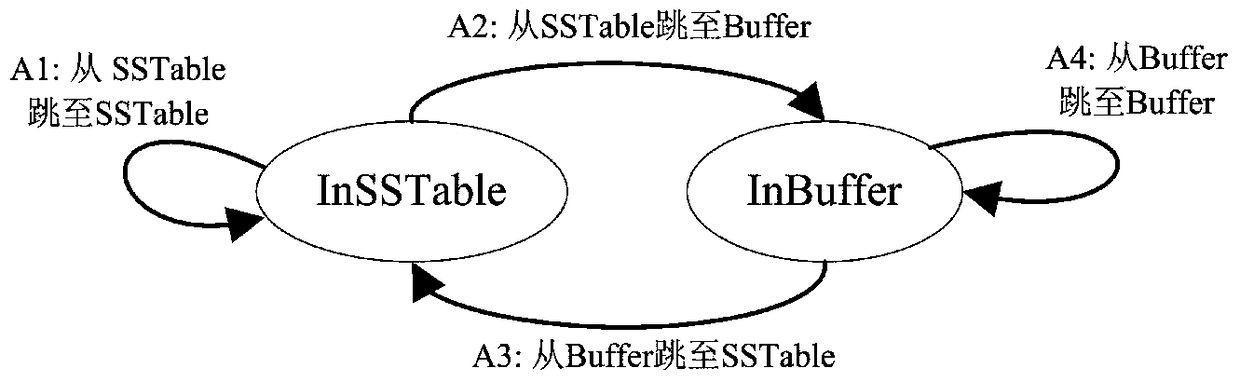
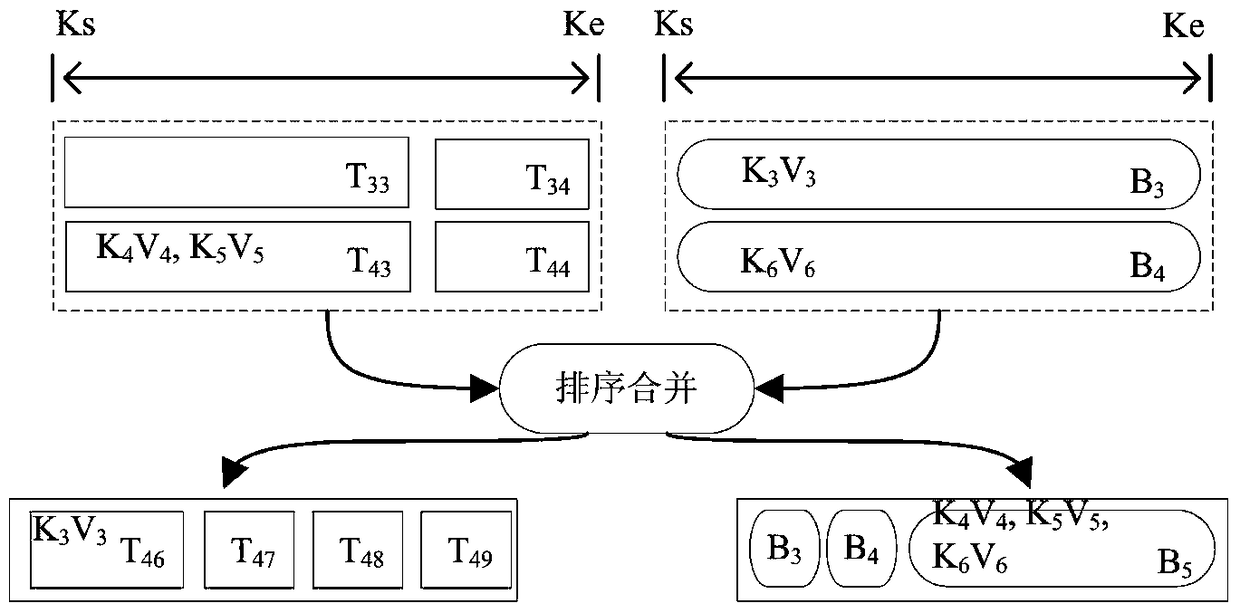
[0037] Two adjacent data storage components C i And data storage component C i+1 Take the key-value pairs after sorting and merging as an example. A typical LSM-tree-based key-value storage system places the key-value pairs in the data storage component C i+1 , This method tries to put it in the data storage component C i+M , M is greater than or equal to 1, and M is as large as possible.
[0038] This method uses a level-by-level judgment mechanism to judge whether it can jump to the data storage component C. i+M . You can skip to data storage component C i+M The condition is: data storage component C i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com