Zigbee initial secret key distribution method based on RSSI covert communication
A technology of initial key and distribution method, applied in wireless communication, security devices, electrical components, etc., can solve the problems of network security threats, impossible keys, encryption, etc., and achieve the effect of network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
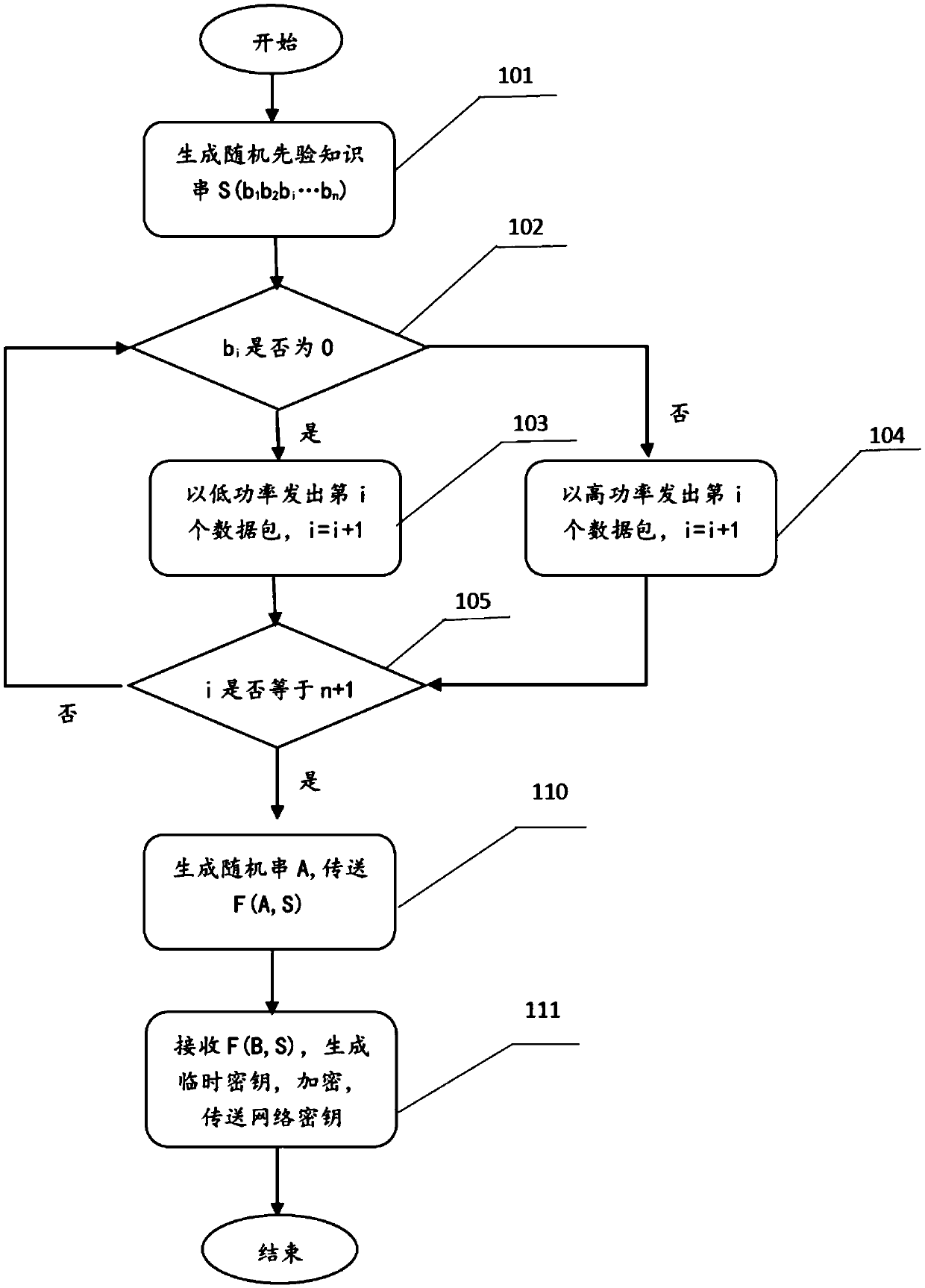
[0043] figure 2 It is the steps of the trust center node solution in a specific embodiment, and those skilled in the art should understand that the steps in this embodiment are regarded as a preferred implementation mode of the present invention, and are not understood as limiting the protection scope of the present invention, that is, The following specific steps are only as a preferred mode of the technical solution of the present invention.
[0044] Specifically, it can be achieved through the following preferred implementation method:
[0045] Step 101: The trusted node randomly generates a bit string S (b1, b2, b3, ..., bn) as prior knowledge for generating a symmetric key.
[0046] Step 102: According to the modulation rule, judge whether the i-th bit of the bit string is 0, if it is 0, execute step 103, and send a low-power data packet, otherwise execute step 104, and send a high-power data packet.
[0047] Step 103: the optional transmitting power of Zigbee terminal...
Embodiment 2
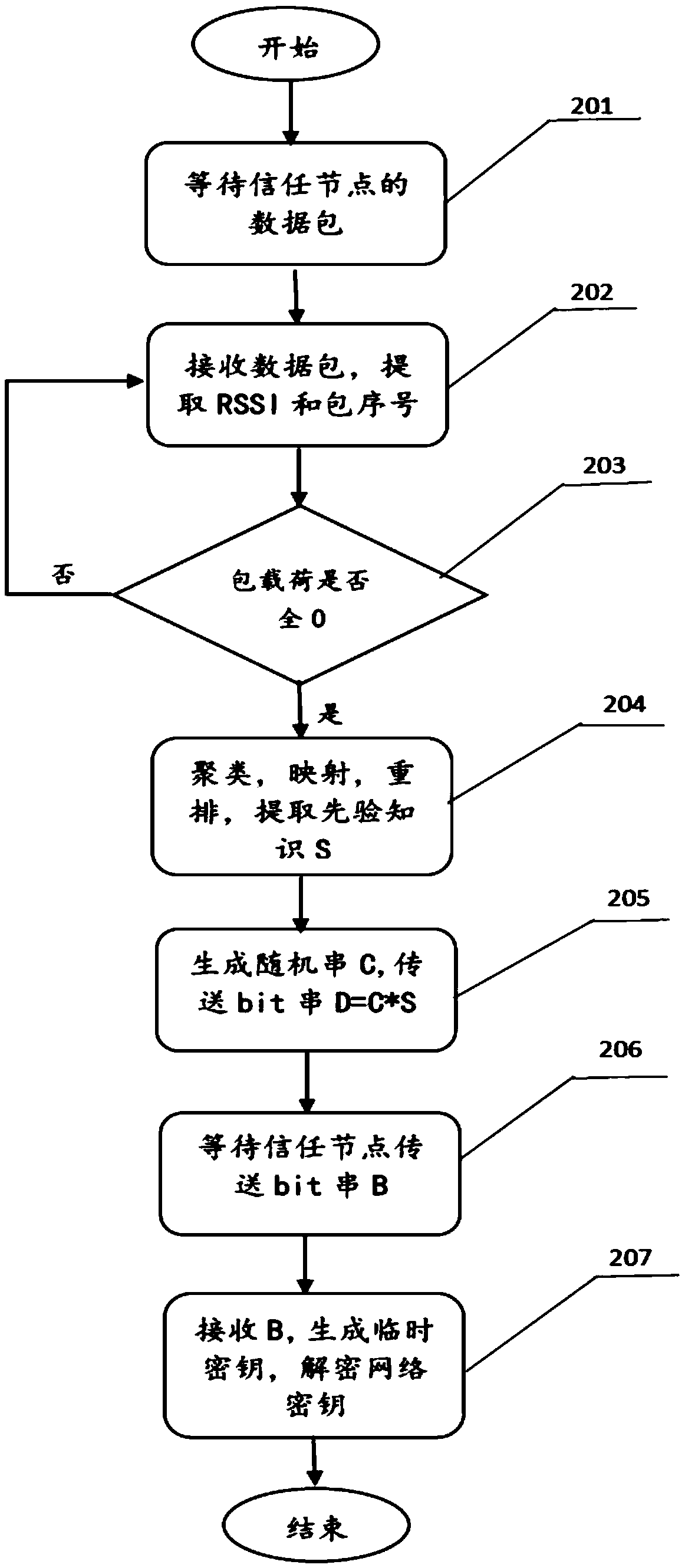
[0054] In a specific embodiment, such as image 3 As shown, when there is a newly joined node, the distribution of keys and the establishment of secure communication can be realized in the following ways:
[0055] Step 201: Waiting for the trusted node to transmit the data packet.
[0056] Step 202: when the network access node receives the data packet, record the received signal strength value (RSSI) and the sequence of each data packet, and the arrival sequence of the i data packet is i, so that a data packet is recorded for each data packet Two-tuple (S, I), S represents the signal reception strength of the packet, and I is the arrival sequence of the packet.
[0057] Step 203: When the data payload of the received packet is all 0, it means that the peer end has completed the data transmission in secret, go to step 203, otherwise go to step 201.
[0058] Step 204: After the network access node receives all n packets from the trusted node, the network access node obtains a...
Embodiment 3
[0063] In order to further describe the technical solution of the present invention in detail, the method steps of the present invention are described below with a specific example of communication steps:
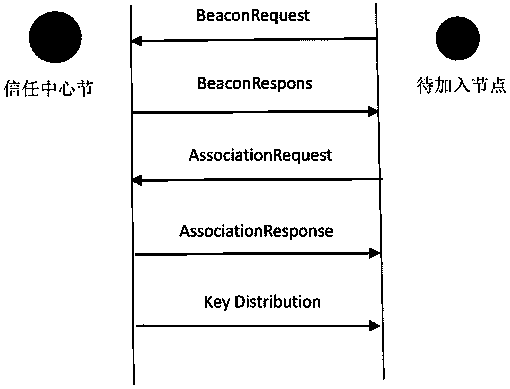
[0064] After the trust center node authenticates the node to be joined and allows it to join the network, the initial key distribution is about to start, which is the method described in the present invention.
[0065] 1) The trust center node randomly generates a 13-bit bit string 0100110010111 as public prior knowledge.
[0066] 2) The trusted node modulates the above 13-bit prior knowledge through RSSI strength, and modulates the 13-bit string into 13 data packets. The trusted node transmits 13 data packets to the network access node to covertly transmit the prior knowledge of 0100110010111. The data in the packet can be arbitrary without any practical meaning. The modulation rule is: bit0 is modulated with low RSSI, and bit1 is modulated with high RSSI. For example, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com