A kind of Internet of things communication encryption method and device
A communication encryption and Internet of Things technology, applied in the field of Internet of Things communication encryption methods and devices, to reduce the risk of information leakage, reduce the possibility of loss, and increase the difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
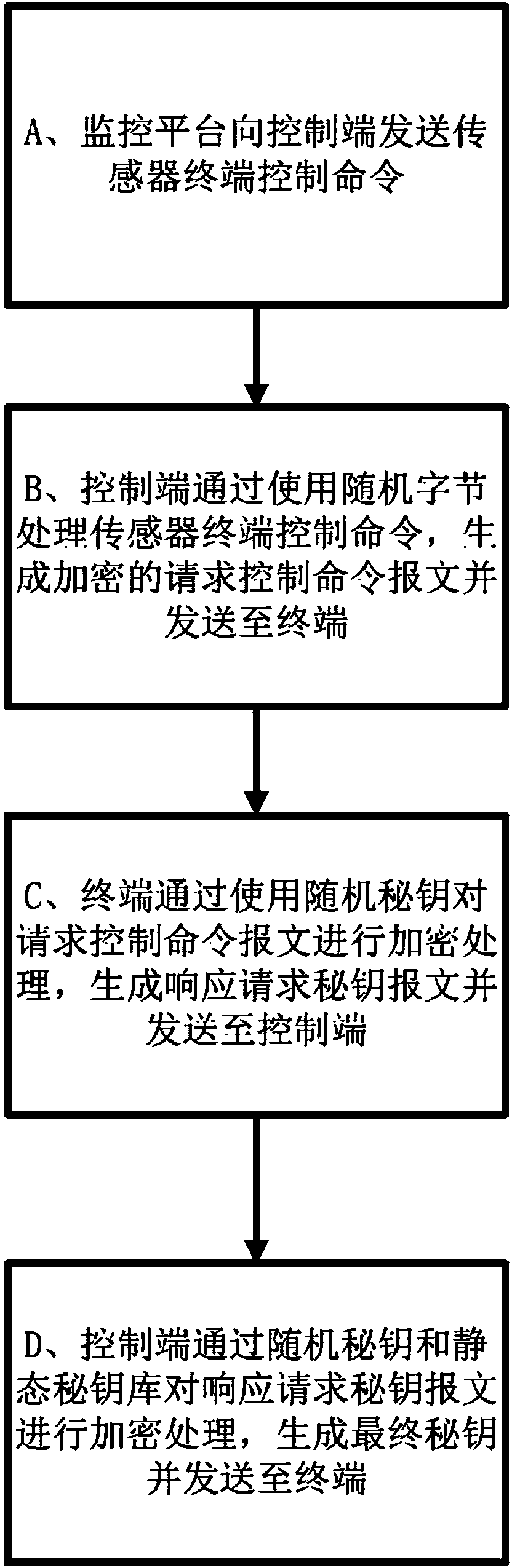
[0021] Example 1, such as figure 1 A flow chart of a communication encryption method for the Internet of Things is shown, including the following steps: A. The monitoring platform sends a sensor terminal control command to the control terminal, and the message of the command includes a frame header, a frame length, a message identification byte, and a destination terminal ID, specific control command and frame tail; B. The control terminal processes the sensor terminal control command by using random bytes, generates an encrypted request control command message and sends it to the terminal; C. The terminal uses a random secret key to request the control command message The text is encrypted, and the response request key message is generated and sent to the control terminal; D. The control terminal encrypts the response request key message through the random key and the static key storehouse, generates the final key and sends it to the terminal .
[0022] The monitoring platfo...
Embodiment 2
[0041] Example 2, such as Figure 4 As shown, a schematic flow diagram of a communication encryption method combined with an Internet of Things device.
[0042] Among them, the IoT monitoring platform is actually what we call the human-computer interaction part; the IoT control terminal is the part that sends control information; the IoT terminal is the part that controls the actual arrival of information and executes commands; the control terminal receives The processing process of the initial command sent from the platform is also the initial part of this encryption algorithm.
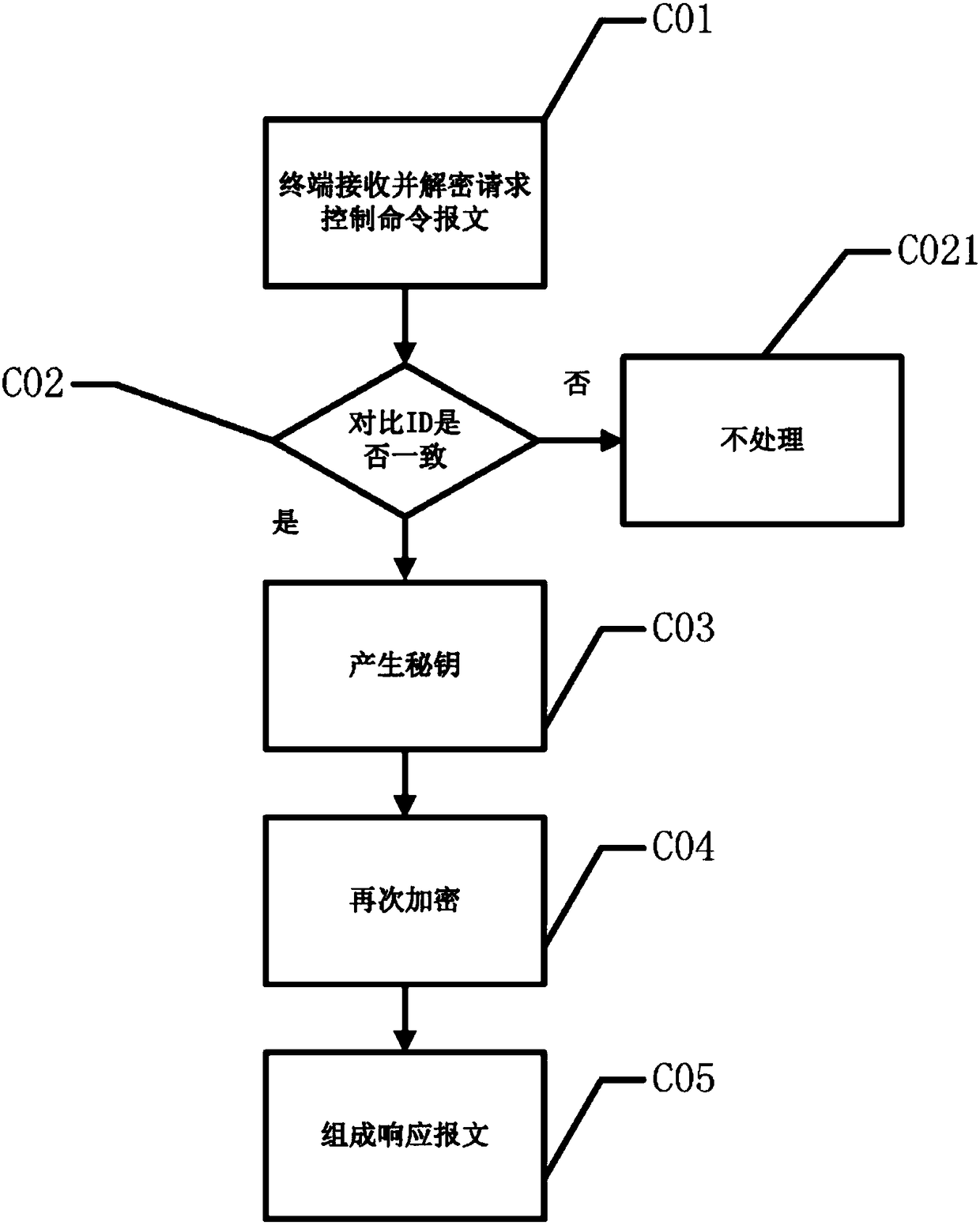
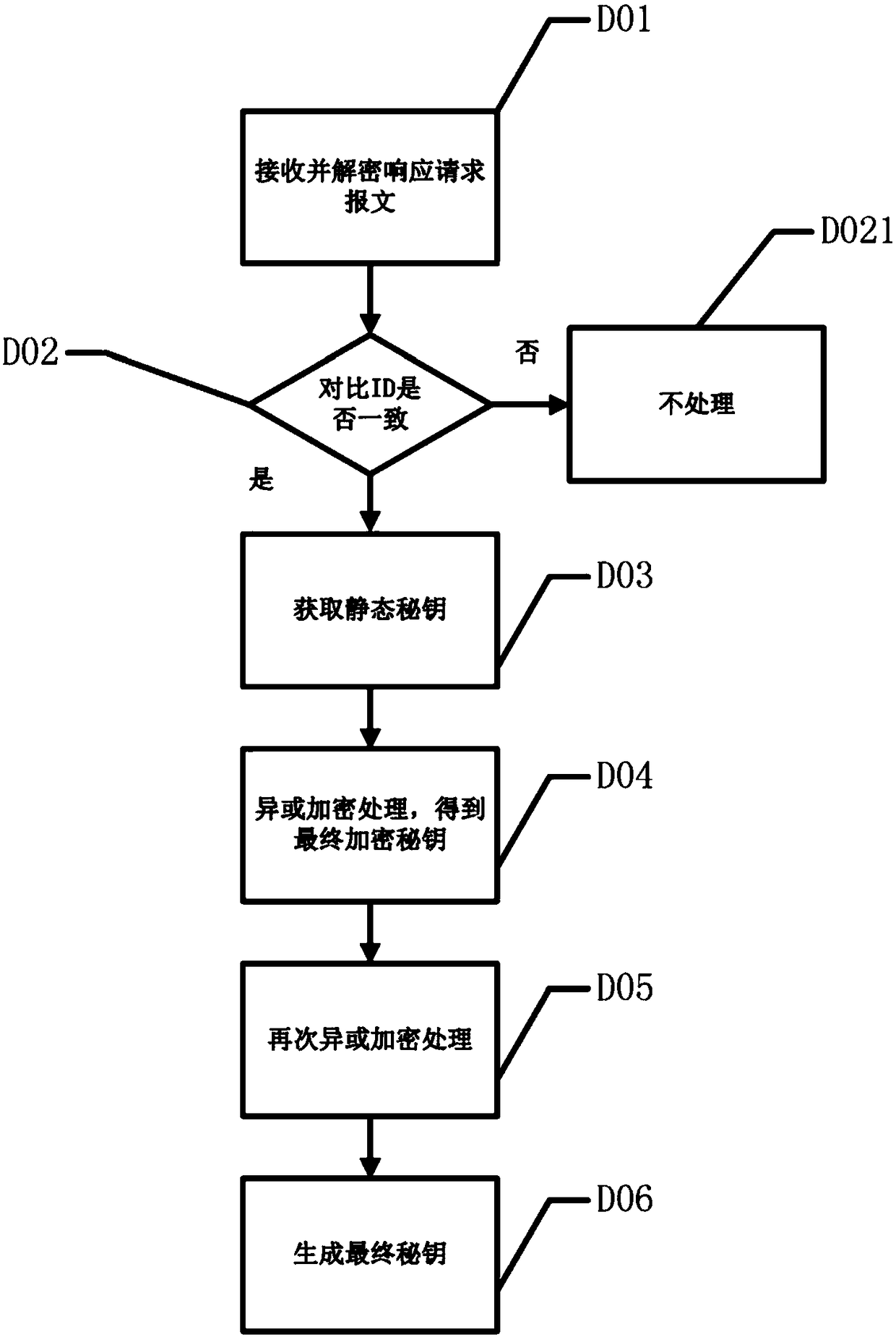
[0043] Step 1, the terminal receives the request control command; Step 2, the terminal processes the request control command; Step 3, the terminal generates a random secret key and generates a request command response message; Step 4, the terminal encrypts the response message; Step 5, the control terminal Receive and process the response message; step 6, the control terminal obtains the terminal ra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com