Single interaction authenticated key agreement protocol of identity-based cryptosystem
A technology of key negotiation and mutual authentication, applied in the field of single-interactive authentication key agreement protocol, which can solve the problems of inability to calculate session keys, occupying system-related resources, etc. The effect of high safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The present invention will be further described below in conjunction with the accompanying drawings and specific preferred embodiments, but the protection scope of the present invention is not limited thereby.
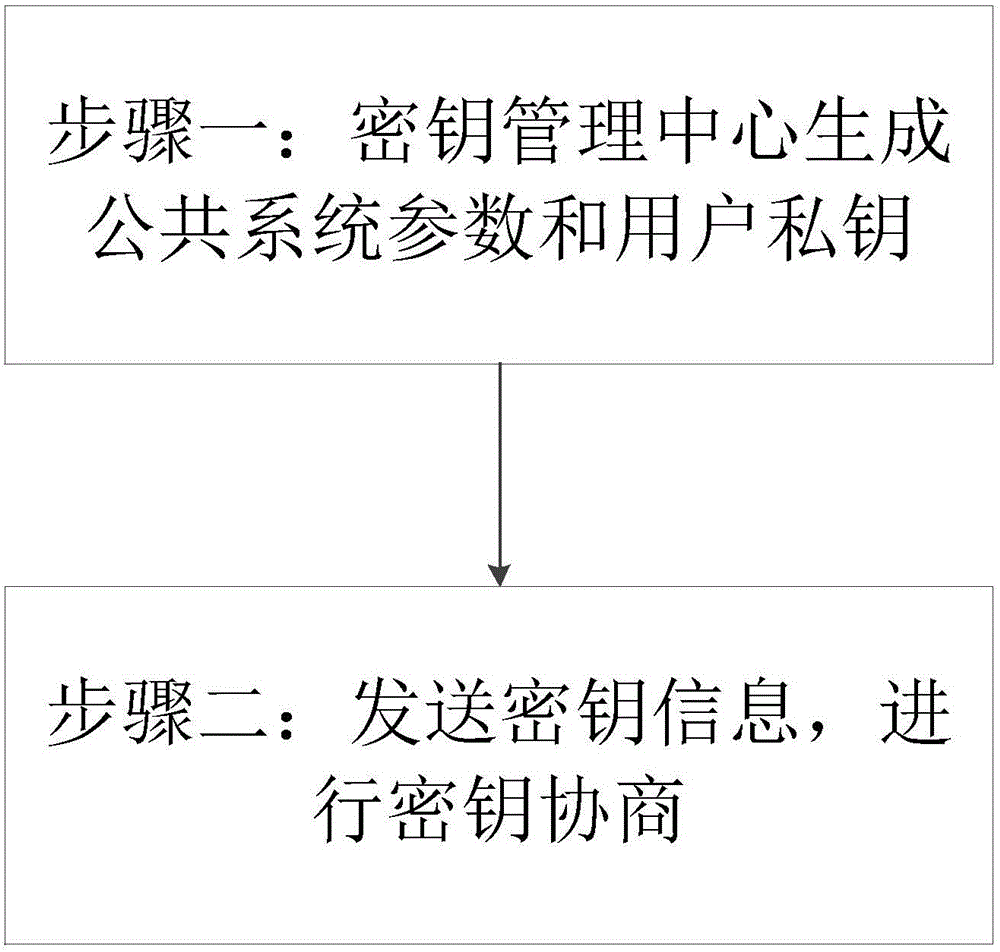
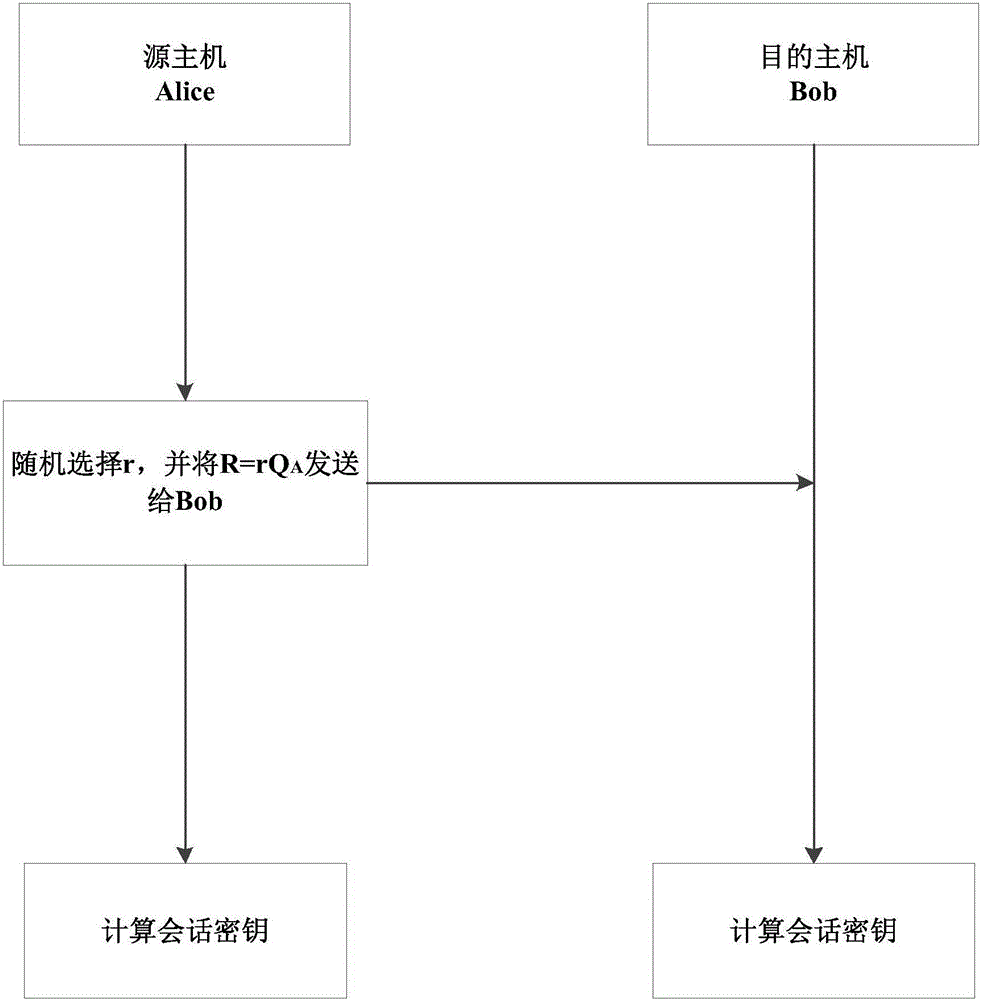
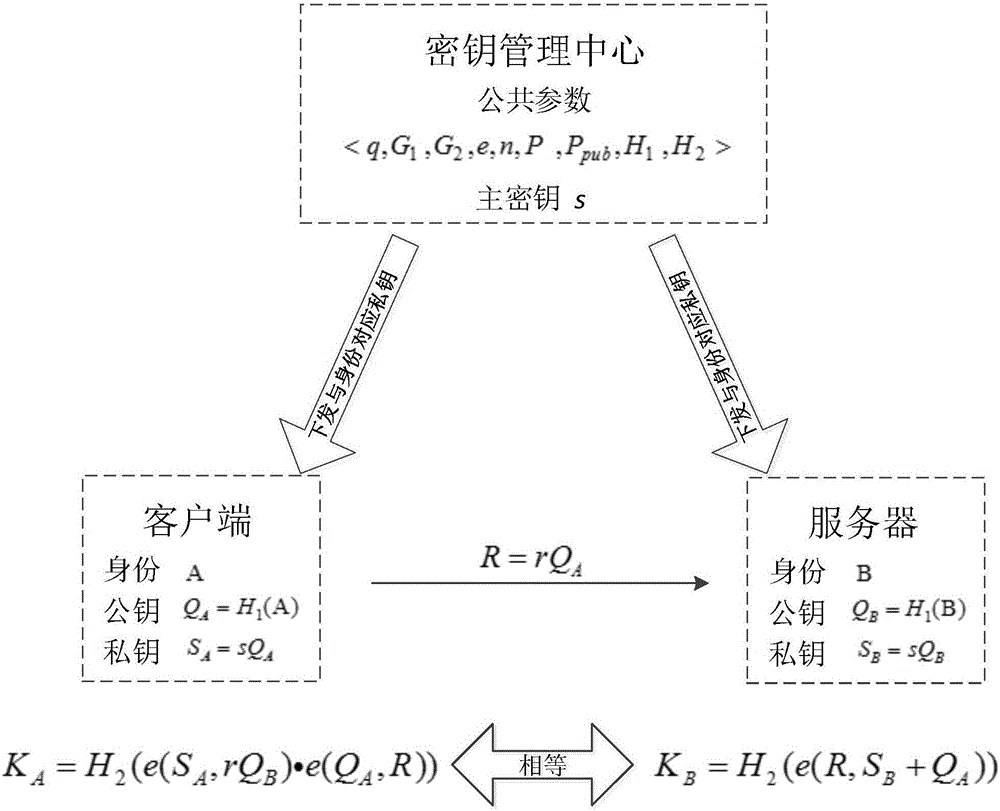
[0034] In order to improve the efficiency of key agreement and reduce the number of interactions, the present invention proposes a single-interaction authentication key agreement protocol based on an identity cryptosystem; the main technical principles involved are:
[0035] ○Bilinear mapping properties:
[0036] Let q be a large prime number, G 1 is the additive group of order q, G 2 is the q factorial group, mapping e:G 1 ×G 1 →G 2 is a bilinear map, then for any Q,R∈G1 ,a,b∈Z, there is e(aQ,bR)=e(Q,R) ab .
[0037] ○Security properties of the key agreement protocol proposed by Blake-Wilson et al. in "Key agreement protocols and their security analysis":
[0038] ① Known session key security. Known old session keys do not affect other session key secur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com