Patents
Literature
49 results about "Execution tree" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
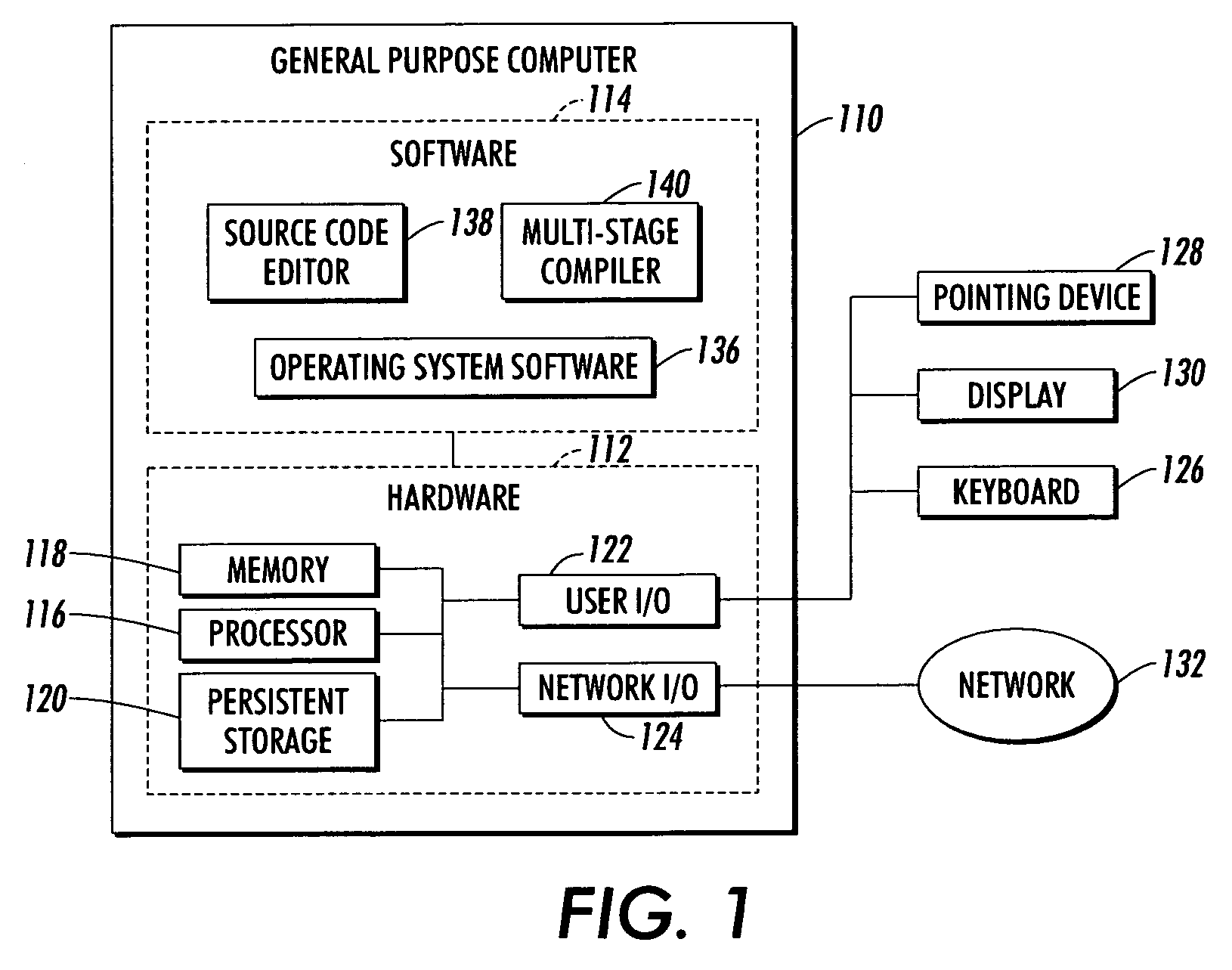
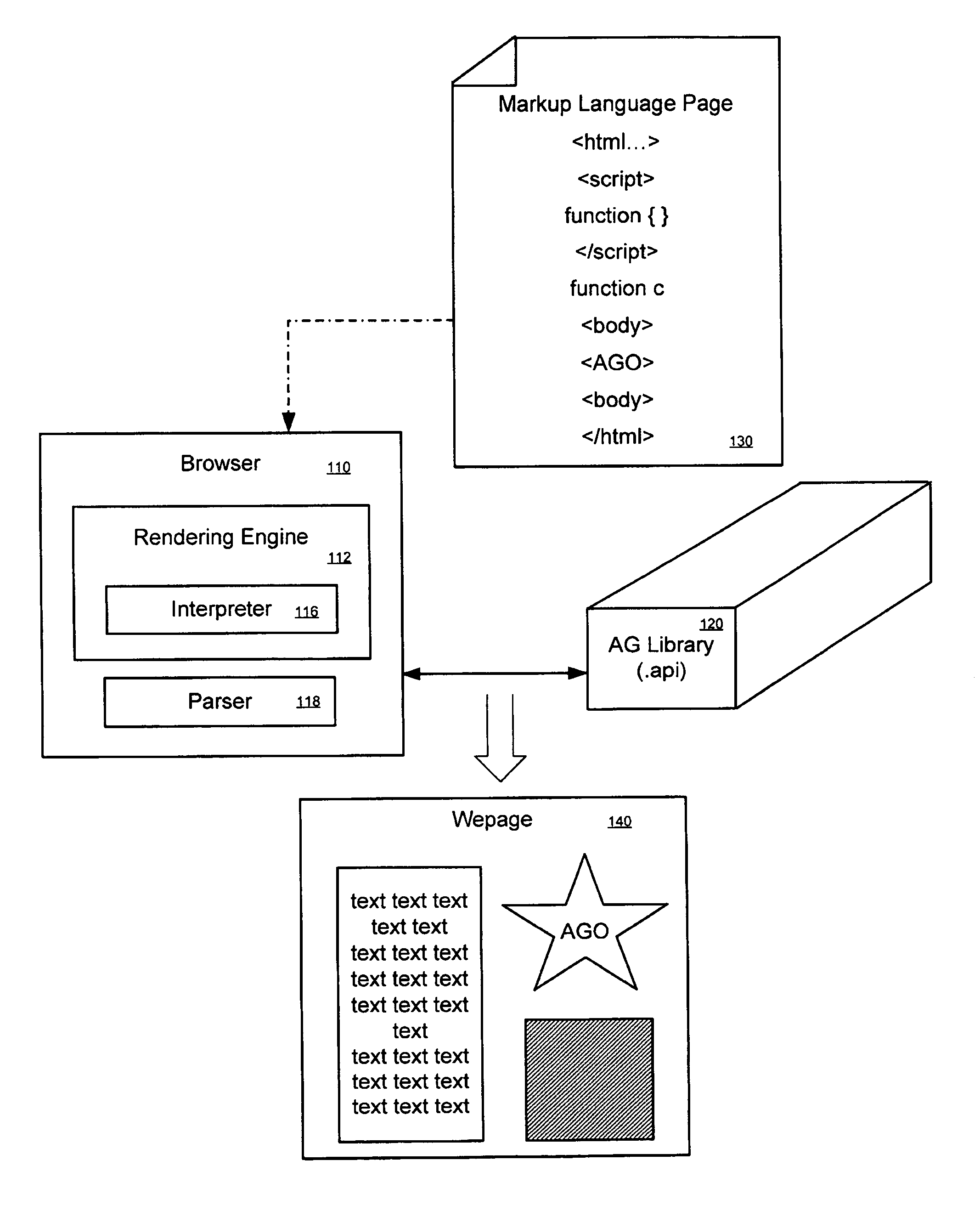
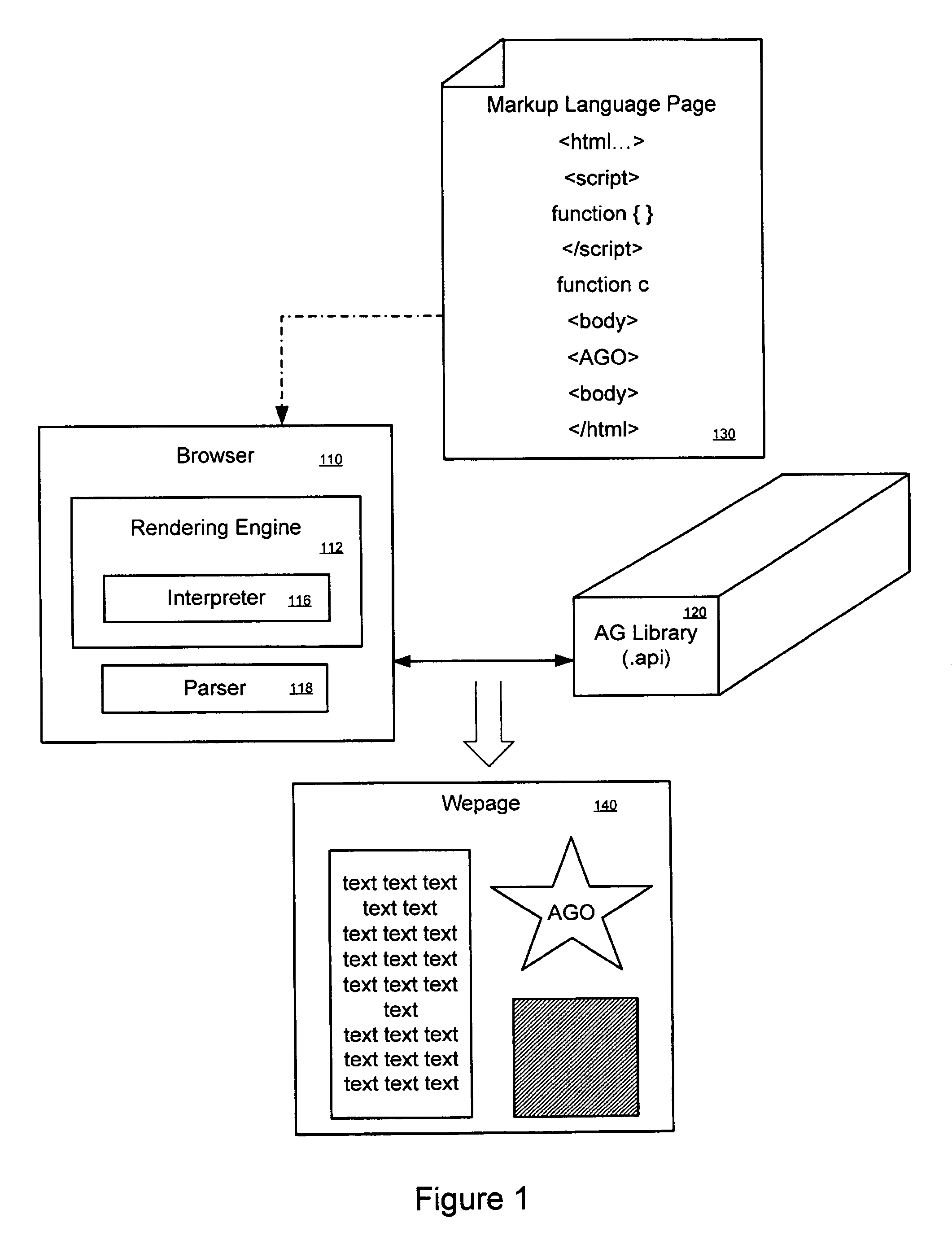
Procedurally expressing graphic objects for web pages
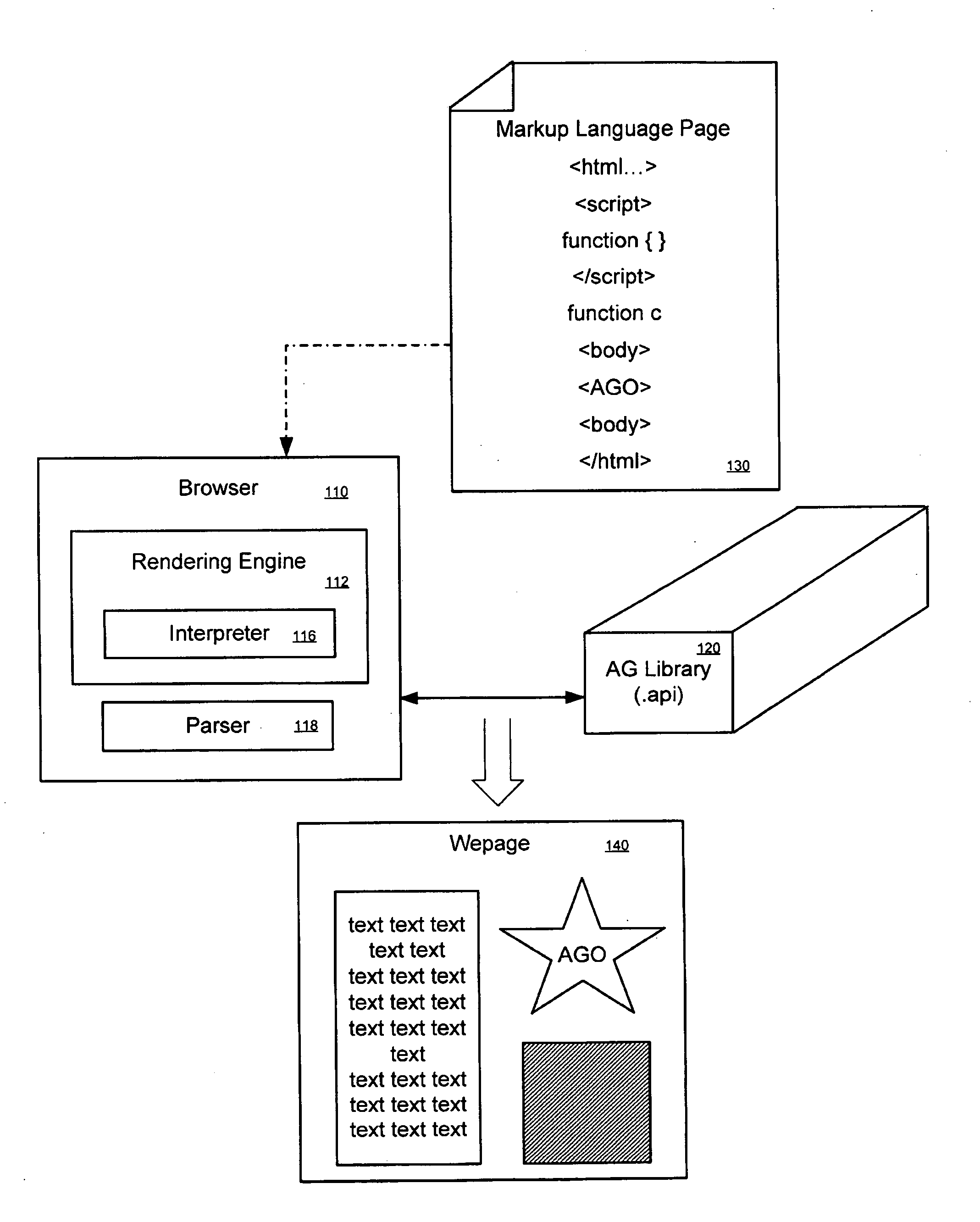
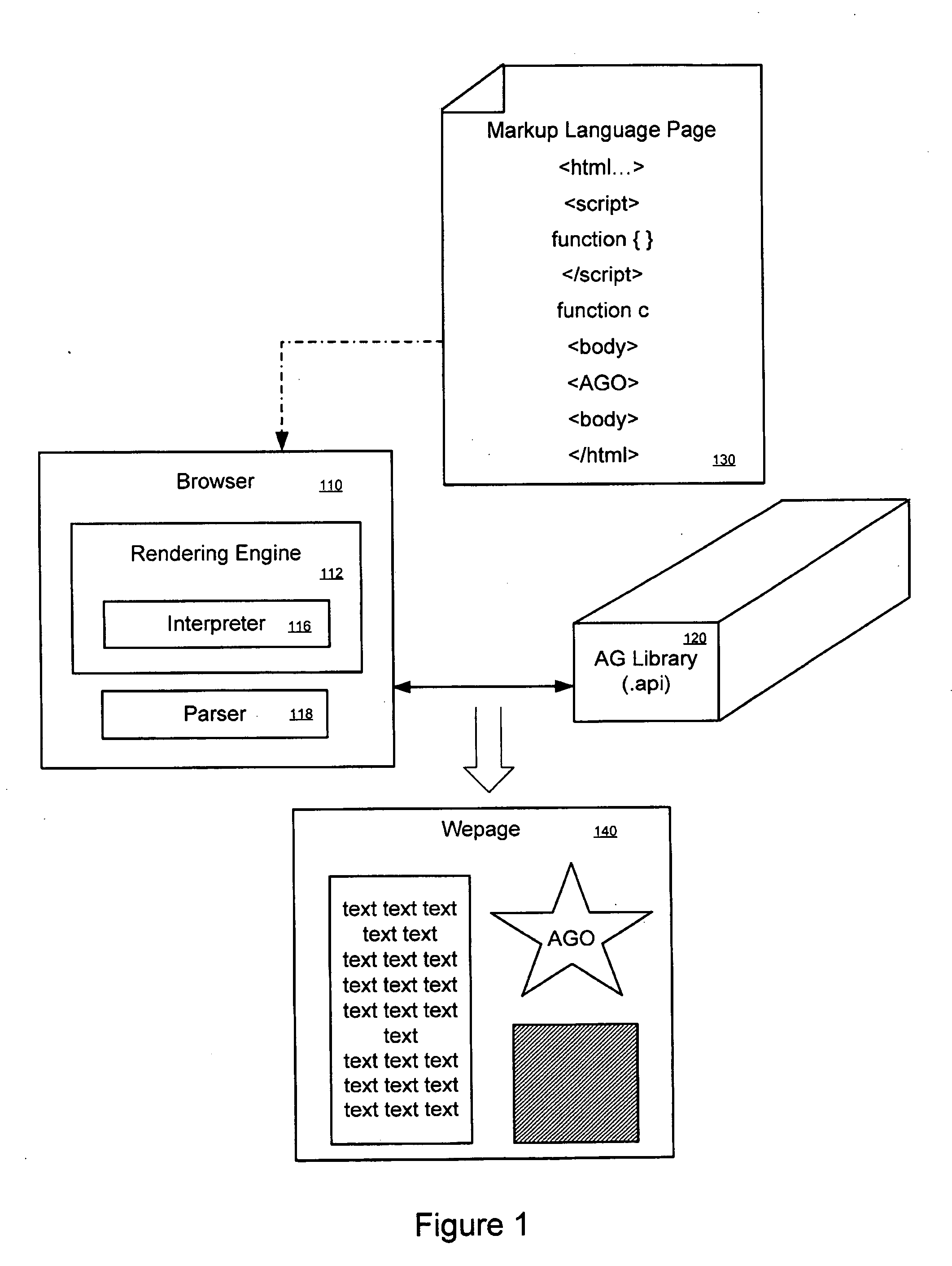
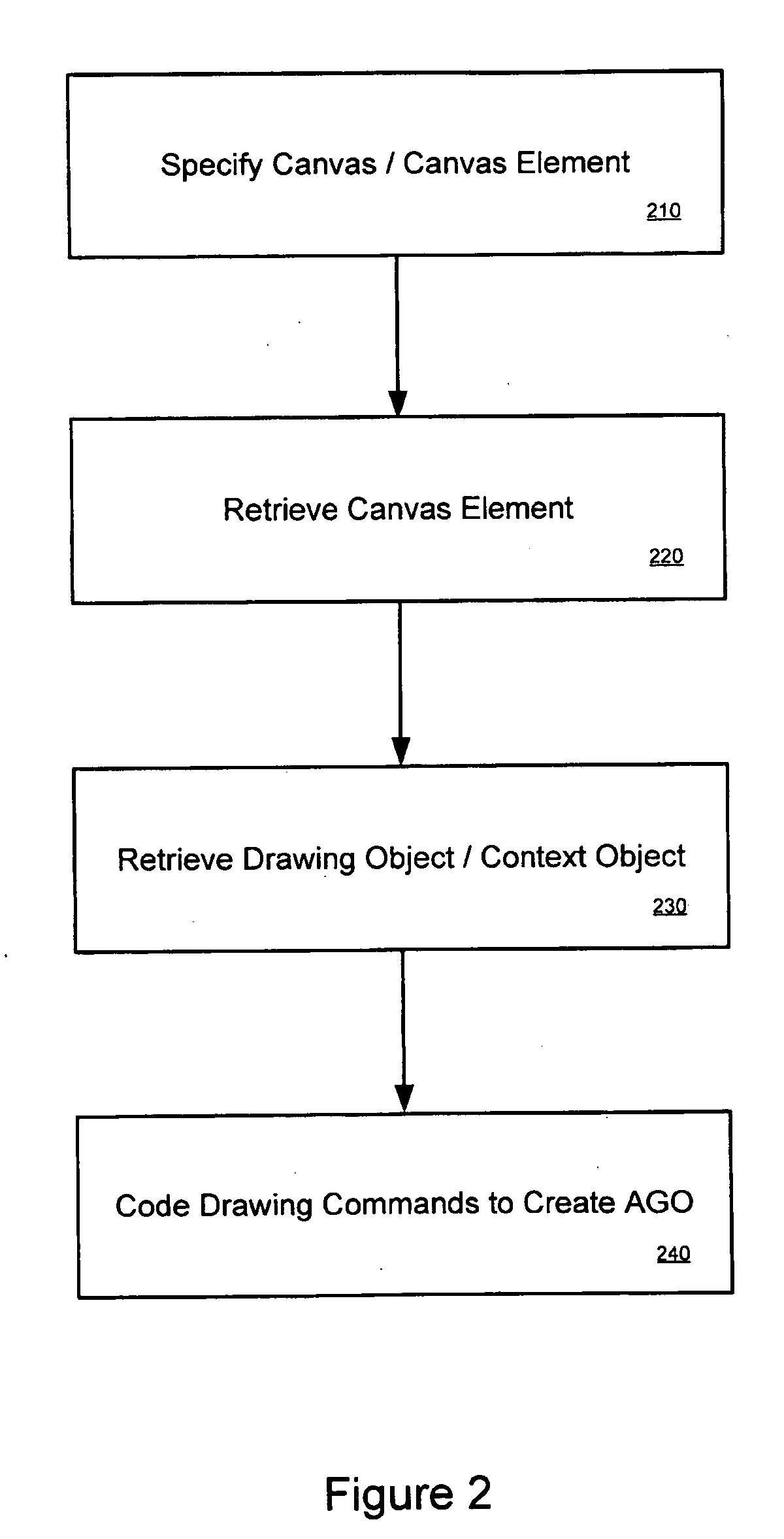
A graphics object can be expressed using procedural language embedded in a markup language document. In a embodiment, a drawing space is specified in markup language. A drawing command to arbitrarily draw a graphics object into the drawing space is specified in procedural language. Interpretation of the markup and procedural language commands results in the rendering of the arbitrary graphics object. In another embodiment, there is a browser comprising a rendering engine, an interpreter, and parser. The rendering engine is configured to interpret a markup language instruction that specifies a drawing space as well as drawing commands in procedural language for drawing an arbitrary graphic object into the drawing space. The parser can then parse the drawing commands and convert them into an execution tree of tree objects.
Owner:APPLE INC
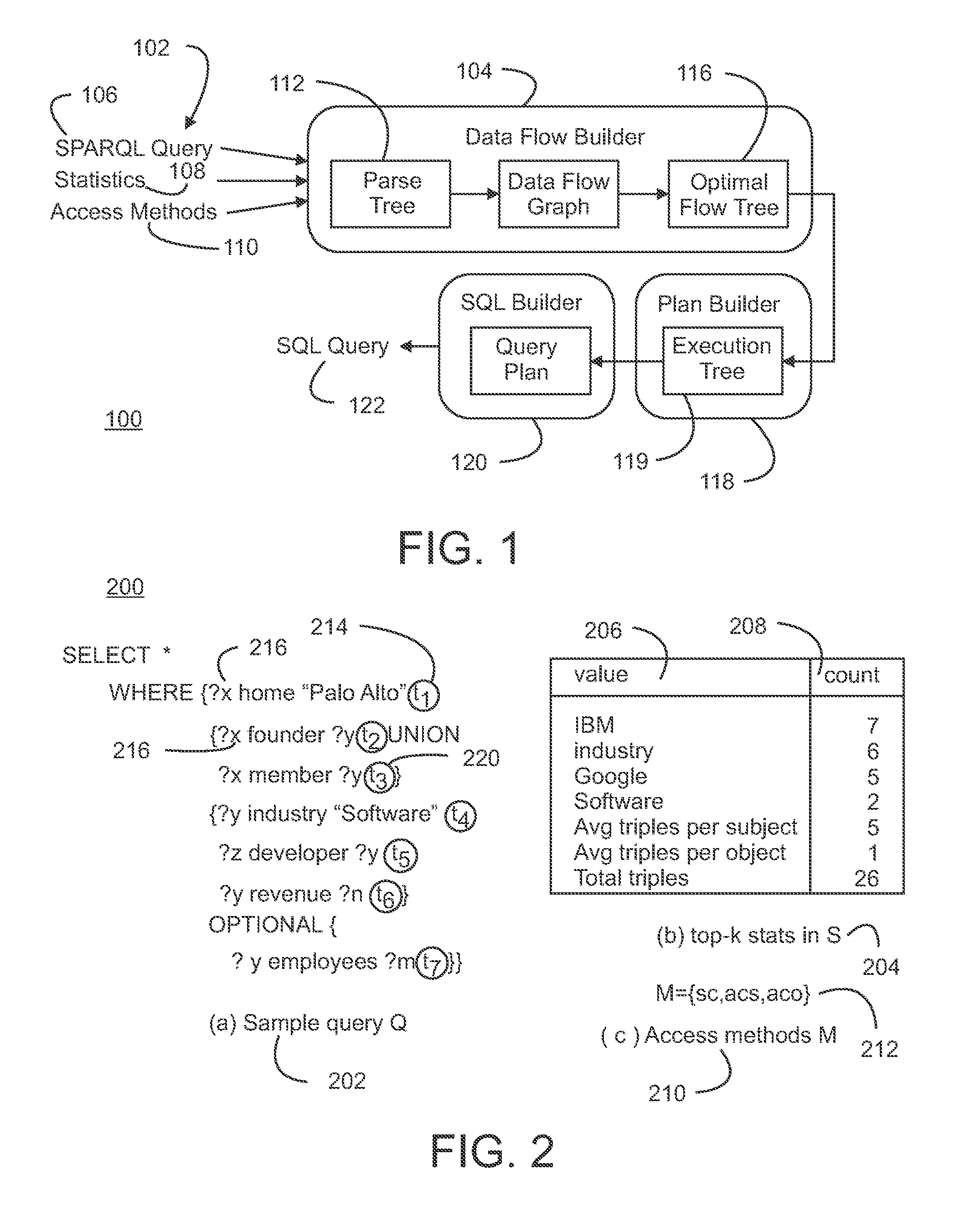
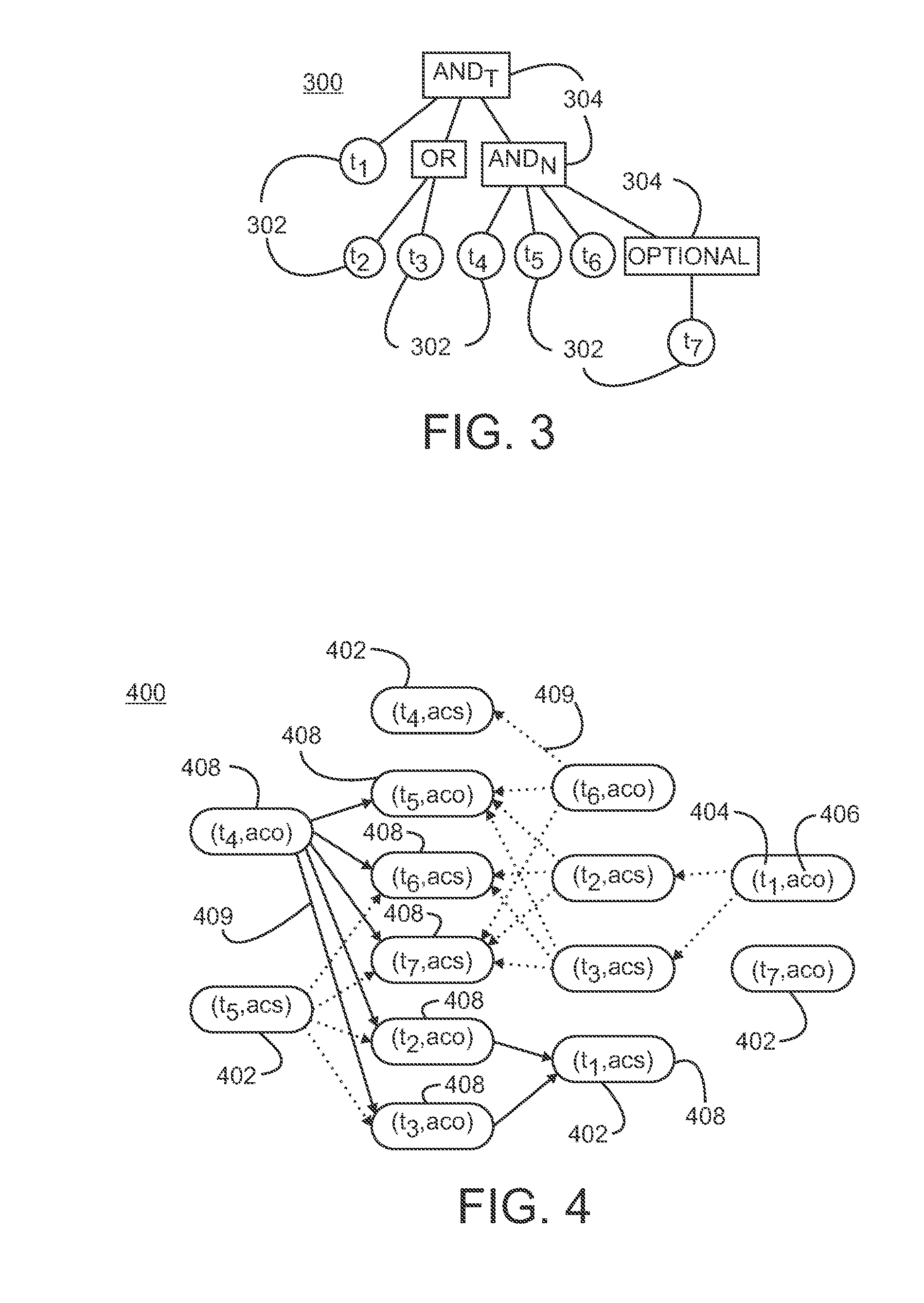
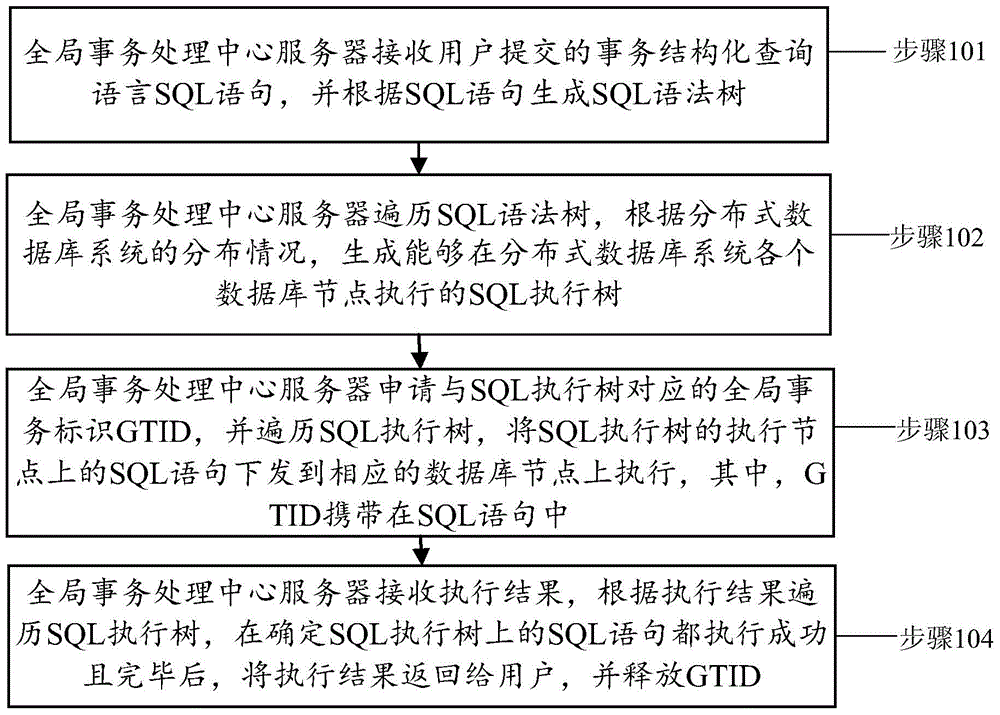
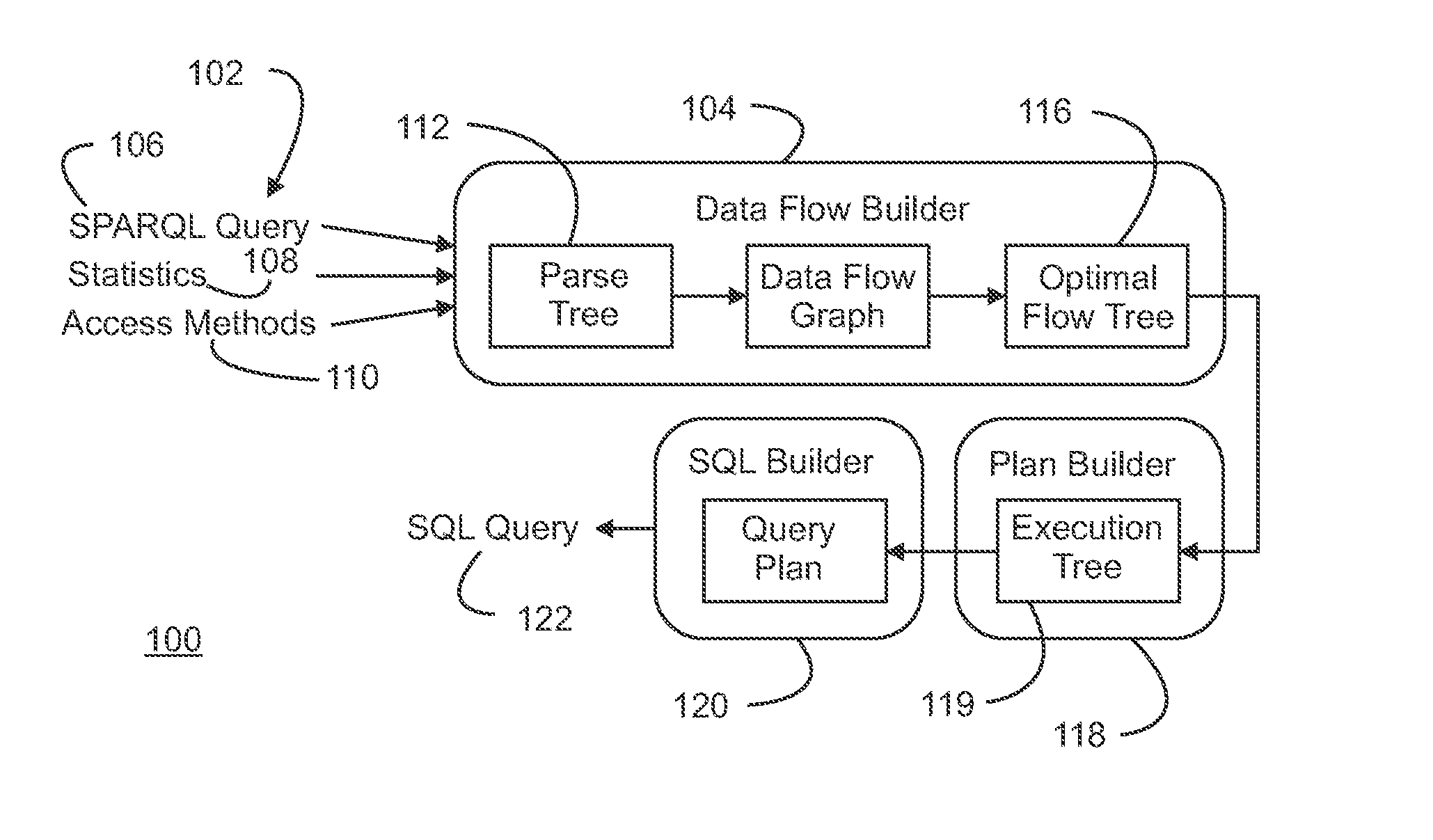
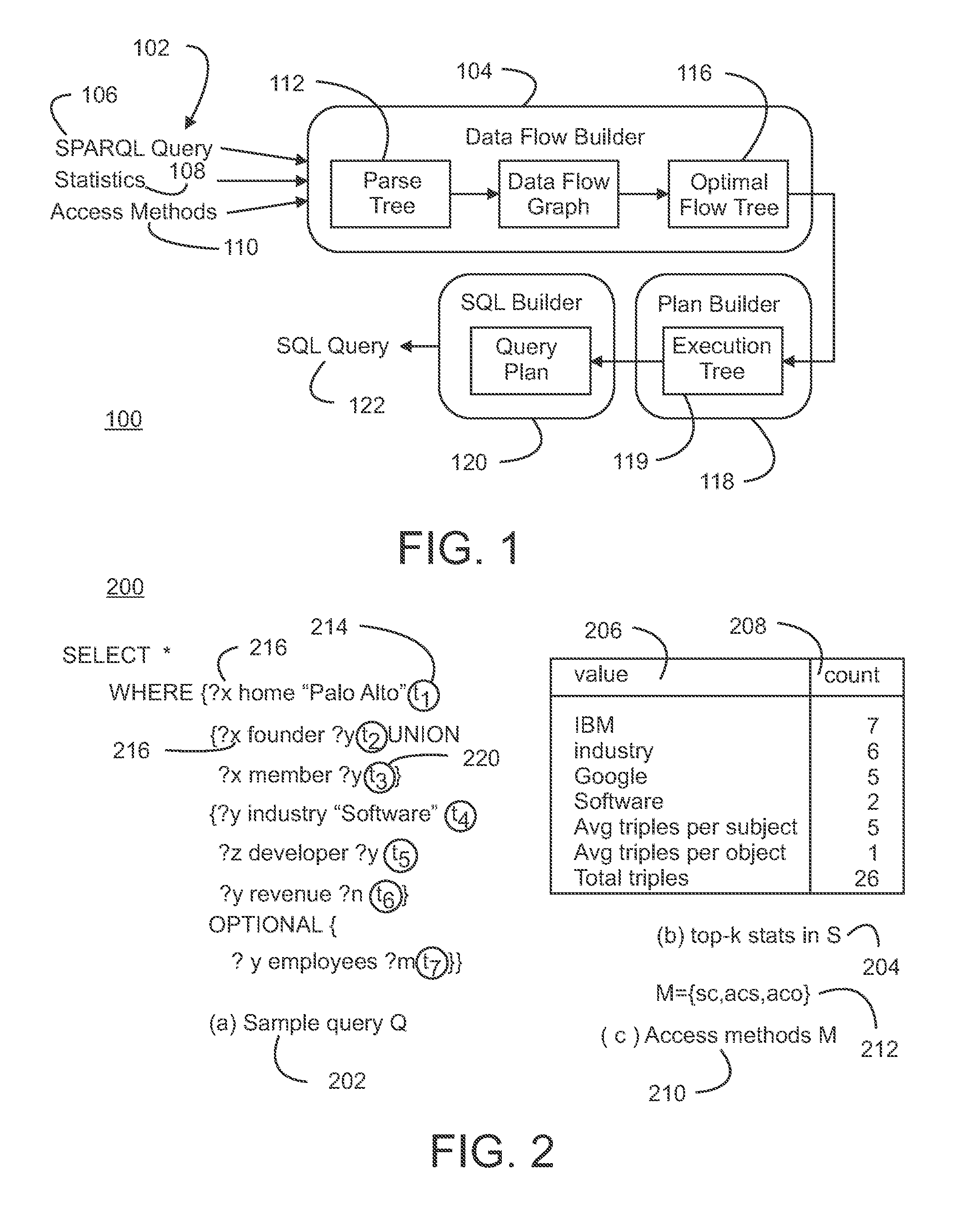
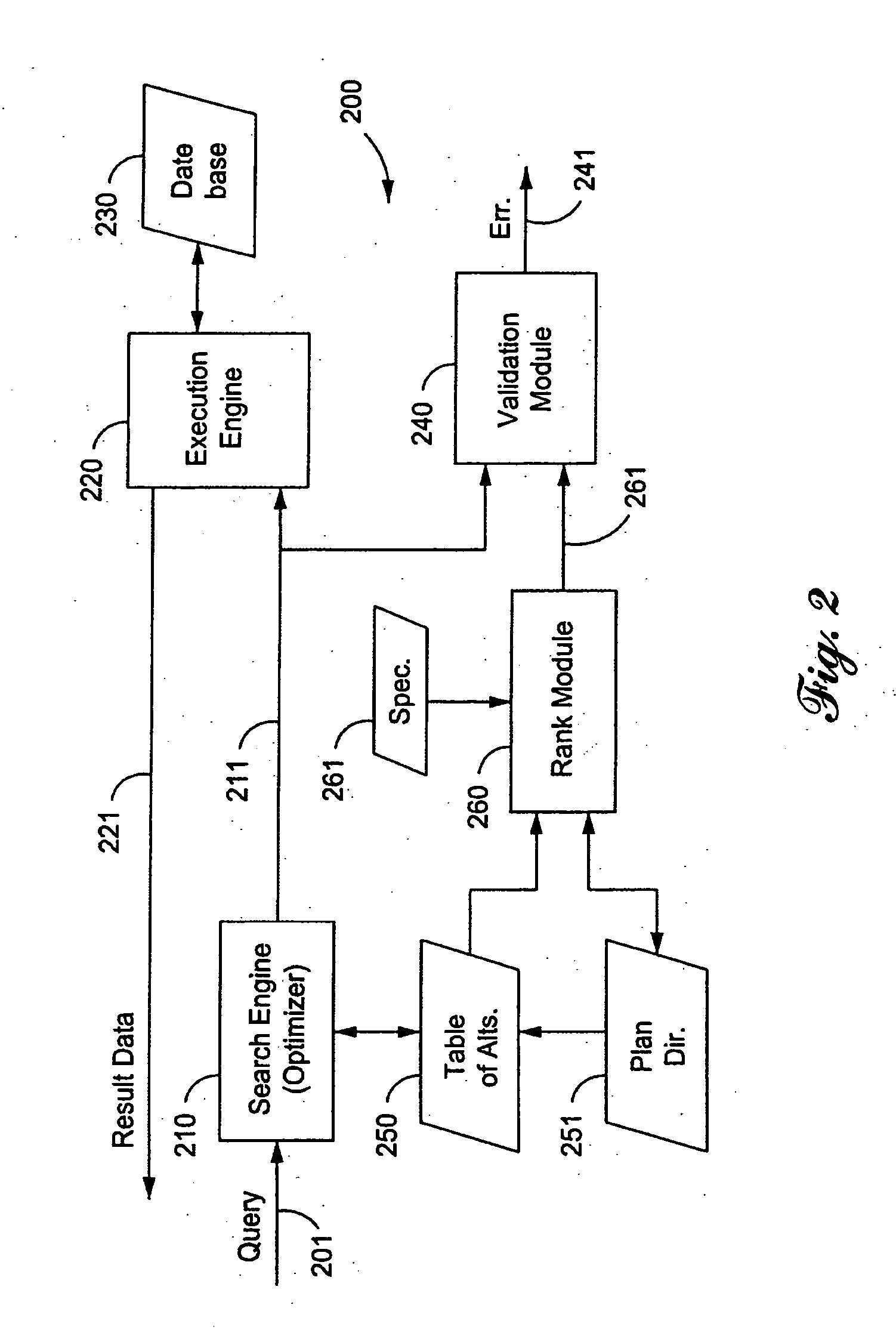
Method and Apparatus for Optimizing the Evaluation of Semantic Web Queries
InactiveUS20140304251A1Effective evaluationAmenable to optimizationDigital data information retrievalDigital data processing detailsQuery planAccess method
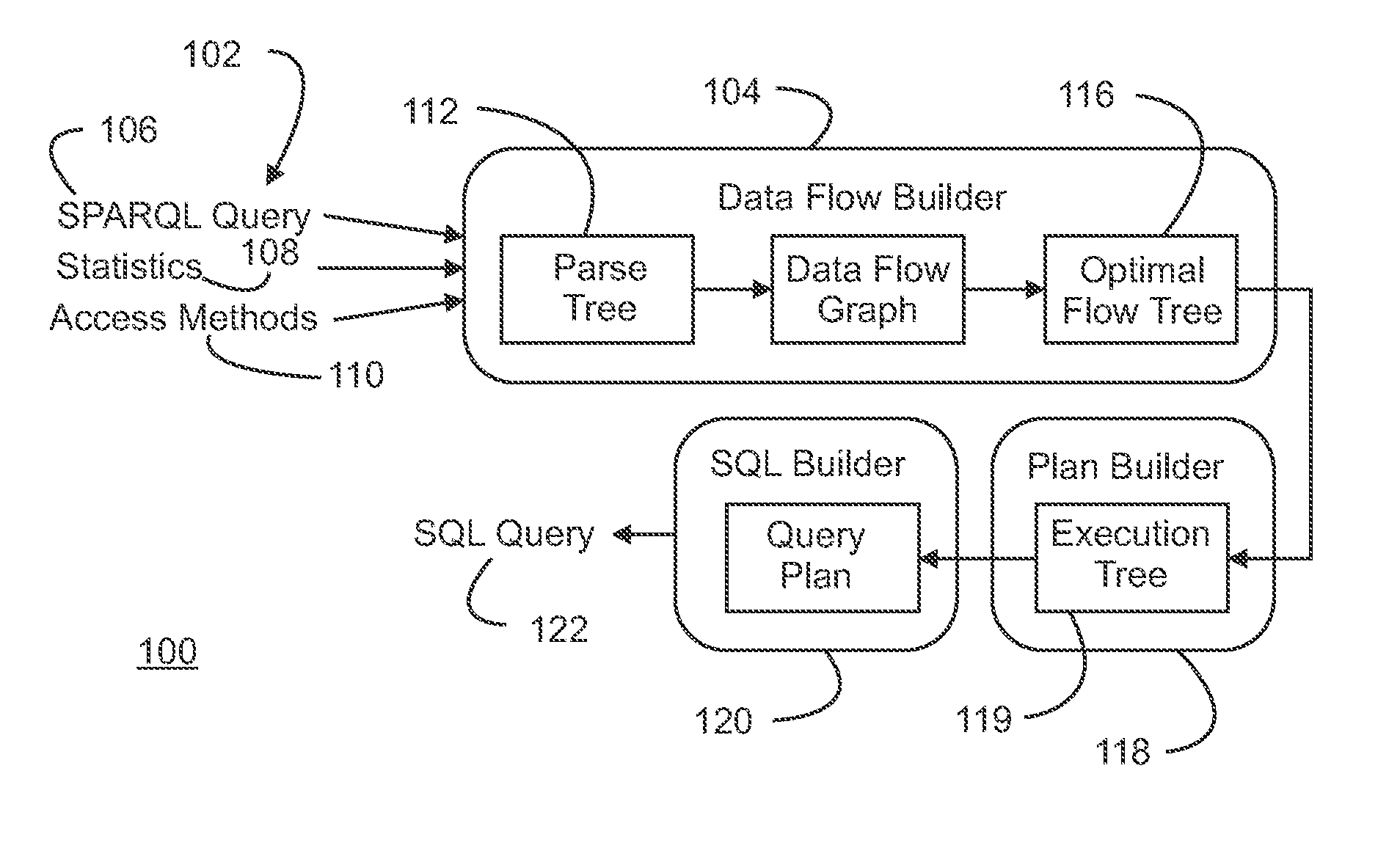
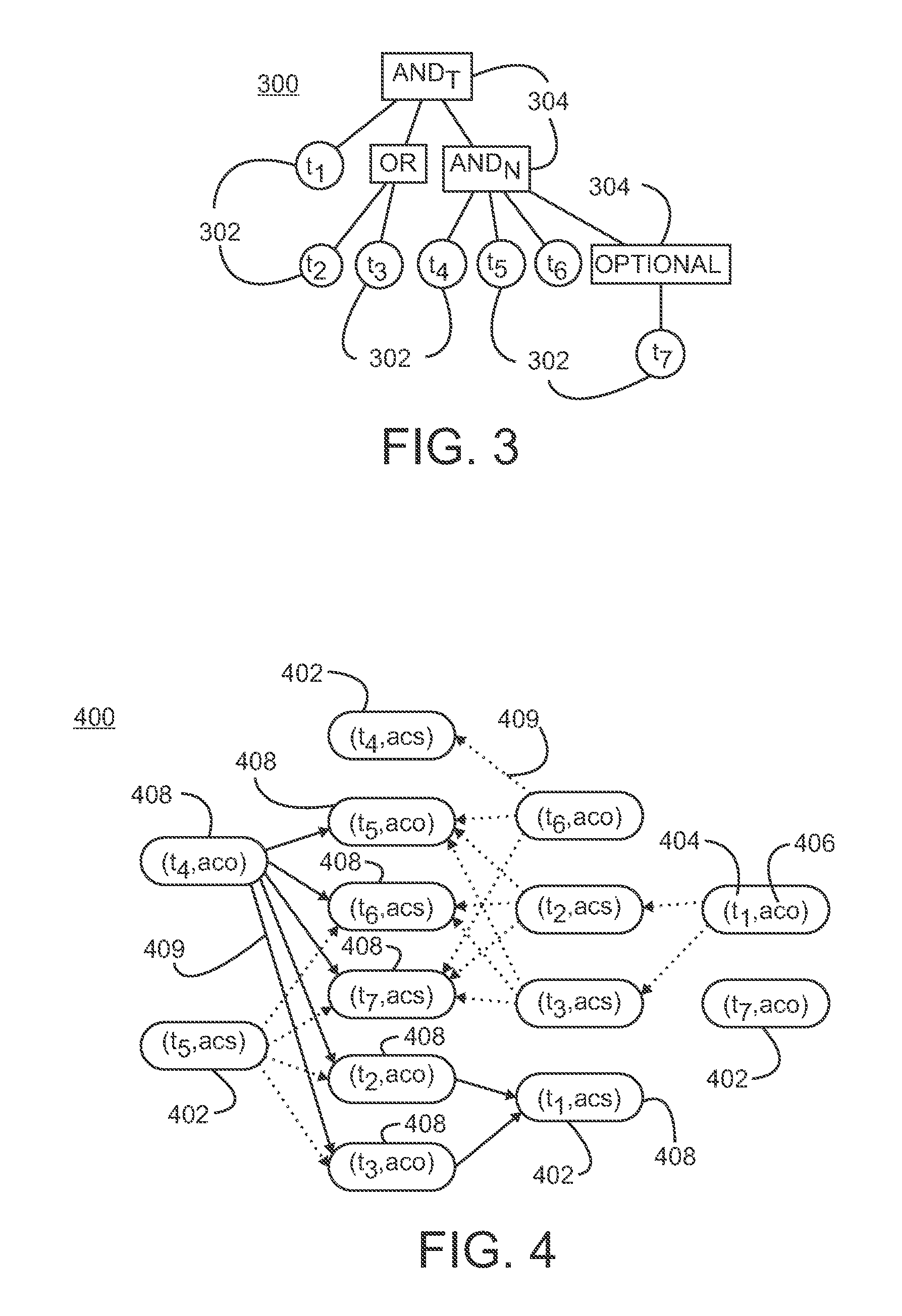
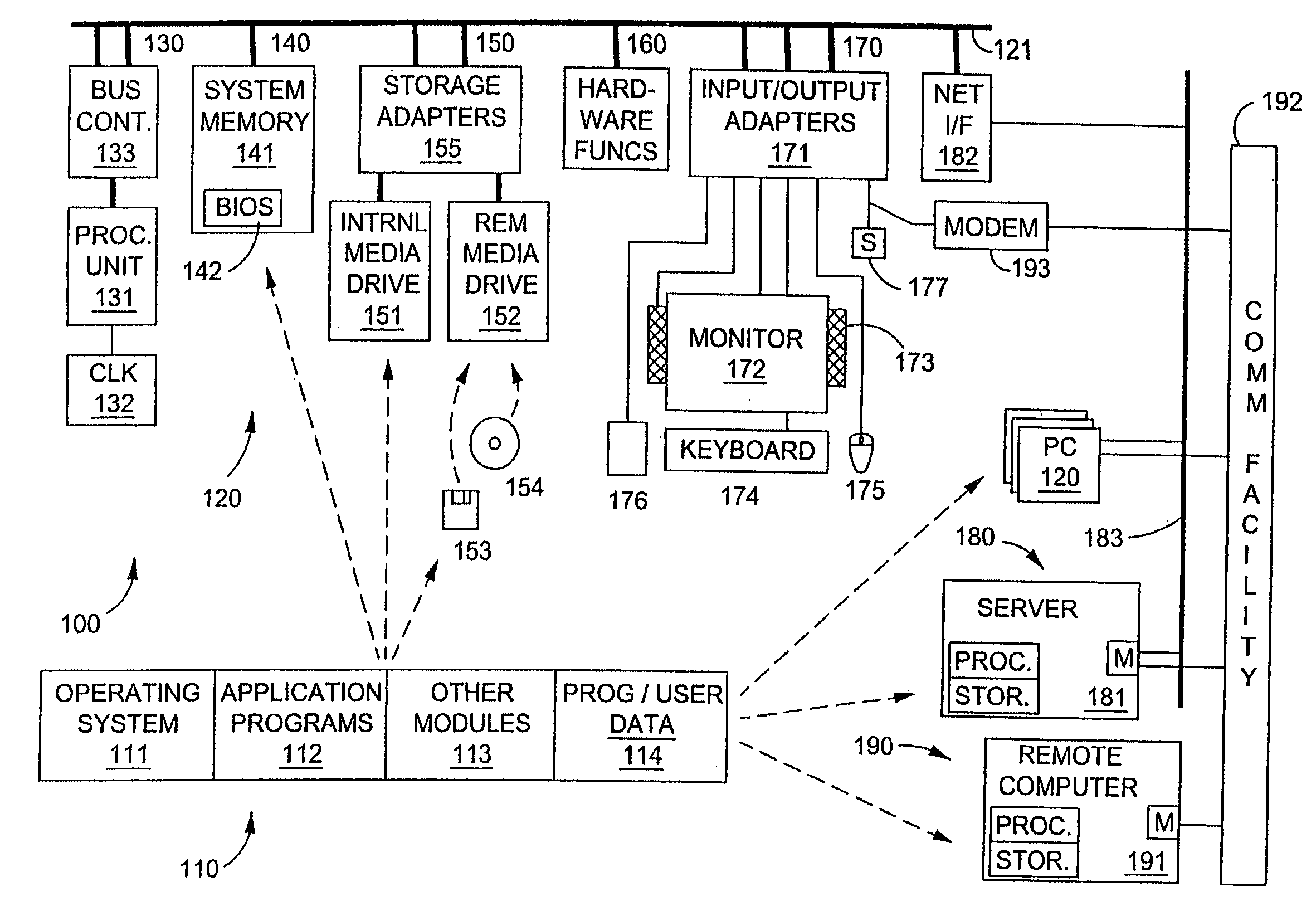
A semantic query over an RDF database is received with RDF database statistics and access methods for evaluating triple patterns in the query. The semantic query is expressed as a parse tree containing triple patterns and logical relationships among the triple patterns. The parse tree and access methods create a data flow graph containing a plurality of triple pattern and access method pair nodes connected by a plurality of edges, and an optimal flow tree through the data flow graph is determined such that costs are minimized and all triple patterns in the semantic query are contained in the optimal flow tree. A structure independent execution tree defining a sequence of evaluation through the optimal flow tree is created and is transformed into a database structure dependent query plan. This is used to create an SQL query that is used to evaluate the semantic query over the RDF database.
Owner:IBM CORP
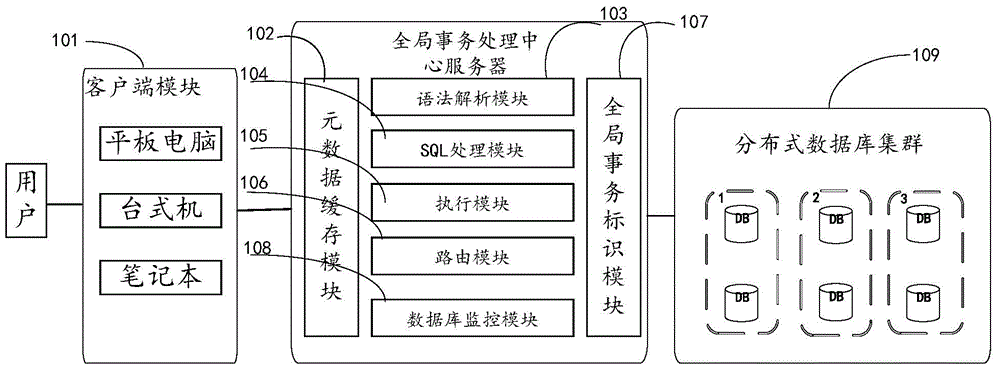
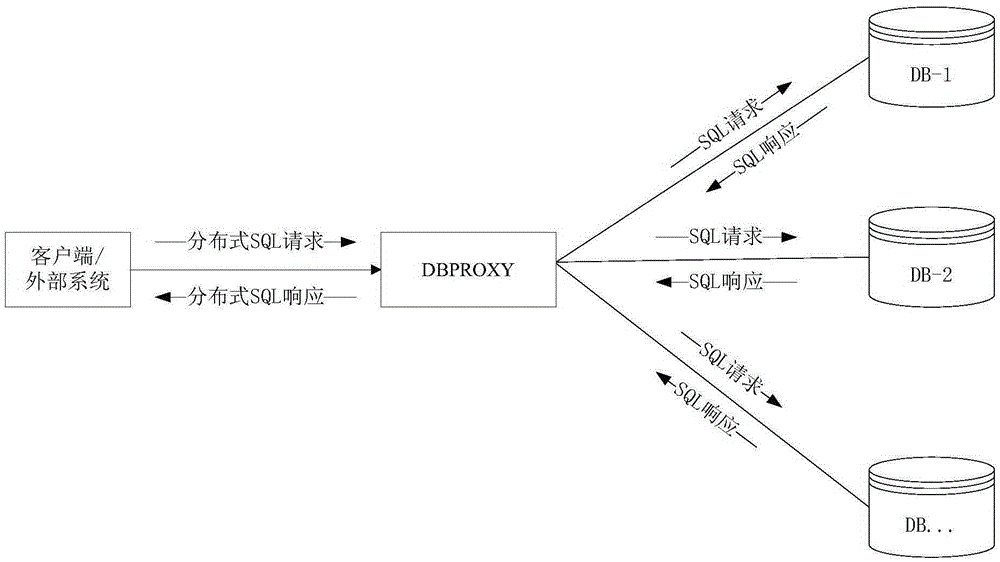
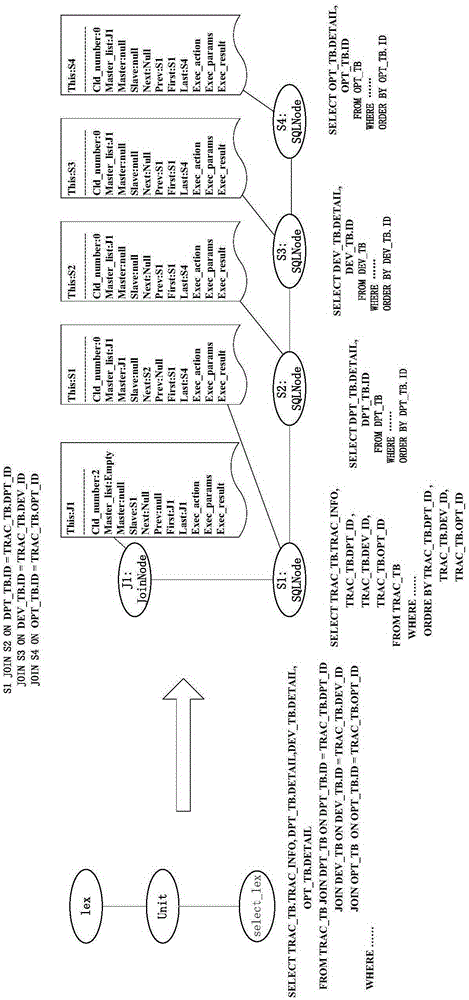
Transaction processing method and device of distributed database system
ActiveCN105608086AImprove processing efficiencySpecial data processing applicationsTransaction processing systemQuery language
The invention discloses a transaction processing method and device of a distributed database system. The method comprises the following steps: receiving a transaction SQL (Structured Query Language) statement handed by a user via a global transaction processing central server, and generating a SQL syntax tree according to the SQL statement; traversing the SQL syntax tree, and generating a SQL execution tree which can be executed in each database node of the distributed database system according to the distribution situation of the distributed database system; applying for a GTID (Global Transaction ID) corresponding to the SQL execution tree, traversing the SQL execution tree, and issuing the SQL statement on the execution node of the SQL execution tree to be executed on the corresponding database node, wherein the GTID is carried in the SQL statement; and receiving an execution result, traversing the SQL execution tree according to the execution result, returning the execution result to a user after a determination result shows that all SQL statements on the SQL execution tree finish being executed, and releasing the GTID.
Owner:ZTE CORP +1
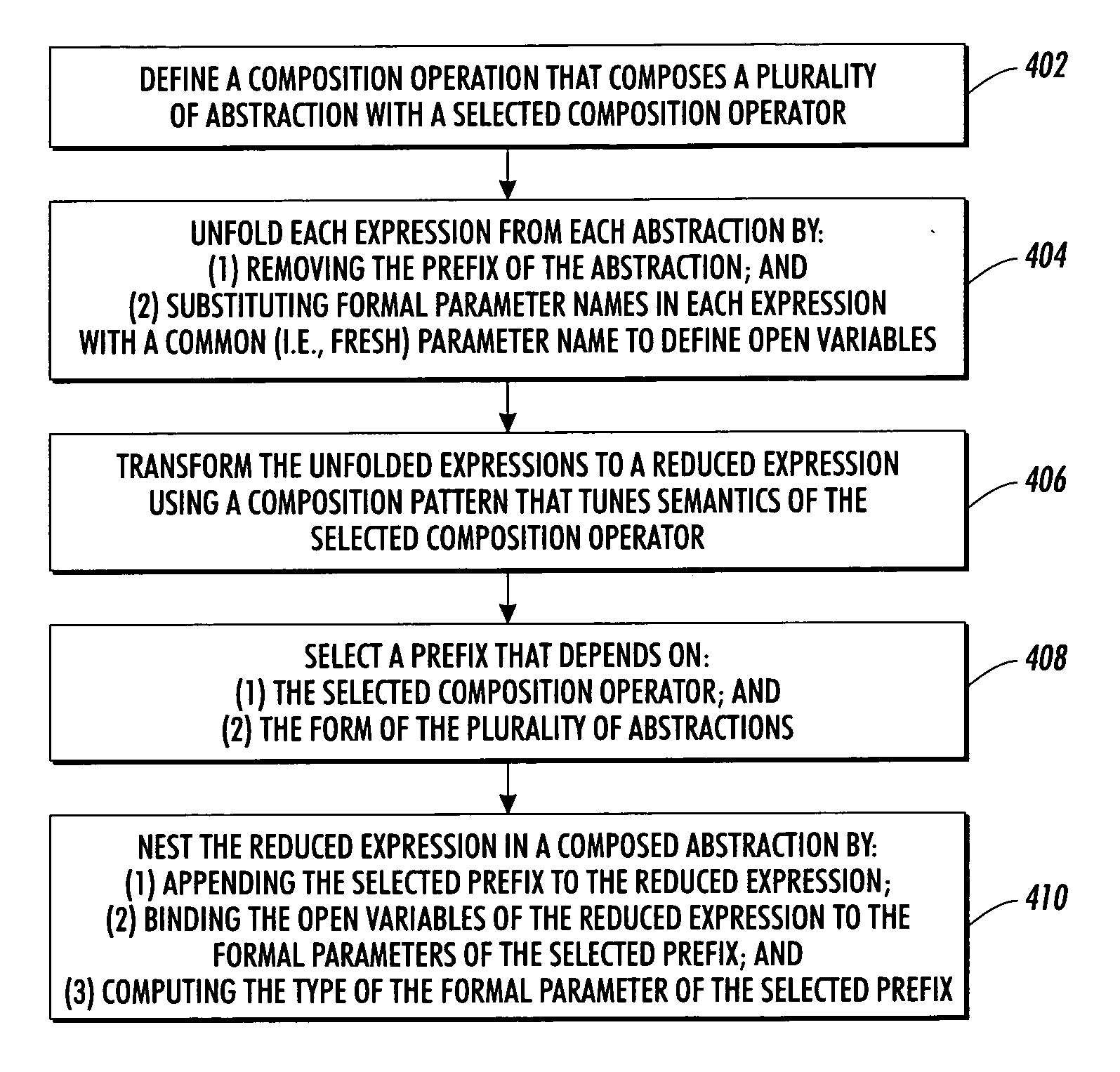
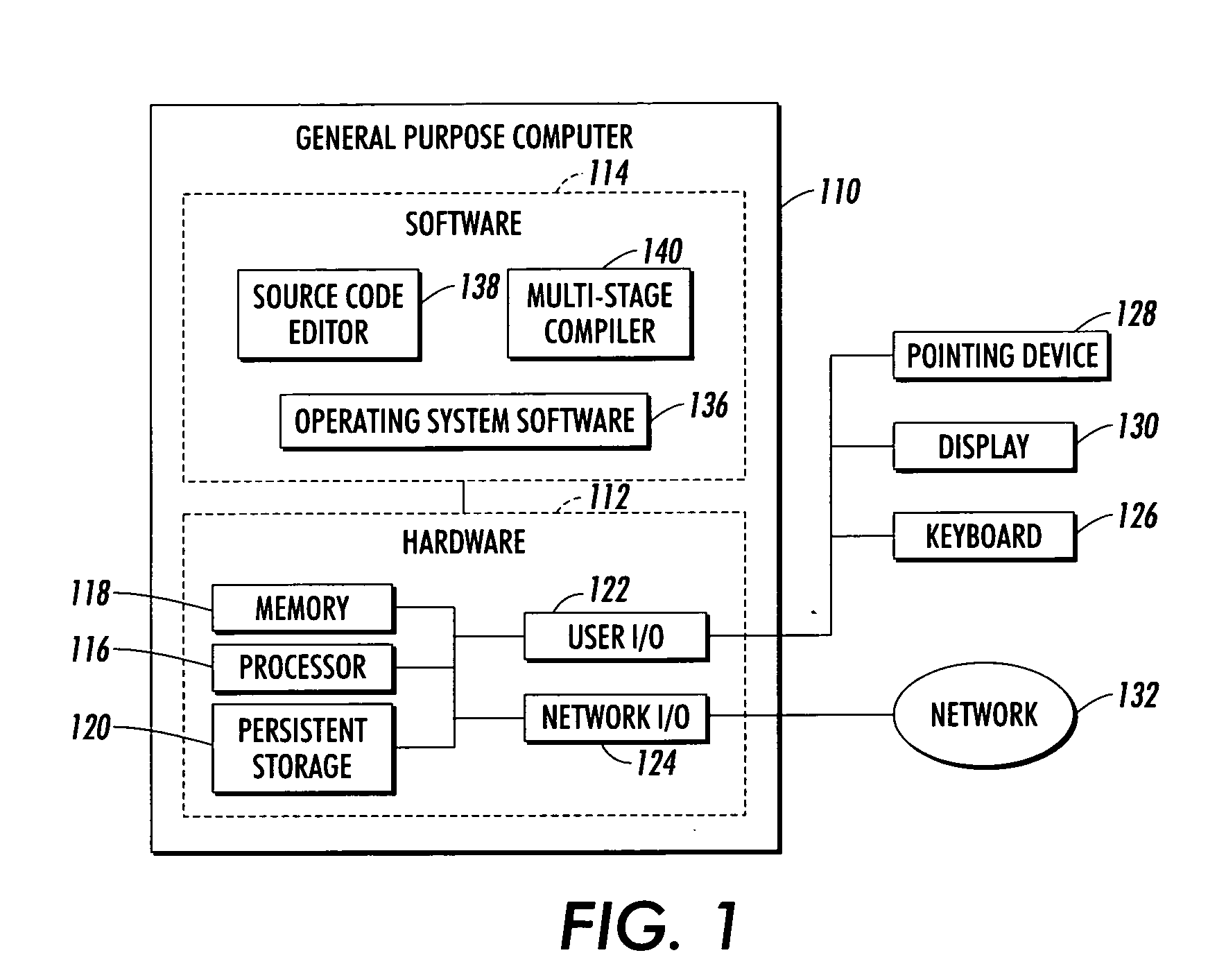
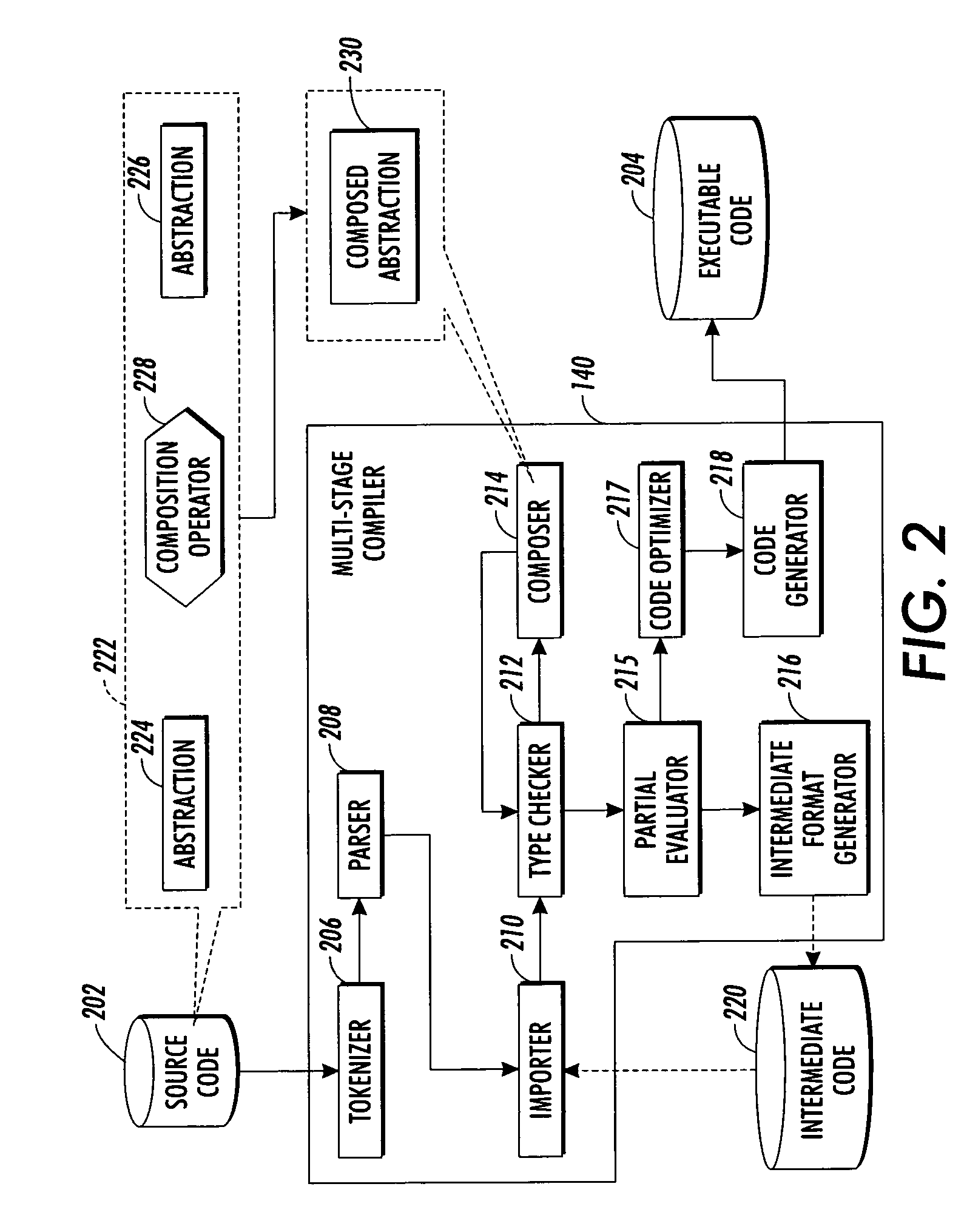
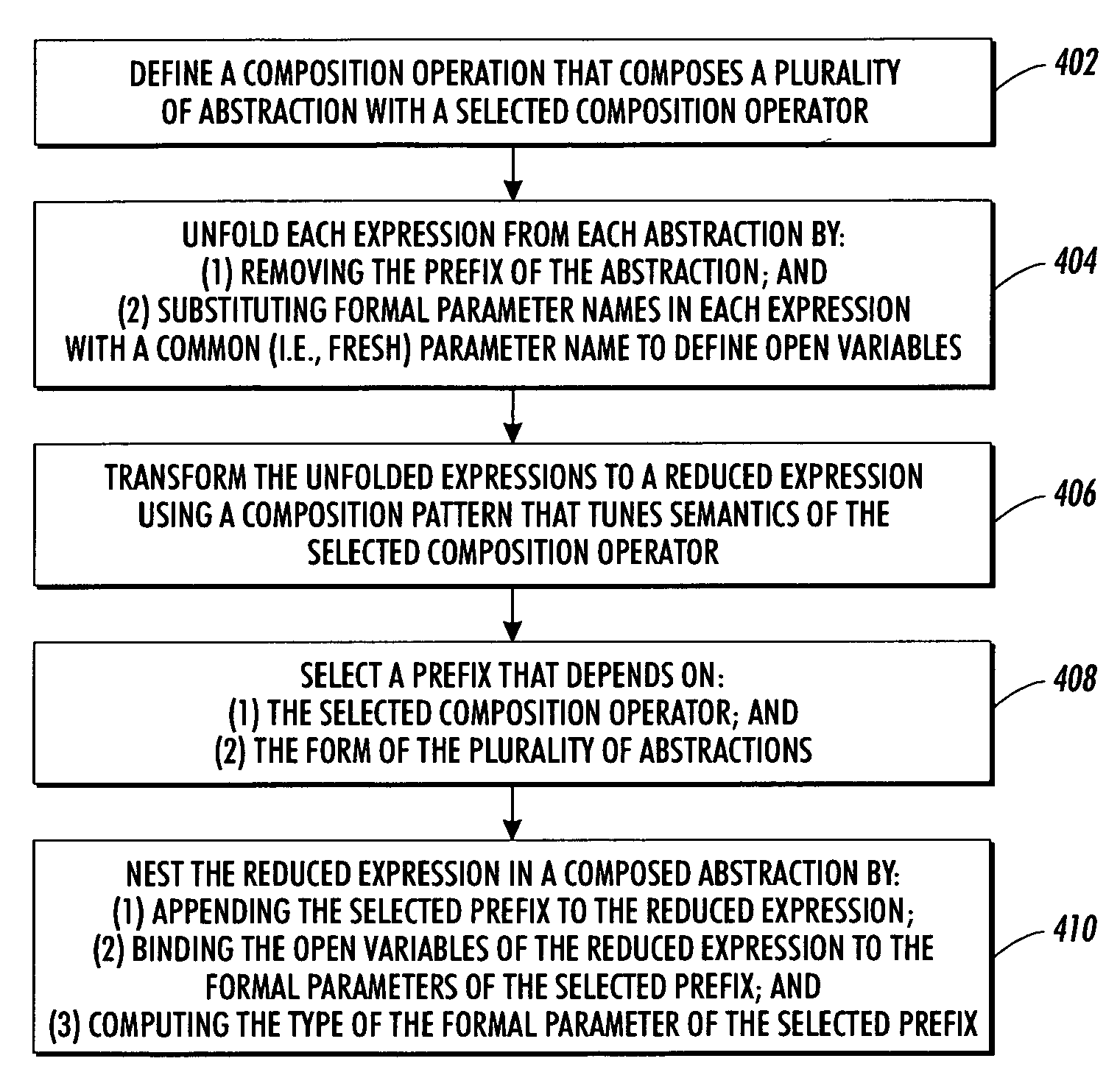
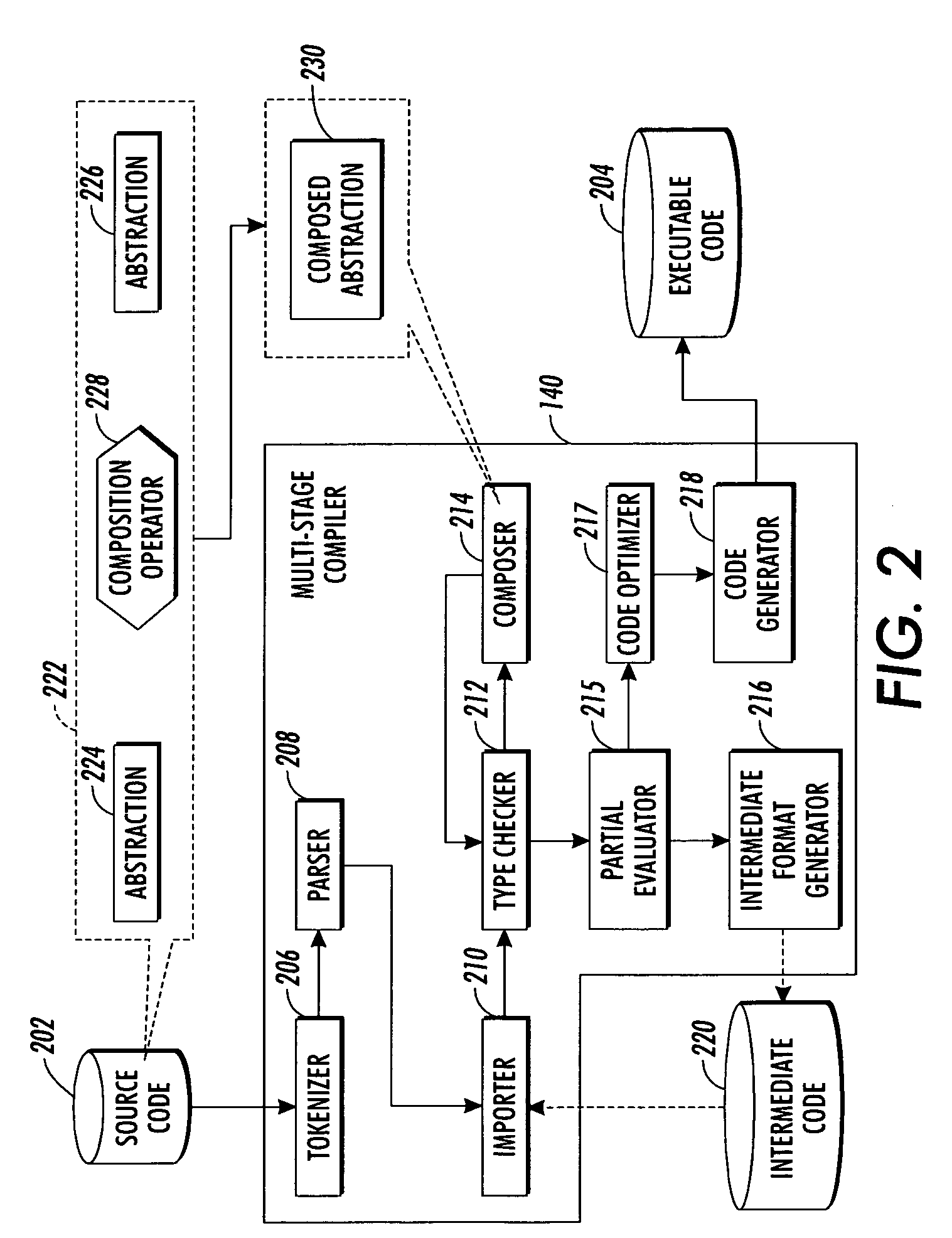
Program compiler with abstraction composer
InactiveUS20040148592A1Simplifying program maintenanceImprove legibilitySoftware engineeringSpecific program execution arrangementsTheoretical computer scienceSource code
Source code is compiled using a multi-stage compiler that includes a tokenizer, a type checker, and a composer. The tokenizer segments source code into a sequence of tagged segments. The source code includes at least one instruction that composes a first abstraction and a second abstraction with a selected composition operator. The parser builds a tree using the sequence of tagged segments. The type checker performs a first pass of the tree to determine whether abstractions on the tree are well typed. The composer reduces the at least one instruction composing the first and the second abstractions on the tree to a third abstraction. The composer substitutes the first and the second abstractions on the tree with the third abstraction, wherein the type checker performs a second pass of the tree to determine whether the third abstraction is well typed.
Owner:XEROX CORP
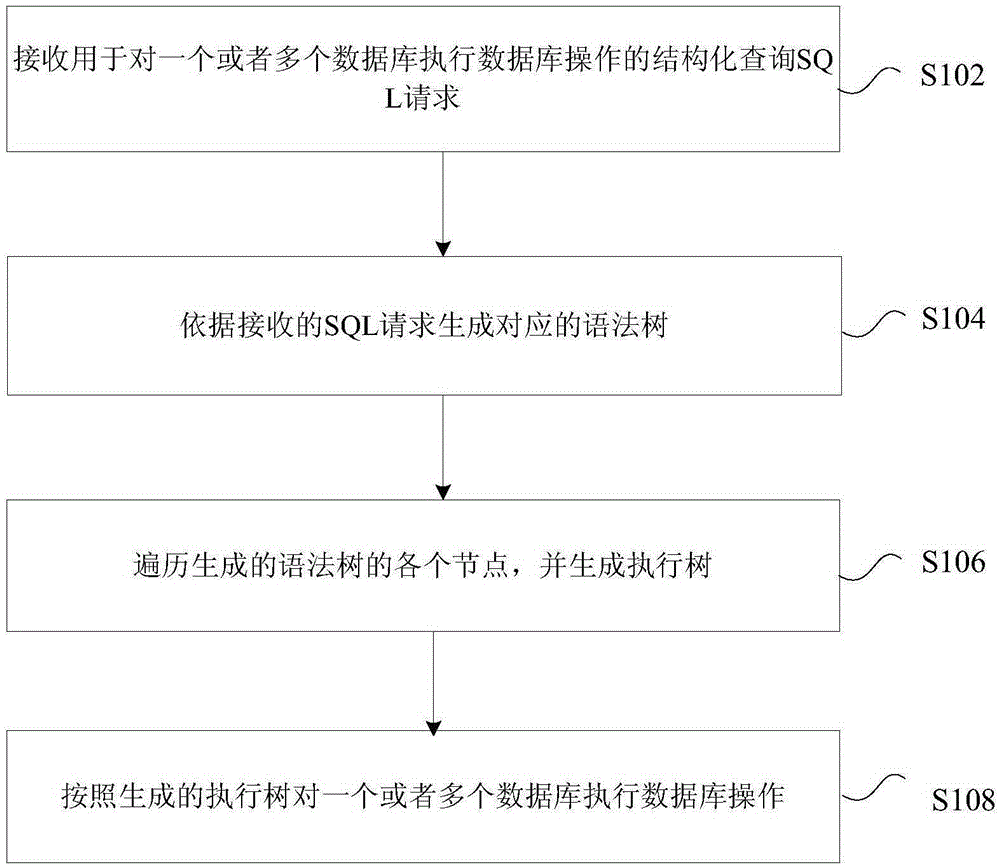
Execution method and device for databases
ActiveCN106547796ASolve the technical problem of not supporting linked data query across database nodesDatabase distribution/replicationSpecial data processing applicationsSQLGrammaticality
The invention provides an execution method and device for databases. The method comprises following steps: receiving structured query SQL requests of database operation for one or multiple databases; generating corresponding syntax trees in accordance with the received SQL requests; searching all nodes for generation of the syntax trees and generating execution trees; and executing database operation for one or multiple databases based on generated syntax trees. By adoption of the execution method and device for databases, that technical problem in the prior art that associated data of inter-database nodes cannot be searched is solved, thereby achieving the technical effect of searching associated data for inter-database nodes.
Owner:NANJING ZHONGXING XIN SOFTWARE CO LTD
Program compiler with abstraction composer
InactiveUS7284242B2Easy maintenanceImprove legibilitySoftware engineeringSpecific program execution arrangementsSource codeProgram compilation
Source code is compiled using a multi-stage compiler that includes a tokenizer, a type checker, and a composer. The tokenizer segments source code into a sequence of tagged segments. The source code includes at least one instruction that composes a first abstraction and a second abstraction with a selected composition operator. The parser builds a tree using the sequence of tagged segments. The type checker performs a first pass of the tree to determine whether abstractions on the tree are well typed. The composer reduces the at least one instruction composing the first and the second abstractions on the tree to a third abstraction. The composer substitutes the first and the second abstractions on the tree with the third abstraction, wherein the type checker performs a second pass of the tree to determine whether the third abstraction is well typed.
Owner:XEROX CORP
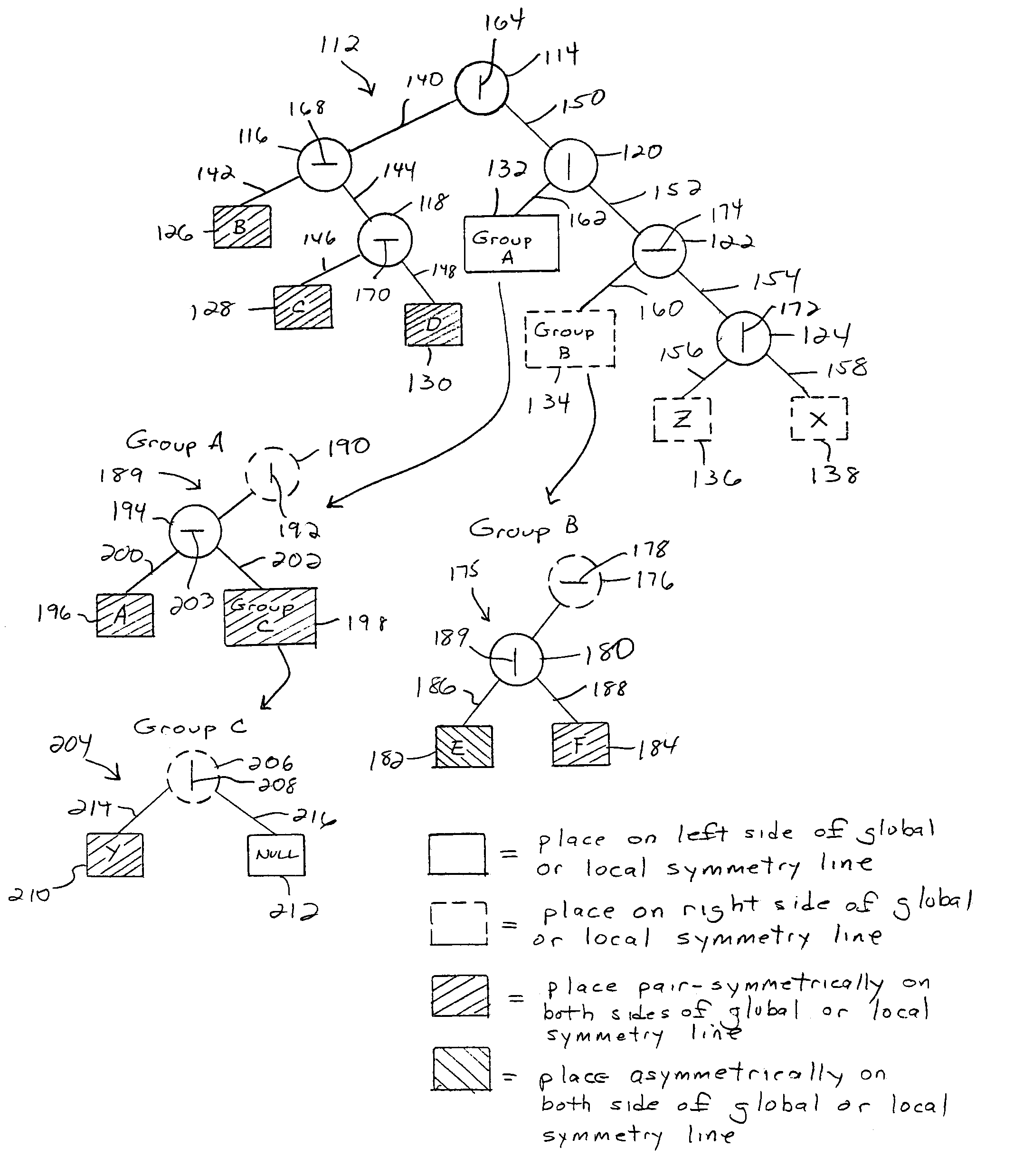
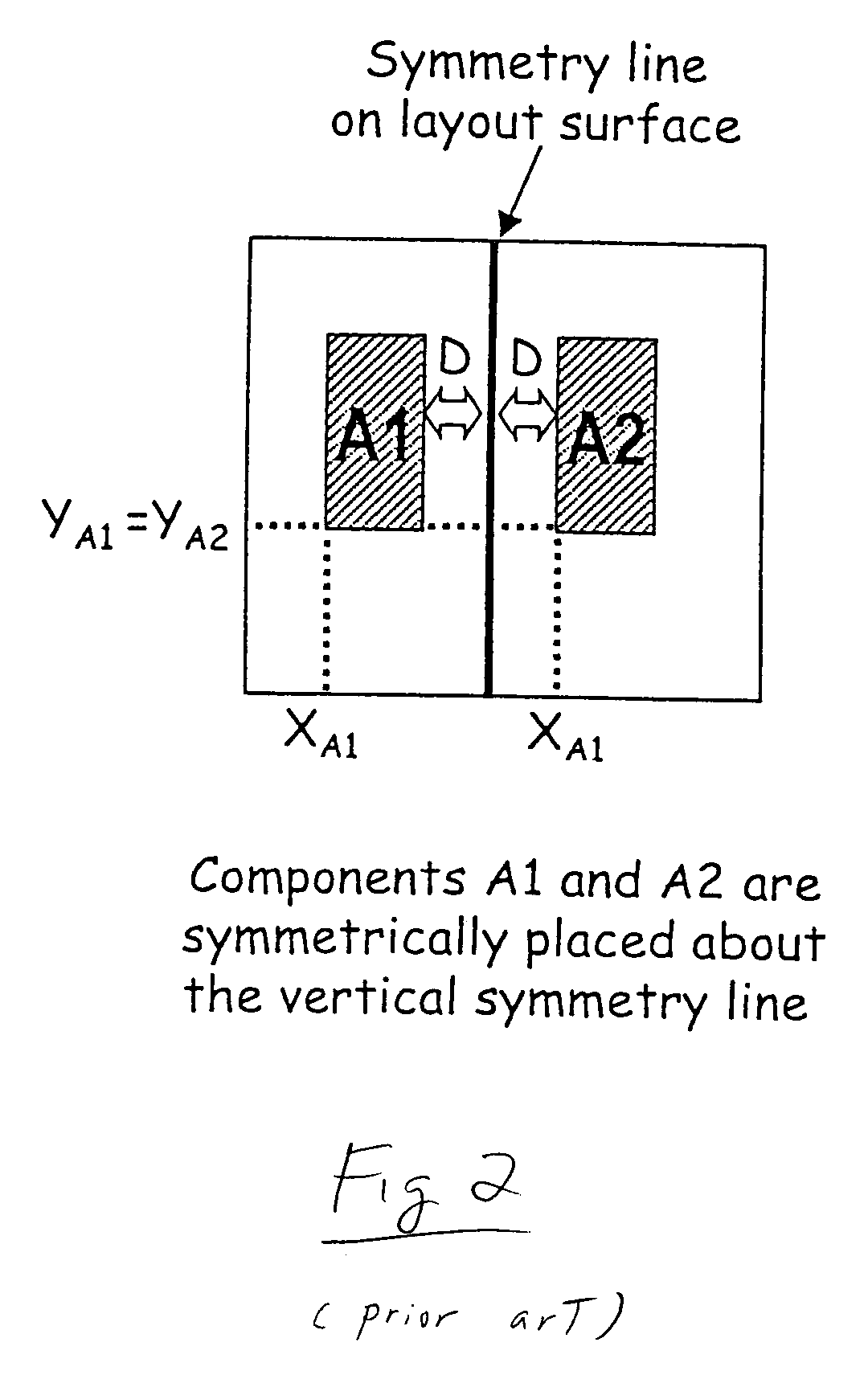
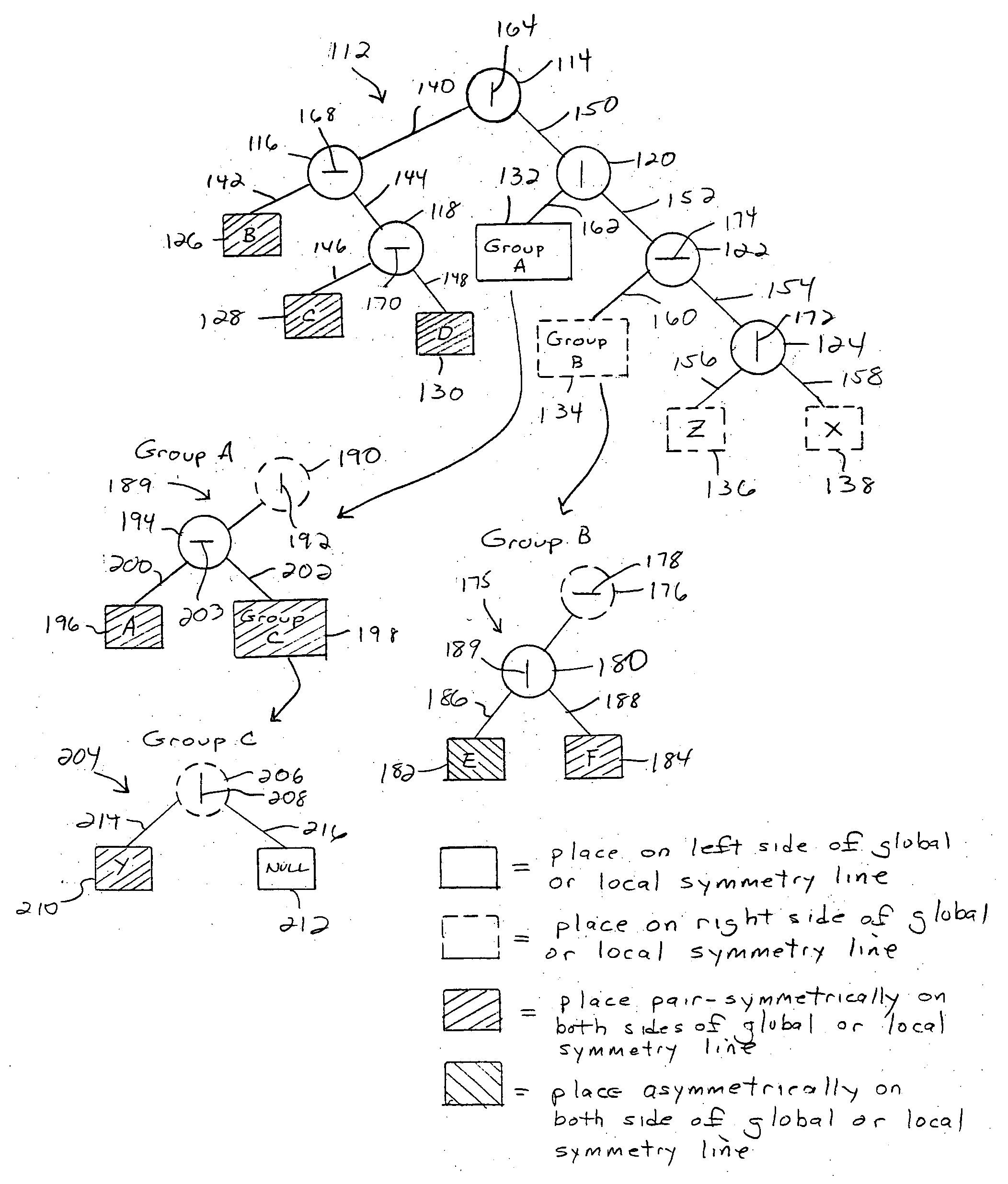
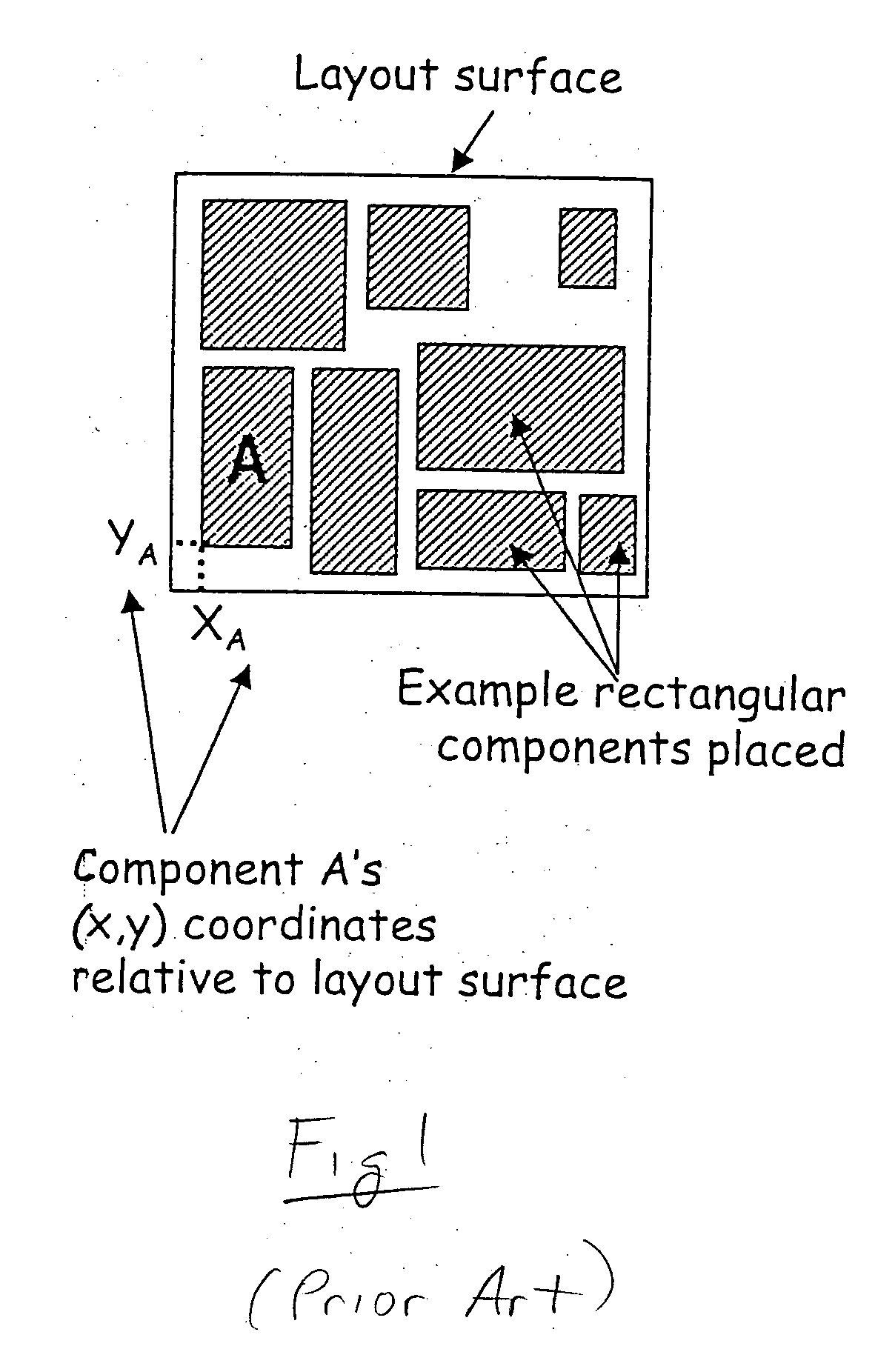
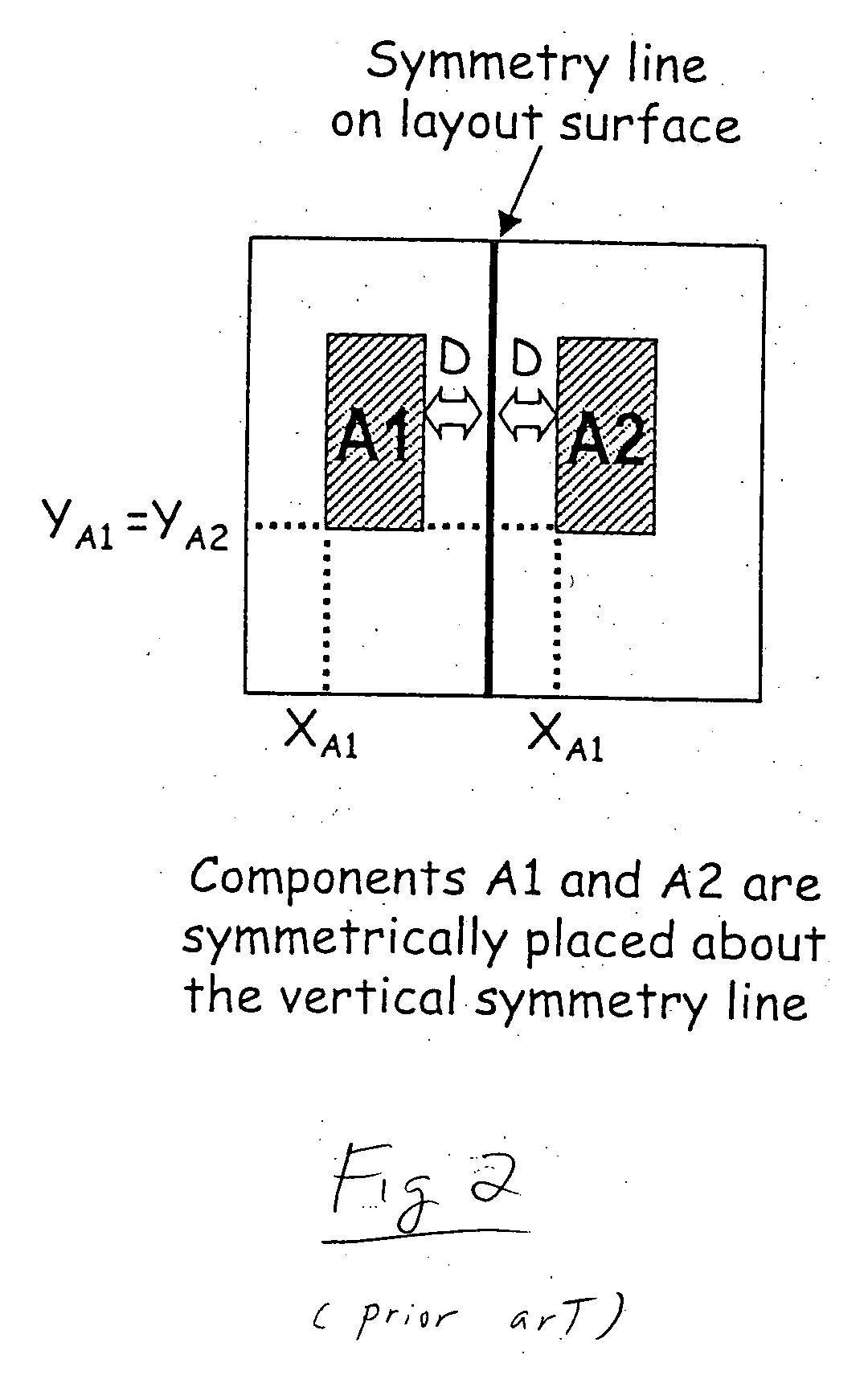
Method for generating constrained component placement for integrated circuits and packages
A method for determining component placement in a circuit includes forming a tree structure that defines the placement of each of a plurality of components associated with the tree structure on a first side, a second side or on both sides of a symmetry line, with at least one component tagged for symmetric placement on both sides of a symmetry line; performing at least one search of the tree structure to determine an initial placement of a subset of the components; and performing another search of the tree structure to determine a final placement of the subset of components whereupon at least a part of each component tagged for symmetric placement is positioned on each side of the symmetry line. The method can be embodied as instructions stored on a computer readable medium which, when executed by a processor, cause the processor to implement the method.
Owner:CADENCE DESIGN SYST INC
Procedurally expressing graphic objects for web pages
A graphics object can be expressed using procedural language embedded in a markup language document. In a embodiment, a drawing space is specified in markup language. A drawing command to arbitrarily draw a graphics object into the drawing space is specified in procedural language. Interpretation of the markup and procedural language commands results in the rendering of the arbitrary graphics object. In another embodiment, there is a browser comprising a rendering engine, an interpreter, and parser. The rendering engine is configured to interpret a markup language instruction that specifies a drawing space as well as drawing commands in procedural language for drawing an arbitrary graphic object into the drawing space. The parser can then parse the drawing commands and convert them into an execution tree of tree objects.
Owner:APPLE INC
Database kernel query optimization method based on equivalence class
ActiveCN103678589AImprove query performanceSpecial data processing applicationsExecution planQuery optimization
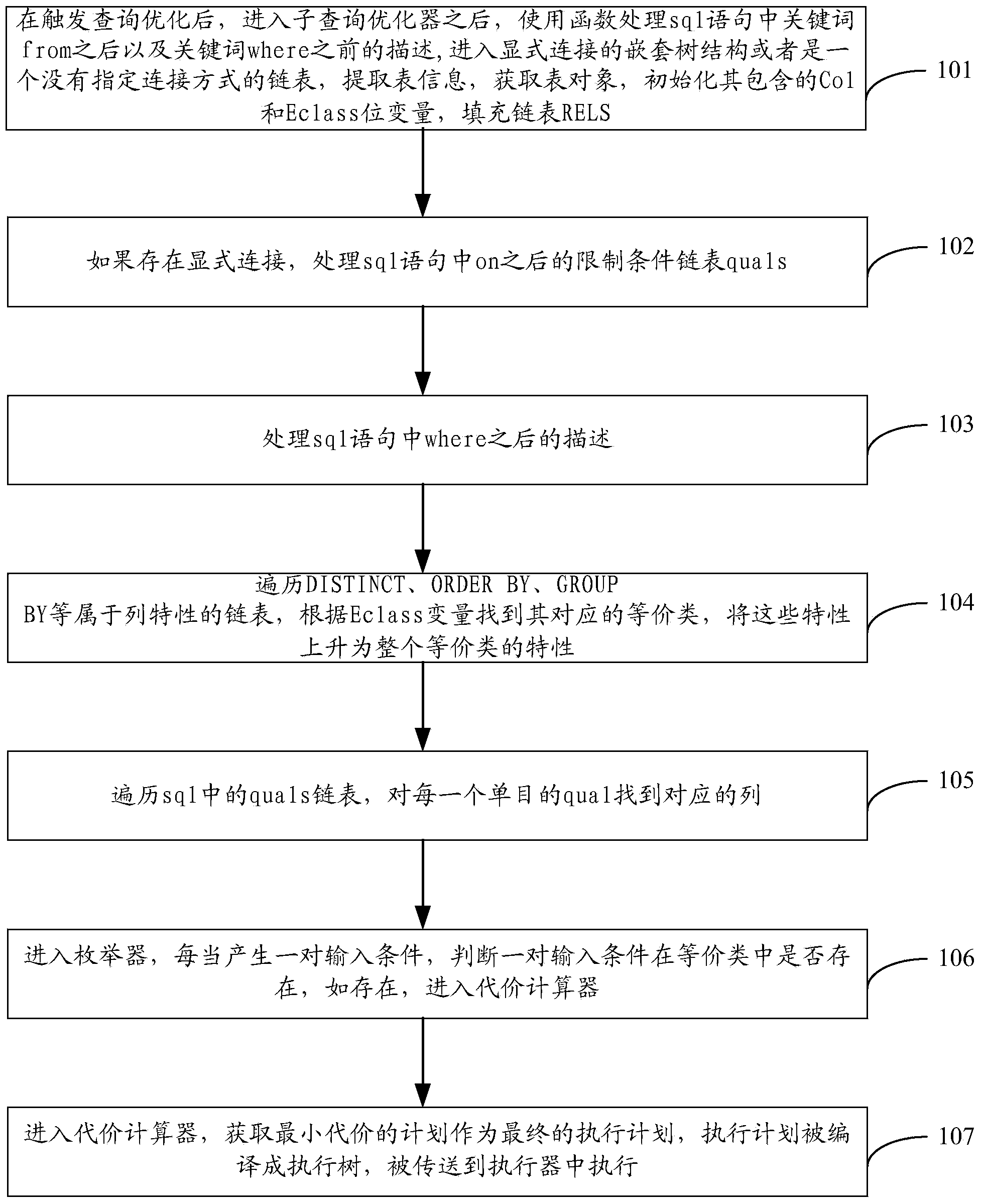
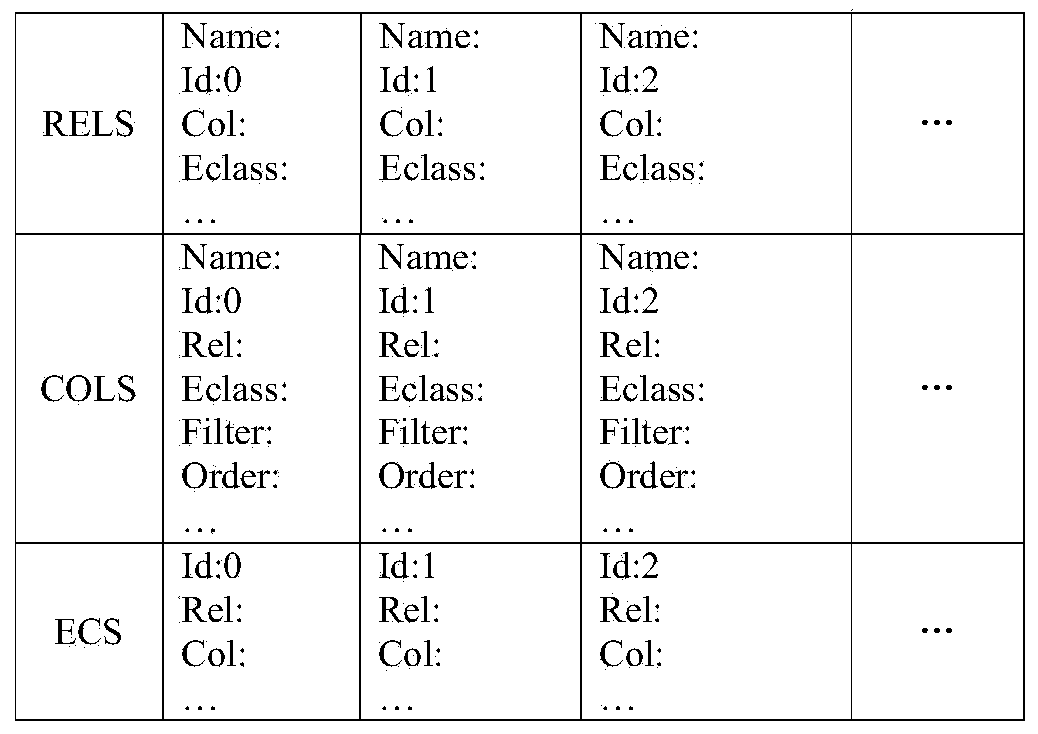
The invention belongs to the field of software, and provides a database kernel query optimization method based on an equivalence class. The method comprises the steps of using a function for processing description after the keyword 'from' and before the keyword 'where' in sql sentences after inquire statements enter a sub query optimizer, processing a nest tree structure with explicit connection or a linked list with no connection mode assigned, extracting list information, obtaining list objects, initializing the Col and Eclass bit variables contained by the list objects, and filling a linked list RELS; processing the restricted condition linked list 'quals' after the 'on' and after the 'where' in the sql sentences, and carrying out transmission on the restricted conditions according to the Eclass bit variables; entering an enumerator, enlarging planed searching space according to the Eclass bit variables, enumerating more equivalence plans, and entering a cost calculator to count cost; obtaining the plan with the minimum cost as a final execution plan, wherein the execution plan is compiled into an execution tree, and the execution plan is sent to an actuator to be executed. The database kernel query optimization method based on the equivalence class has the advantages of being high in performance.
Owner:YONYOU NETWORK TECH
Big data self-adaption topology processing method based on storm
ActiveCN105760511AAchieve dynamic customizationReach disposalSpecial data processing applicationsData streamData adaptive
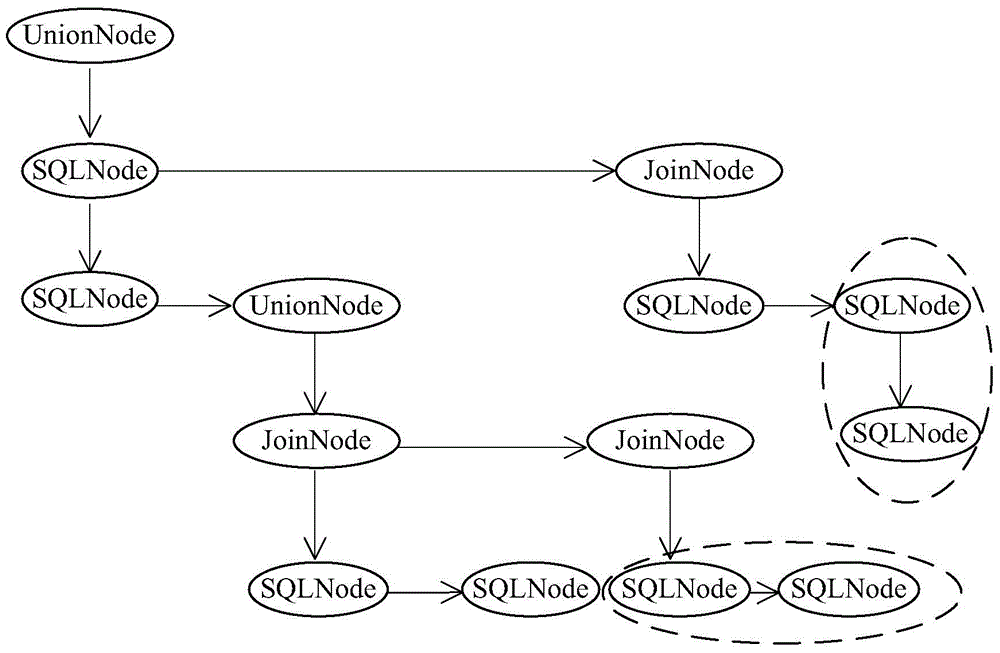
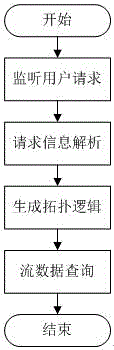
The invention provides a big data self-adaption topology processing method based on a storm.The method comprises the steps of user request monitoring, request information analyzing, topology logic generating and data flow query.Operation operator are selected according to different needs of different users by monitoring the customized service request of the users in real time, services are dynamically customized, topology logic of storm recognizable operation is generated, and therefore dynamic customizing and real-time processing of the data processing services are achieved; the corresponding operators are conveniently selected through an operator execution tree, the optimal operation execution topology meeting the customizing requests of the users is formed, the pertinence of data flow query and mining is enhanced, and the timeliness of data is guaranteed as much as possible.
Owner:南京乐图软件技术有限公司
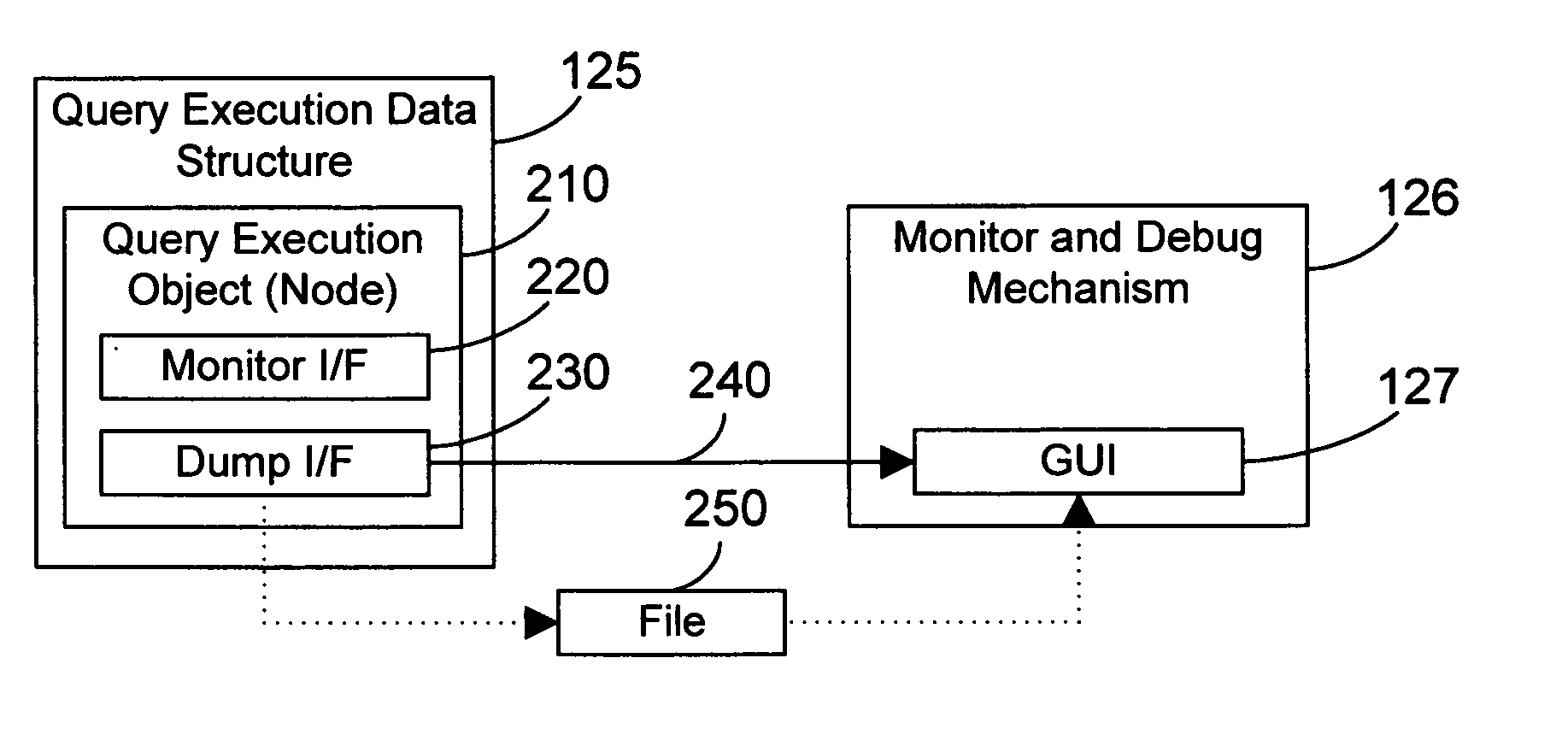
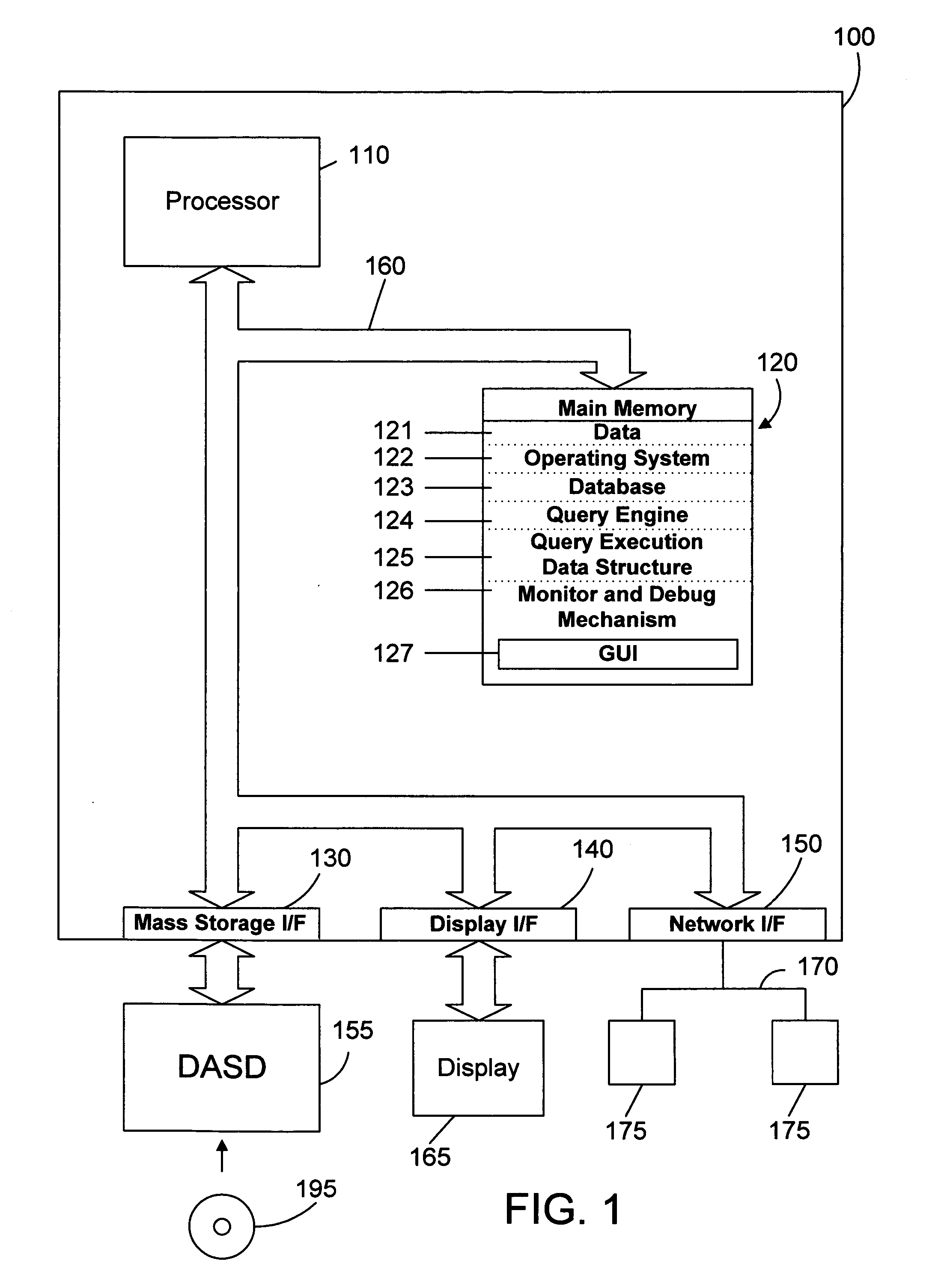
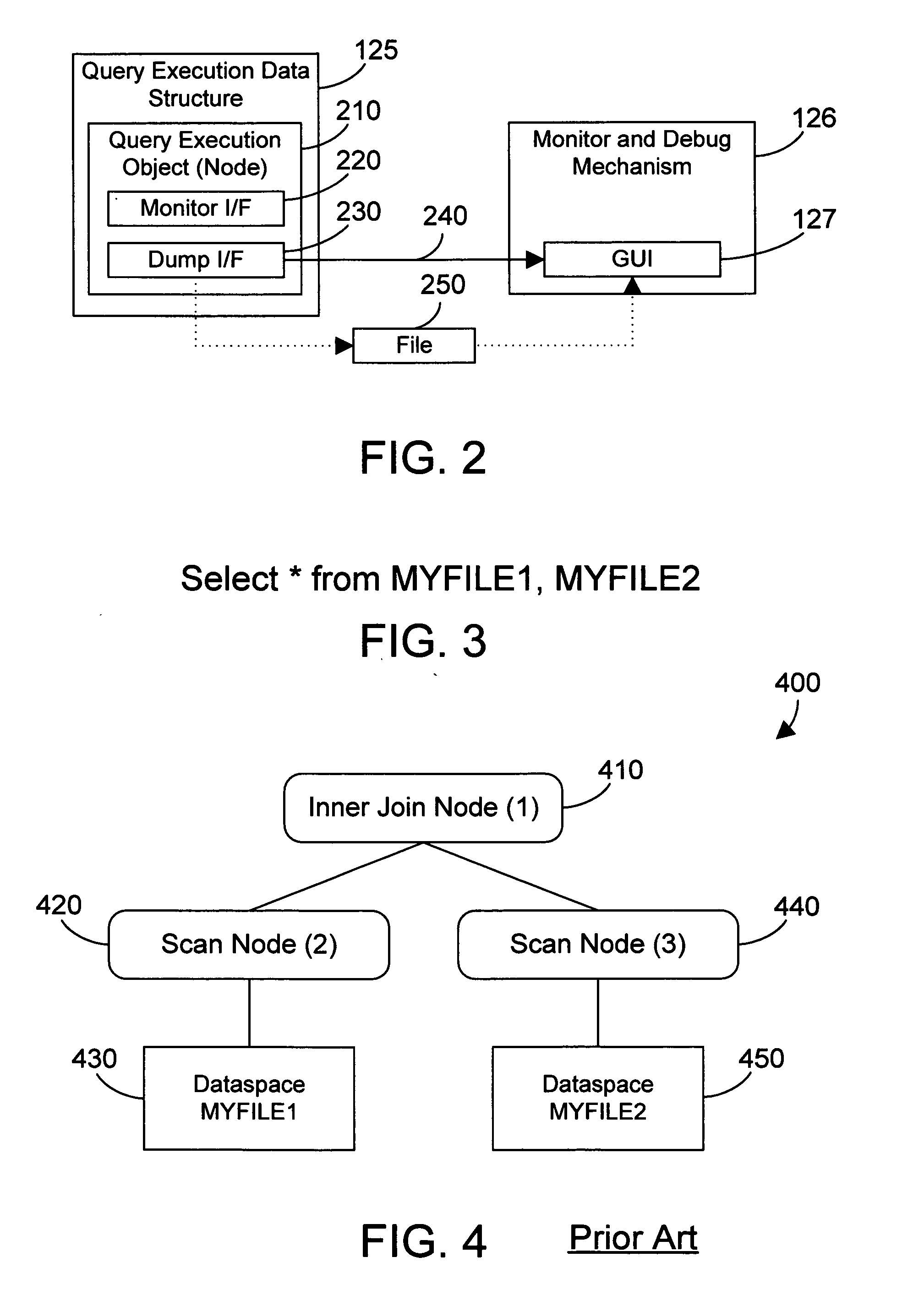
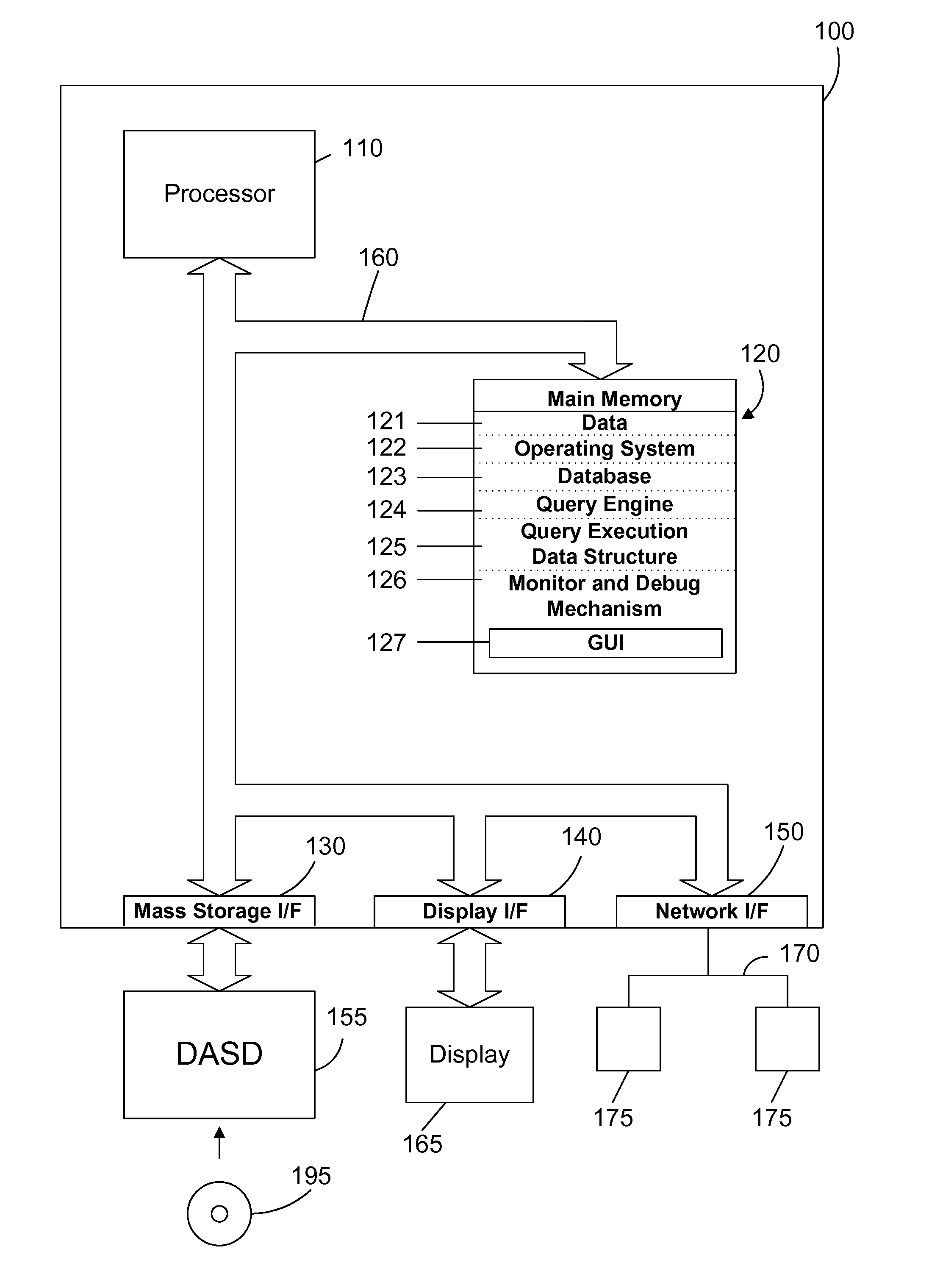
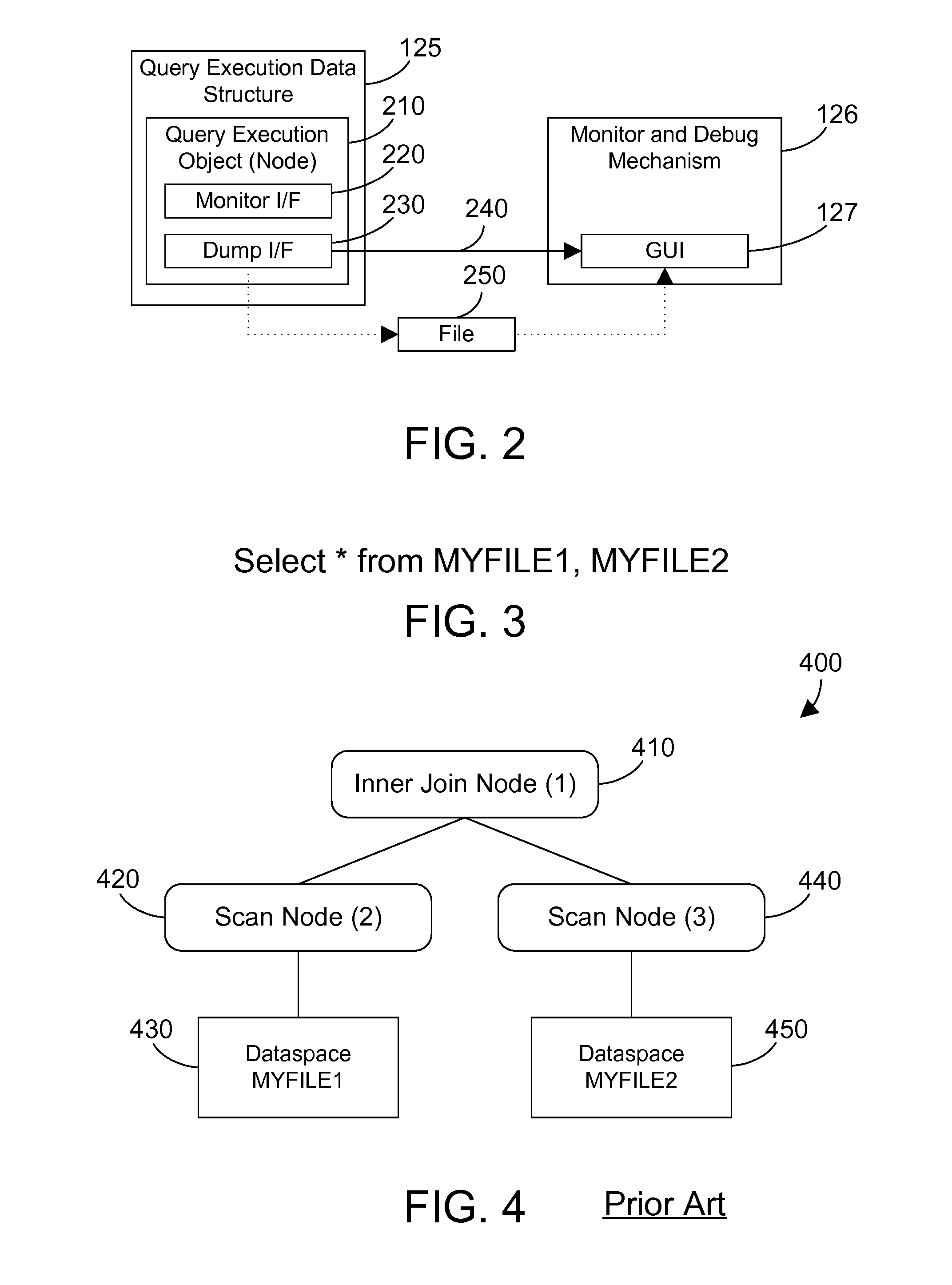
Apparatus and method for monitoring and debugging query execution objects
InactiveUS20070112737A1Efficient debuggingEffective monitoringSpecial data processing applicationsInput/output processes for data processingGraphicsGraphical user interface
Nodes in a query execution data structure have monitor and dump methods defined. The monitor method enables the collection of information from the node. The dump method outputs the monitored information from each node. A monitor and debug mechanism of the preferred embodiments includes a graphical user interface that allows a user to graphically examine a query execution tree, to enable monitoring of the nodes on a node-by-node basis, and to view information dumped from the query execution data structure as the query is executed or after the query is executed. The result is a powerful tool that allows efficiently monitoring and debugging a query implemented in an object oriented query execution data structure.
Owner:IBM CORP
Method for generating constrained component placement for integrated circuits and packages
InactiveUS20050028122A1Computer aided designSpecial data processing applicationsIntegrated circuitTheoretical computer science
A method for determining component placement in a circuit includes forming a tree structure that defines the placement of each of a plurality of components associated with the tree structure on a first side, a second side or on both sides of a symmetry line, with at least one component tagged for symmetric placement on both sides of a symmetry line; performing at least one search of the tree structure to determine an initial placement of a subset of the components; and performing another search of the tree structure to determine a final placement of the subset of components whereupon at least a part of each component tagged for symmetric placement is positioned on each side of the symmetry line. The method can be embodied as instructions stored on a computer readable medium which, when executed by a processor, cause the processor to implement the method.
Owner:CADENCE DESIGN SYST INC
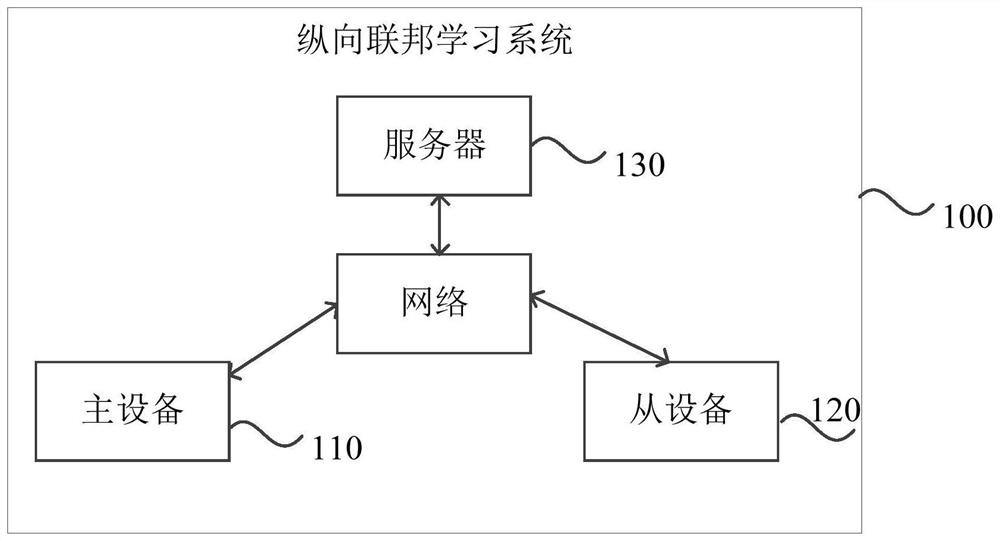
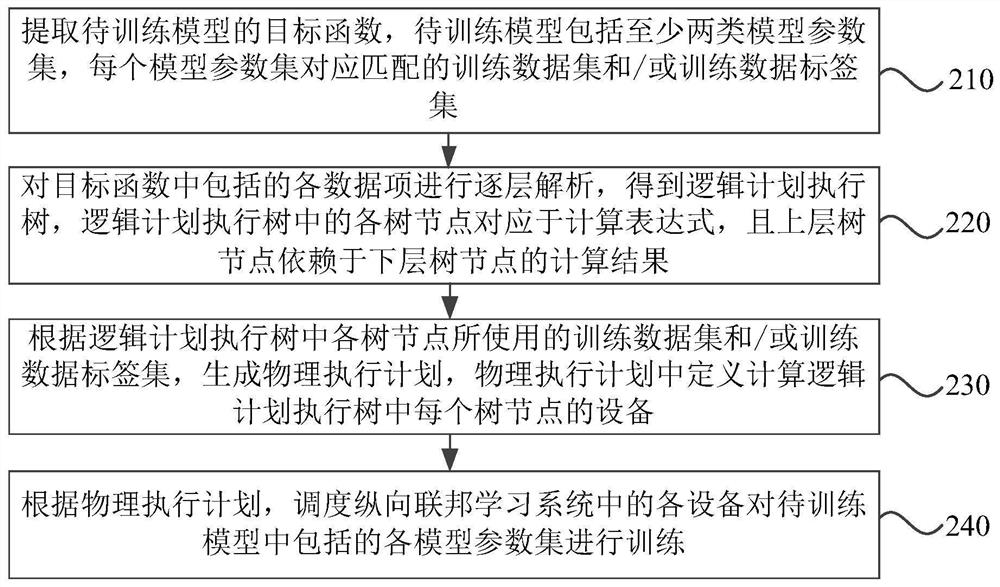
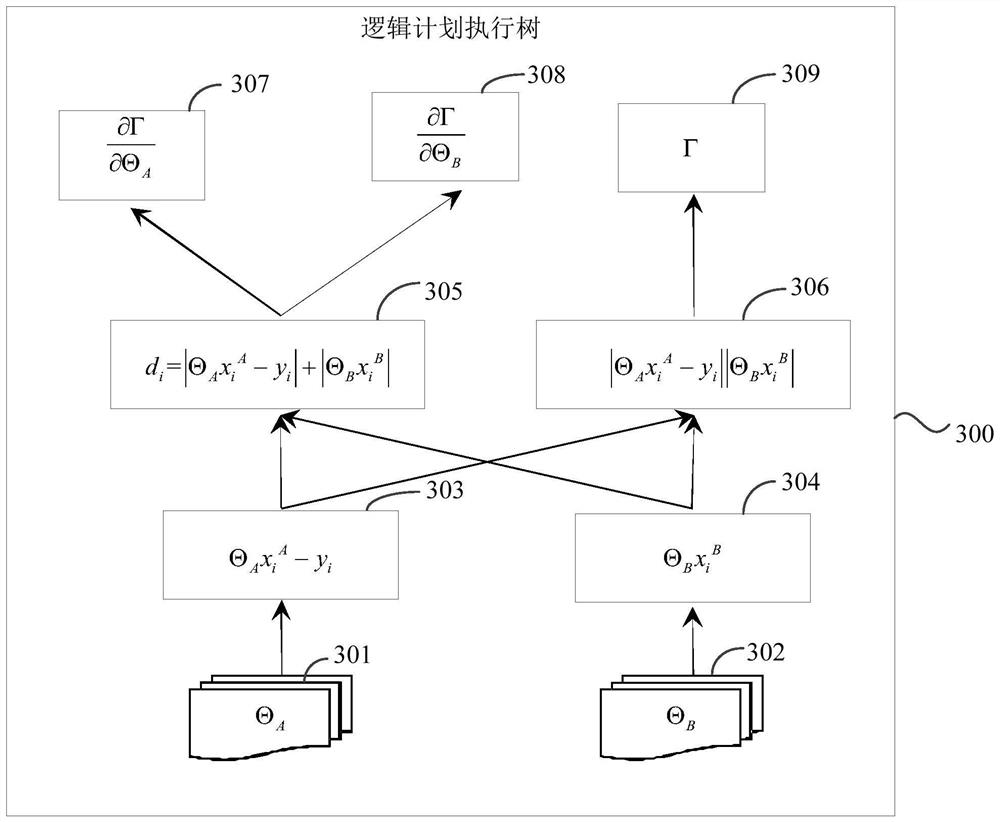
Model training method and device based on longitudinal federated learning system and storage medium
The embodiment of the invention discloses a model training method and device based on a longitudinal federated learning system and a storage medium. The method comprises: executing an objective function of a model to be trained, wherein the model to be trained comprises at least two types of model parameter sets, and each model parameter set corresponds to a matched training data set and / or training data label set; analyzing each data item included in the target function layer by layer to obtain a logic plan execution tree; generating a physical execution plan according to the training data set and / or the training data label set used by each tree node in the logic plan execution tree; and according to the physical execution plan, scheduling each device in the longitudinal federated learning system to train each model parameter set included in the to-be-trained model. According to the scheme of the embodiment of the invention, the model training process of longitudinal federation learning does not need to be customized and developed manually, and the model training process based on a longitudinal federation learning system is simplified.
Owner:TRANSWARP INFORMATION TECH SHANGHAI
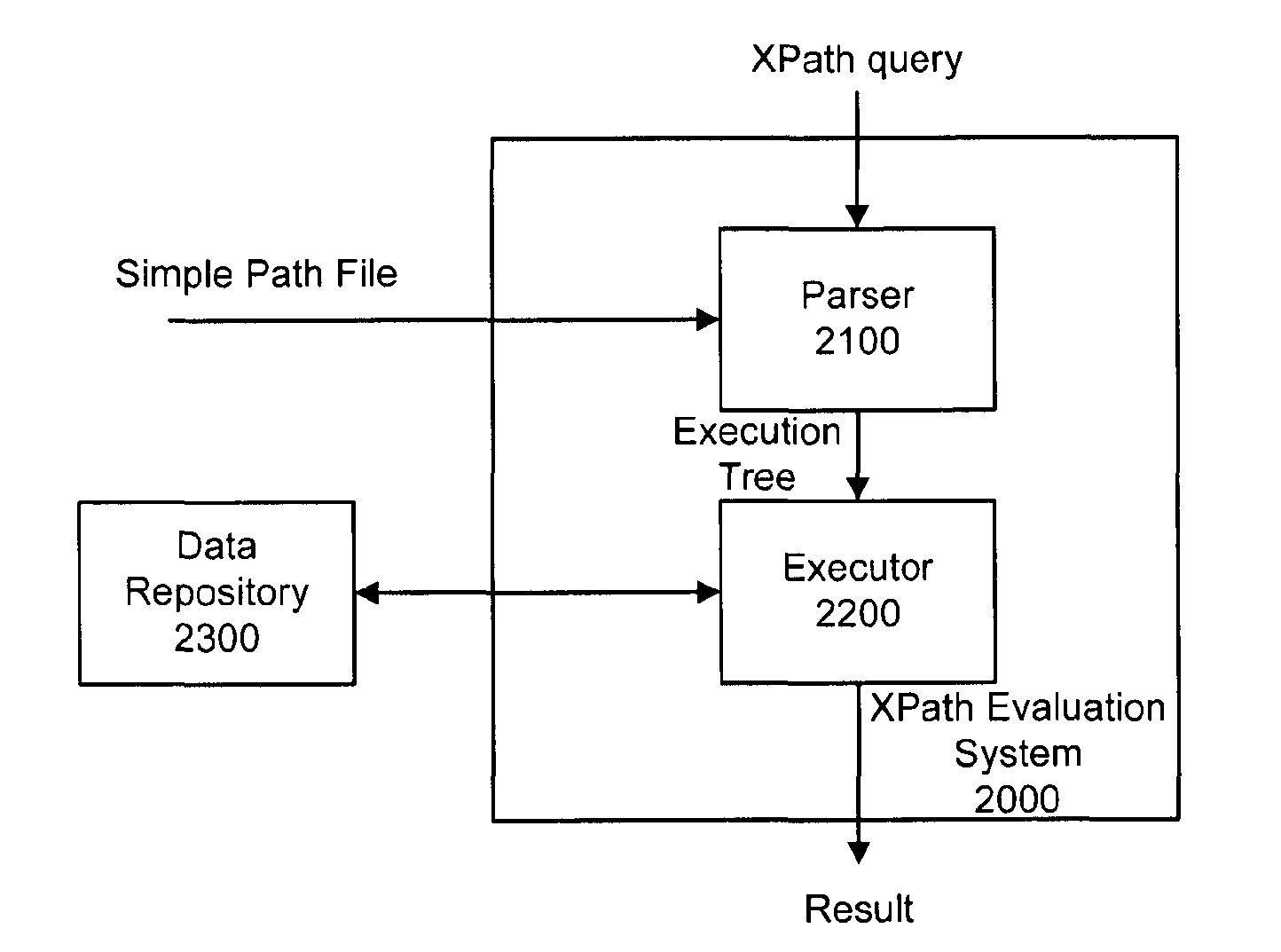
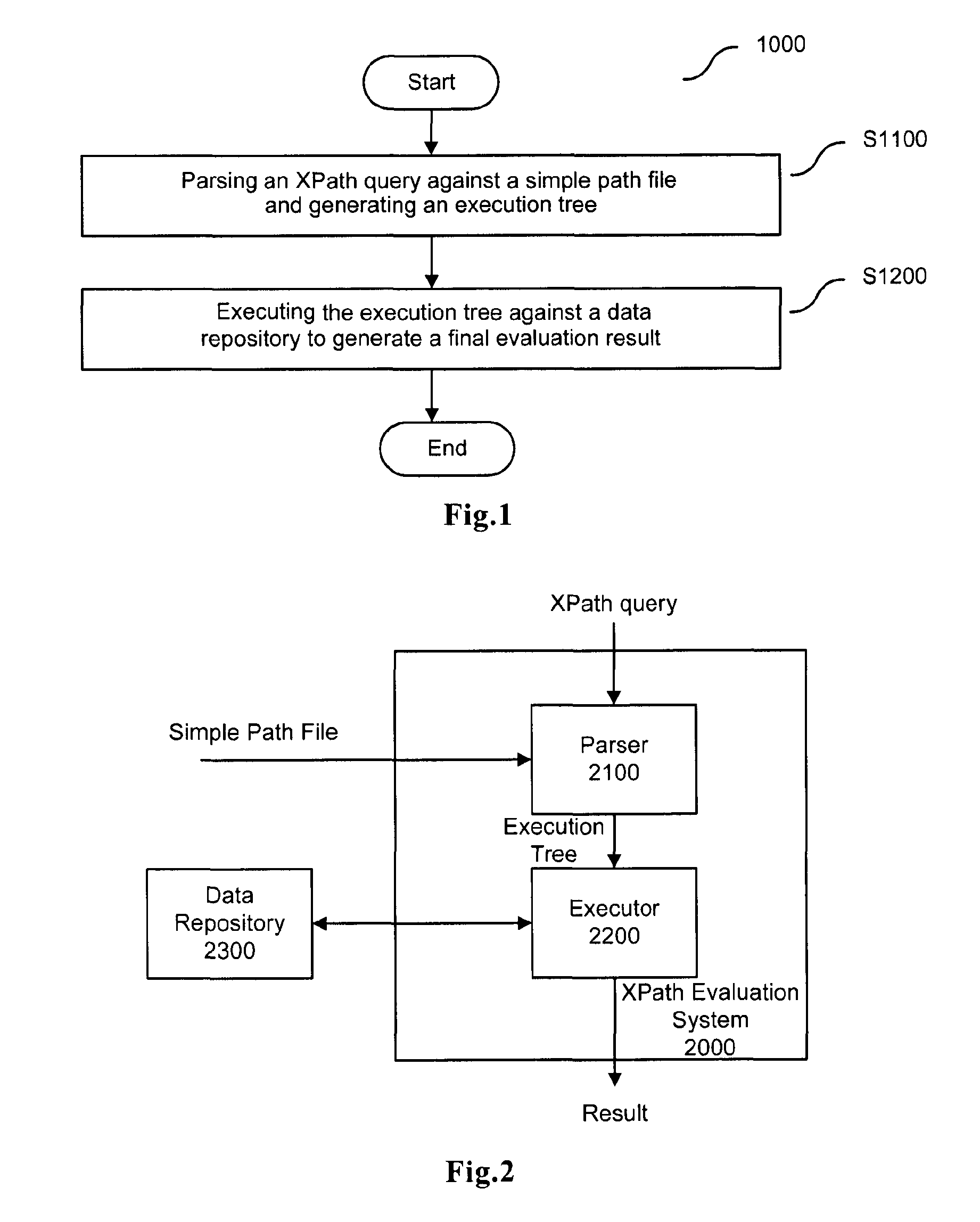
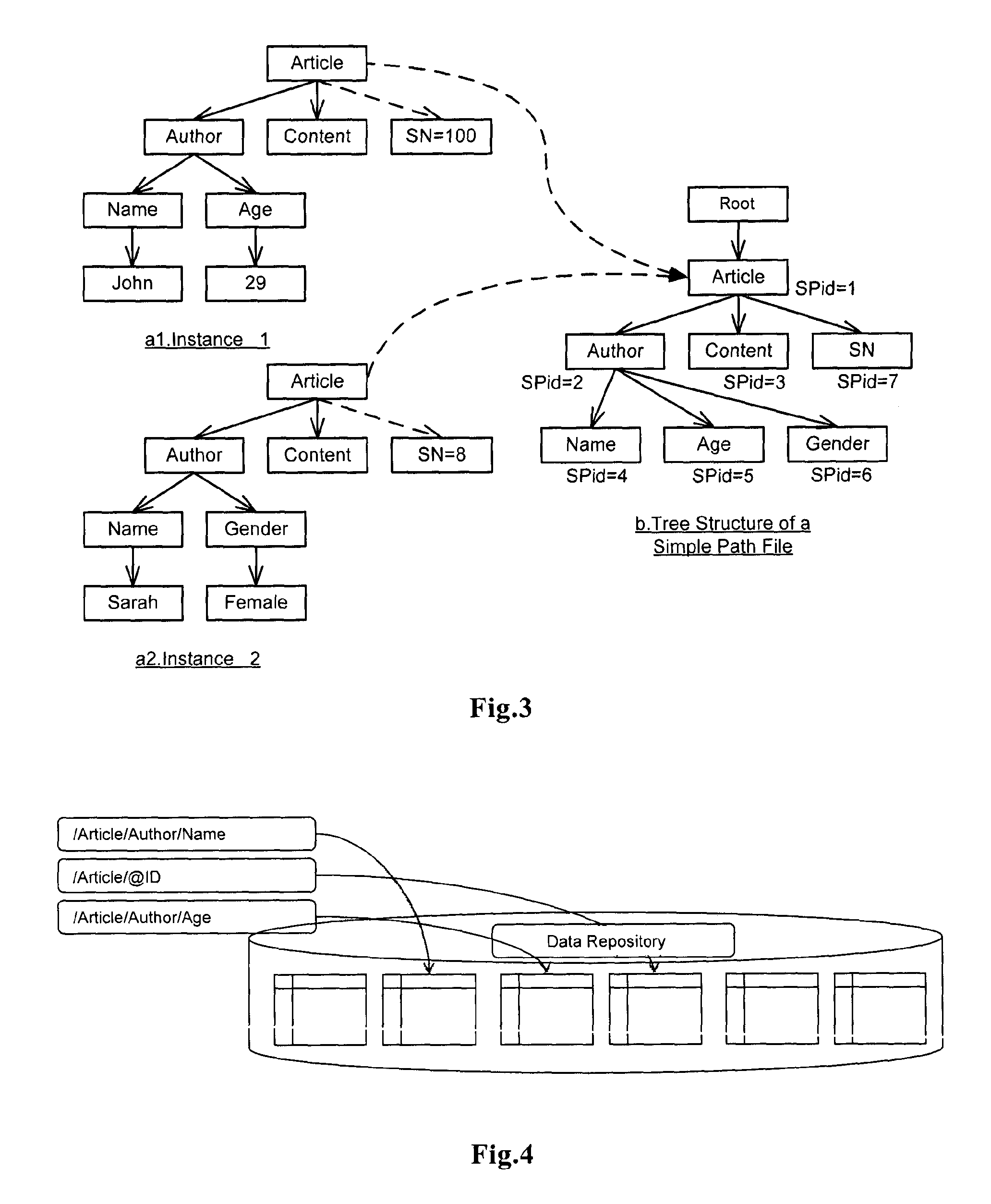
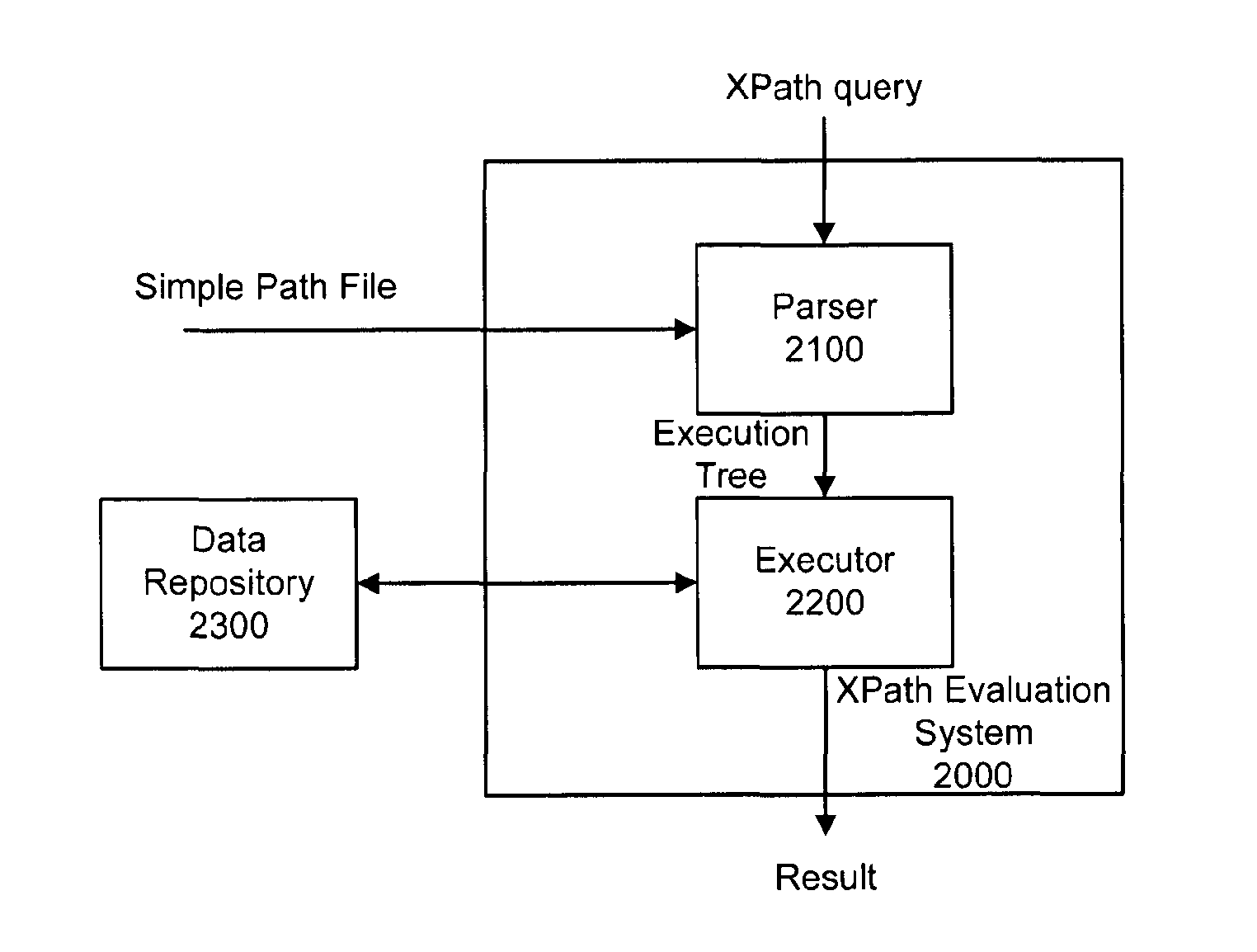
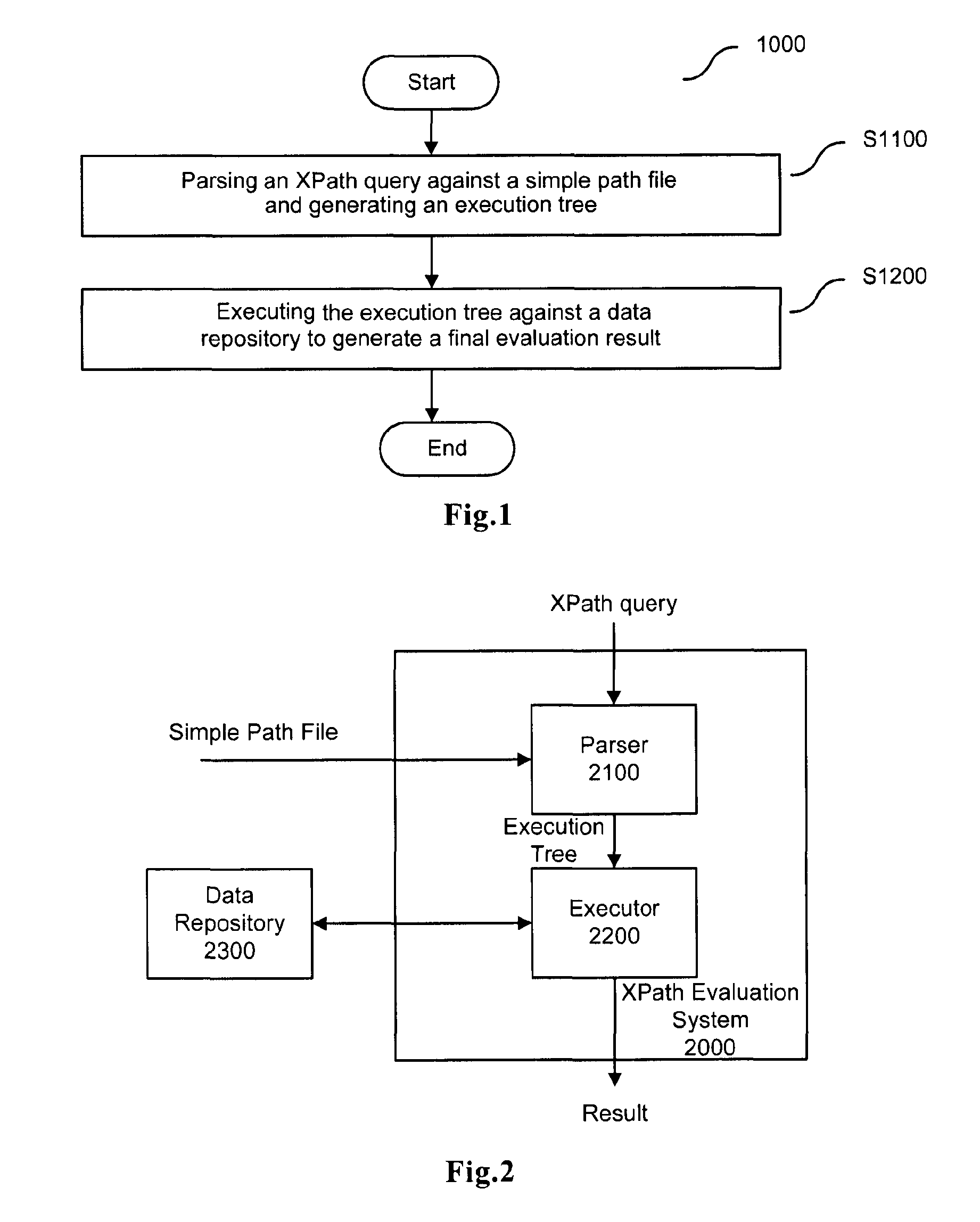
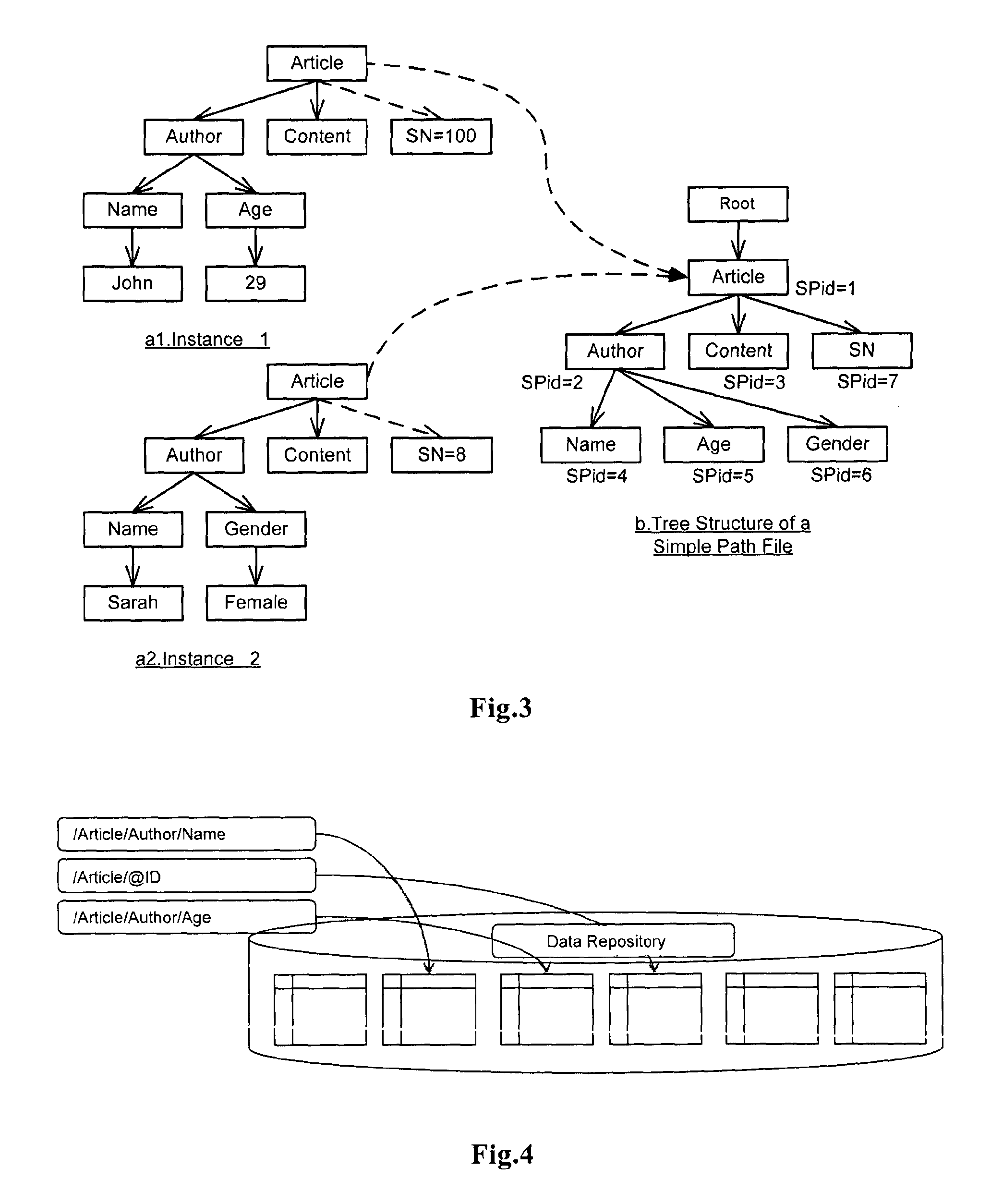
Xpath evaluation in an XML repository
ActiveUS20110078186A1Save computing resourcesImprove efficiencyDatabase updatingDigital data processing detailsXPathData store
XPath evaluation in an XML data repository includes parsing an input XPath query using a simple path file to generate an execution tree about the XPath query, where the simple path file includes an XML file that is generated based on the hierarchical architecture of a plurality of XML files in the data repository, and the names of the nodes in the generated XML file are generated by recording the tag information of respective nodes in the plurality of XML files in the data repository. Execution of an execution tree for the data repository generates a final evaluation result.
Owner:IBM CORP
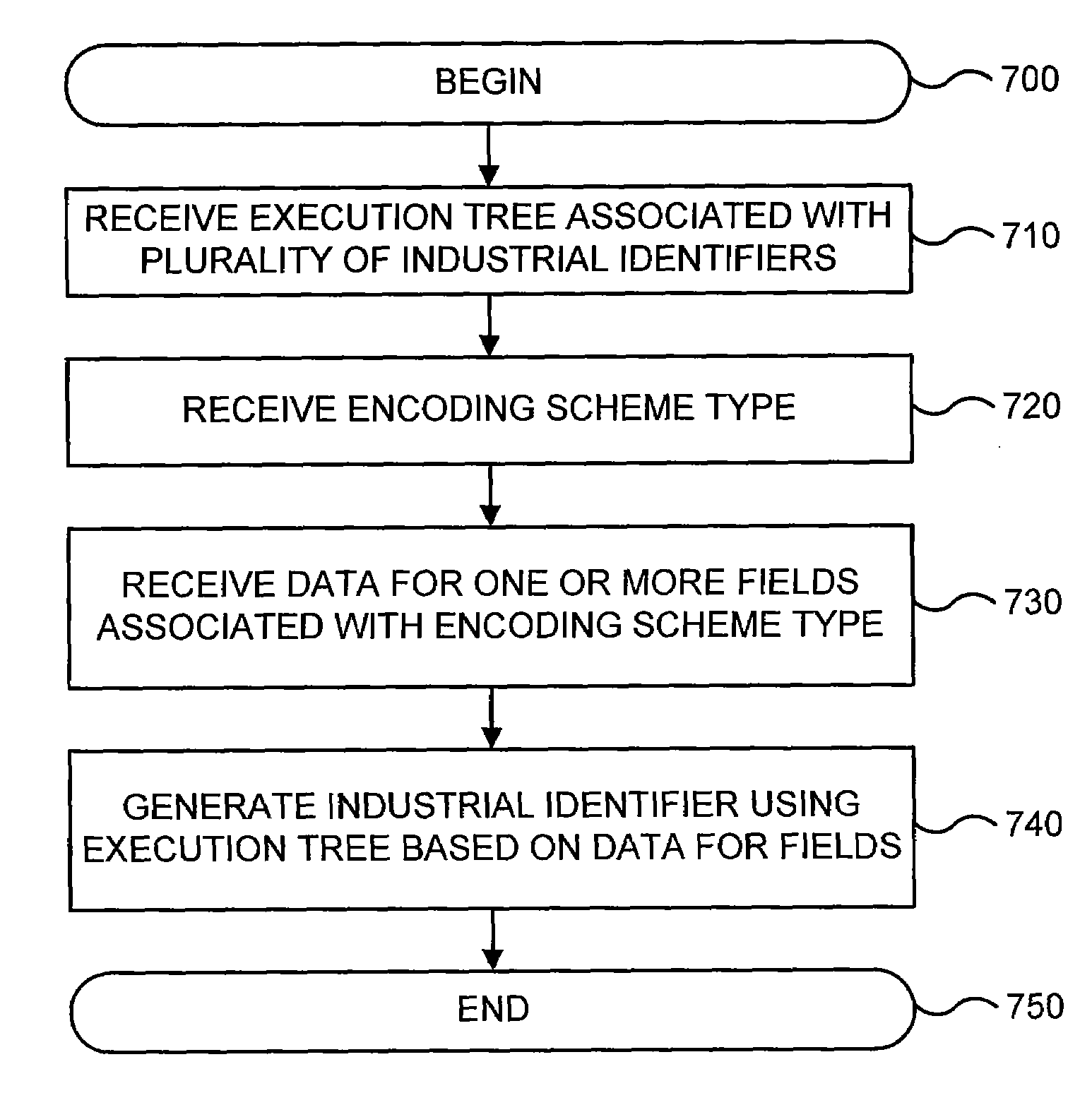
Industrial identify encoding and decoding language
In various embodiments, a method for processing industrial identifiers includes receiving unstructured data. An encoding scheme is determined for the unstructured data based on an execution tree associated with a plurality of industrial identifiers. The encoding scheme is then output to an application. Data may be received for one or more fields associated with one of the plurality of industrial identifiers. An industrial identifier may be generated based on the execution tree in response to the data.
Owner:ORACLE INT CORP
Method and apparatus for optimizing the evaluation of semantic web queries
A semantic query over an RDF database is received with RDF database statistics and access methods for evaluating triple patterns in the query. The semantic query is expressed as a parse tree containing triple patterns and logical relationships among the triple patterns. The parse tree and access methods create a data flow graph containing a plurality of triple pattern and access method pair nodes connected by a plurality of edges, and an optimal flow tree through the data flow graph is determined such that costs are minimized and all triple patterns in the semantic query are contained in the optimal flow tree. A structure independent execution tree defining a sequence of evaluation through the optimal flow tree is created and is transformed into a database structure dependent query plan. This is used to create an SQL query that is used to evaluate the semantic query over the RDF database.
Owner:IBM CORP
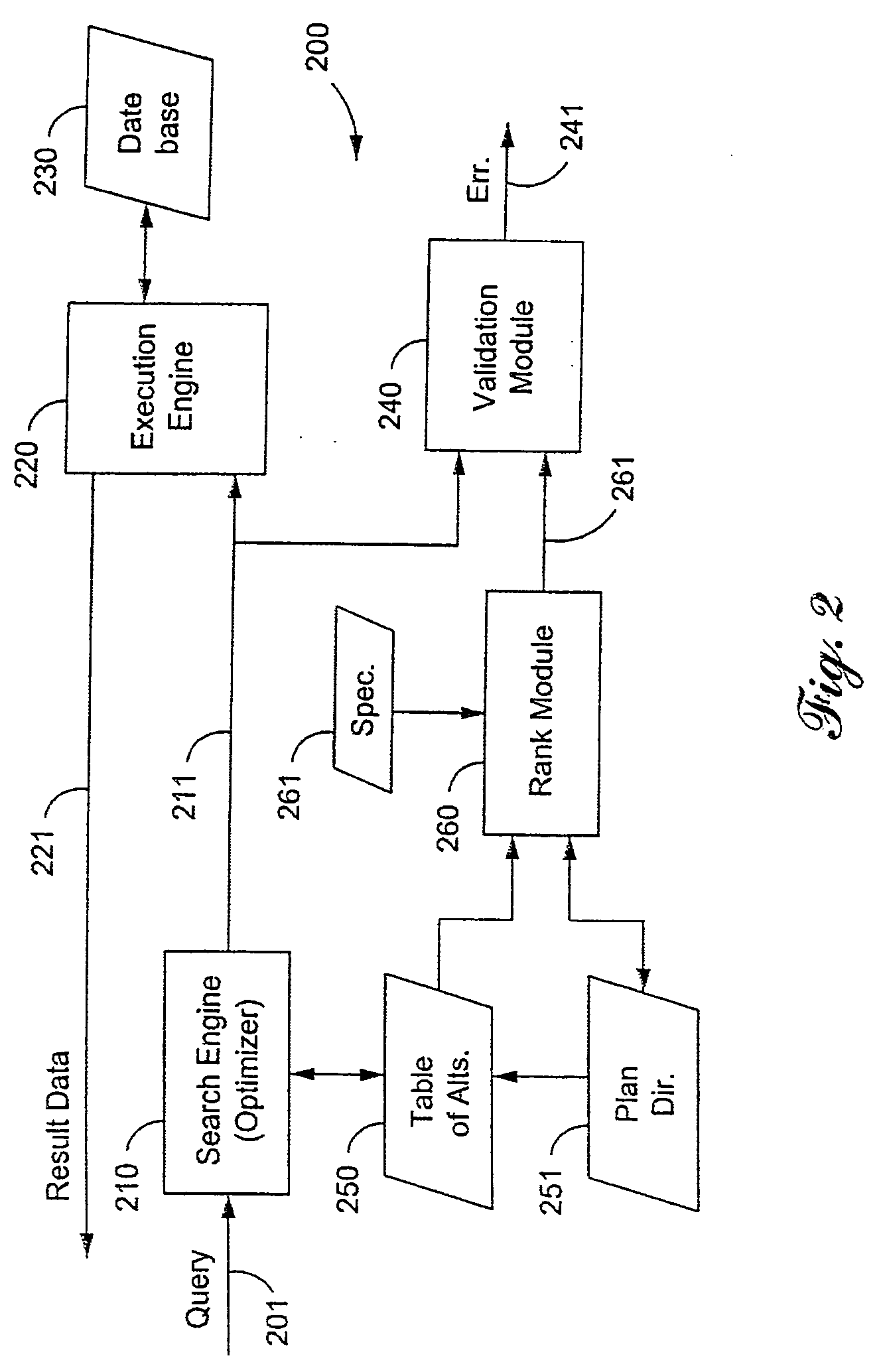
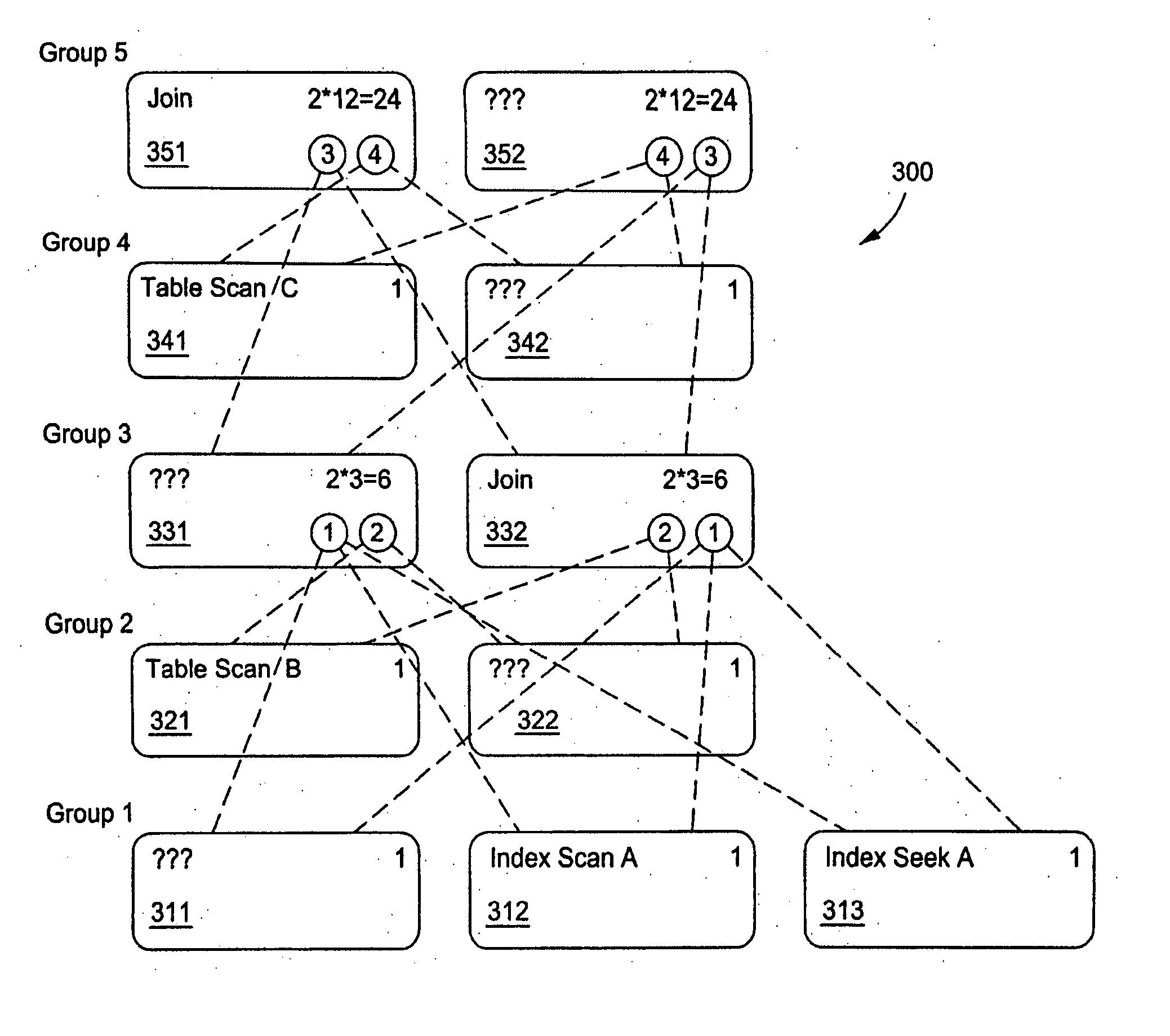
Validating multiple execution plans for database queries
InactiveUS20050267874A1Data processing applicationsDigital data information retrievalExecution planData structure
Validation of large numbers of alternative execution plans for a database query, either an exhaustive enumeration of the complete space of alternatives, or else an unbiased random sample, is performed by efficiently constructing execution trees from a data structure having groups alternative operators that are ranked in a directory. Each global rank of a plan identifies that plan uniquely among all the alternative plans. The operators are unranked from the directory according to a specification that characterizes the desired plans.
Owner:MICROSOFT TECH LICENSING LLC
XPath evaluation in an XML repository
InactiveUS9135367B2Save computing resourcesImprove efficiencyDatabase updatingDigital data processing detailsXPathData store
XPath evaluation in an XML data repository includes parsing an input XPath query using a simple path file to generate an execution tree about the XPath query, where the simple path file includes an XML file that is generated based on the hierarchical architecture of a plurality of XML files in the data repository, and the names of the nodes in the generated XML file are generated by recording the tag information of respective nodes in the plurality of XML files in the data repository. Execution of an execution tree for the data repository generates a final evaluation result.
Owner:INT BUSINESS MASCH CORP
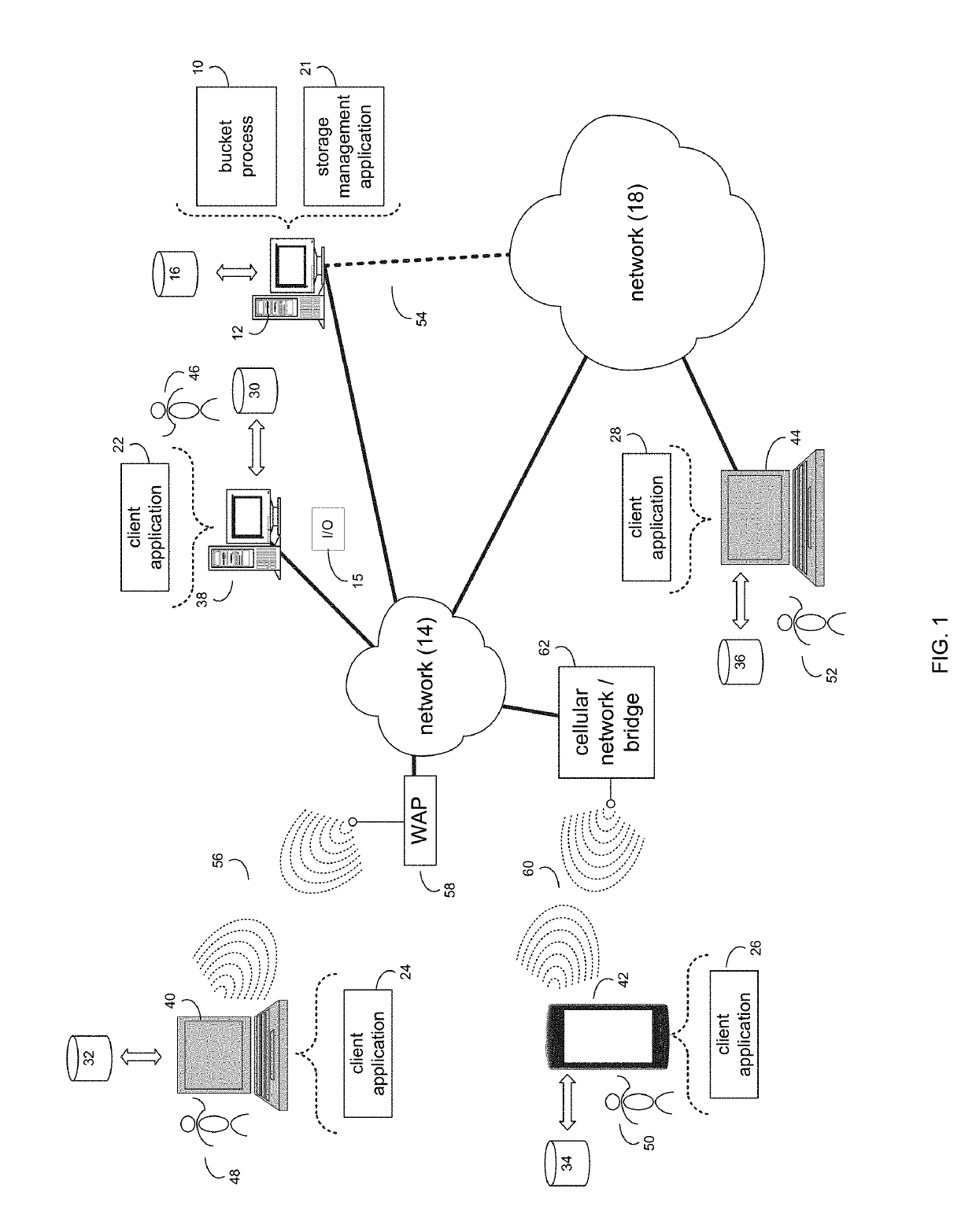
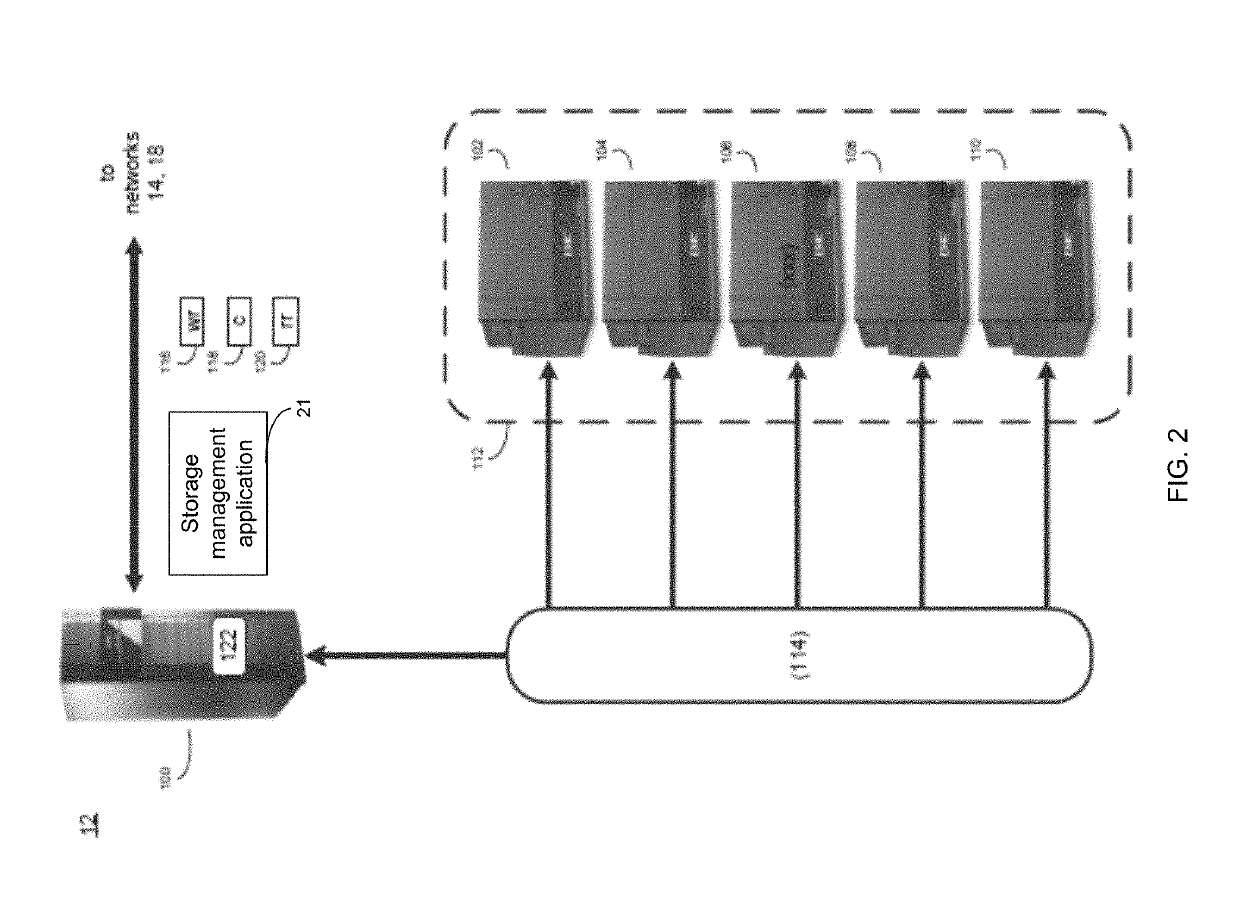
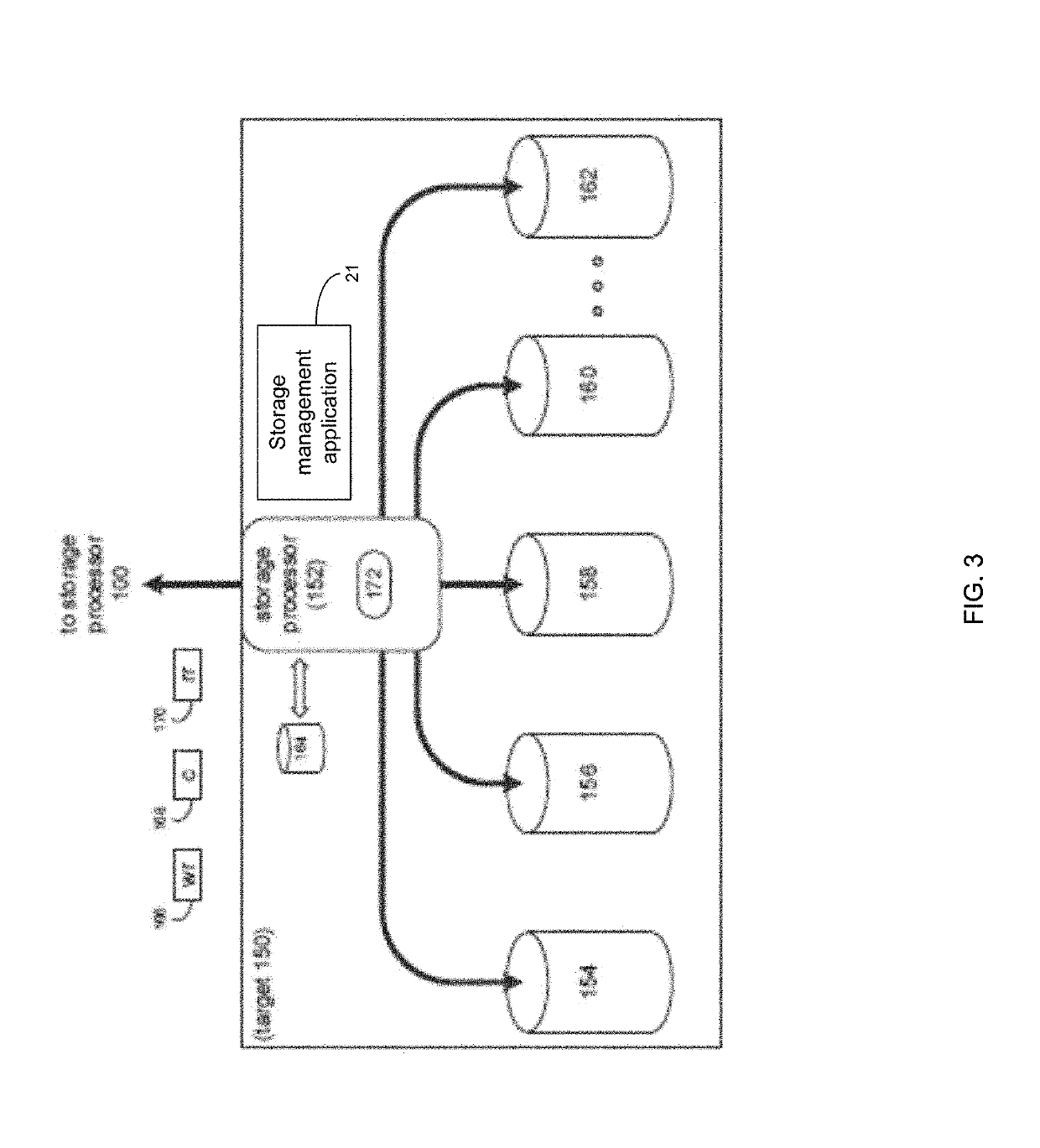
System and method accelerated random write layout for bucket allocation with in hybrid storage systems
ActiveUS10540114B2Memory architecture accessing/allocationInput/output to record carriersParallel computingEngineering
A method, computer program product, and computer system for receiving, by a computing device, an I / O request. A bucket for the I / O request may be allocated. An offset and mapping information of the I / O request may be written into a log. The offset and mapping information of the I / O request may be written into a tree structure. Garbage collection for the tree structure may be executed to reuse the bucket.
Owner:EMC IP HLDG CO LLC
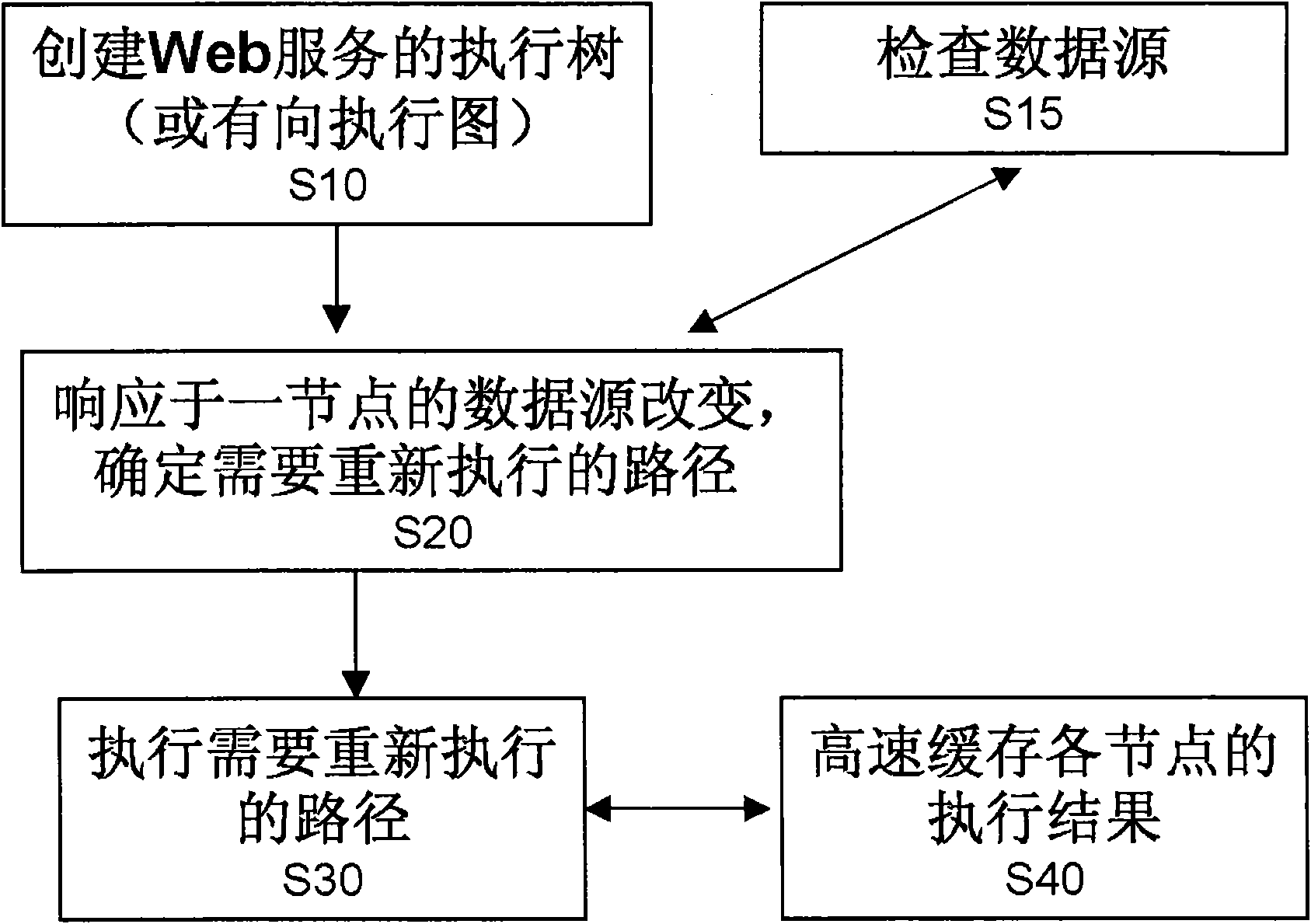
Method and system for executing data stream of Web service
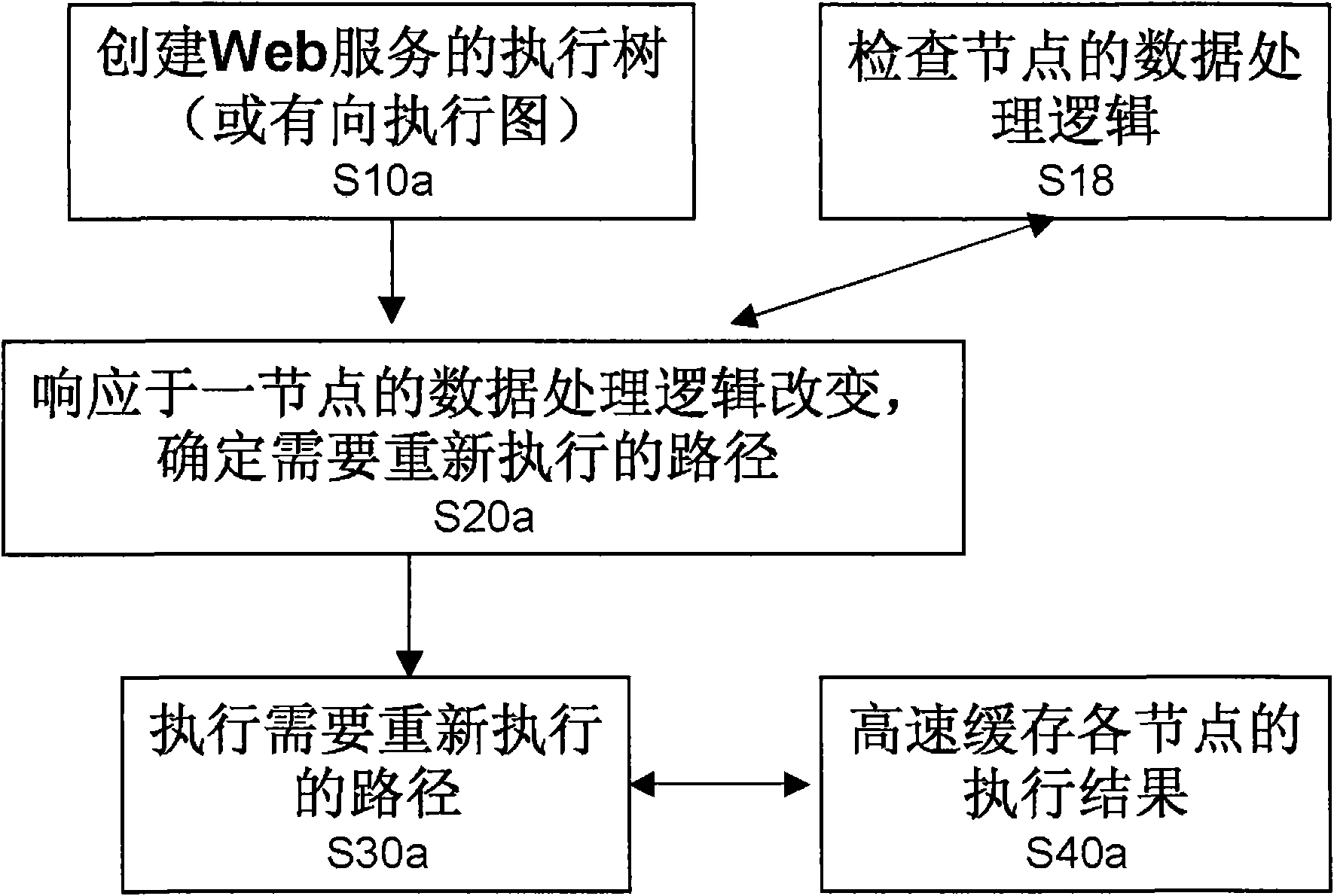
InactiveCN101616070AExecution path reductionImprove acceleration performanceData switching networksData streamWeb service
The invention provides a method and a system for executing a data stream of a Web service. The method comprises the following steps: creating an execution tree of the Web service; responding to the change of a data source of a node or responding to the change of the data processing logic of a node and determining a changed path so as to determine a path requiring to be renewedly executed; executing the path requiring to be renewedly executed, wherein the execution tree comprises a plurality of execution paths, and each execution path comprises a plurality of nodes and connections among the nodes. Once the execution tree is created, when the data stream requires to be renewedly operated next time, if the execution path of the data stream is not changed, for example the place for receiving data of a node is not changed, only the data source is changed or the data processing logic is changed, the execution tree does not need to be renewedly created according to the method and the system, but the execution paths can be reduced.
Owner:IBM CORP
Apparatus and method for monitoring and debugging query execution objects
ActiveUS20080148103A1Efficient debuggingEffective monitoringHardware monitoringSpecial data processing applicationsGraphicsGraphical user interface
Nodes in a query execution data structure have monitor and dump methods defined. The monitor method enables the collection of information from the node. The dump method outputs the monitored information from each node. A monitor and debug mechanism of the preferred embodiments includes a graphical user interface that allows a user to graphically examine a query execution tree, to enable monitoring of the nodes on a node-by-node basis, and to view information dumped from the query execution data structure as the query is executed or after the query is executed. The result is a powerful tool that allows efficiently monitoring and debugging a query implemented in an object oriented query execution data structure.
Owner:IBM CORP
Validating multiple execution plans for database queries
InactiveUS20050149492A1Data processing applicationsDigital data information retrievalExecution planData structure
Validation of large numbers of alternative execution plans for a database query, either an exhaustive enumeration of the complete space of alternatives, or else an unbiased random sample, is performed by efficiently constructing execution trees from a data structure having groups alternative operators that are ranked in a directory. Each global rank of a plan identifies that plan uniquely among all the alternative plans. The operators are unranked from the directory according to a specification that characterizes the desired plans.
Owner:MICROSOFT TECH LICENSING LLC
A static detection method for state-related defects in a large-scale system
ActiveCN109710538AHigh precisionAccurate calculationSoftware testing/debuggingGeneration processState dependent
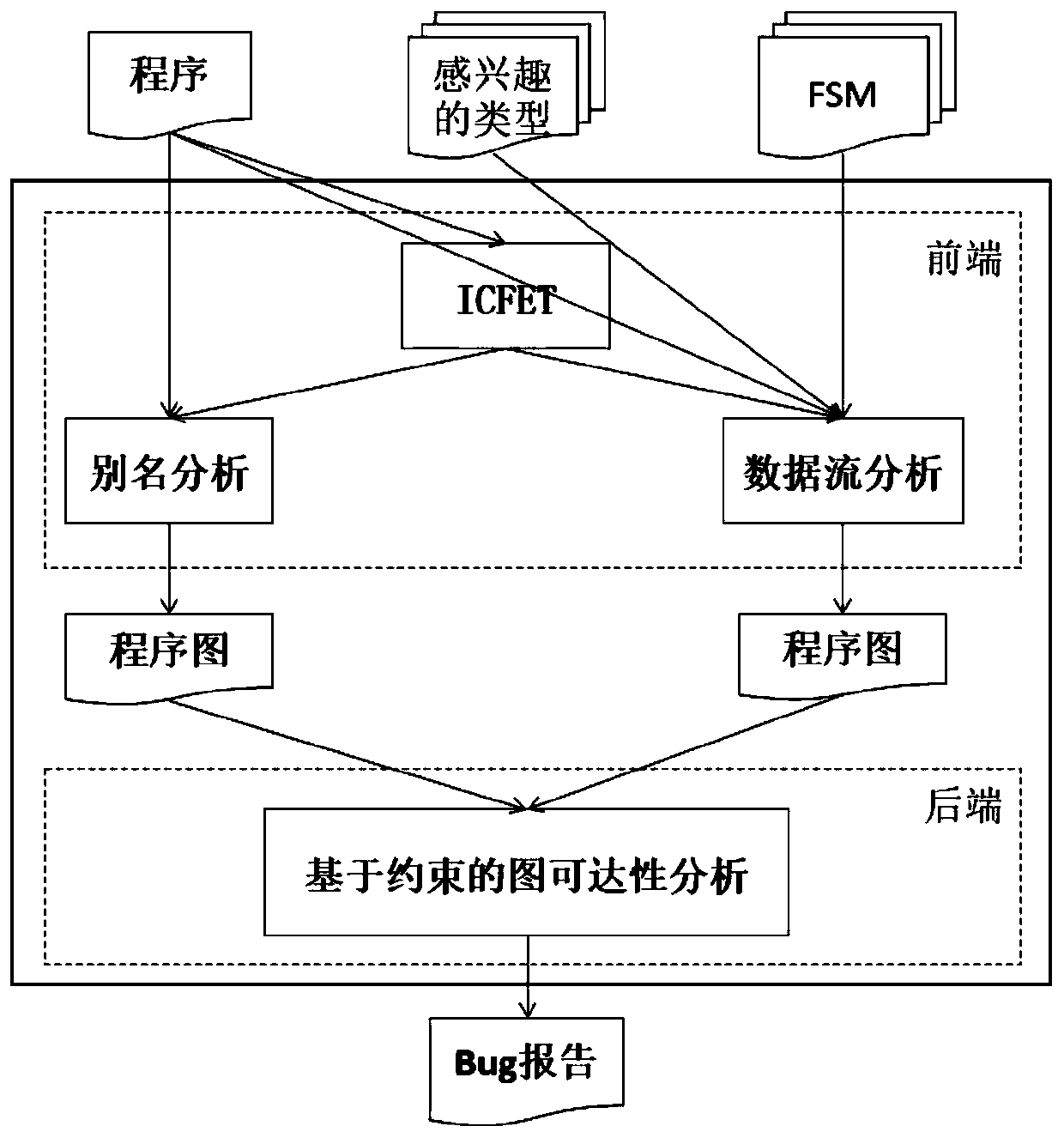
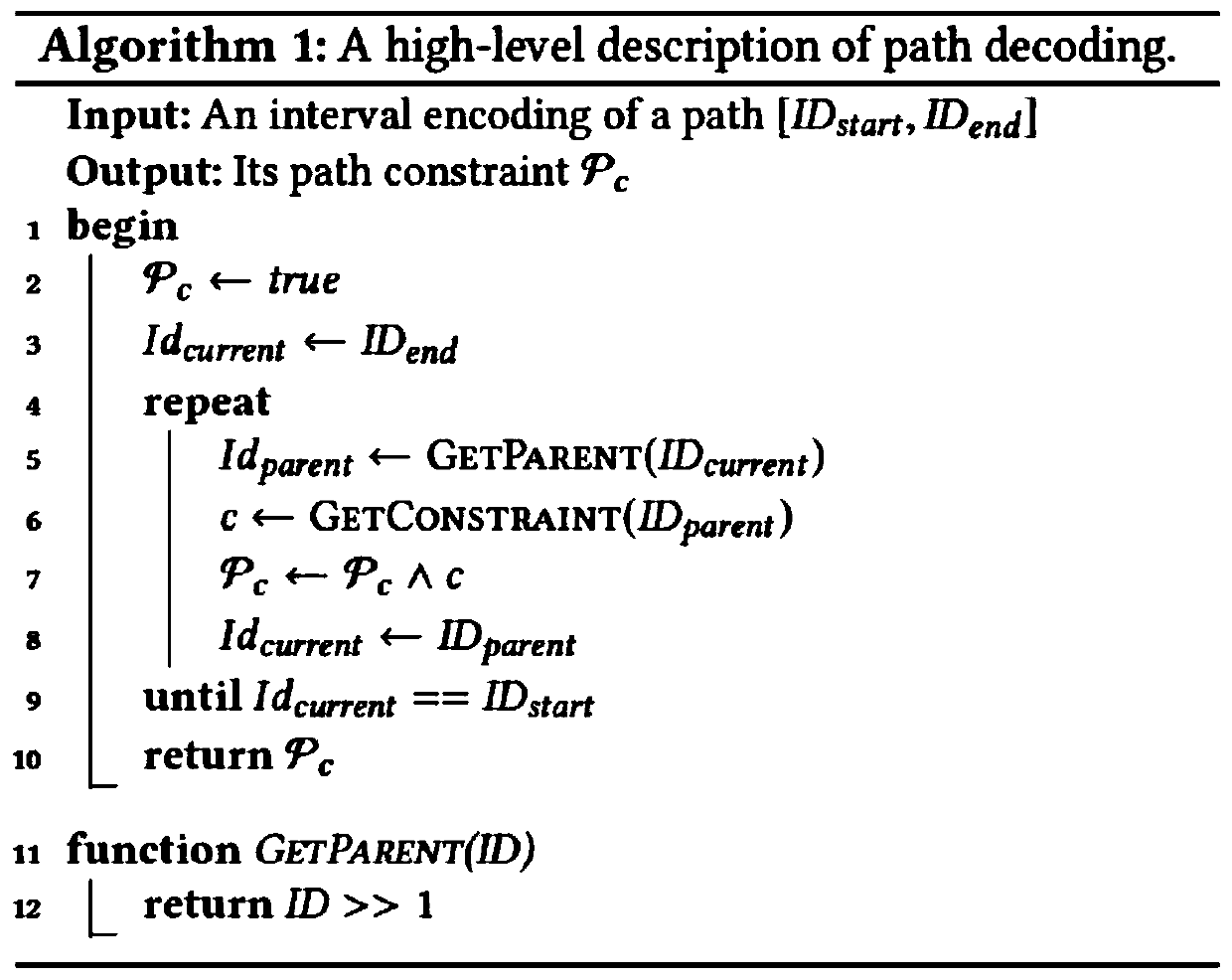
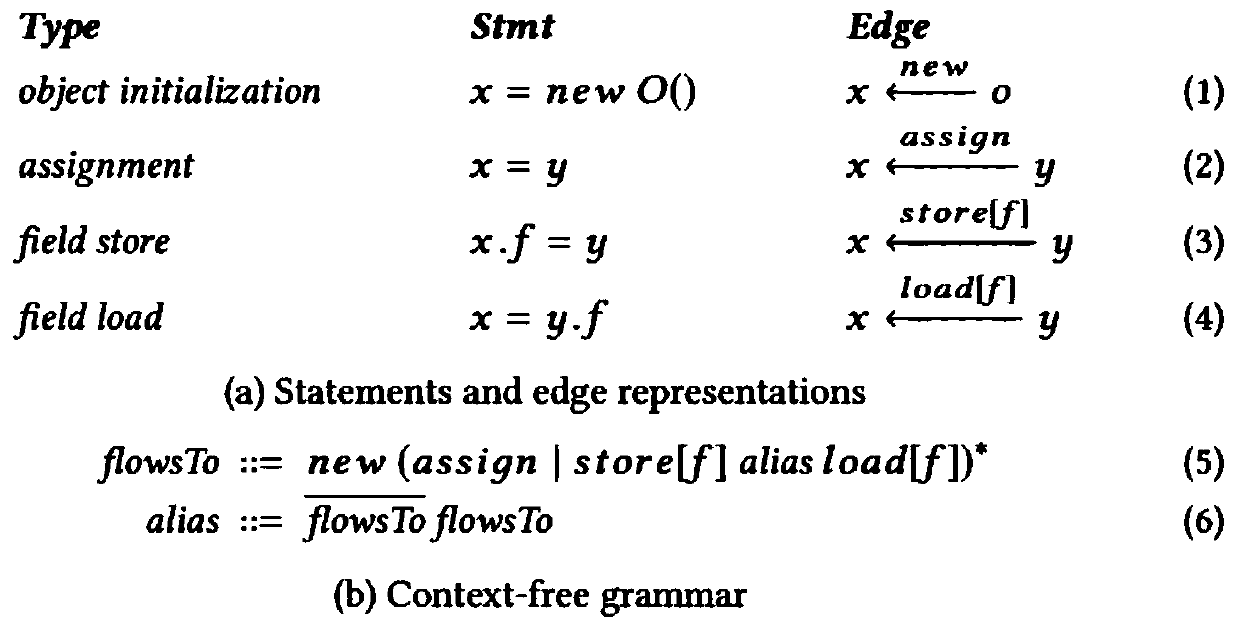
The invention relates to a static detection method for state-related defects in a large-scale system. The static detection method comprises the following steps: firstly, abstracting the state-relateddefects in the large-scale system into a form represented by a finite state machine; secondly, generating an inter-process control flow execution tree (ICFET) based on a symbol execution technology, and proposing a new interval-based path encoding / decoding algorithm to represent path constraints; based on the ICFET, alias analysis and data flow analysis are then performed in a context-sensitive and path-sensitive manner, tracking the flow of each object of each specified type to identify a sequence of events that may occur on the object. And finally, generating a program diagram according to the ICFET and alias analysis and data flow analysis. Constraint-based graph reachability calculation is performed, and if a reachable edge can reach an undefined or erroneous state in a finite state machine, there is an event sequence of undefined or erroneous states that can drive an object or group of objects to a specification, generating an erroneous report.
Owner:NANJING UNIV
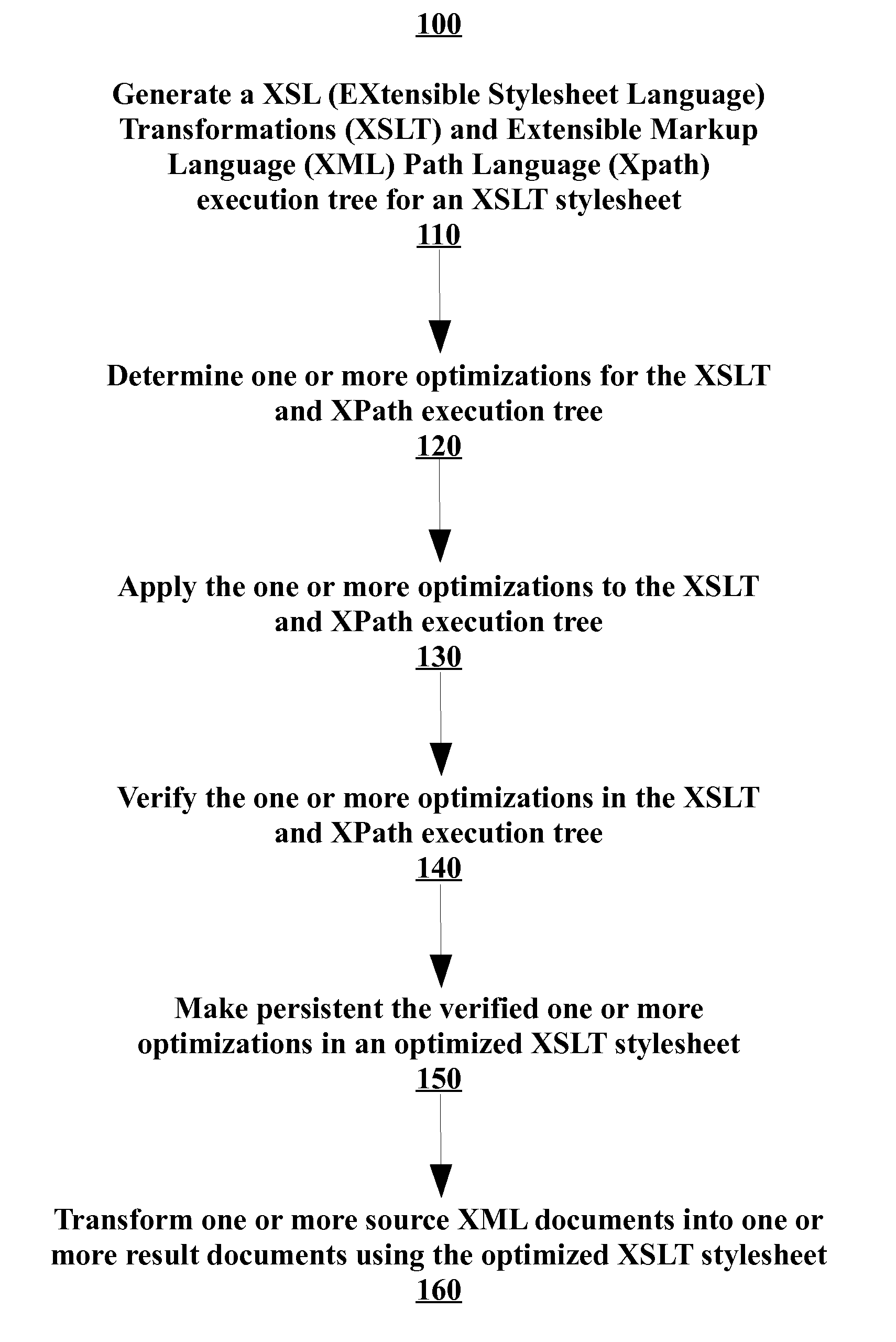
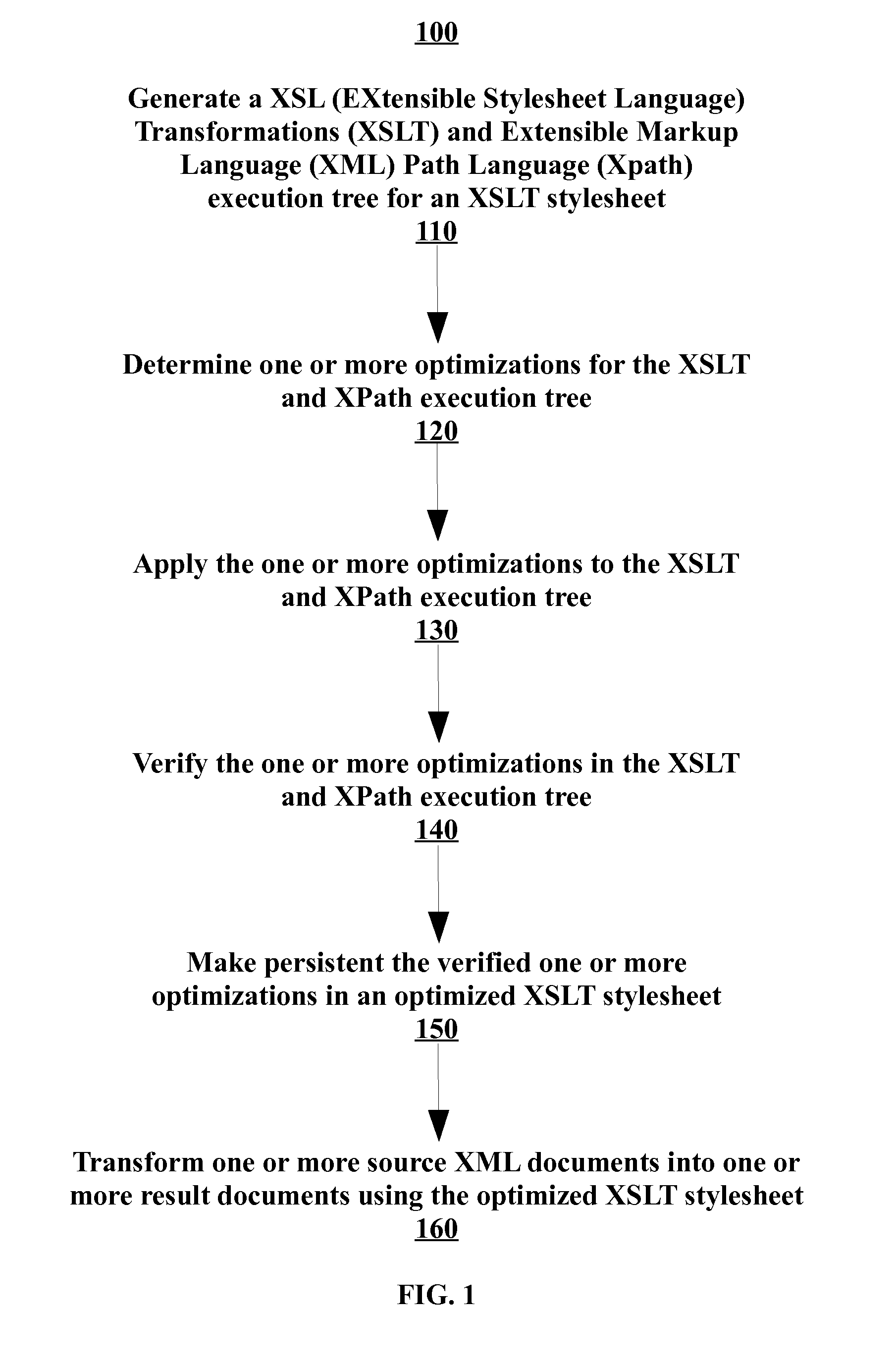
Profile-based optimization of xslt transformations
Methods and apparatus, including computer program products, for profile-based optimizations of Extensible Stylesheet Language Transformations (XSLT) transformations. A method includes generating a XSL (Extensible Stylesheet Language) Transformations (XSLT) and Extensible Markup Language (XML) Path Language (XPath) execution tree for an XSLT stylesheet, determining one or more optimizations for the XSLT and XPath execution tree, applying the one or more optimizations to the XSLT and XPath execution tree, verifying the one or more optimizations in the XSLT and XPath execution tree, making the verified one or more optimizations persistent in an optimized XSLT stylesheet, and transforming one or more source XML documents into one or more result documents using the optimized XSLT stylesheet.
Owner:ALTOVA
Dynamic symbol execution visualization method for vulnerability mining
ActiveCN106502912AIncrease coverageImprove teaching experienceSoftware testing/debuggingPlatform integrity maintainanceCode coverageTheoretical computer science
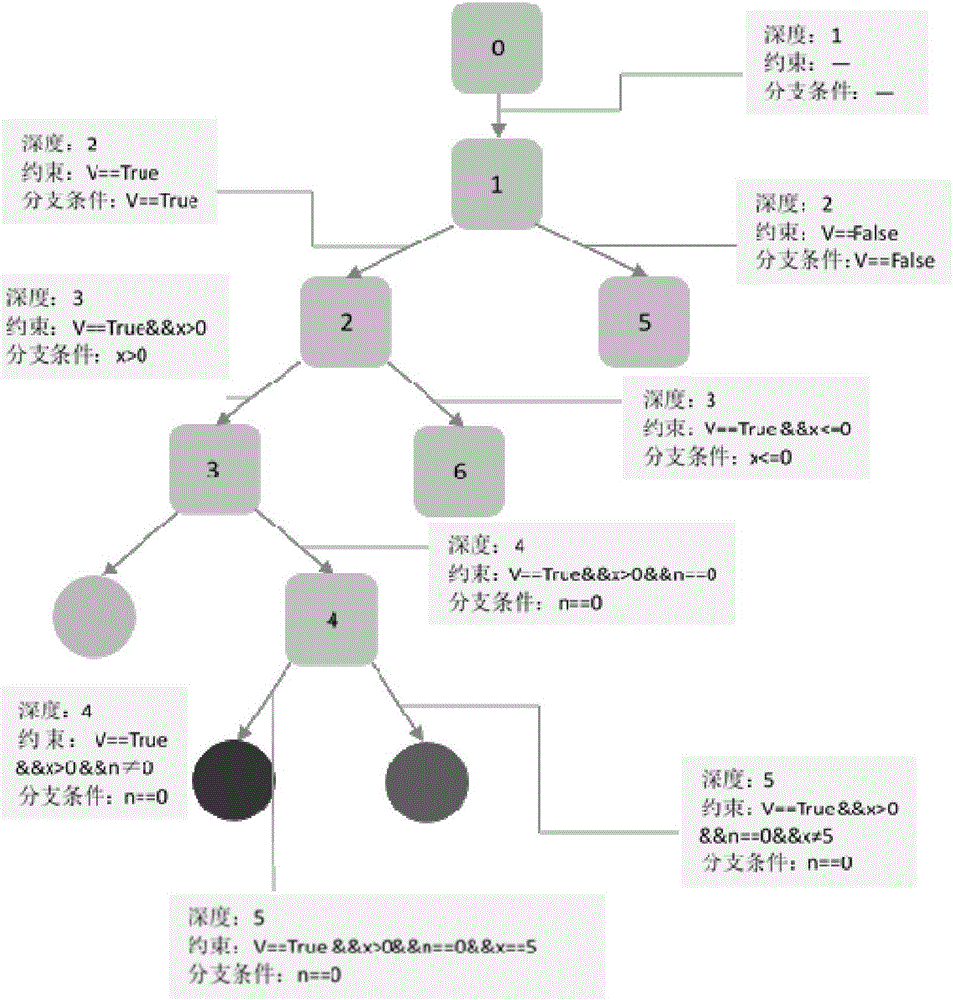
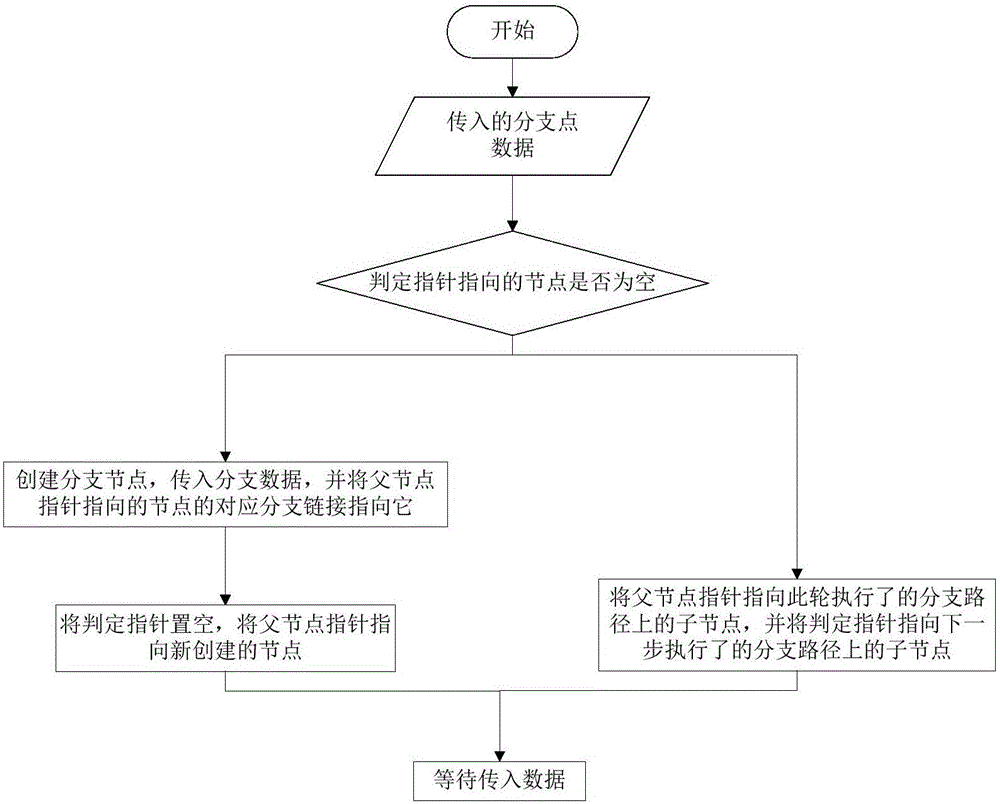
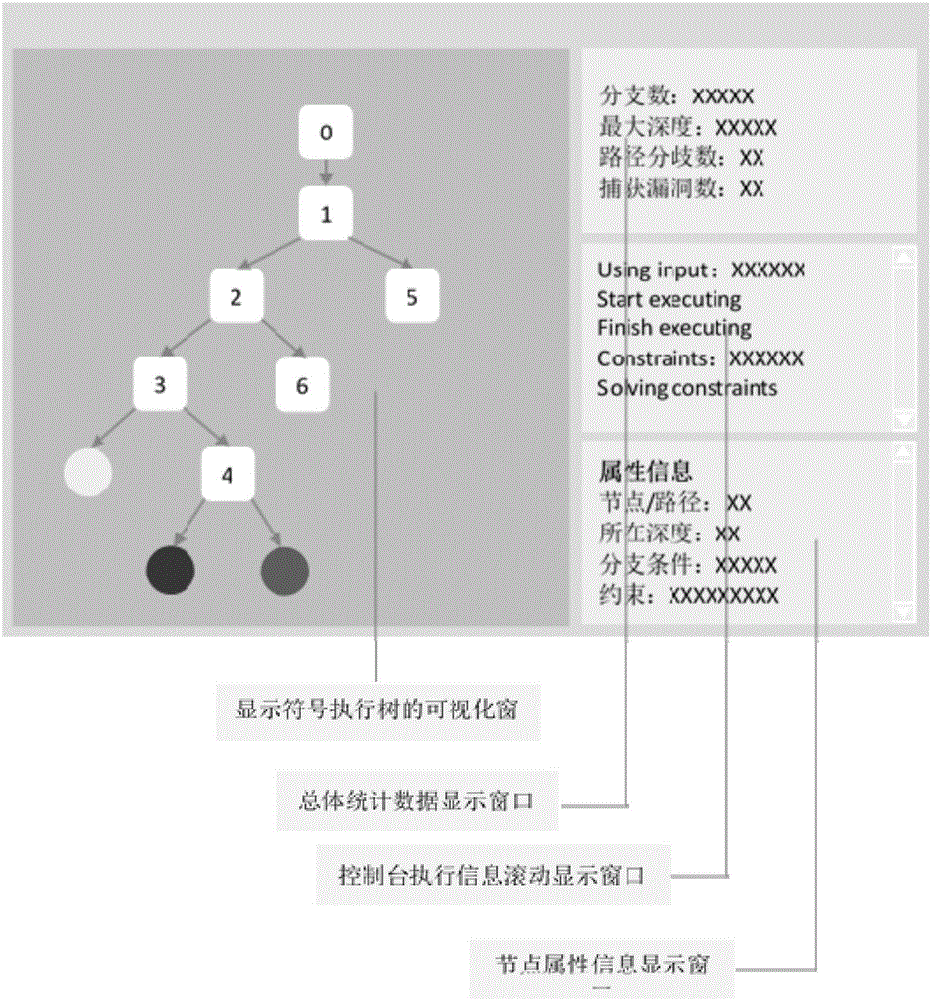
The invention discloses a dynamic symbol execution visualization method for vulnerability mining, and relates to the technical field of symbol execution visualization. The technical problems that in the prior art, symbol execution cannot be dynamically presented in the vulnerability mining process, and the low traversal efficiency caused by a code coverage bottleneck is difficult to overcome are solved. The method mainly comprises the steps that a vulnerability mining tool and a symbol execution visualization tool are started; the symbol execution visualization tool is set in the state of waiting to be called, and the vulnerability mining tool is executed to branch points; the vulnerability mining tool calls a symbol execution tree drawing module of the symbol execution visualization tool to construct branch nodes and then sends branch information to the branch nodes; overall statistic data of all the current branch nodes is updated through a data statistics module of the symbol execution visualization tool; in the overall statistic data, the symbol execution tree drawing module creates next branch nodes and sets the positions of the branch nodes according to calling data and branch information. The method is used for symbol execution visualization.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Process access file control method and device
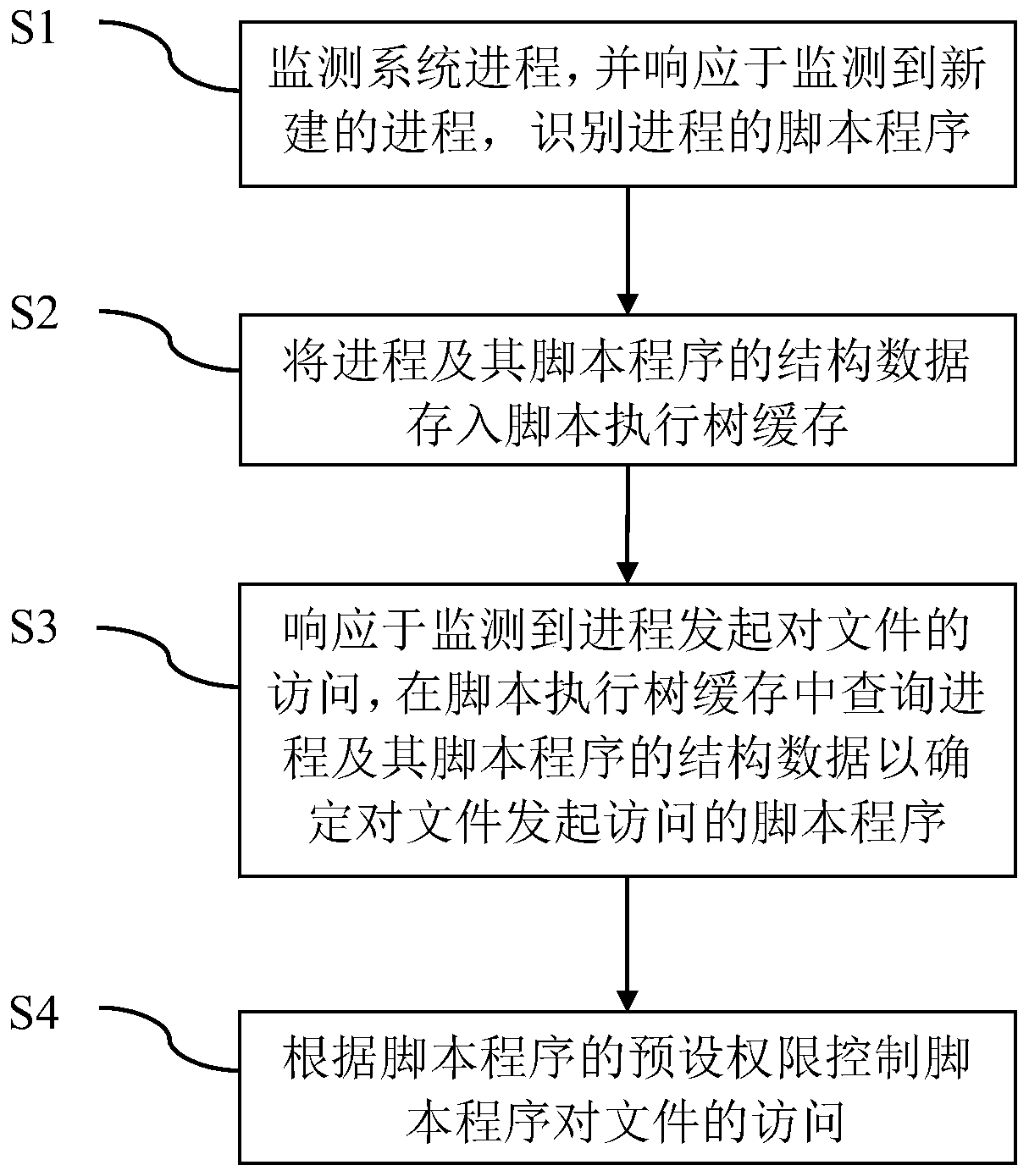
ActiveCN110781491ANot be tampered with illegallyDigital data protectionPlatform integrity maintainanceSoftware engineeringScriptlet
The invention relates to a process access file control method and device, and the method comprises the steps: monitoring a system process, responding to the monitored newly built process, and recognizing a script program of the process; storing the process and the structure data of the script program into a script execution tree cache; in response to monitoring that the process initiates access tothe file, querying the process and structure data of the script program of the process in the script execution tree cache to determine the script program which initiates access to the file; and controlling the access of the script program to the file according to the preset authority of the script program. According to the method provided by the invention, only the specified script program is allowed to access the specified file, and important data is protected from being illegally tampered.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
Binary system translation method and device based on execution tree depth
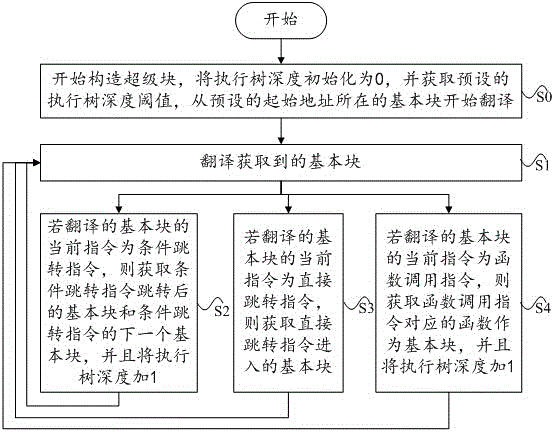
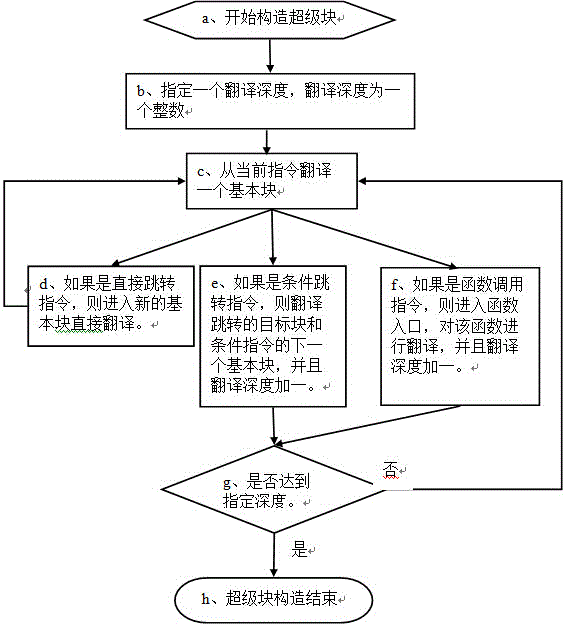
ActiveCN104375879AImprove performanceNext instruction address formationSoftware simulation/interpretation/emulationBasic blockExecution tree
The invention discloses a binary system translation method and device based on the execution tree depth. The method comprises the steps that when a super block begins to be constructed, the execution tree depth is initialized to be zero, a preset execution tree depth threshold value is obtained, translation is started from a basic block where a preset initial address is located, and in the translating process, if a current instruction of the translated basic block is a direct skip instruction, a basic block which the direct skip instruction enters is translated; if the current instruction of the translated basic block is a condition skip instruction, a basic block after the condition skip instruction skips and the next basic block of the condition skip instruction are translated, and one is added into the execution tree depth; if the current instruction of the translated basic block is a function call instruction, functions corresponding to the function call instruction are translated, one is added into the execution tree depth, when the execution tree depth reaches the execution tree depth threshold value, translation is finished, and all the translated basic blocks form the super block. The method and the device can promote the performance of an execution translation program.
Owner:浙江迪捷软件科技有限公司
Industrial identify encoding and decoding language
Owner:ORACLE INT CORP
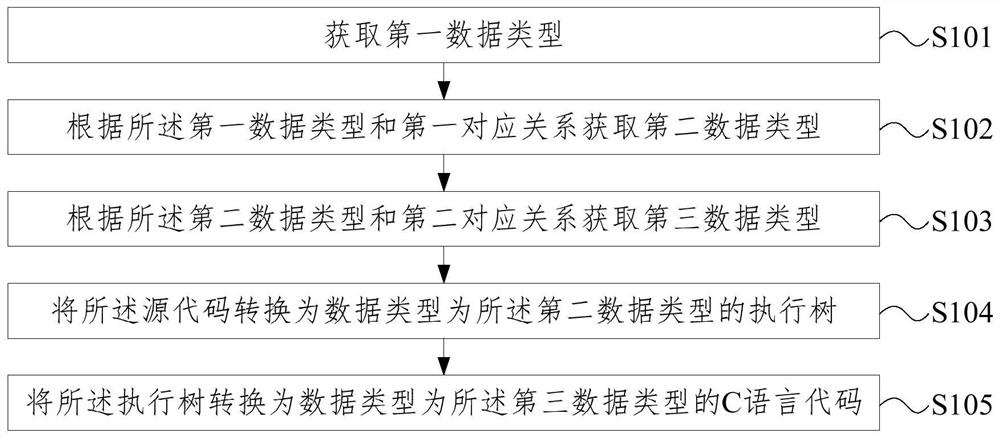
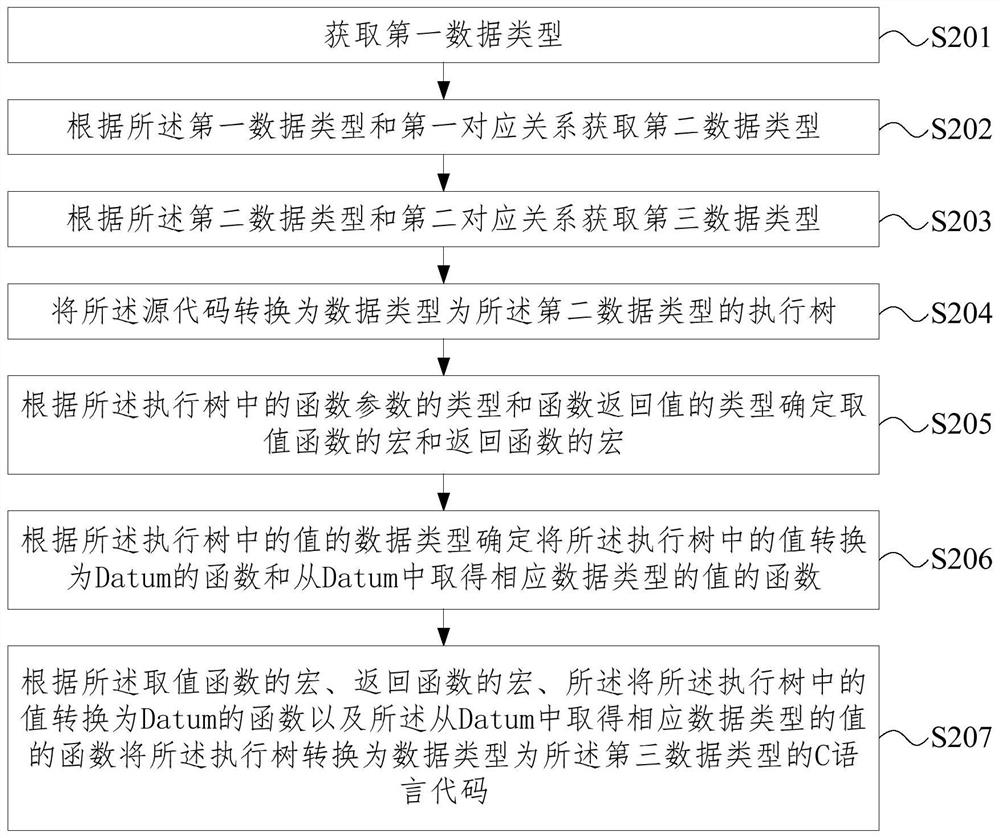
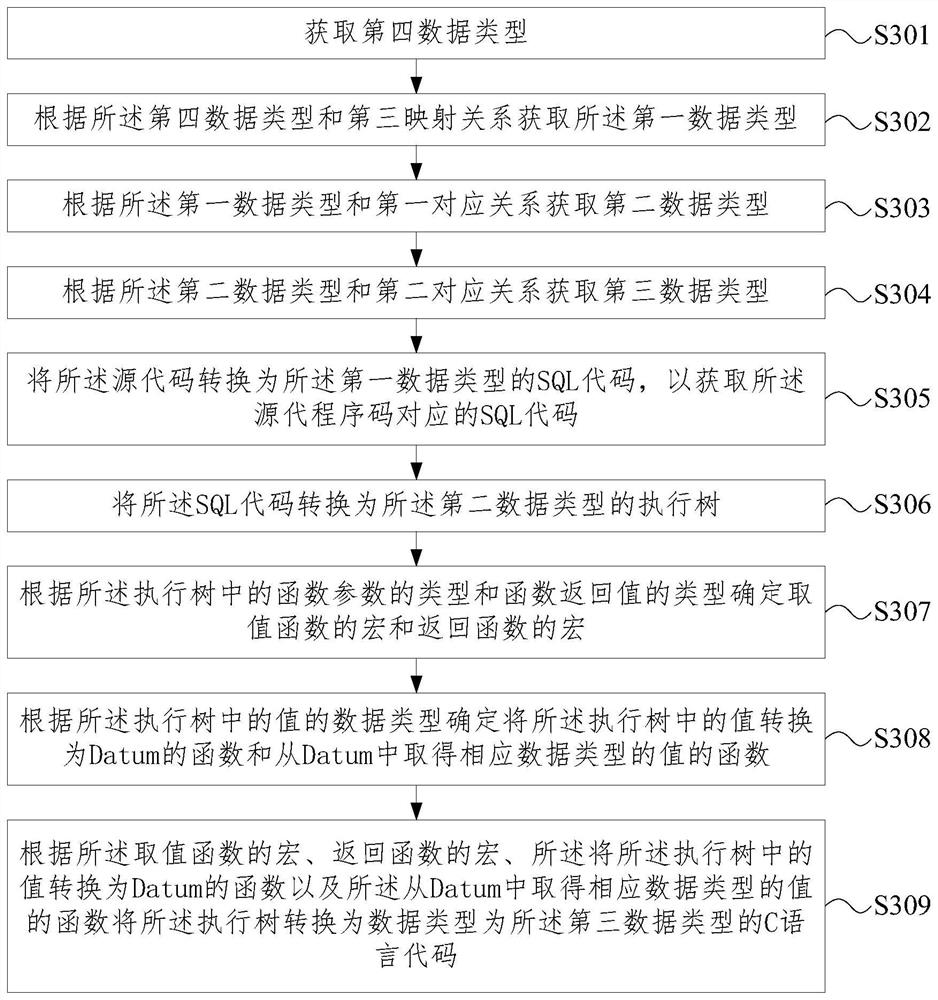
Method and device for converting code language
The embodiment of the invention provides a method and device for converting a code language, and relates to the technical field of databases. The method comprises the steps of obtaining a first data type and a data type of an SQL code corresponding to a source code; obtaining a second data type according to the first data type and the first corresponding relationship, wherein the second data typeis a data type of an execution tree corresponding to the SQL code of the first data type; obtaining a third data type according to the second data type and the second corresponding relationship, wherein the third data type is a data type of a C language corresponding to the execution tree of the second data type; converting the source code into an execution tree of which the data type is a seconddata type; and converting the execution tree into a C language code of which the data type is a third data type. The method is used for realizing data processing of the database in a compilation execution mode under the condition that the source code is the SQL code and the target code is the C language code.
Owner:北京人大金仓信息技术股份有限公司
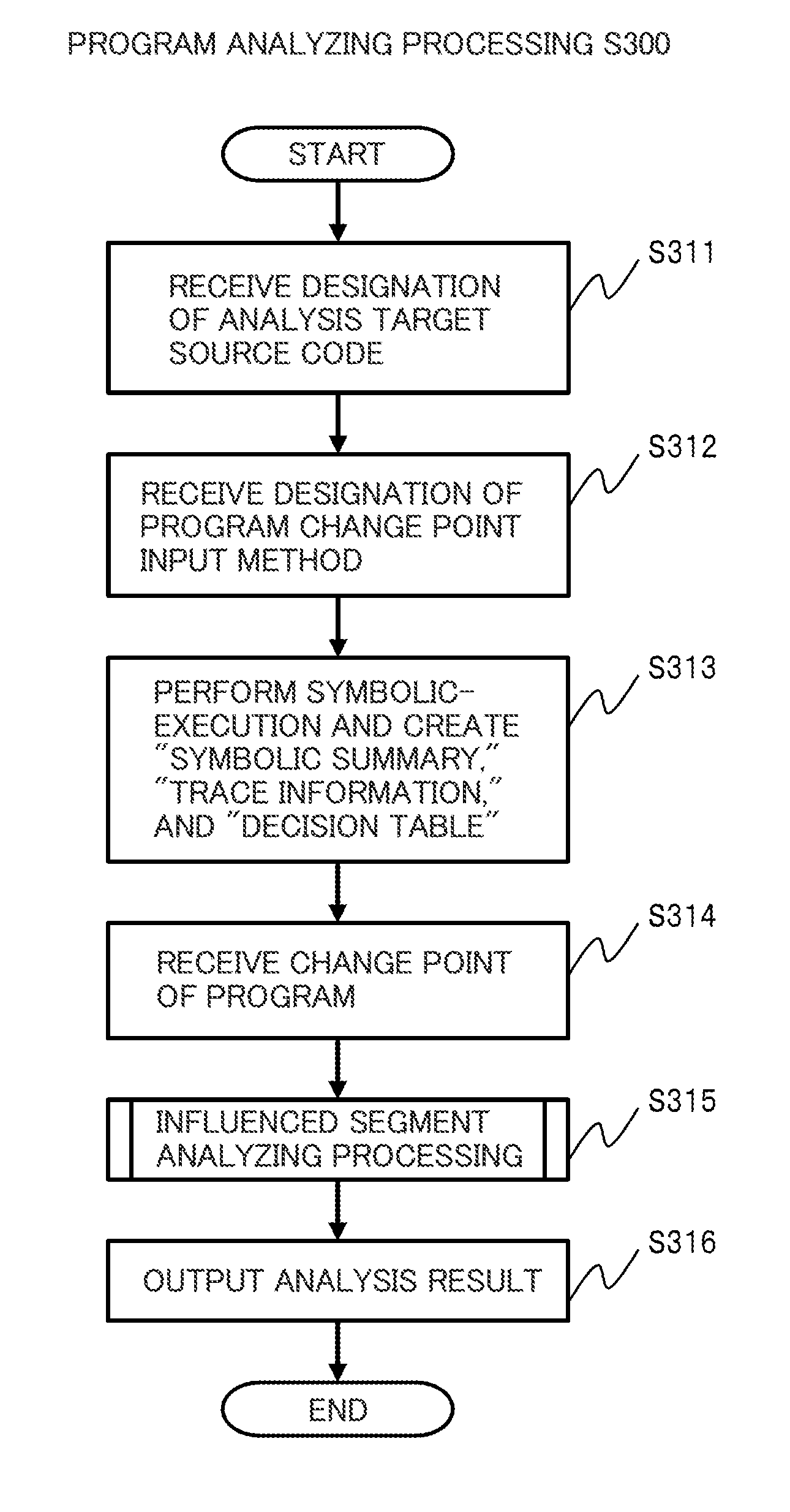
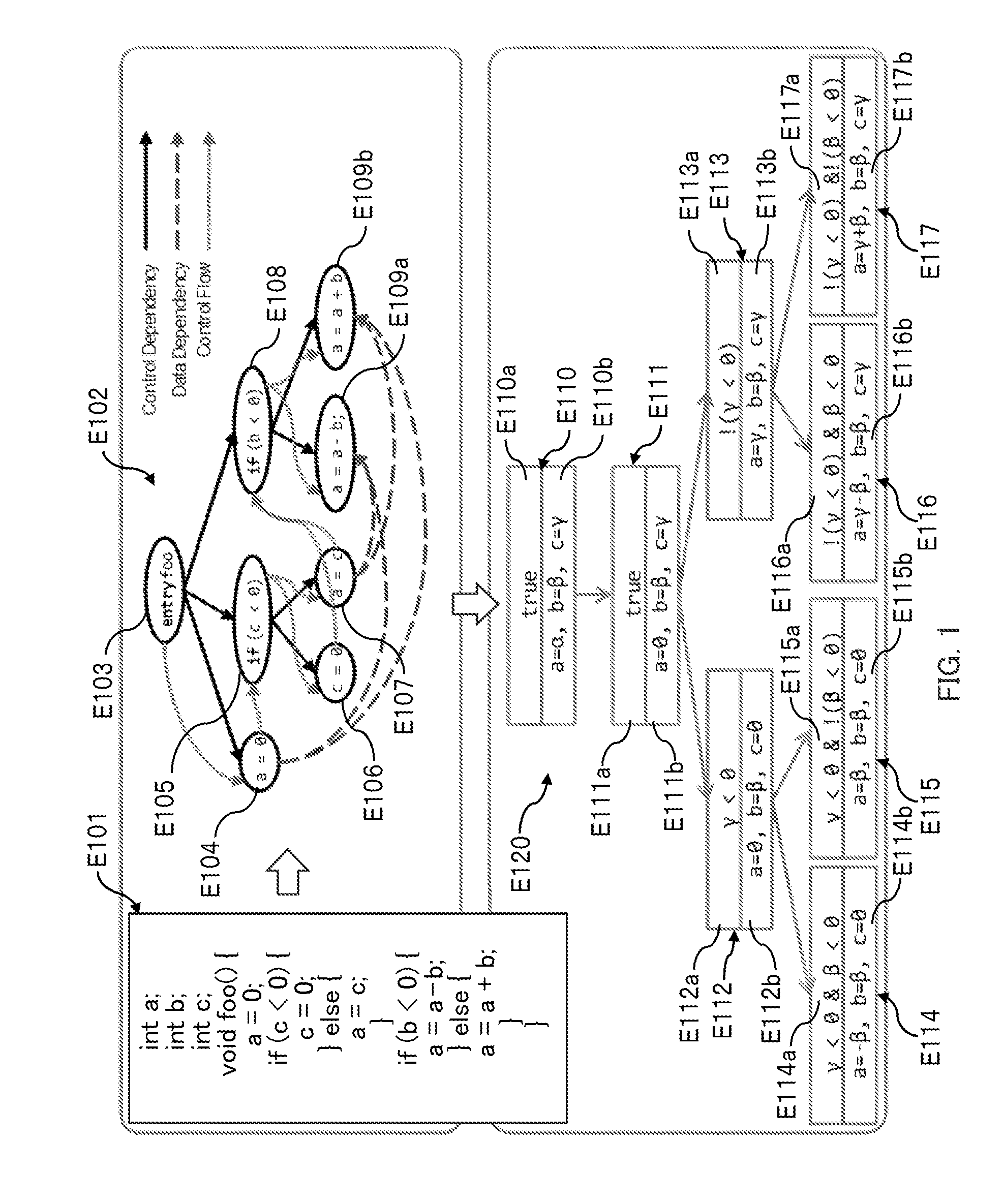
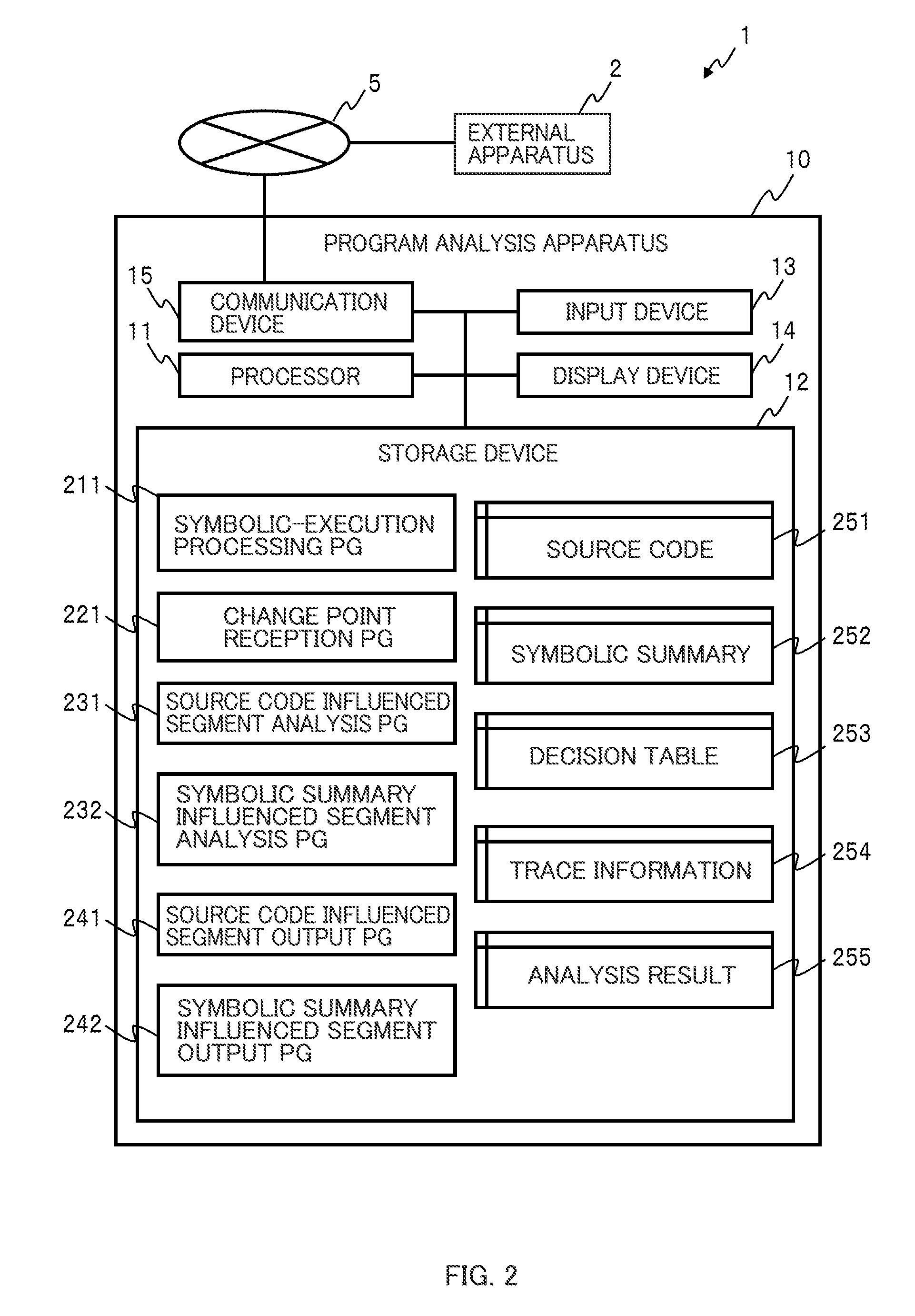
Program analysis apparatus and program analysis method
InactiveUS20150199183A1Improve development efficiencySoftware maintainance/managementSoftware reuseDecision tableAnalysis working
An object is to assist analysis work on a program in software development and improve program development efficiency. A program analysis apparatus performs symbolic-execution on a program stored in a storage device, receives an input of a change point of the program, and based on a result of the symbolic-execution, identifies an influenced segment of the program when the program is changed for the change point. The program analysis apparatus receives the change point by receiving a change operation on any one of a symbolic summary which is a terminal node of an execution tree obtained by the symbolic-execution, a decision table based on the symbolic summary, and a source code. The program analysis apparatus visualizes the influenced segment of the identified program in any mode of the symbolic summary, the source code, and the decision table.
Owner:HITACHI LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com