Secure electronic payment method based on four parties
An electronic payment and four-way technology, applied in the payment system, payment system structure, logistics, etc., can solve problems such as repeated identity authentication, low algorithm efficiency, and inability to guarantee the atomicity of commodities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
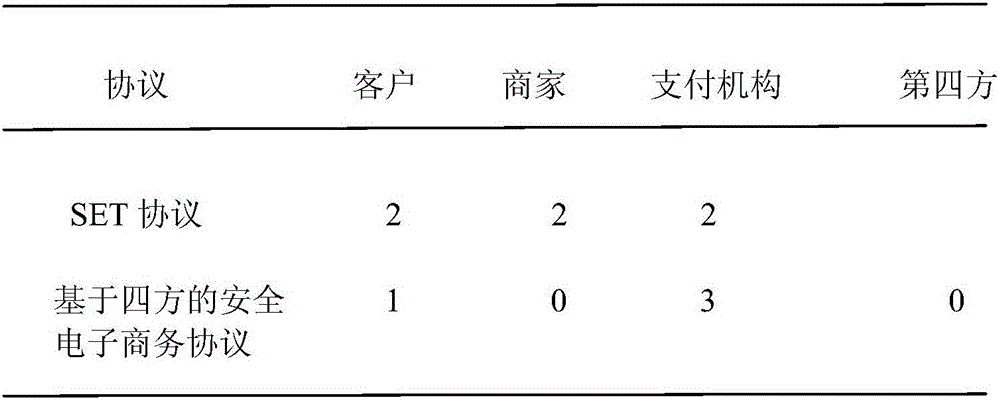
[0010] Firstly, the meaning of the symbols used in the protocol is given, as shown in Table 2.
[0011] Table 2 Description of protocol symbols
[0012]
[0013]
[0014] ① Payment Agreement Master Agreement Description
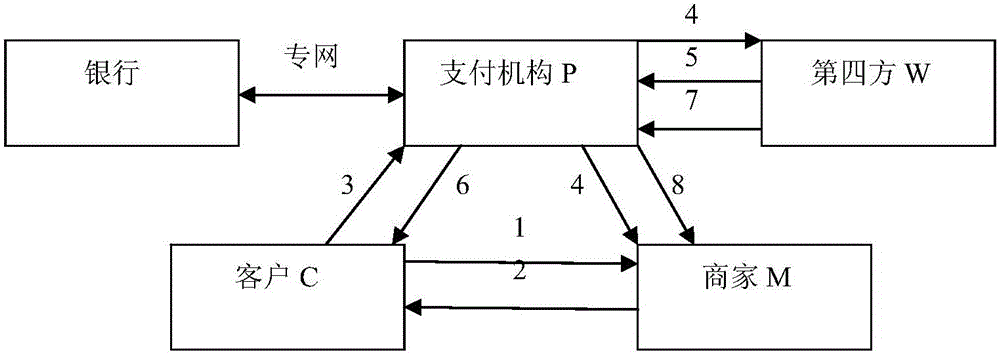
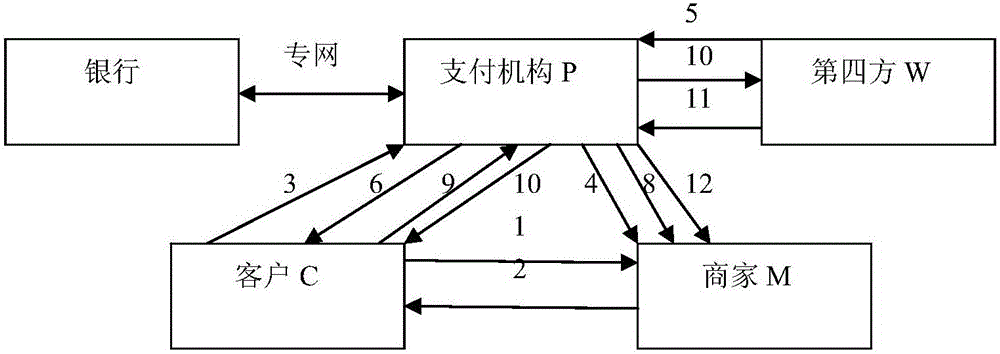
[0015] In this agreement, the participants are customer C, merchant M, payment institution P and the fourth party W. The main agreement process of the payment agreement is as follows: figure 1 shown. The detailed process of numbering in the figure is as follows:
[0016] (1) C→M: {(OI′||CerC)}[OI′=D IVC (OI)]
[0017] Customer C browses the products sold by merchant M, agrees to the quotation, and digitally signs the order OI: OI′=D RKC (OI). Merge OI' and client certificate message: OI'||CerC, and send the merged message to merchant M.
[0018] (2) M→C: {Y}[E PKC (OI')=OI, OI"=D RKM (OI'),OI"=D PKW (OI″),
[0019] y=D SKM (Num||CerP||CerM||CerW||Pay||OI″′)
[0020] Merchant M decrypts after receiving OI': E PKC (OI')=OI, confirm that the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com