Dynamic symbol execution visualization method for vulnerability mining
A technology of dynamic symbolic execution and symbolic execution, which is applied in the fields of instruments, platform integrity maintenance, and electrical digital data processing. It can solve problems such as low traversal efficiency and inability to dynamically present symbols, so as to improve teaching experience and improve understanding. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0033] Most symbolic execution tools support writing third-party plug-ins, and open internal interfaces for plug-ins to use. The calling algorithm for this visualization will be implemented in the plug-in code. The algorithm in the plug-in can obtain the type of code currently being executed by the symbolic execution tool, detect whether it is a branch statement, and call the visualization tool for visualization once detected.
[0034] The specific execution process of symbolic execution visualization is as follows:
[0035] Start the vulnerability digger and symbolic execution visualizer
[0036] Symbolic execution visualizer waiting to be invoked
[0037] The vulnerability mining tool executes to the branch point
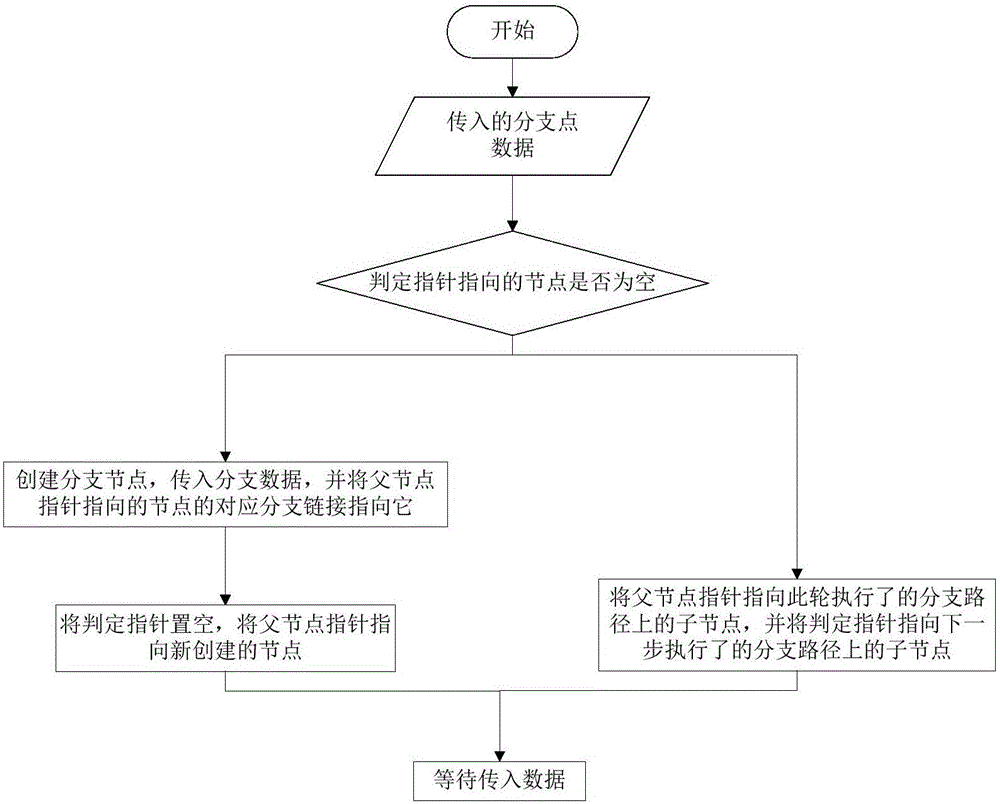
[0038] The vulnerability mining tool invokes the symbolic execution tree drawing module of the symbolic execution visualization tool to construct a branch node, and passes in branch information (branch position, branch condition, true and false value of the bra...
Embodiment 2
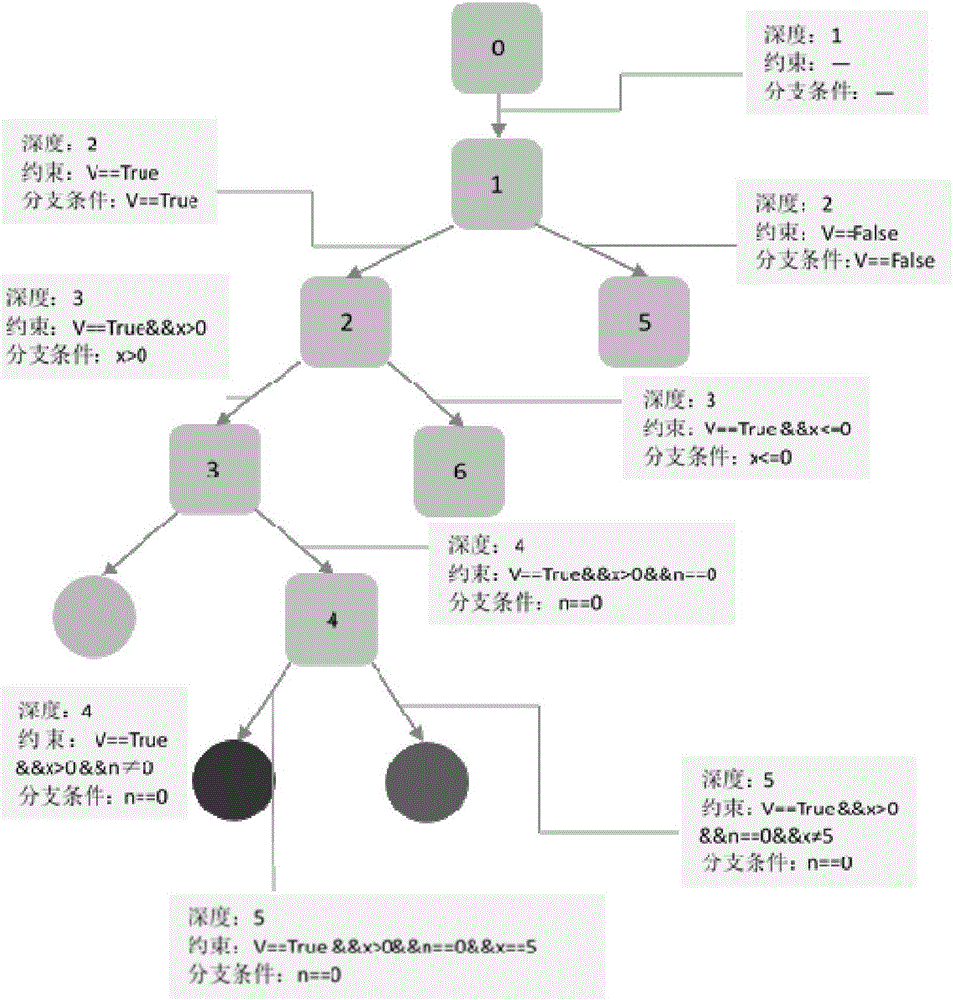
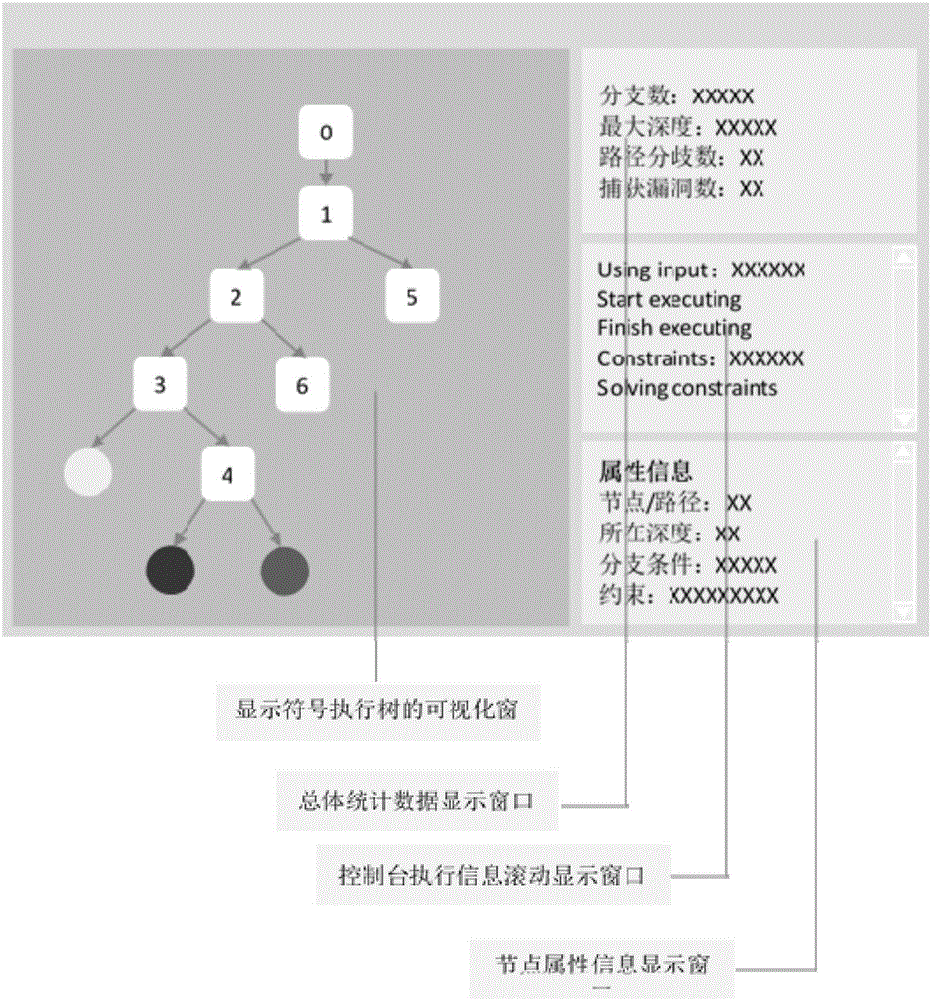
[0064] 1) Symbolic execution tree drawing module: This module builds and draws a symbolic execution tree, and once called, draws branch nodes from the root of the symbolic execution tree according to the incoming branch data. When the symbolic execution tool executes a branch, it will call this module, and input the branch location information (the memory address value where the branch is located), the branch condition, the true and false value of the branch condition during execution, and the test case used in this round; at the same time, it will also Some data will be automatically generated in the module, such as the depth of the branch node, the time information when the branch point is found, and so on. Then this module will store this information in the newly constructed branch node, and at the same time draw the branch node on the user interface in real time. The corresponding true or false branch of the branch node is connected to the next node until the program is ex...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com