Two-dimensional code-based intelligent security chip signature information transmission method and system
A technology of security chip and signature information, applied in the field of authentication, can solve the problem of difficult data communication between smart cards and background systems, and achieve the effects of reducing user burden, strong usability, and high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053]In order to describe the technical content of the present invention more clearly, further description will be given below in conjunction with specific embodiments.
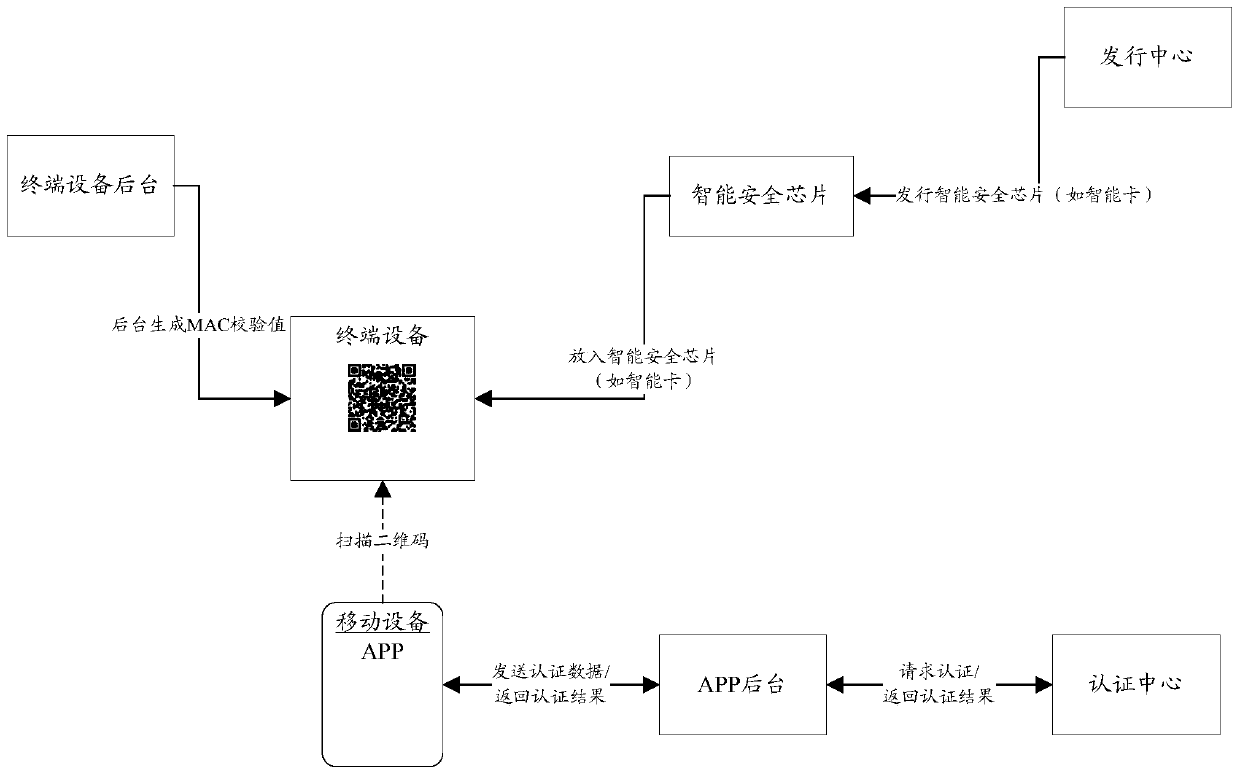
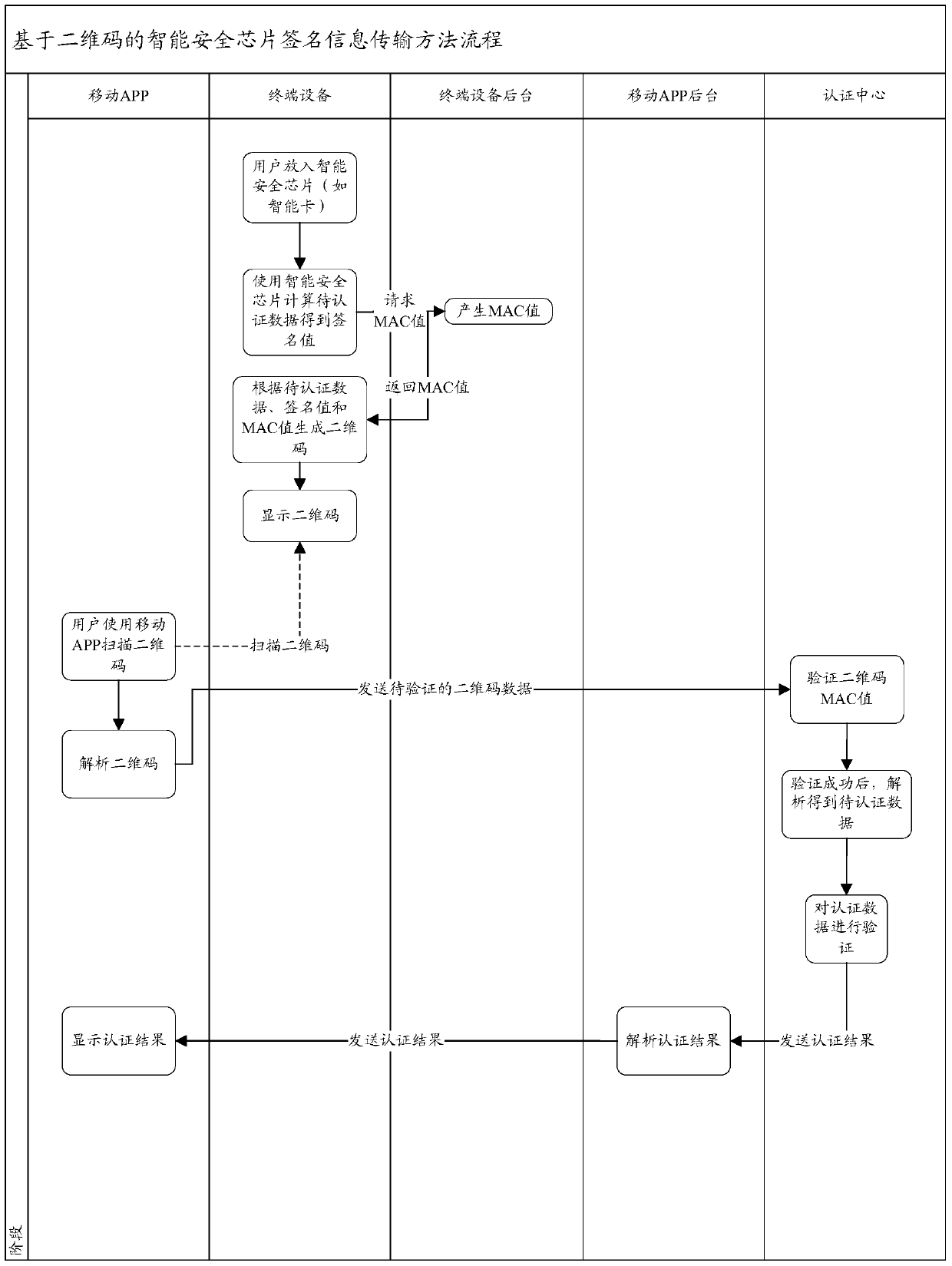
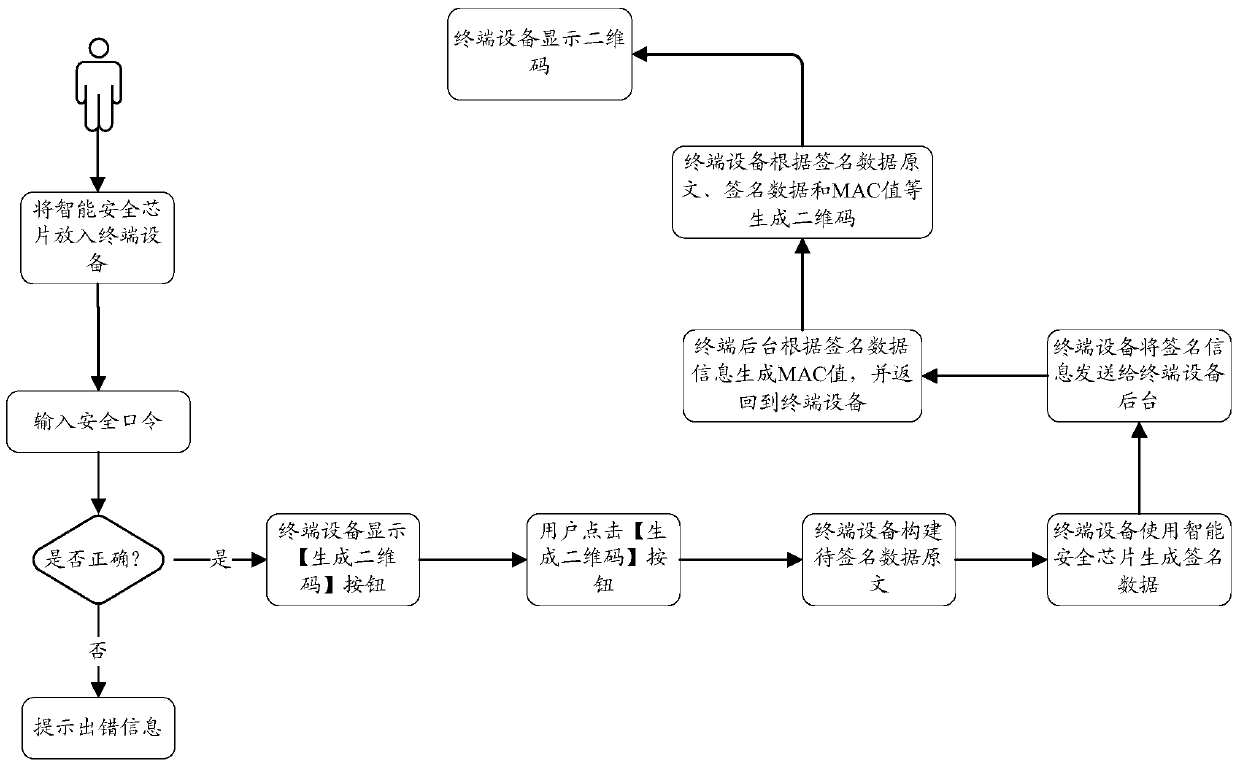
[0054] The purpose of the present invention is to provide a two-dimensional code authentication method based on an intelligent security chip and a cryptographic algorithm, so as to realize the security authentication function of the user login platform, so as to achieve the purpose of security login. At the same time, solve the problems existing in the current application mode, such as users need to write down the account password information under different platforms, if the mobile terminal is attacked by viruses and Trojan horses, and the communication between mobile terminal devices (especially iPhone devices) and smart cards requires an external card reader etc., and can safely log in to the platform system to complete a series of subsequent interactive operations. At present, there is no relevant soluti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com