Method for user behavior analysis under https environment and system thereof
A behavior analysis and user technology, applied in the Internet field, can solve problems such as technical limitations, scene limitations, and the inability to realize the ability to analyze user behavior on the entire network, and achieve the effect of reducing development and maintenance costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
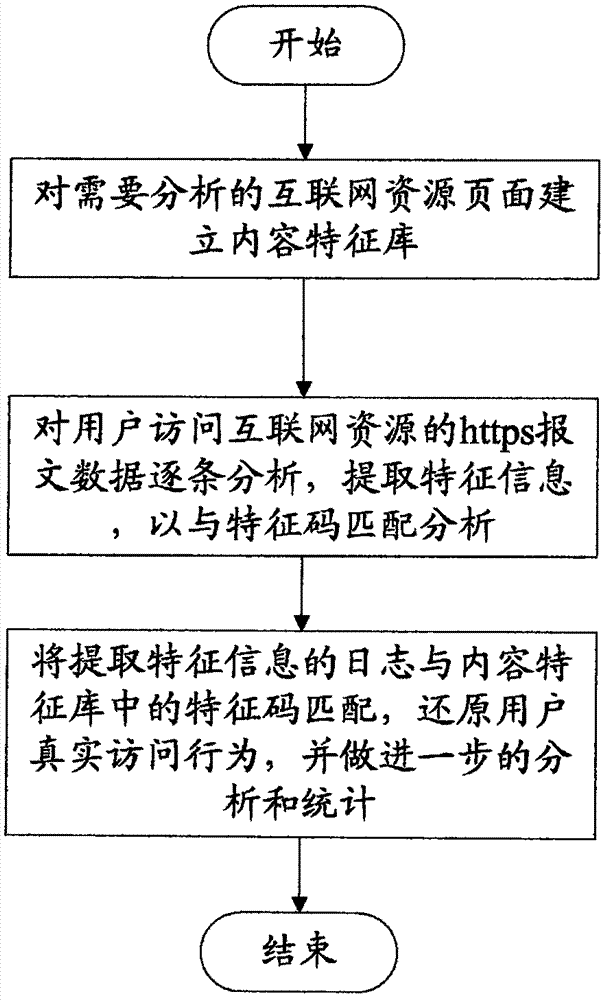
[0055] Such as figure 1 As shown, a method for analyzing user behavior in an https environment includes:
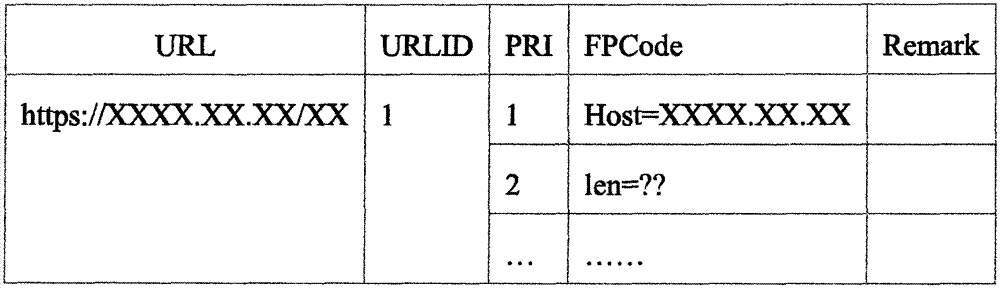
[0056] Step 1) set up a content feature library for the Internet resource page that needs to be analyzed. The feature library is composed of multiple feature codes. The feature codes include: the Host of the HTTPS request URL, the page size, the page contains resource content, resource content size, dynamic resource information, One or a combination of embedded URLs and their quantities;
[0057] Step 2) analyze the https message data of the user's access to Internet resources one by one, extract feature information, and analyze with feature code matching;
[0058] Step 3) Match the log of extracted feature information with the feature code in the content feature database, restore the user's real access behavior, and make further analysis and statistics.
[0059] The present invention realizes user Internet behavior analysis under https by establishing an Internet content...
Embodiment 2
[0061] The present invention is further described in conjunction with the embodiments, wherein, preferably, in step 2), the extracted feature information is selected from the following:
[0062] Access the Host / Domain of the URL;
[0063] The total length of the uncached part of the https request page;
[0064] The number of uncached images or CSS loaded resources in the https request page;
[0065] The size of each resource object loaded by the page;
[0066] The time when the https request occurred.
[0067] Preferably, in step 2), one or more characteristic fingerprints are formed based on the combination of one or more characteristic information above, and the user access path is determined through user access https requests within a certain time range.
[0068] Preferably, in step 3), the log of the feature information is extracted and the feature code matching in the content feature library is specifically selected from the following methods:
[0069] Unique matching...
Embodiment 3
[0073] In one embodiment, the present invention mainly comprises following main steps:
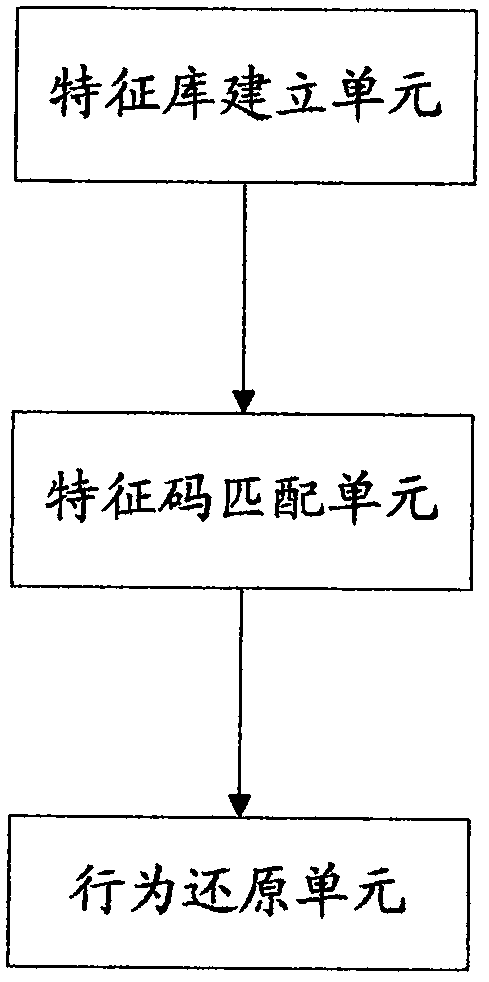
[0074] 1. Establish a content feature library for the Internet resource pages that need to be analyzed
[0075] Use crawler technology to crawl each webpage that needs to be analyzed for the website that needs to be analyzed, and build a webpage feature database based on the data of the crawled webpage. The feature database is composed of multiple feature codes (fingerprints). The feature codes include but are not limited to HTTPS request URLs Host, page size, page contains resource content, resource content size, dynamic resource information, embedded URLs and quantity, etc.
[0076]
[0077] 2. Analyze the HTTPS message data of users accessing Internet resources one by one, extract feature information, and match and analyze with feature codes / fingerprints
[0078] When HTTPS encrypts the communication channel through TLS / SSL, the following information can still be obtained after capt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com