Method and system for realizing resource encrypted access
A resource and ciphertext technology, applied in transmission systems, electrical components, etc., can solve problems such as failure to receive user access requests in a timely manner, low business processing capabilities of business servers, affecting user experience and access quality, and achieve business processing Reduced capacity, reduced risk of leakage, effect of ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
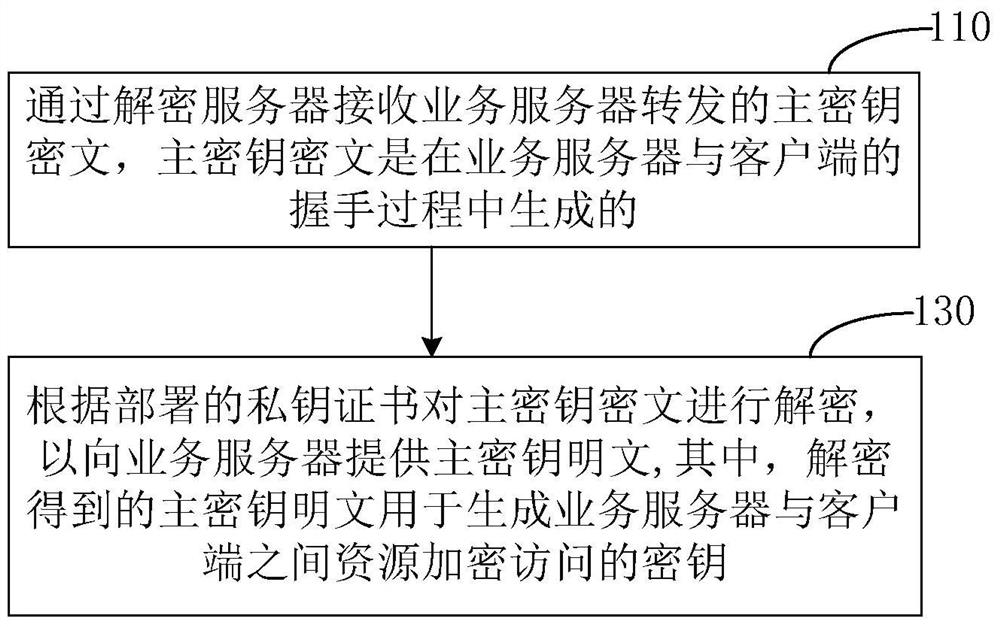
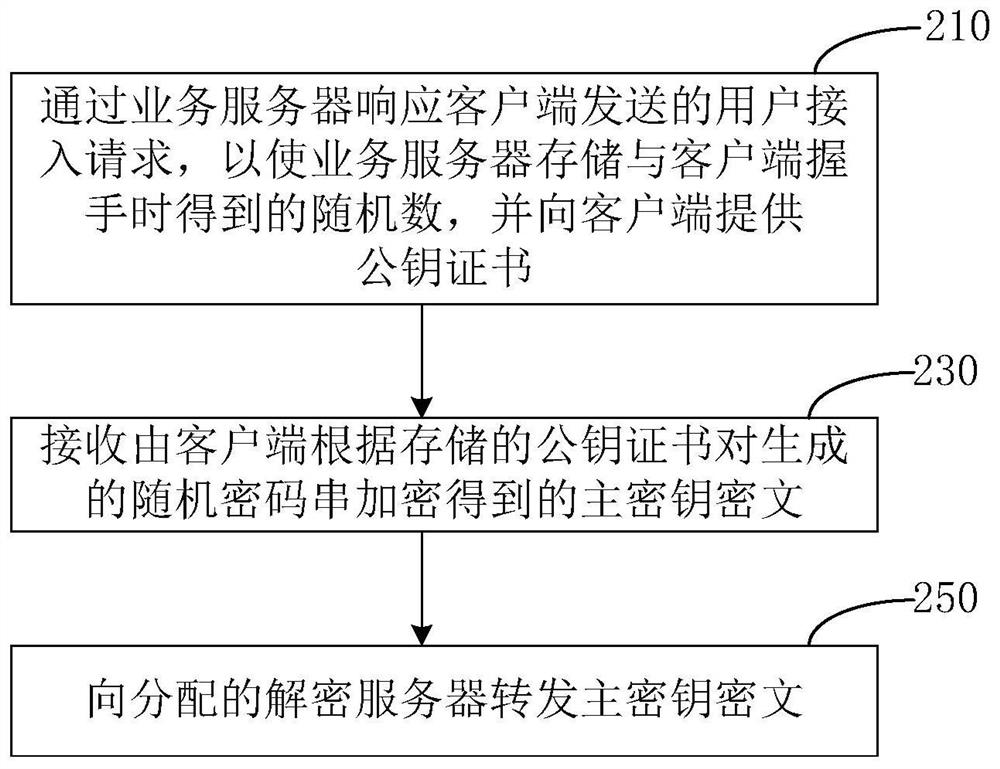
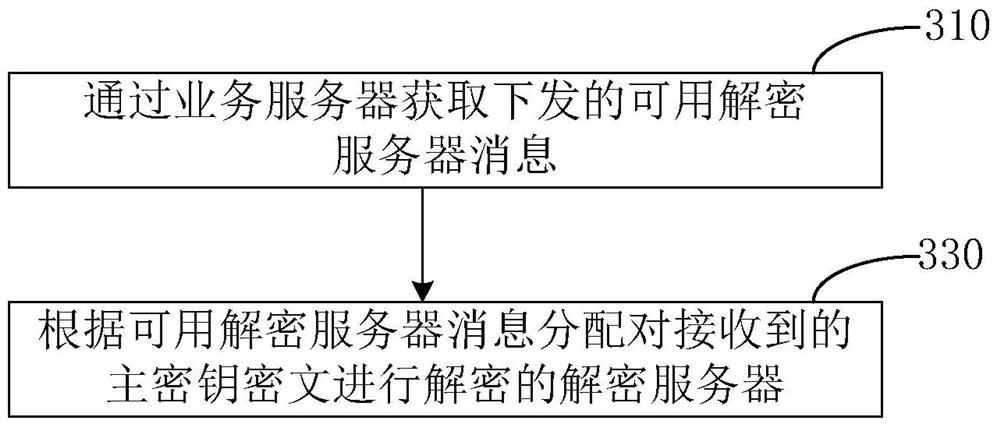
[0032] Typical embodiments that embody the features and advantages of the present invention will be described in detail in the following description. It should be understood that the present invention is capable of various changes in different embodiments without departing from the scope of the present invention, and that the description and illustrations therein are illustrative in nature and not limiting. this invention.
[0033] As mentioned above, the existing security access to resources in the business server is implemented based on the SSL protocol. With the cooperation of the SSL protocol, resource access through the HTTP protocol will first establish a connection between the client and the business server. The secure links between them provide security guarantees for subsequent resource access.
[0034] However, there is still a defect in this secure link, that is, for the business server, the establishment of a secure link with the client needs to consume more CPU r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com