Method and system for hotspot module instruction tracking
A module instruction and hotspot technology, applied in the fields of instrumentation, electrical digital data processing, computing, etc., can solve the problem that the debugger cannot trace the full instruction of the memory page, cannot handle the execution of the system instruction, and the performance overhead of single-step tracing is high, so as to avoid Incompleteness and complexity issues, avoiding inefficiencies, ensuring completeness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
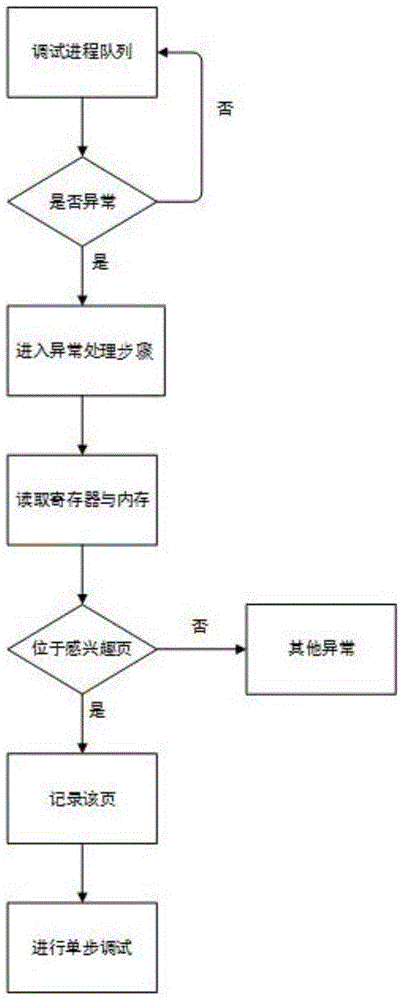
[0027] A method for hot module instruction tracking, comprising the following steps:
[0028] Debug loop steps: After a process becomes the debugged process, it will send a notification to the debugger when it completes certain operations or an exception occurs, and then suspends itself until the debugger commands it to continue execution;
[0029] Exception handling steps: Through the distribution of exceptions, different exception events are processed. Exception handling separates receiving and processing error codes. It is a mechanism in programming languages or computer hardware to handle exceptions that occur in software or information systems. conditions (that is, some special conditions beyond the normal execution flow of the program);
[0030] Read registers and memory steps: Threads have a context, which contains most of the information about the thread, such as the address of the thread stack, the address of the instruction that the thread is currently executing, a...
Embodiment 2
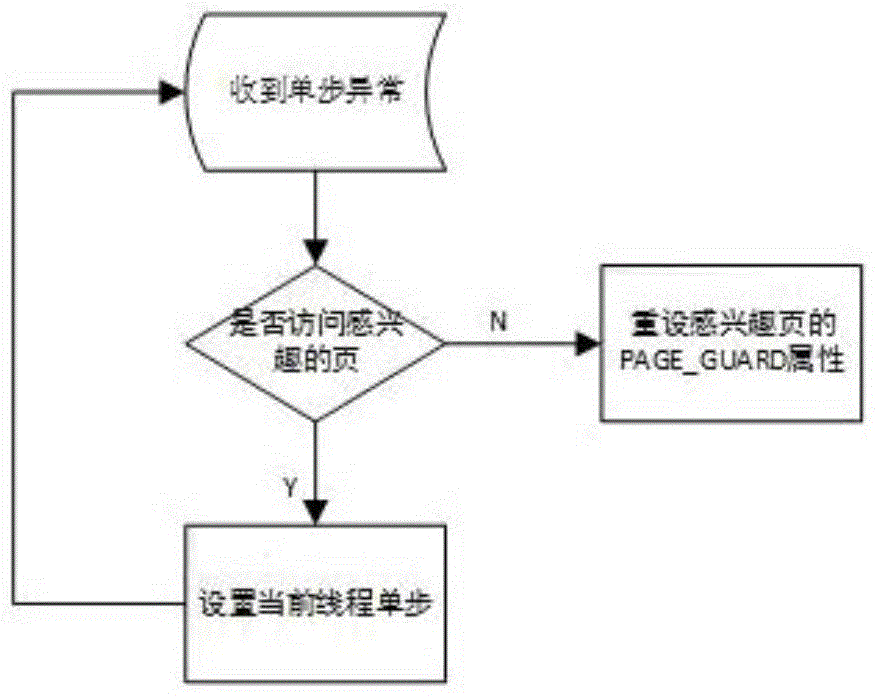
[0035] A method for tracking instructions for hot modules. After single-step debugging, the PAGE_GUARD attribute of the hot module will be lost, and the page number of the missing PAGE_GUARD attribute will be added to a linked list. When the thread of single-step debugging is judged not to access the hot module , will re-add the PAGE_GUARD attribute of the hotspot module according to the linked list, and directly execute this thread in a non-single-step manner; this method mainly includes the following steps:
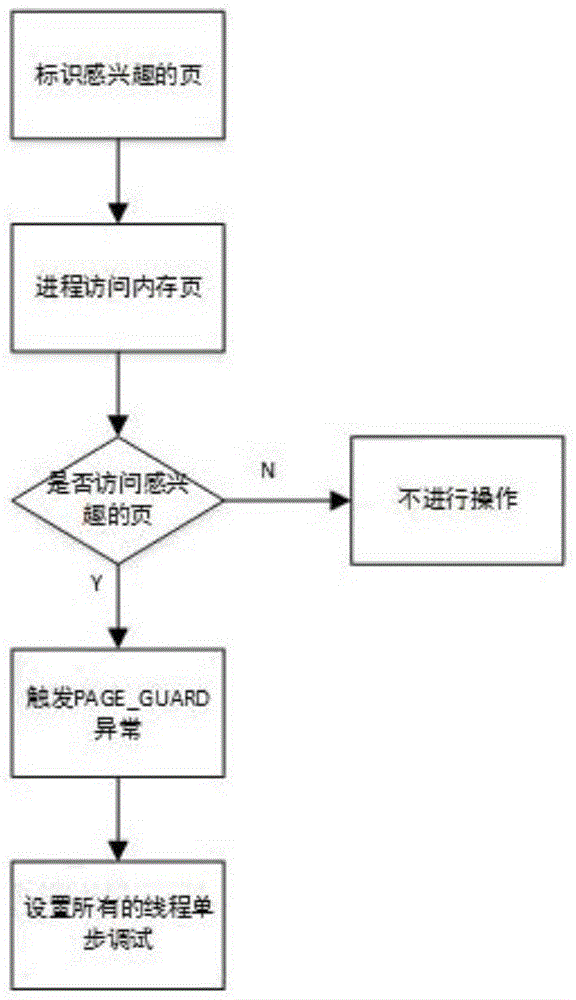
[0036] S1: Identify the pages of interest: set the PAGE_GUARD attribute for the code page where the hotspot module is located, and identify the PAGE_GUARD attribute of these pages;
[0037]S2: Process access memory page: The debugged process accesses the memory page at runtime, because the interested page has been set with the PAGE_GUARD attribute, once the thread accesses the memory page marked as interested, an exception will be triggered, and the main program will Su...
Embodiment 3
[0042] For Windows 7 system of Microsoft Corporation
[0043] The debugger developed based on hotspot module tracking will be debugged under Windows7 system. Use visualstdio2013 to compile and run the project.
[0044] The debugger project can specify an exe execution file, and select a memory page that may be maliciously attacked as the PAGE_GUARD attribute, and then the debugger generates a process, which is designated as the debugged process. Once the debugged process reads the hotspot module Writing will trigger a PAGE_GUARD exception. The debugged process will trigger many exceptions in its life cycle. According to the debugger process receiving the exception event sent by the debugged process and handling the exception, a debugging process is completed. Table 1 lists the debugger Exception events that may be triggered.
[0045] Table 1 Abnormalities that may be triggered by this implementation
[0046]
[0047]
[0048]
[0049] 1. Debugging events and debug...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com