GF (27) finite field and dual authentication-based meaningful (K, N) image sharing and reconstructing method
A dual-authentication, finite-field technology, applied in image data processing, graphics and image conversion, instruments, etc., can solve problems such as bunker image authentication without embedded sharing information, unrecognizable bunkers, and affecting repair capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0111] The present invention is described below in conjunction with specific embodiment:
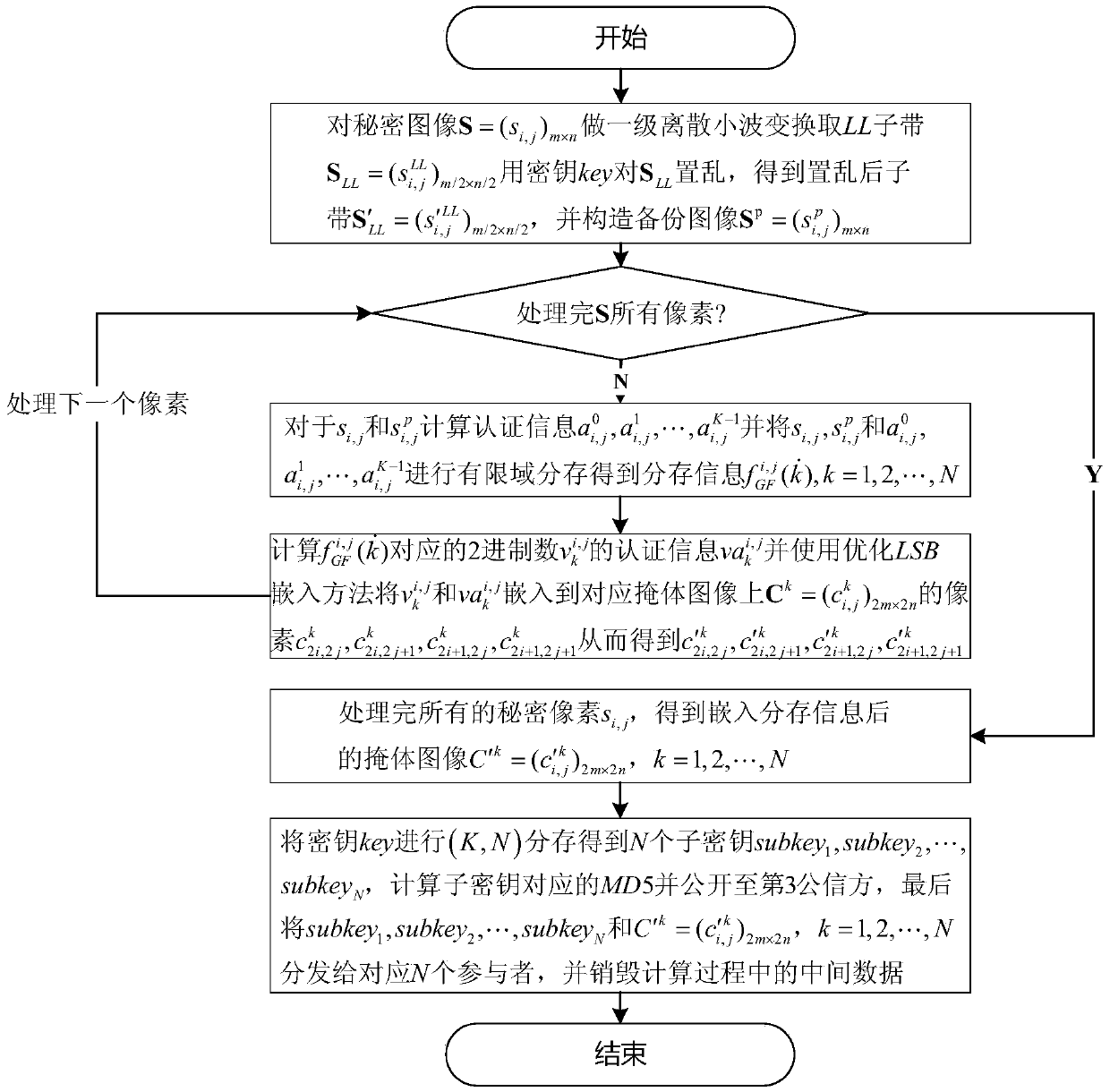
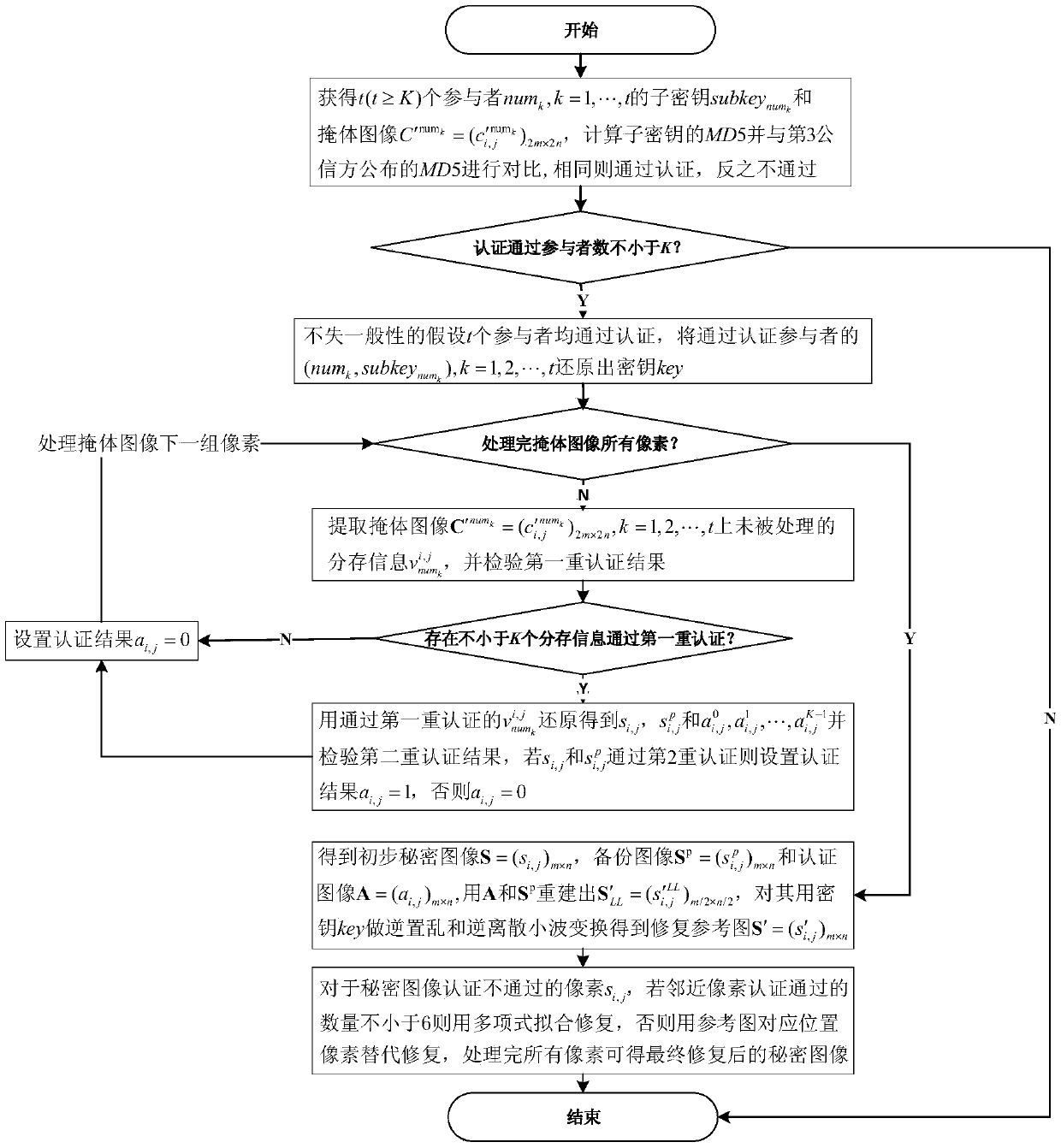
[0112] Taking JAVAjdk1.8.0_20 as the case implementation environment, taking the (3,5) threshold scheme as an example, that is, K=3, N=5, the implementation of the present invention will be described in detail in conjunction with the accompanying drawings, but not limited to this implementation case, where figure 1 It is the flow chart of sharing storage, figure 2 Is the reconstruction flow chart.
[0113] The following is a specific example to illustrate the sharing process:
[0114] Select the 8-bit standard grayscale image boat of 256×256 as the secret image, such as image 3As shown in , the 8-bit standard grayscale images of 512×512, baboon, f16, sailboat, lena and peppers were selected as the mask images of the five participants, as Figure 4 ~ Figure 8 As shown, the selected key is key=131819, K=3, N=5.
[0115] Step 1: Right image 3 Secret image S=(s i,j ) 256×256 Do a d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com