Identity card cloud authentication system and card reading system
An ID card and card reading terminal technology, applied in the electronic field, can solve the problems of uneven task distribution, overloading, stealing and even tampering, etc., to ensure security, improve security, and avoid illegal attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
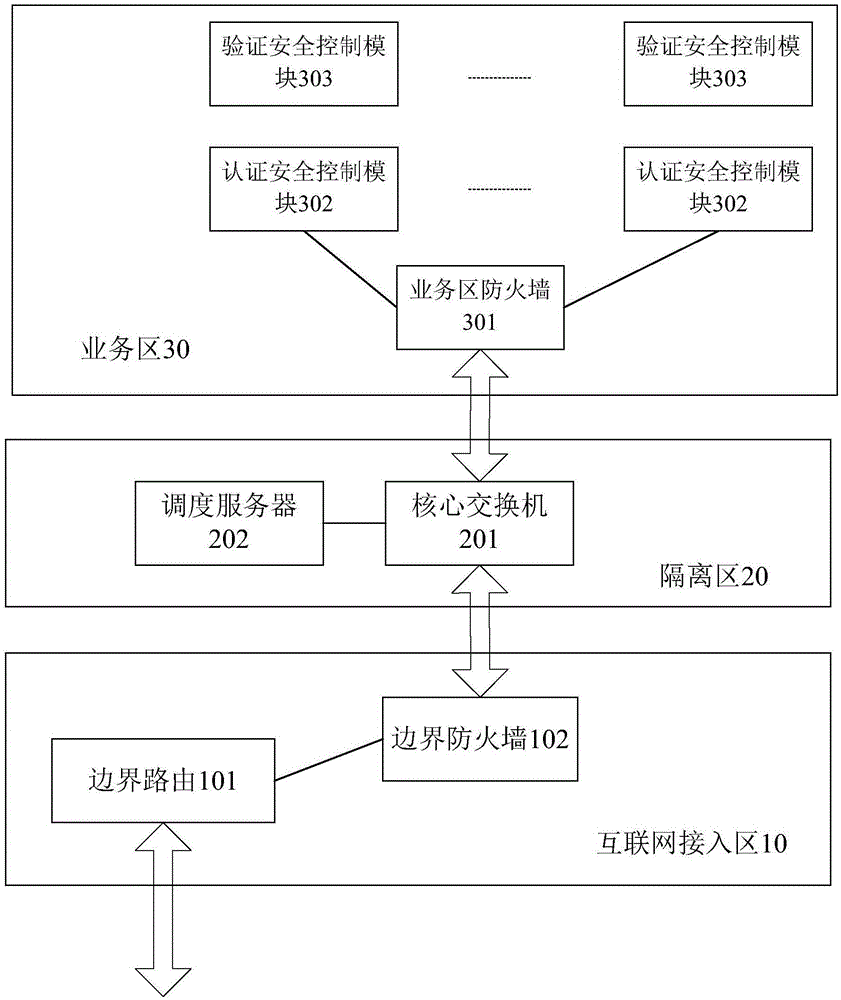
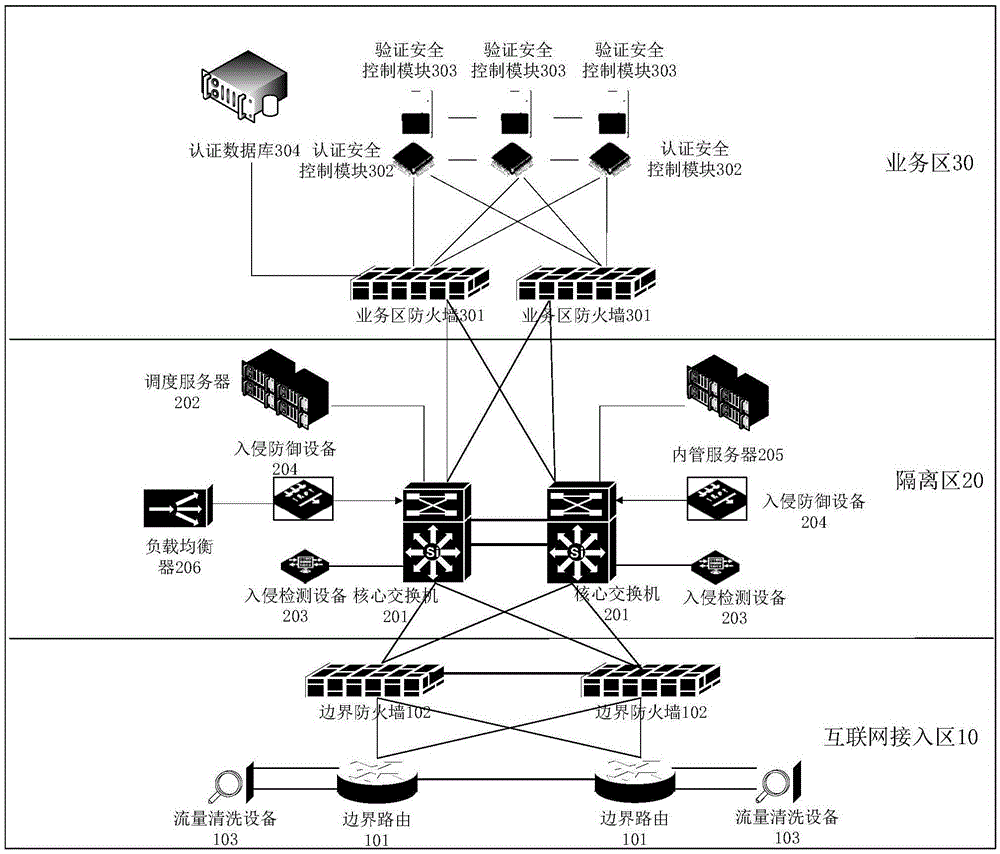
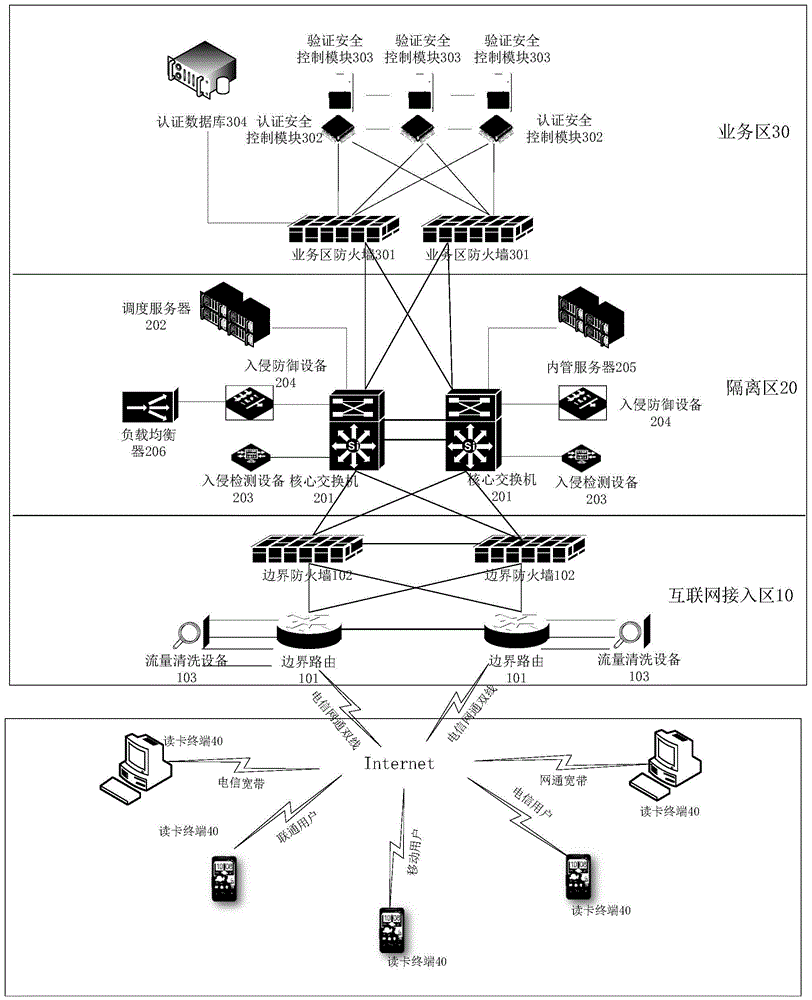
[0039] This embodiment provides an ID card cloud authentication system. Such as figure 1 As shown, the ID card cloud authentication system provided by this embodiment can include three areas according to different functional areas: Internet access area 10, isolation area 20 and business area 30, and different technical measures are taken for each area to obtain from The network level improves the security of the entire system; wherein, the Internet access area 10 is positioned as the Internet entrance of the entire ID card cloud authentication system, and the Internet access area 10 includes at least: a border route 101 and a border firewall 102 . This Internet access area 10 is in an open network environment, and its main function is to be responsible for Internet access, to resist illegal access through border routing and border firewalls, and to be the first line of defense from the Internet into the intranet; the isolated area 20 is to solve the problem of installing a fir...
Embodiment 2
[0082] This embodiment provides a method for data transmission, and the method can use the system provided in Embodiment 1. Such as Figure 4 As shown, the method includes the following steps S101-S110:
[0083] S101: The border router receives the data packet sent by the card reader terminal, selects the border firewall to be sent according to the path selection strategy, and sends the data packet to the selected border firewall;
[0084] In this embodiment, in order to prevent a single point of failure, multiple border firewalls can be deployed. When there are multiple border firewalls, the border router needs to select a path to send the data packet to the core switch, that is, choose which border firewall to send to The core switch, in this embodiment, the border router selects the border firewall to be sent according to the path selection strategy. A border firewall with strong business processing capabilities, etc.
[0085] In this embodiment, the data packet sent by ...
Embodiment 3
[0134] This embodiment provides an internal management server, such as Figure 5 As shown, the internal management server may be a centralized server for centralized management, or a distributed server for integrating network resources. The internal management server includes: a security access unit, a display unit, a first input interface, a security processor, a main control processor, a system management unit, a parameter configuration unit and a second input interface.
[0135] The security access unit is configured to detect a user request, and when it is detected that the user request is a user login request, obtain prompt information corresponding to the user login request, and send the prompt information to the display unit.
[0136] Specifically, the security access unit refreshes or detects whether a user request is received regularly or irregularly, and when a user request is received, judges the type of the user request, and judges whether it is a user login reques...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com