System and method for authenticating identity based on quantum key
A quantum key and identity authentication technology, applied in user identity/authority verification, transmission systems, digital transmission systems, etc., can solve the problems of inability to replicate quantum states, and cannot be accurately measured, to increase the complexity, The effect of strong anti-replay attack and improved security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
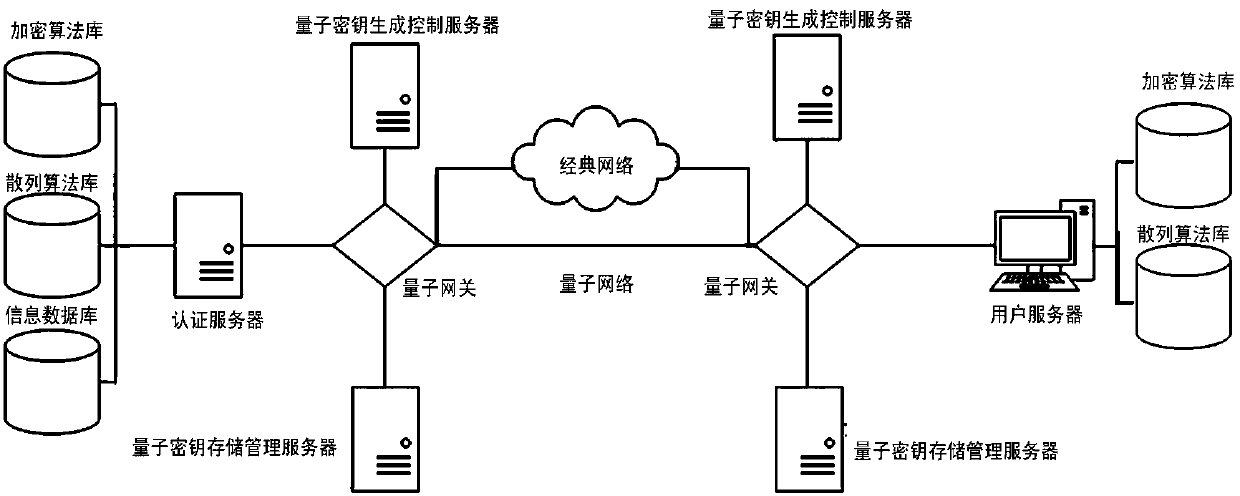
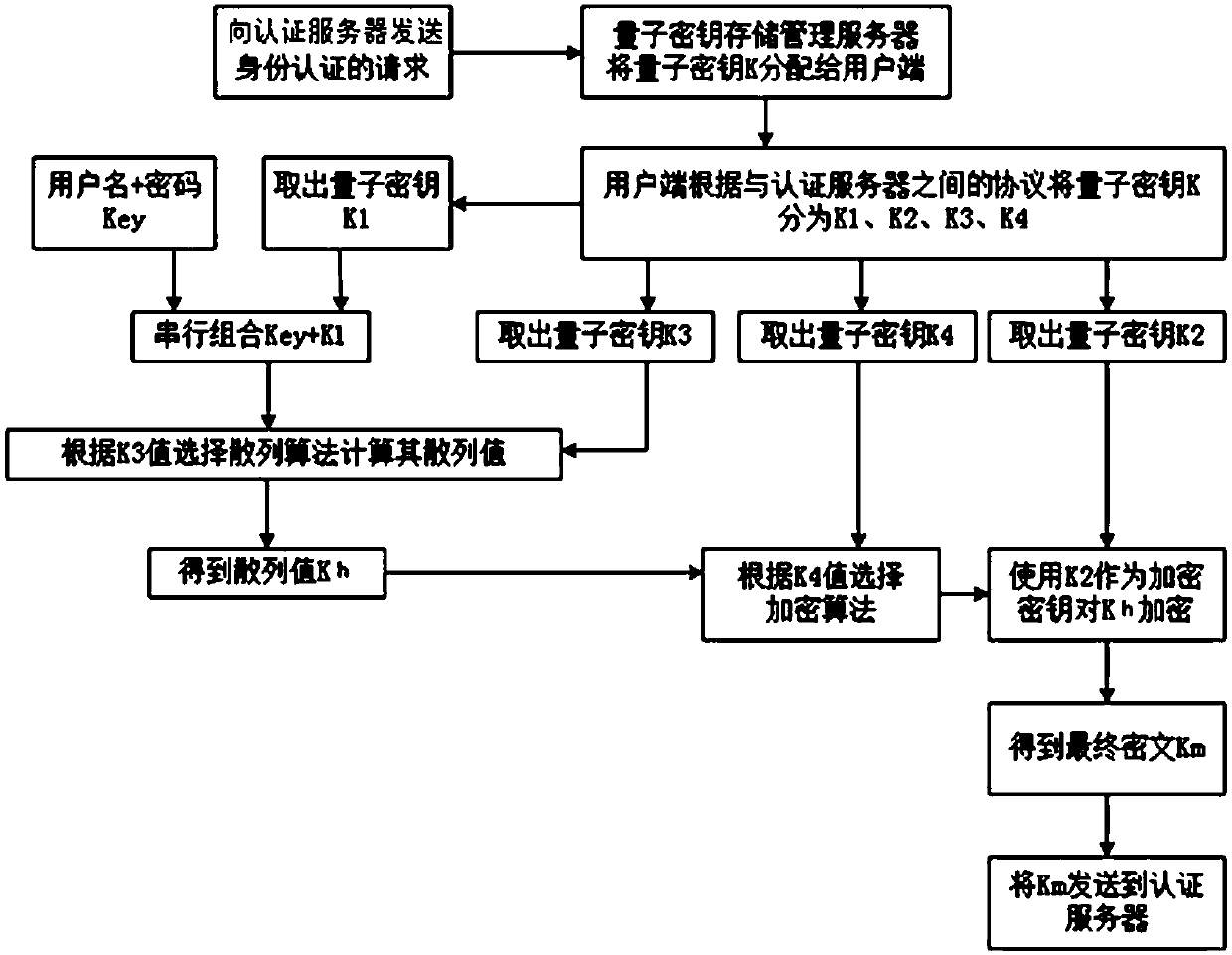
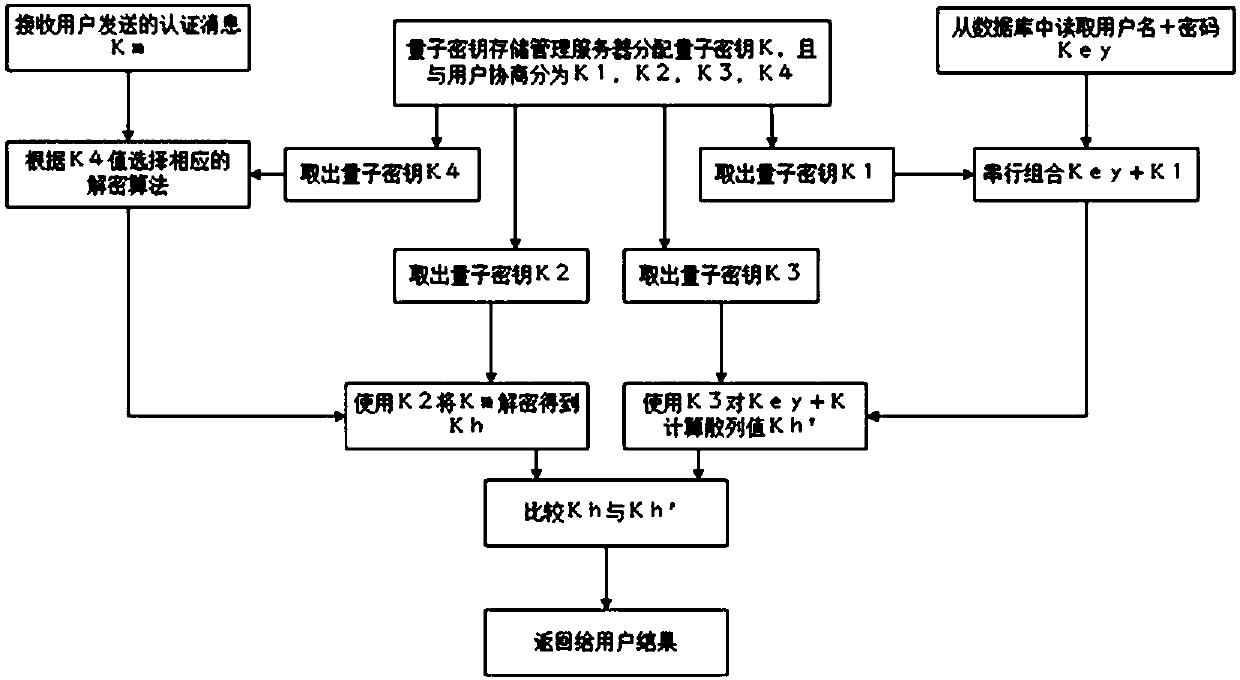
[0036] like figure 1 The present invention shown is composed of a client, an authentication server and a network connecting the two, and the client and the authentication server are connected through respective quantum gateways, and there are two channels between the quantum gateways, that is, the quantum channel and the classical Channels, quantum channels are used to distribute quantum keys, and classical channels are used to transmit classical information other than quantum keys. The client and the authentication server not only have their own quantum gateways, but also have their own quantum key generation control servers, quantum key storage management servers, encryption algorithm libraries, and hash algorithm libraries. The authentication server also has an authentication server and a user information database for storing user informati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com