Method and system for accessing to network by user under web authentication
A technology for accessing the network and users, applied in the field of communication, it can solve the problem of unable to intercept network packets, and achieve the effect of high interception rate and high safety factor
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
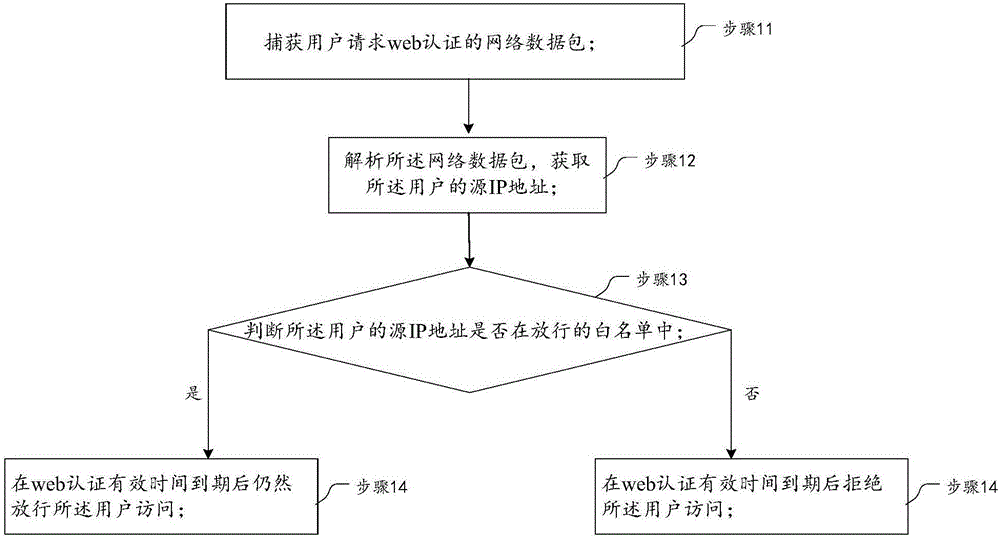
[0036] This embodiment provides a processing flow of a method for a user to access the network under web authentication. figure 1 As shown, it is based on the network driver interface specification NDIS to write the driver, which specifically includes the following steps:
[0037] Step 11. Capture the network data packet requested by the user for web authentication;
[0038] In this embodiment, the following sentences are used to realize network data packet capture. Specifically,
[0039] string strUrl="NCSI_TEXT_URL, strResponse="";
[0040] httpclient-> Get(strUrl,strResponse);
[0041] Step 12. Parse the network data packet to obtain the source IP address of the user;
[0042] CURLcode res;
[0043] CURL*curl=curl_easy_init();
[0044] if(NULL==curl)
[0045] {
[0046] return CURLE_FAILED_INIT;
[0047] }
[0048] curl_easy_setopt(curl,CURLOPT_URL,strUrl.c_str());
[0049] curl_easy_setopt(curl,CURLOPT_CONNECTTIMEOUT,3);
[0050] curl_easy_setopt(curl,CURLOPT_TIMEOUT,3);
[0051] res=curl_eas...
Embodiment 2
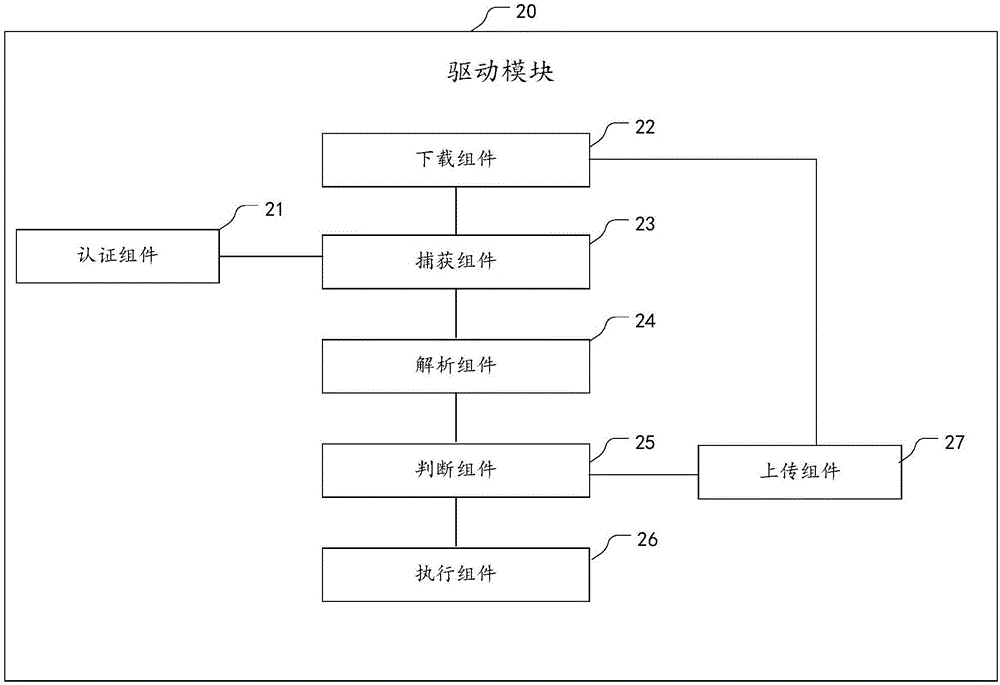
[0074] This embodiment provides a system for users to access the network under web authentication, and its specific implementation structure is as follows figure 2 As shown, it includes: a driver module 20, which runs a driver program written based on the network driver interface specification NDIS, and the driver module includes:
[0075] Capture component 23: it is used to capture network data packets for which the user requests web authentication;
[0076] Parsing component 24: it is used to parse the network data packet to obtain the source IP address of the user;
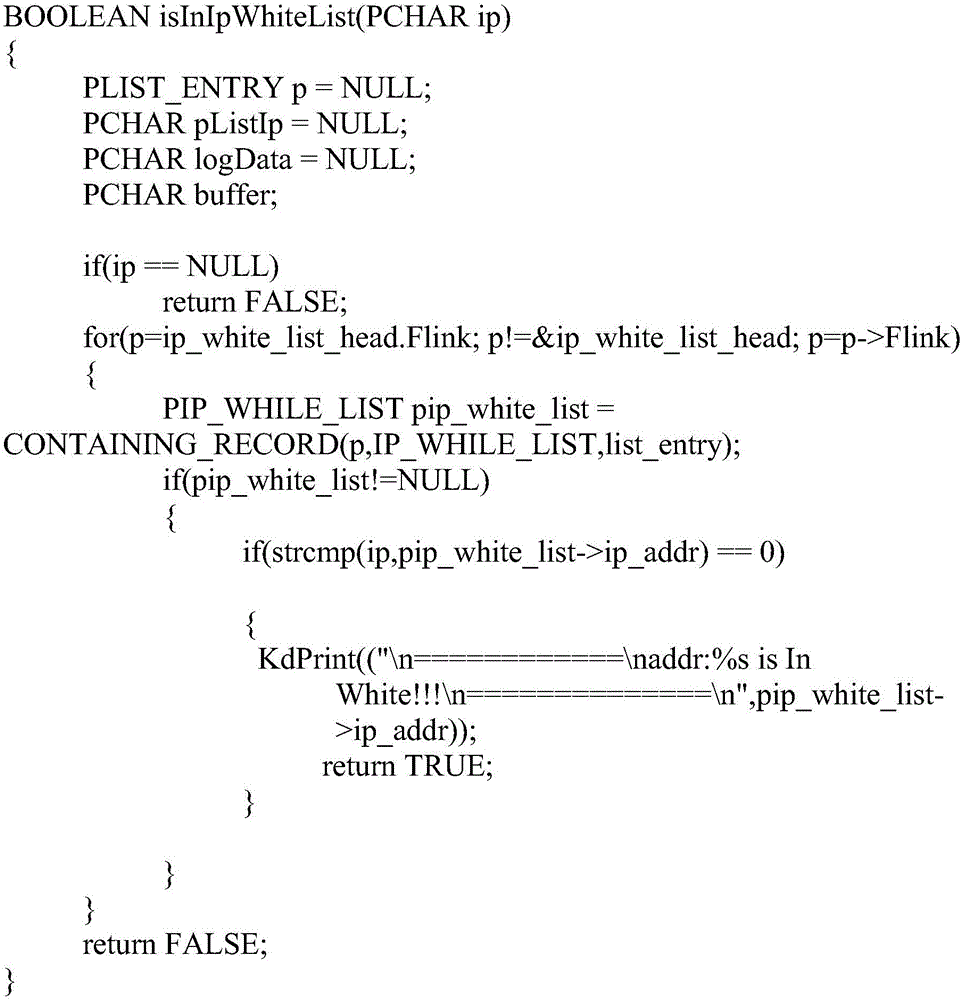
[0077] Judging component 25: it is used to determine whether the source IP address of the user is in the whitelist for release;
[0078] Execution component 26: when the source IP address in the data packet is in the whitelist for release, the user is still released for access after the web authentication valid time expires,
[0079] When the source IP address in the data packet is not in the whitelist for release, the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com