Vulnerability scanning cooperation method based on new communication protocol
A vulnerability scanning and communication protocol technology, which is applied in the field of network security, can solve problems such as inability to achieve collaborative work and fail to meet application requirements, achieving efficient collaborative work and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
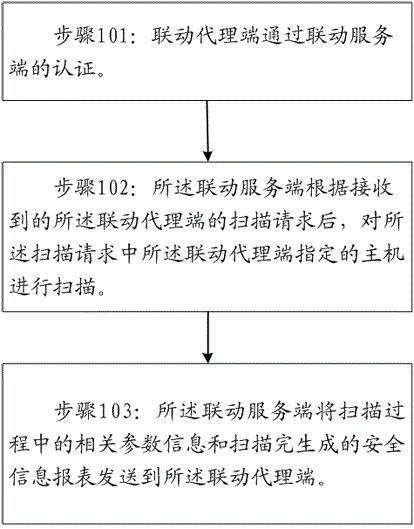
[0014] An embodiment of the present invention provides a linkage method for vulnerability scanning based on a new communication protocol, such as figure 1 As shown, the method is implemented through the following steps:
[0015] Step 101: the linkage agent passes the authentication of the linkage server.
[0016] Specifically, the linkage server uses the MD5 algorithm to encrypt the IP address of the linkage agent to generate a 32-bit hexadecimal authentication key; Initiate the verification, and the linkage server responds after receiving the verification request, and if the verification is successful, continue the subsequent process; otherwise, end the current process.
[0017] The linkage server stores the IP address of the linkage agent and the authentication key together in the sqlite database of the linkage server, and saves the authe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com