Patents
Literature
30results about How to "Protection input" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
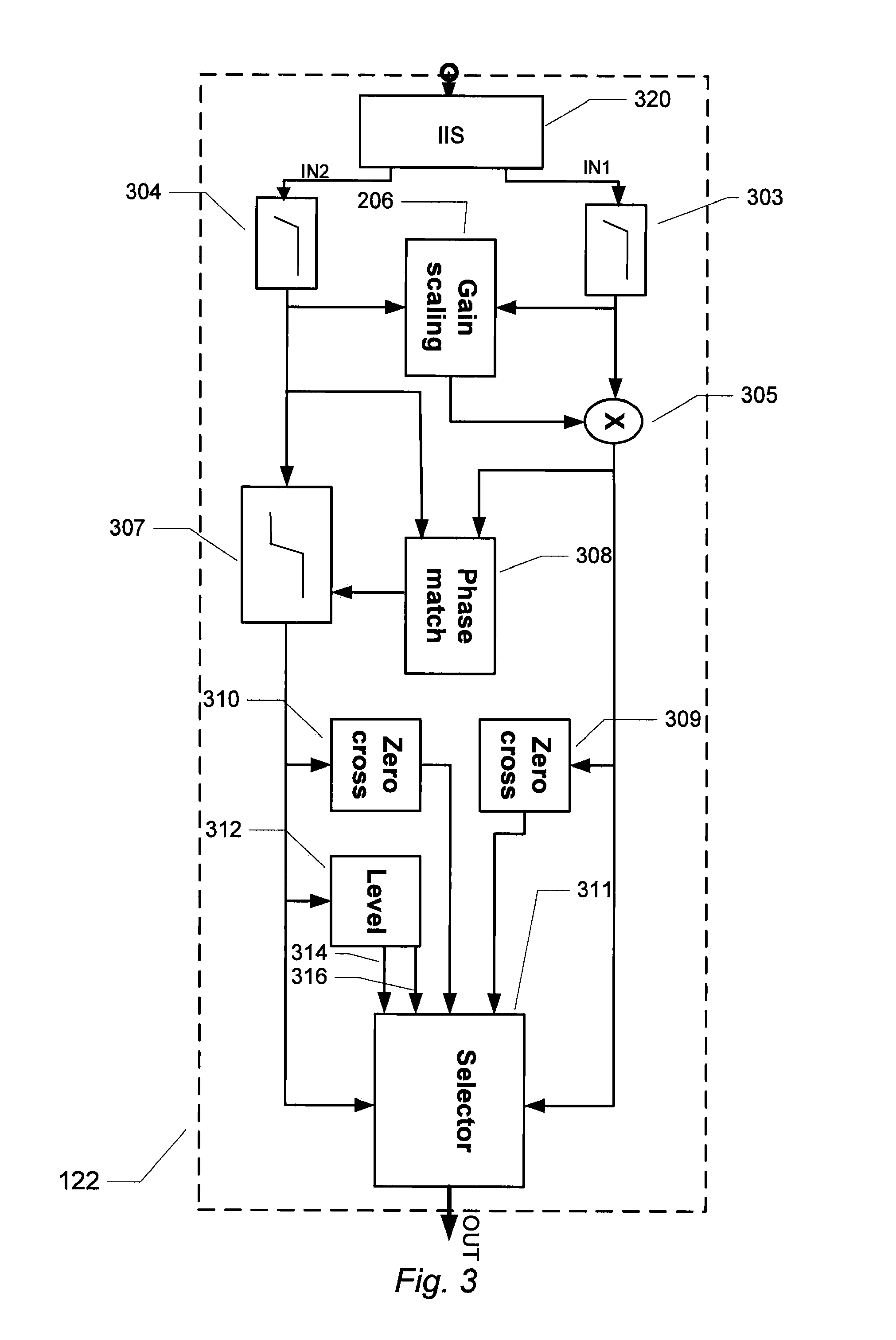
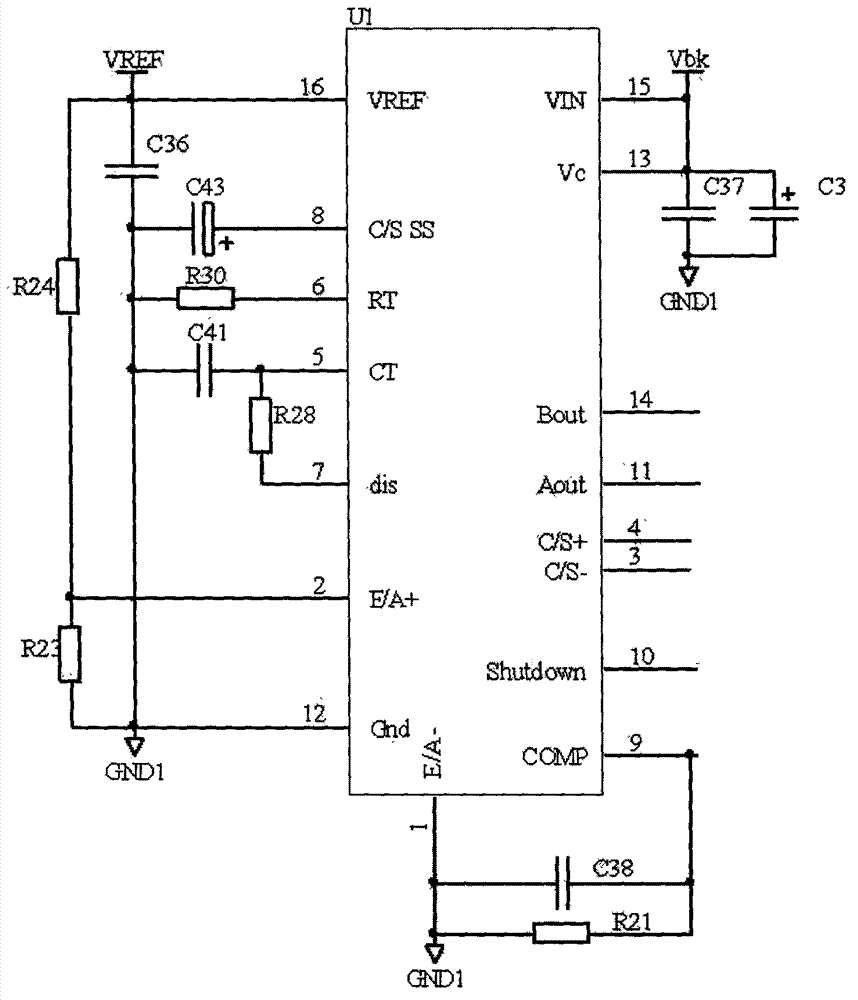
Audio signal controller
ActiveUS20110029109A1Lower Level RequirementsLow costSignal processingLow frequency amplifiersDigital audio signalsAudio frequency
The present invention relates to an audio signal controller adapted to receiving first and second digital audio signals and estimating a signal feature of the first or second digital audio signal. The estimated signal feature is compared with a predetermined feature criterion and the audio signal controller switches from conveying the first digital audio signal to conveying the second digital audio signal to a controller output, or vice versa, at a zero-crossing of the first digital audio signal or the second digital audio signal based on the comparison between the estimated signal feature and the predetermined feature criterion.
Owner:INVENSENSE
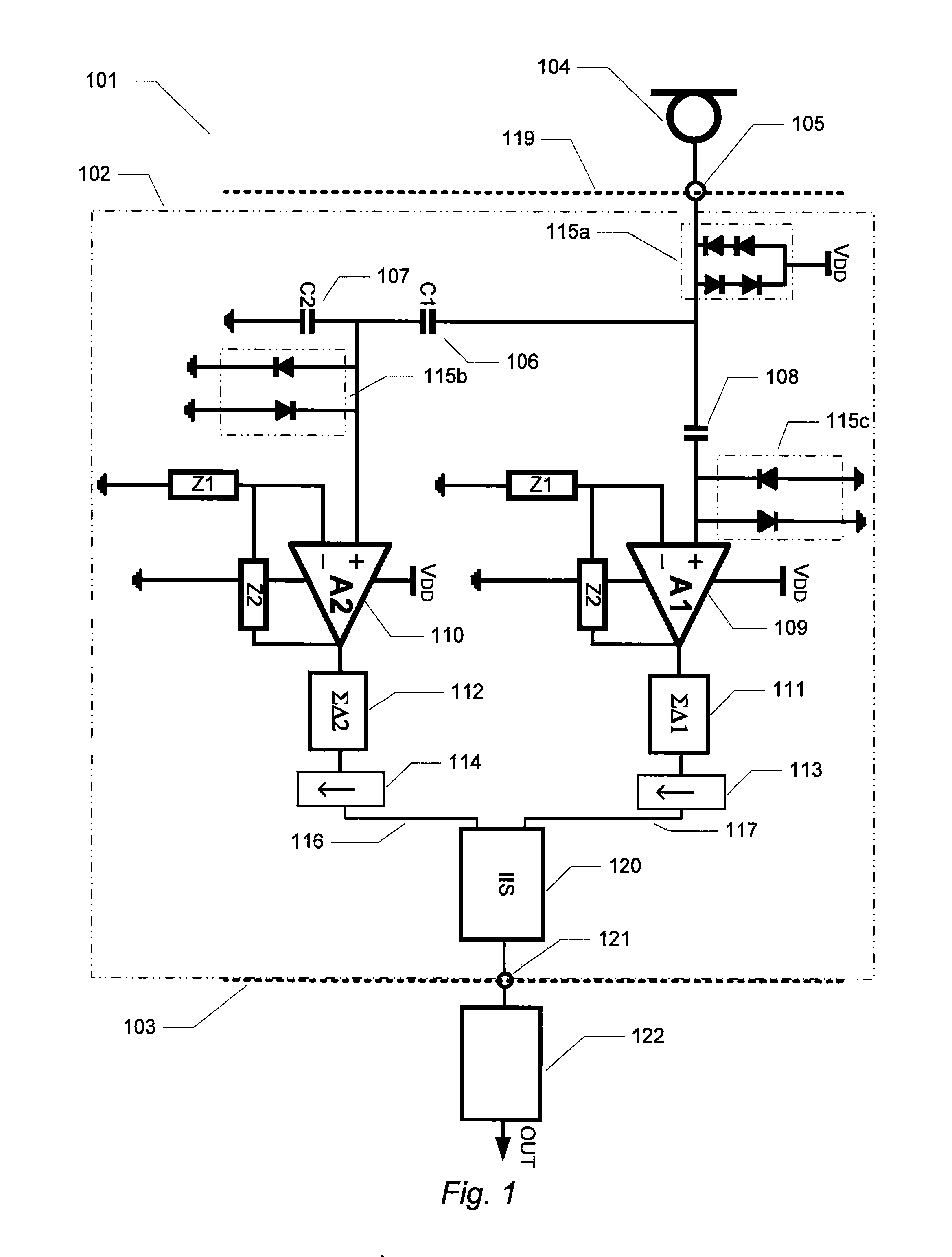
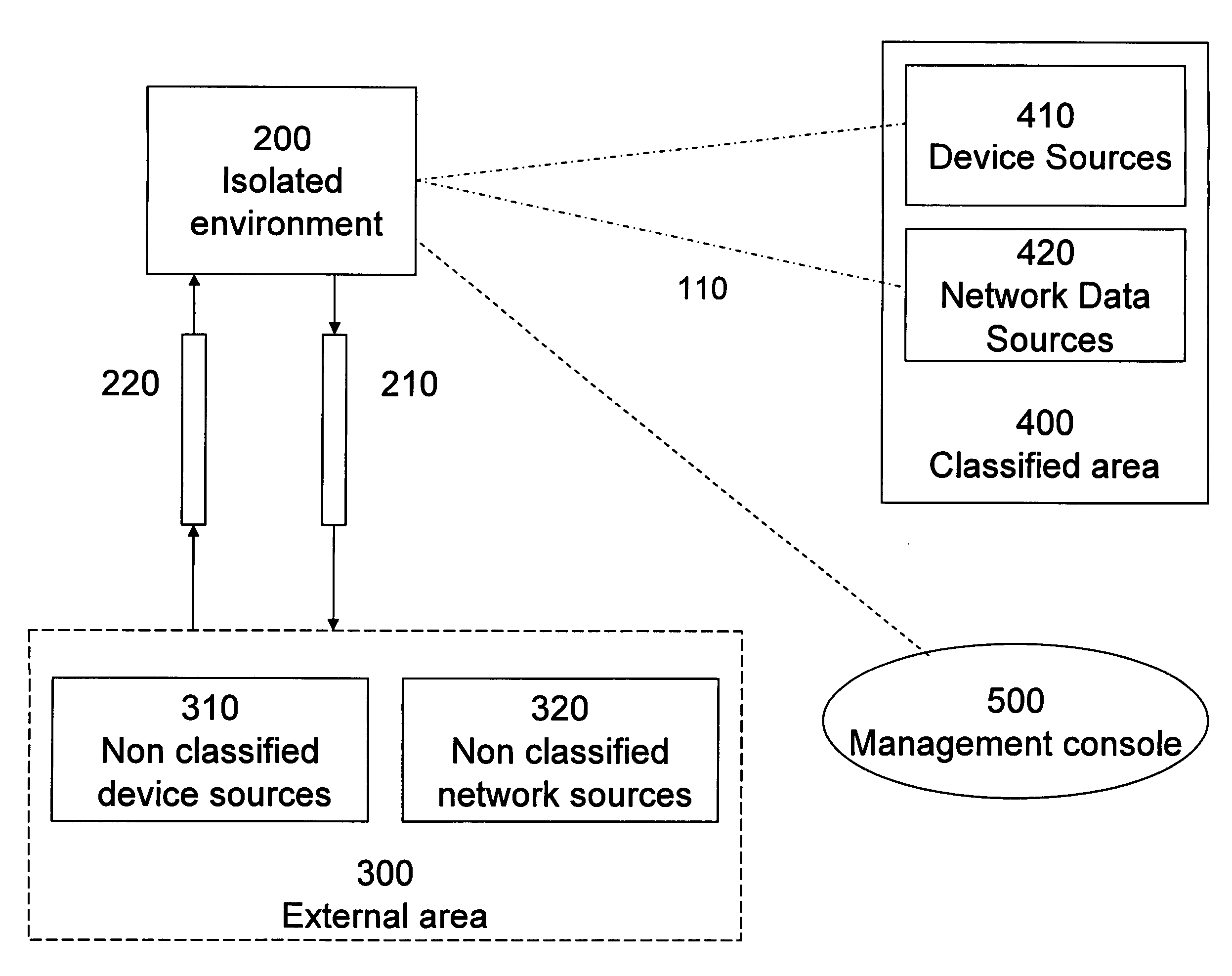
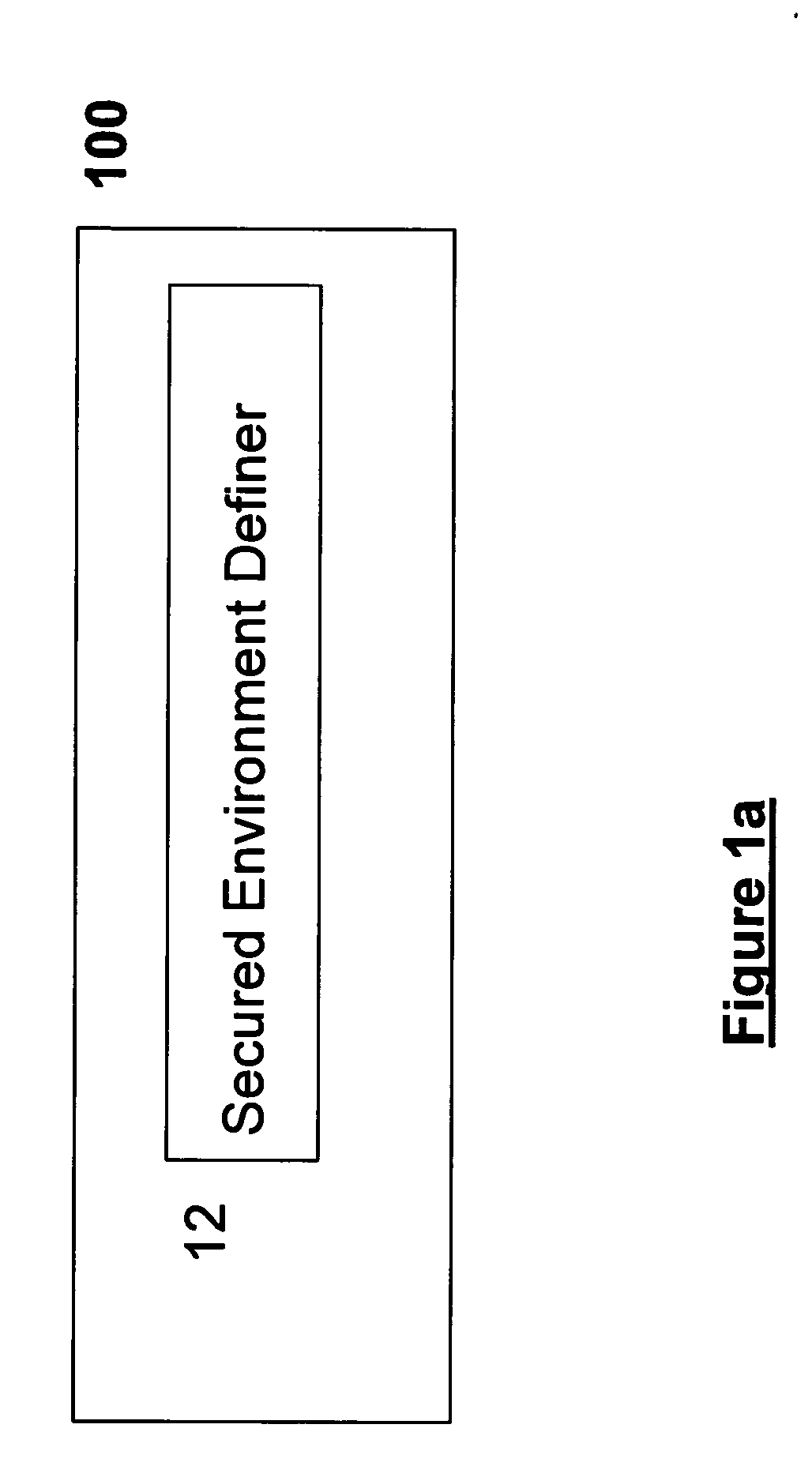
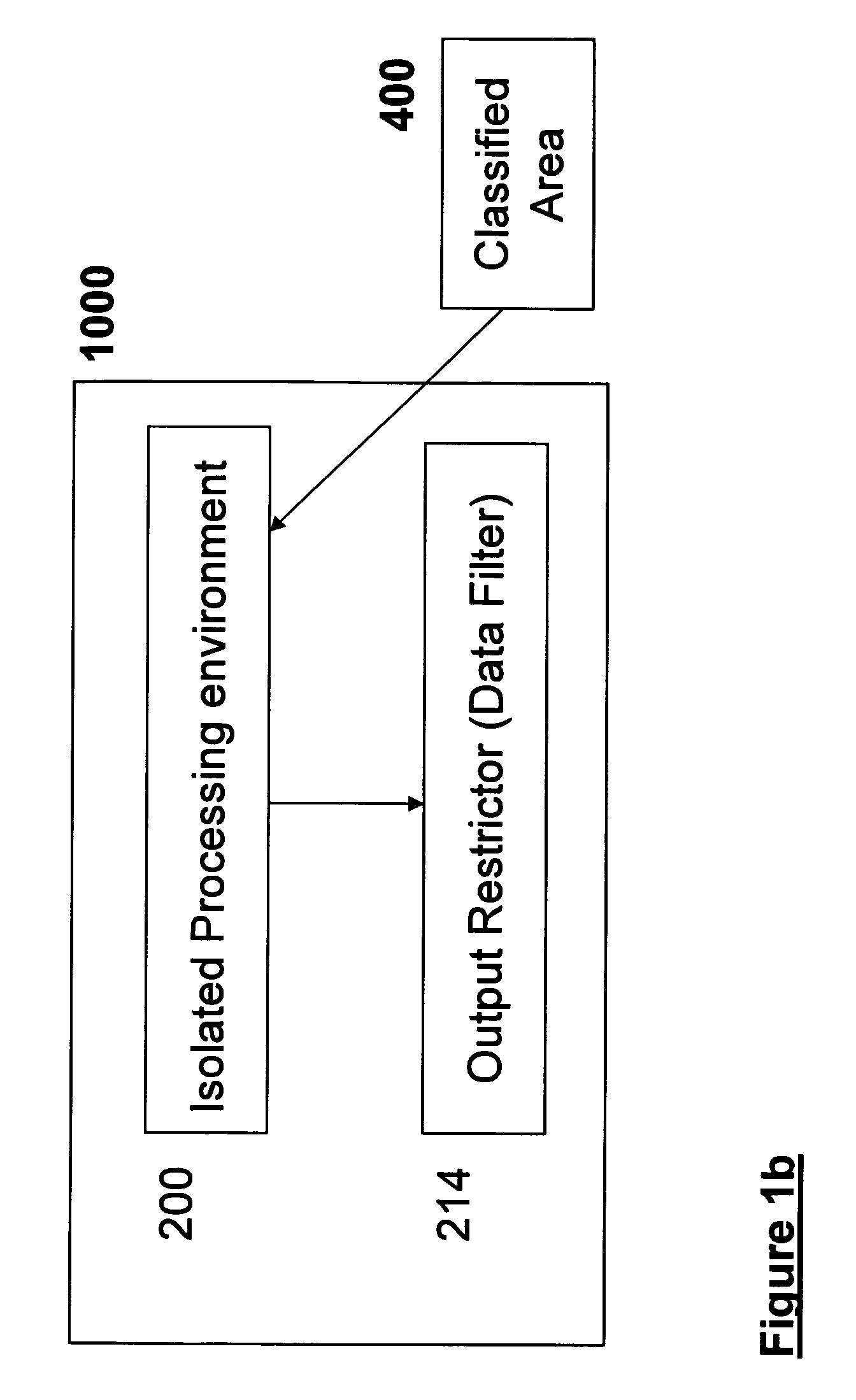
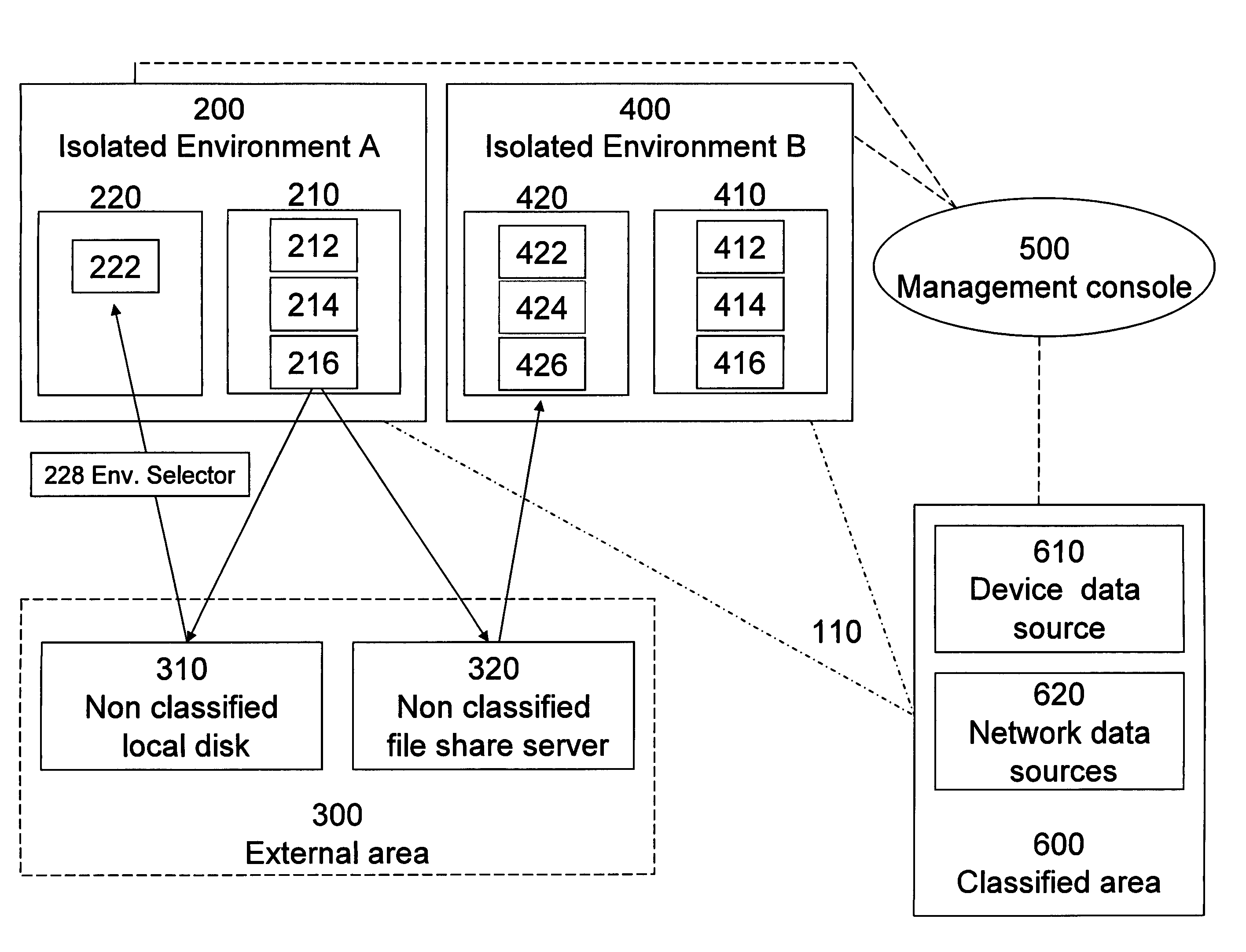
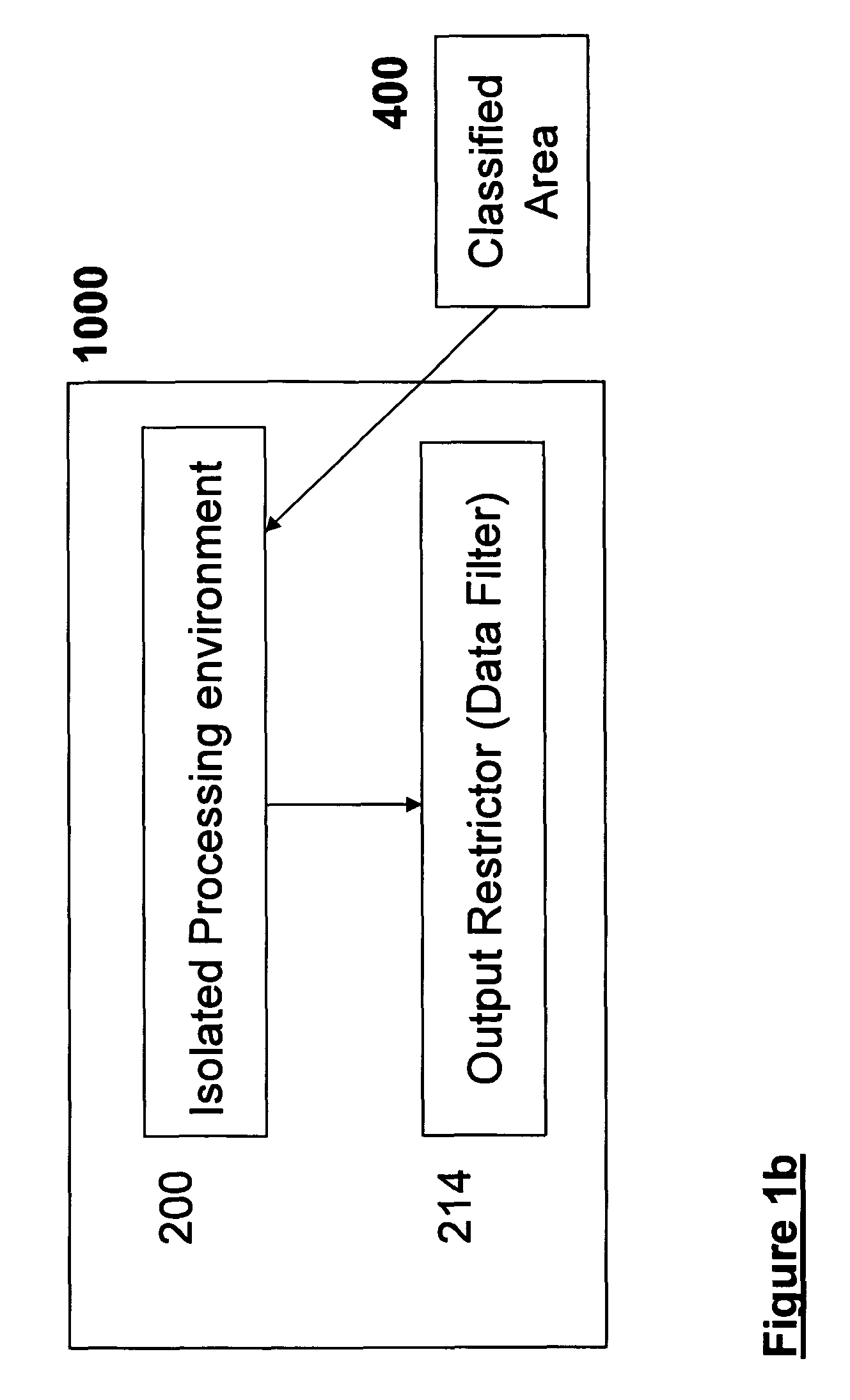
Securing Data in a Networked Environment
ActiveUS20090063869A1Protection inputProgram control using stored programsDigital data processing detailsSafe handlingComputer security
Apparatus for securing data, comprising: an isolated processing environment having a boundary across which data cannot cross and a channel for allowing data to cross the boundary. A filter restricts data passage across the channel. Protected data is initially located in a secure area and is only released to such a secure processing environment so that access for authorized users to the secure data is available, but subsequent release of the secure data by the authorized users to the outside world is controlled.
Owner:MICROSOFT TECH LICENSING LLC
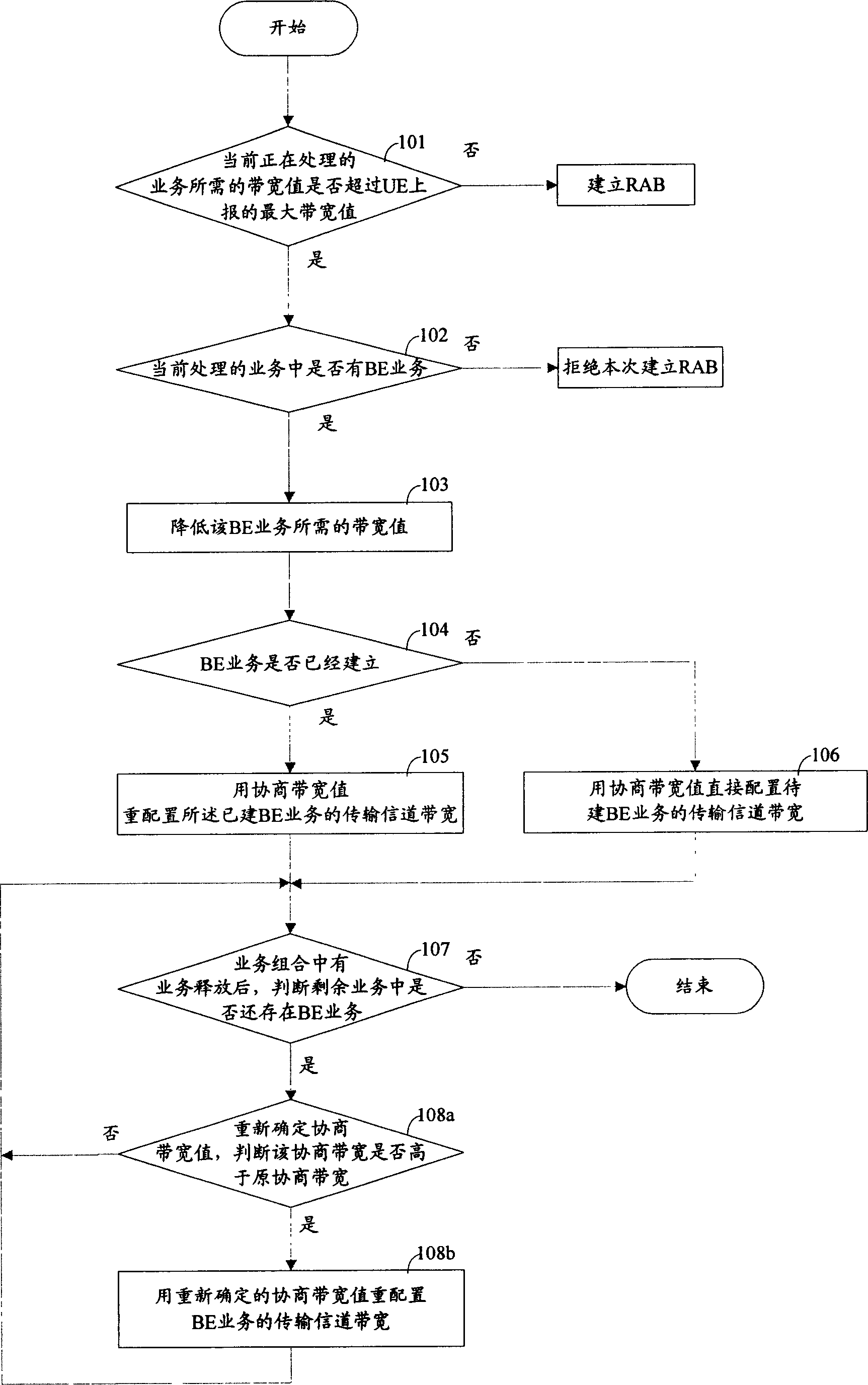
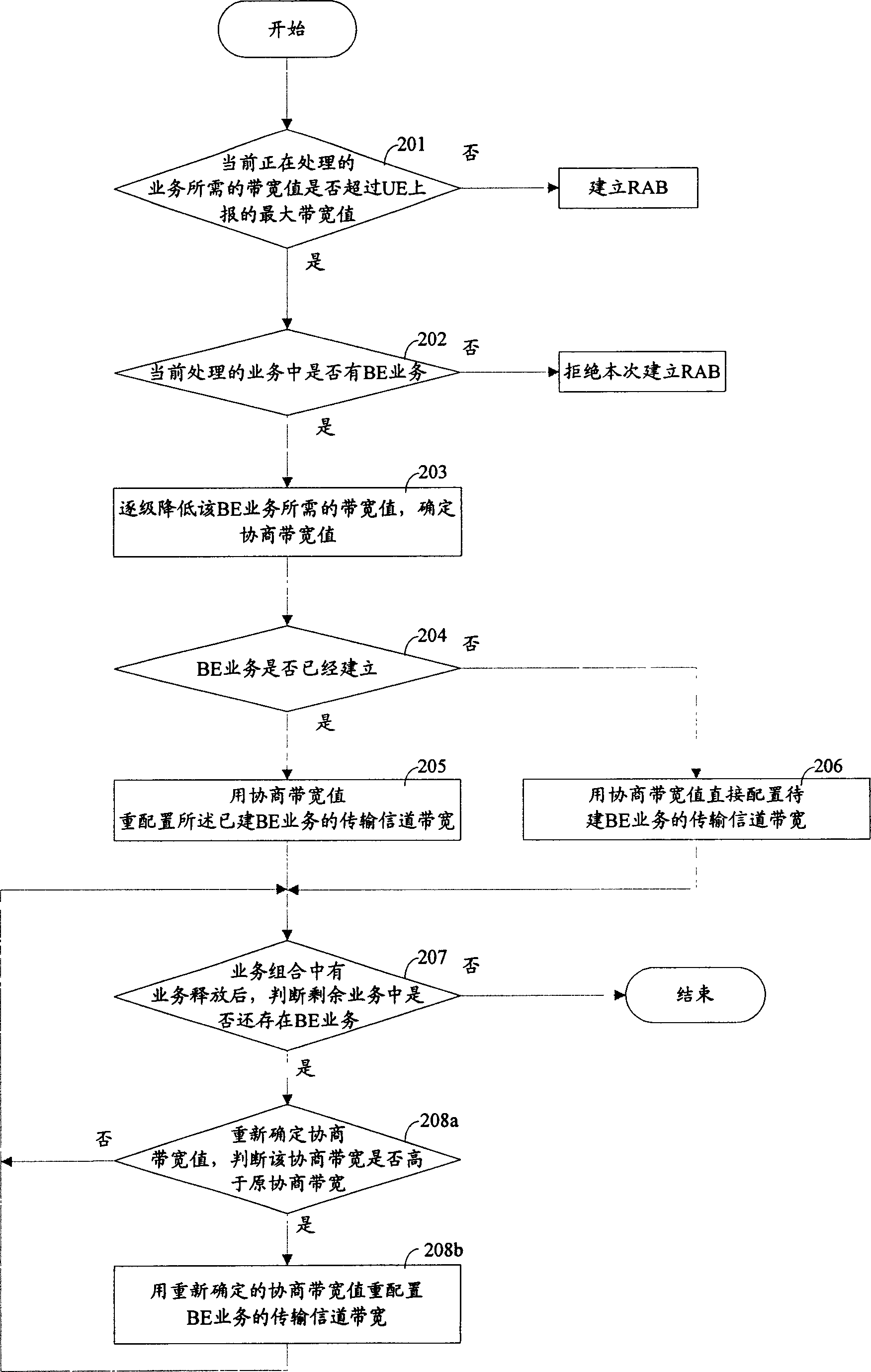
Method for improving service building success rate in mobile communication system
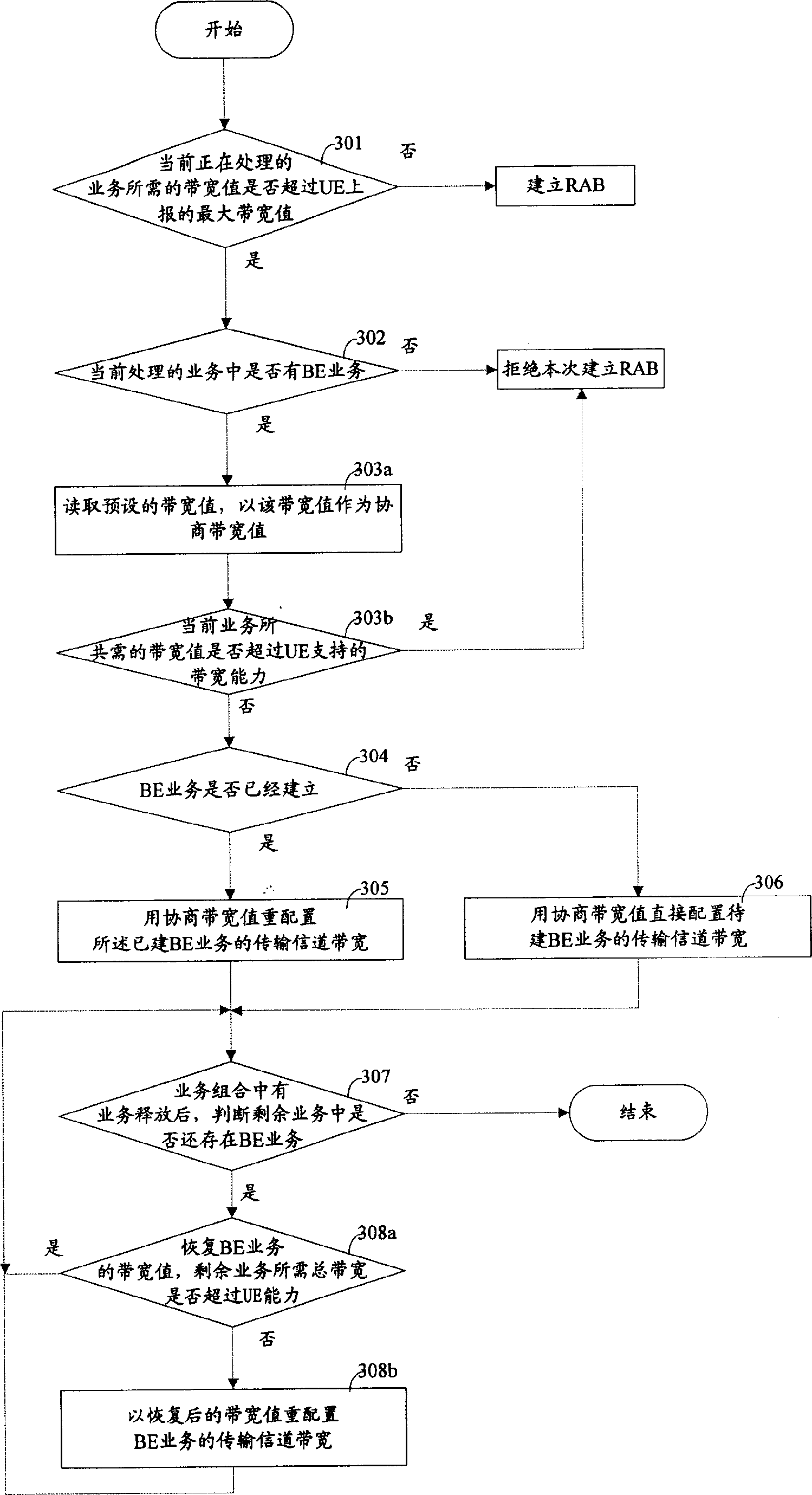
ActiveCN1878395AIncrease success rateLower the bandwidth valueConnection managementRadio/inductive link selection arrangementsNon real timeComputer network
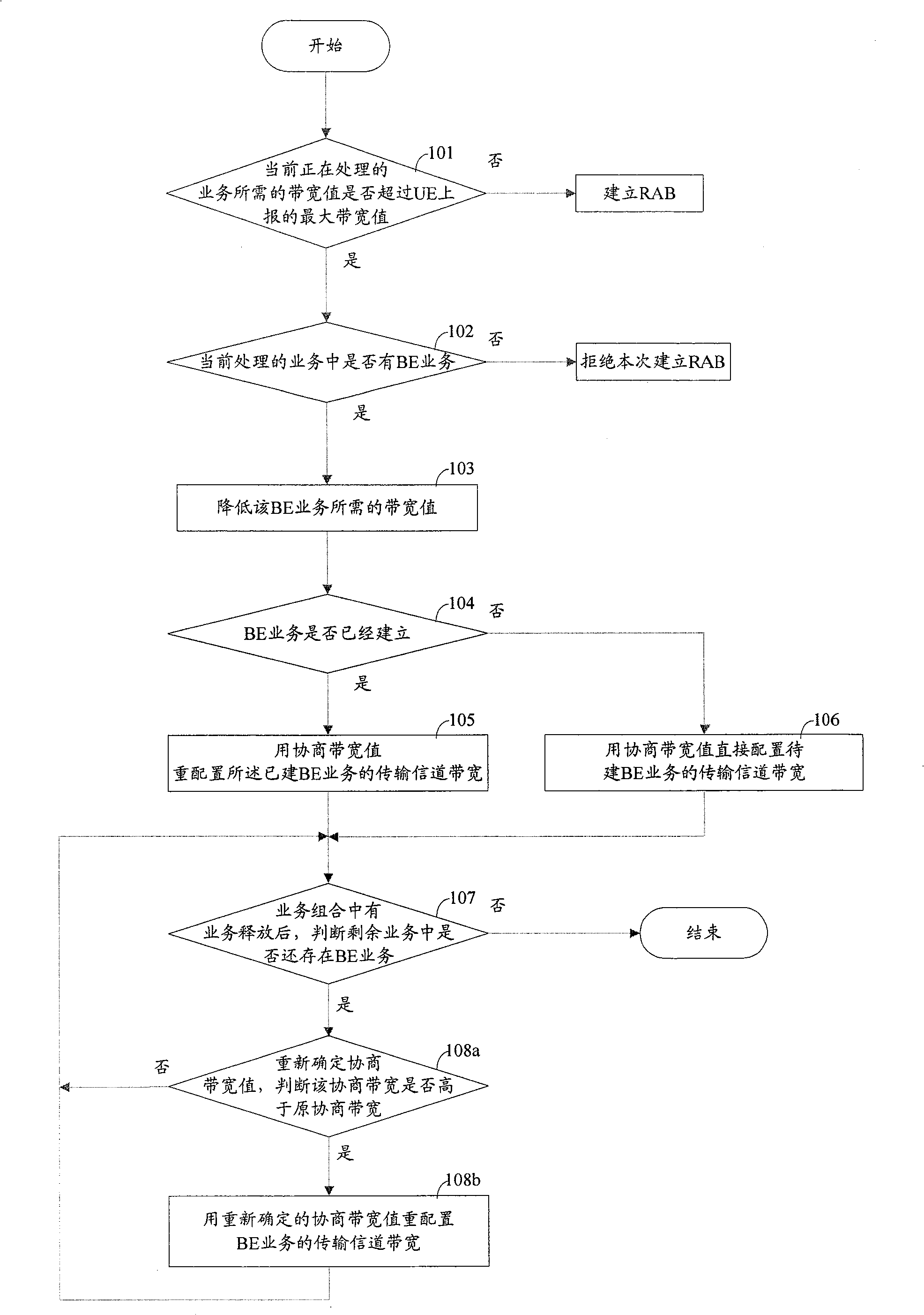
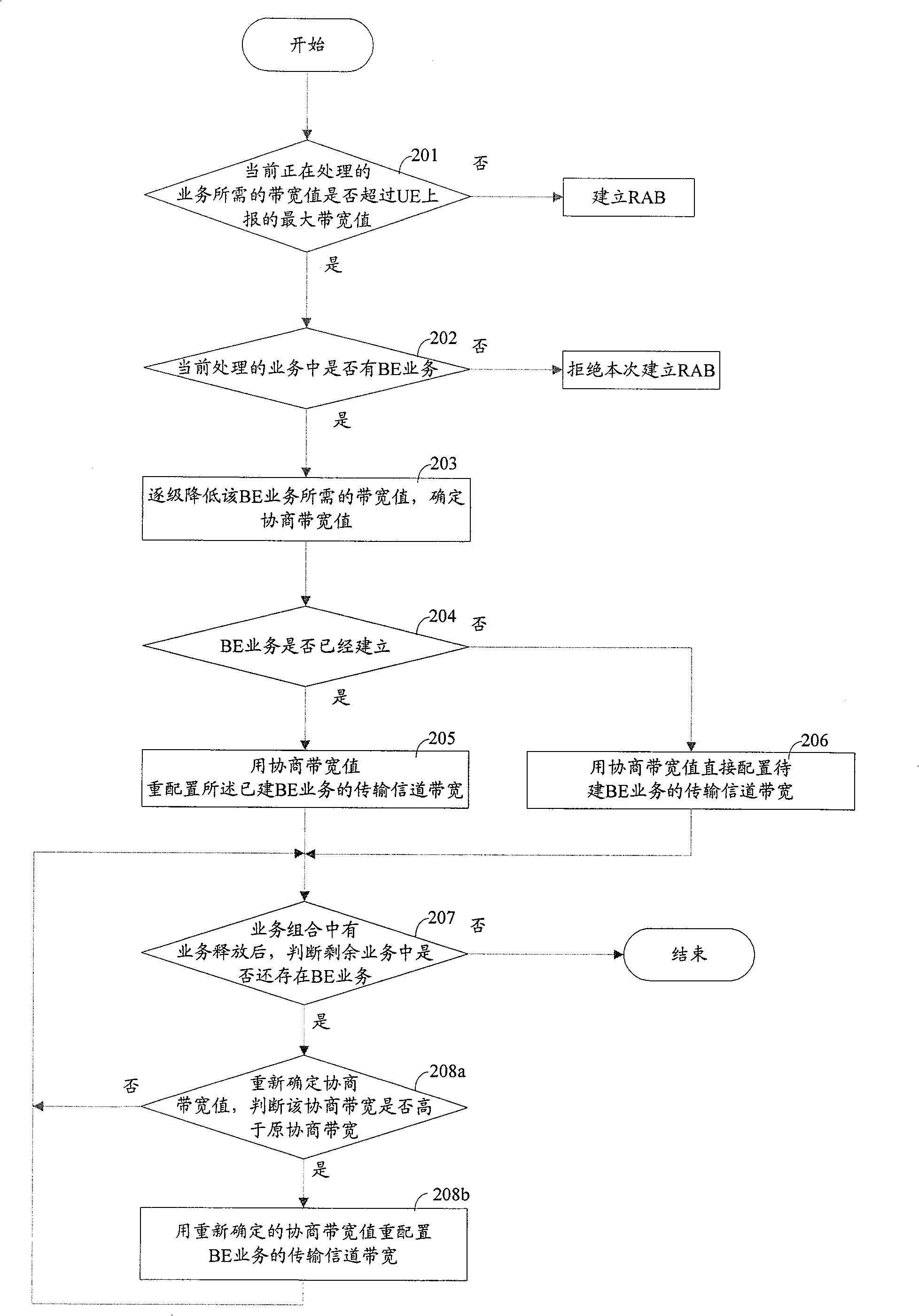
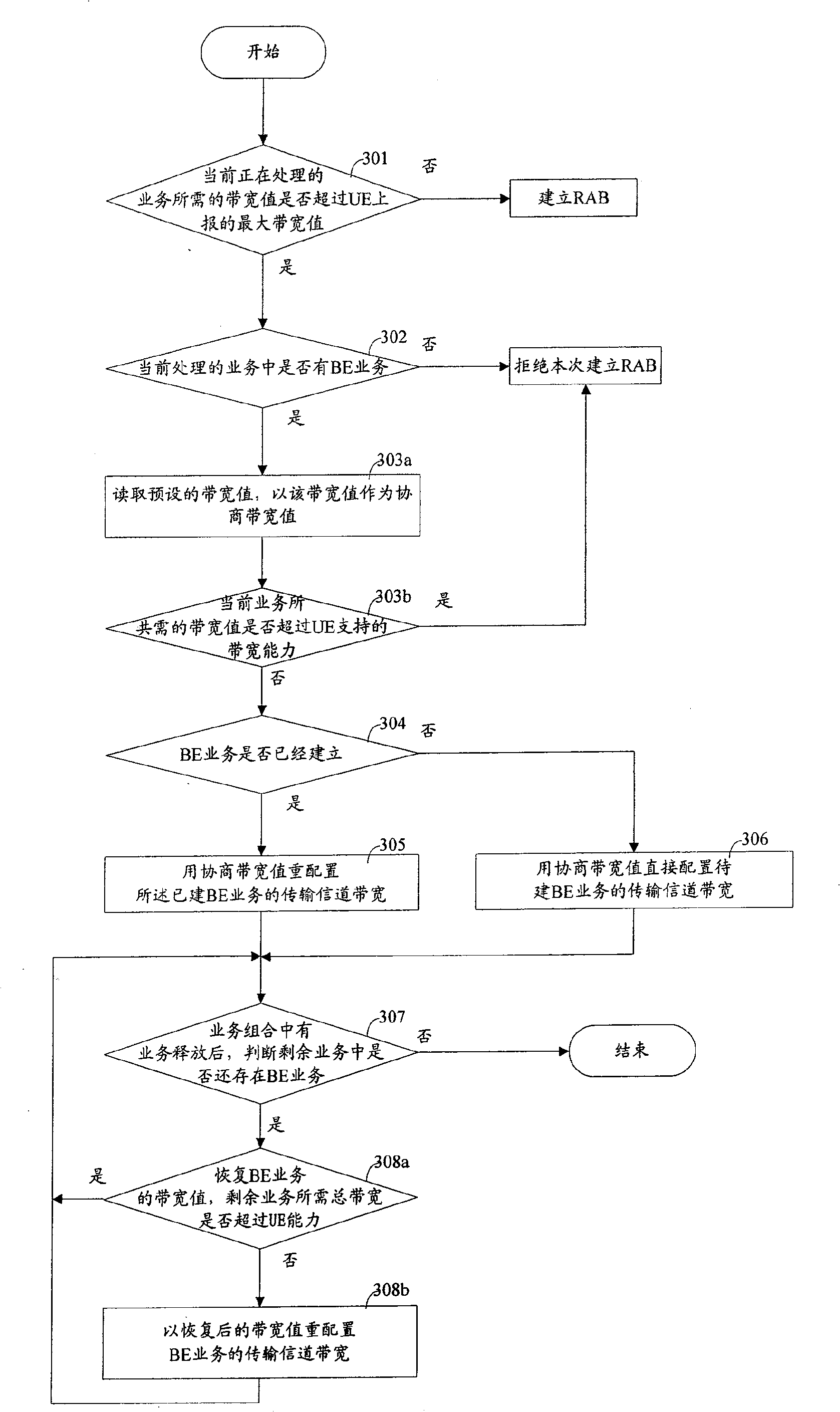
The invention relates to a method for improving the service building success in the mobile communication system, wherein, when the wireless network controller (RNC) receives the distribute request of building service, and judges out the bandwidth needed by present processed service is over the maximum bandwidth reported by the user terminal (UE), check if the present service contains the non real-time service; if contains, decrease the bandwidth needed by the non real-time service, and using said decreased bandwidth to distribute or redistribute the bandwidth transmission signal channel of said non real-time service. The invention can use present bandwidth resource of mobile communication system to improve the success rate of service building without improve the bandwidth ability of UE.
Owner:SHANGHAI HUAWEI TECH CO LTD
Two-D bar code reading method and appts. thereof
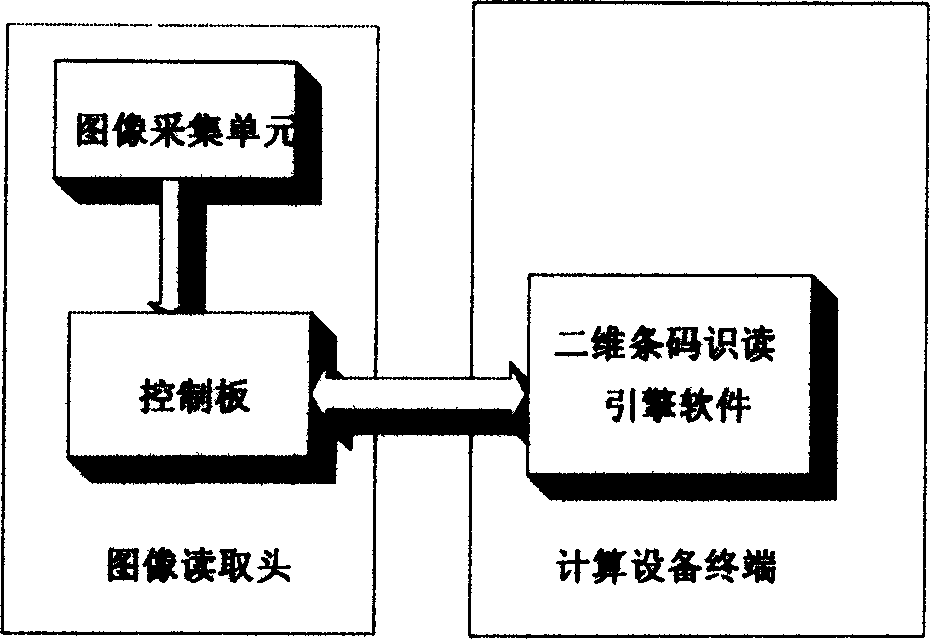
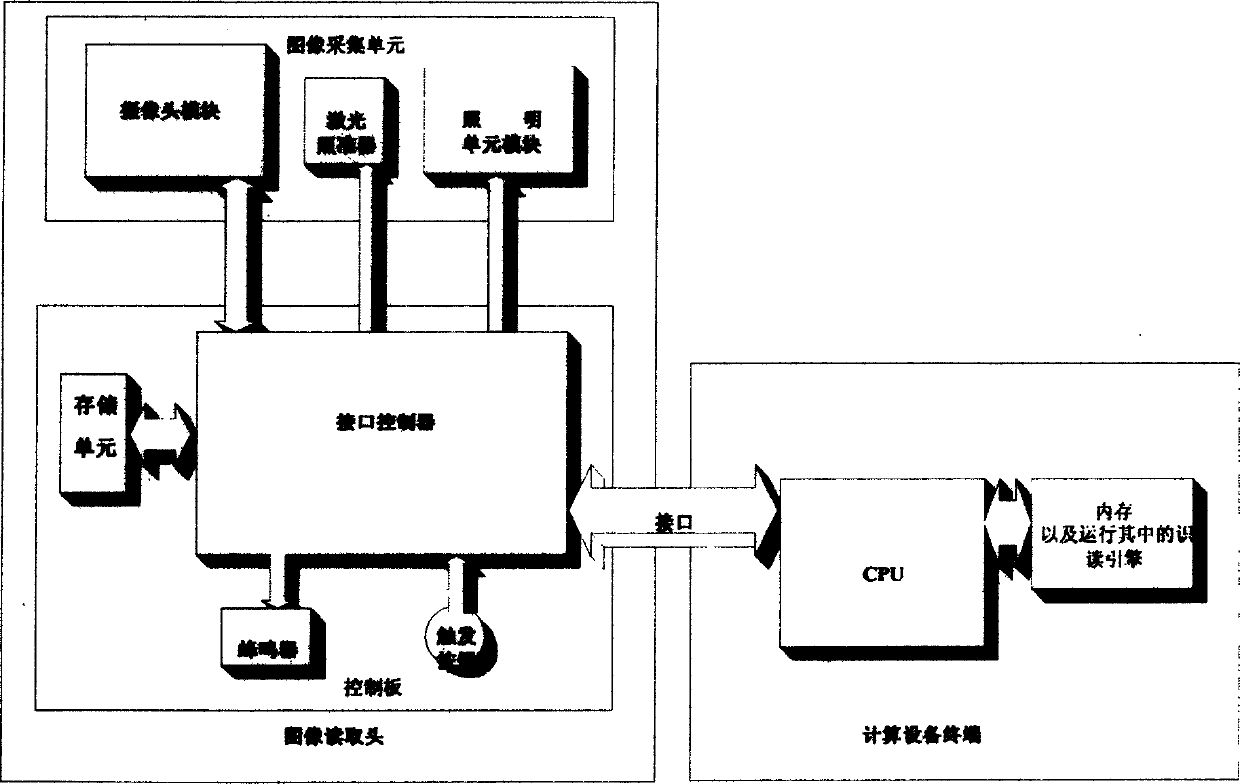
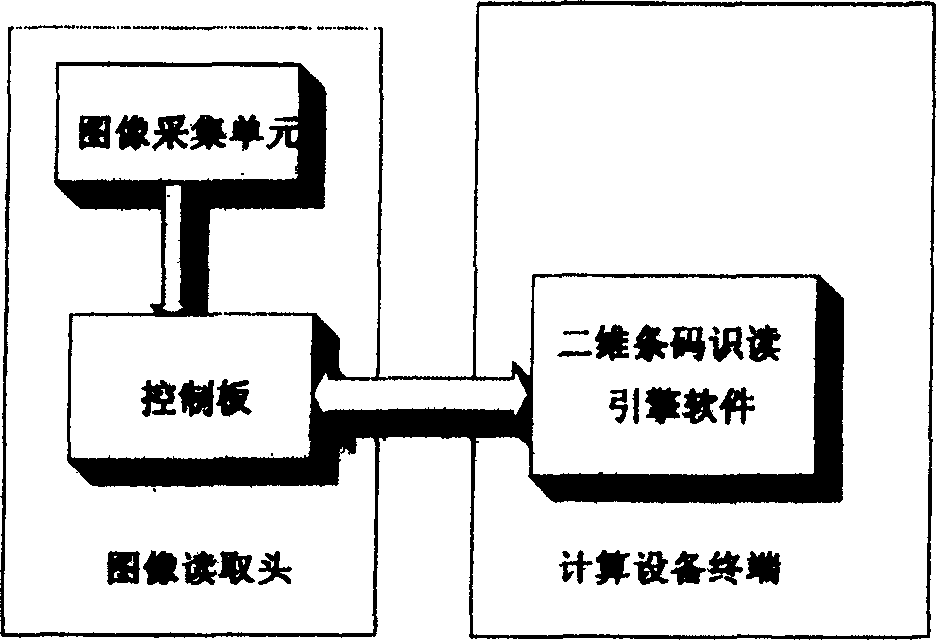
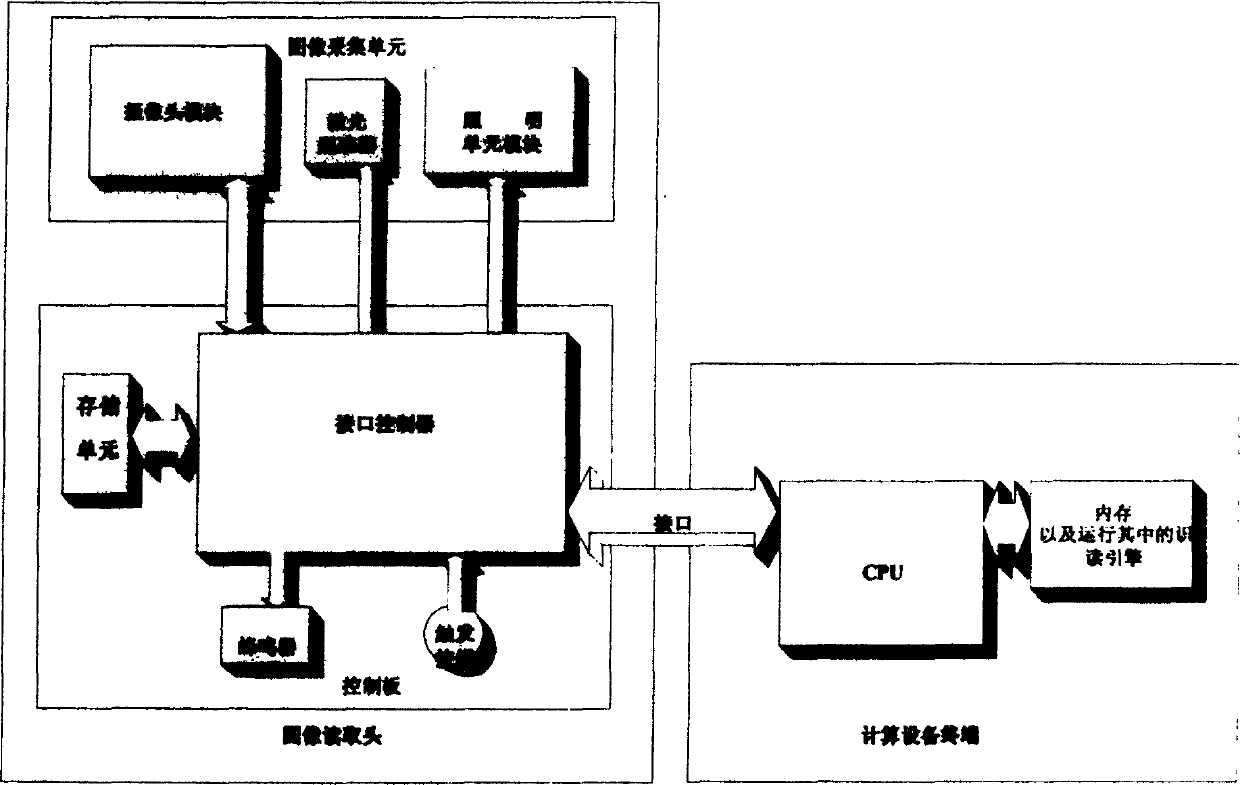
ActiveCN1564185ALiteracy realizationReduce manufacturing costCharacter and pattern recognitionSensing record carriersComputer terminalInterface circuits
A kind of 2D bar reader includes image reading head, terminal of computing device. The said image reading head through control interface circuit is connected to terminal of computing device with engine software for reading and recognizing bar code being installed on. The said terminal of computing device is one of desktop computer, server, palm computer, embedded type system or handset possible to install engine software for reading and recognizing bar code. It is initiation of the invention that recognition function is transferred to terminal of computing device connected. Thus, the image reading head possesses features of simple feature, easy of manufacture, high processing capacity, good recognition effect.
Owner:BEIJING INSPIRY XINCHUANG TECH
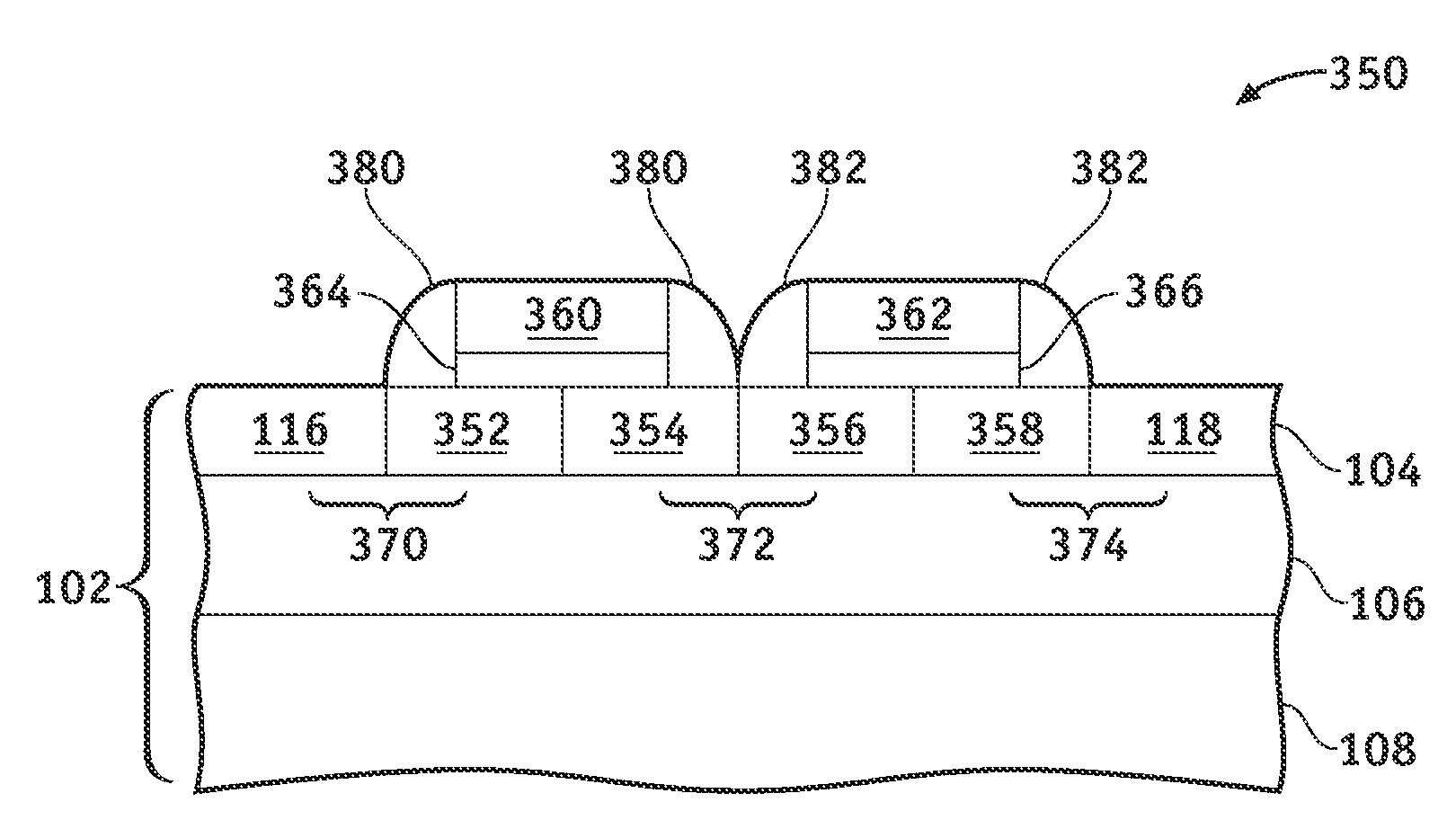
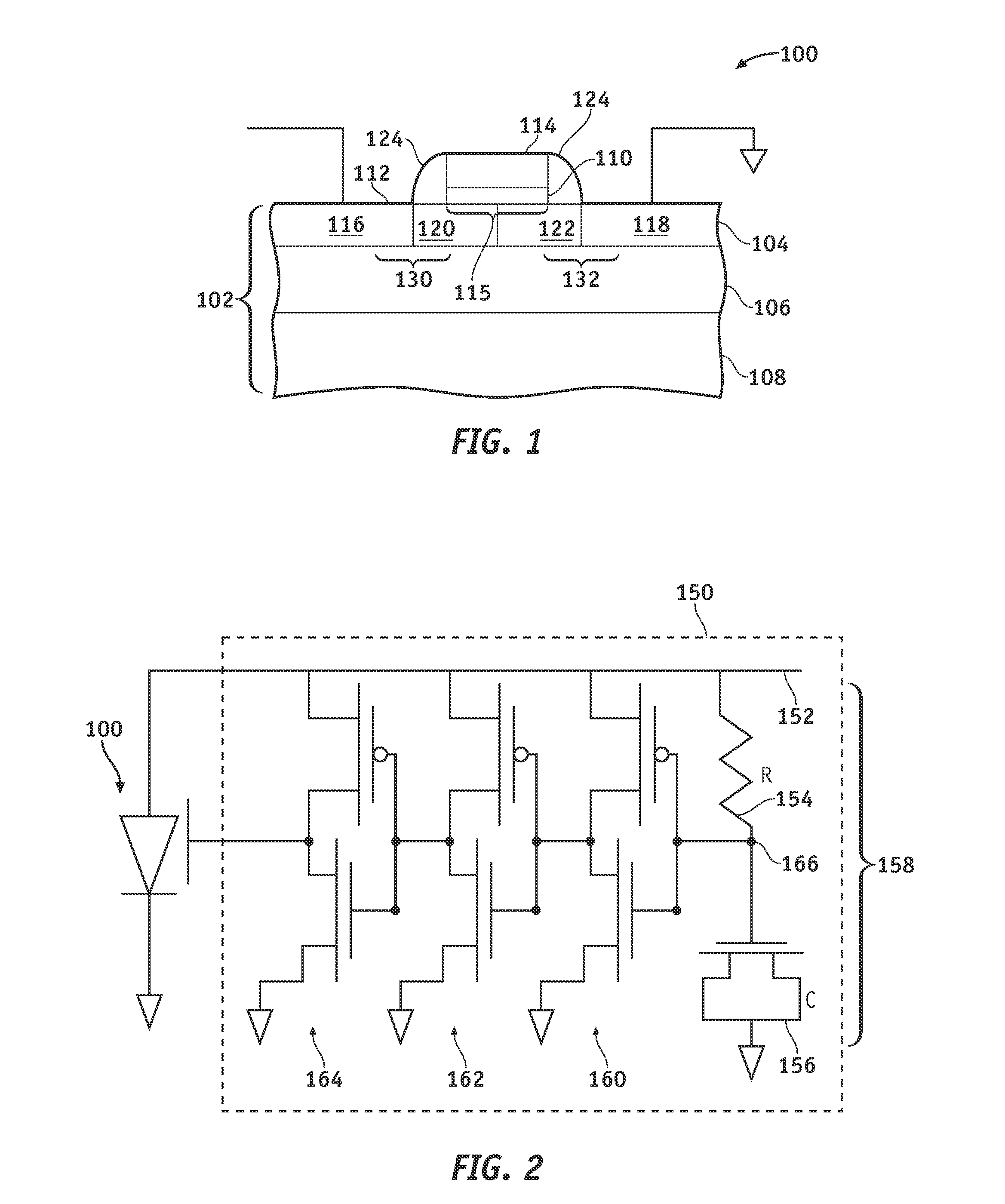
Electrostatic discharge protection devices and methods for protecting semiconductor devices against electrostatic discharge events
ActiveUS20080087962A1Protection inputTransistorSemiconductor/solid-state device detailsElectrostatic discharge protectionAnode
Methods and devices are provided for protecting semiconductor devices against electrostatic discharge events. An electrostatic discharge protection device comprises a silicon substrate, a P+-type anode region disposed within the silicon substrate, and an N-well device region disposed within the silicon substrate in series with the P+-type anode region. A first P-well device region is disposed within the silicon substrate in series with the first N-well device region and an N+-type cathode region is disposed within the silicon substrate. A gate electrode is disposed at least substantially overlying the first N-well and P-well device regions of the silicon substrate.
Owner:ADVANCED MICRO DEVICES INC
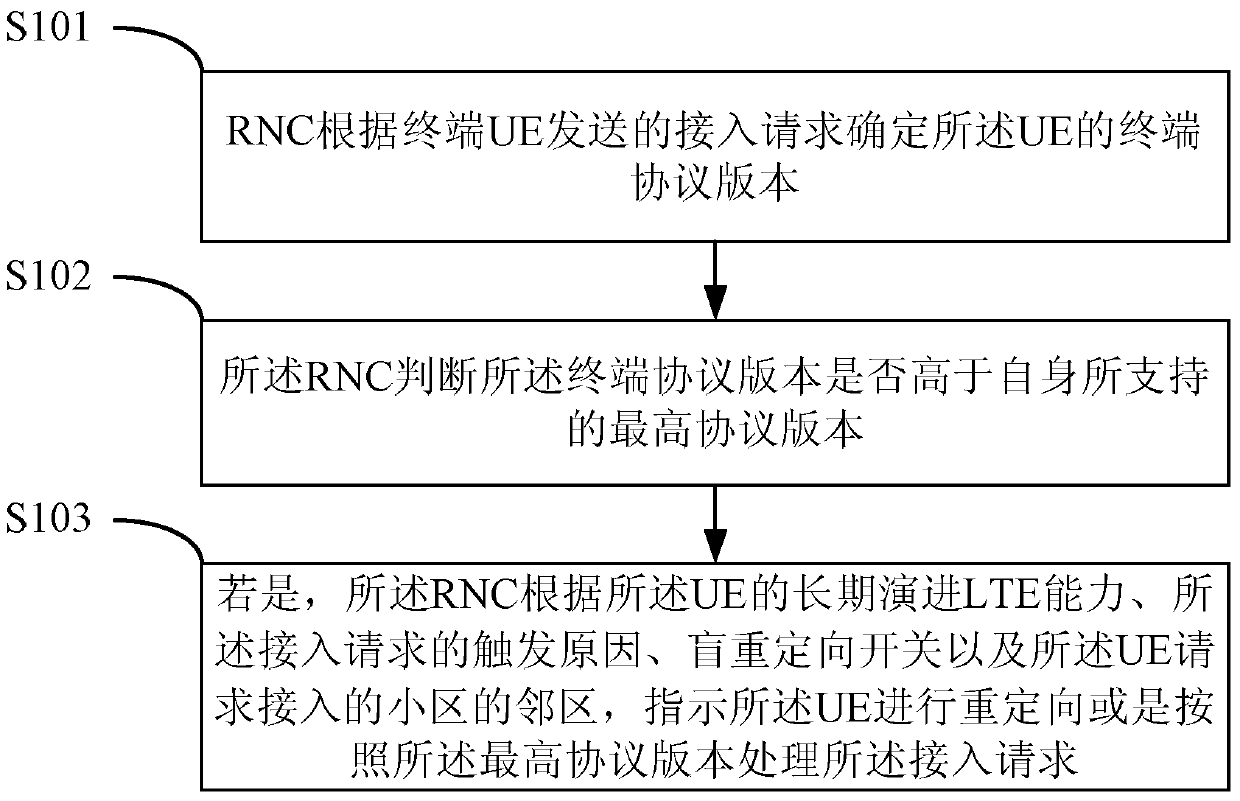
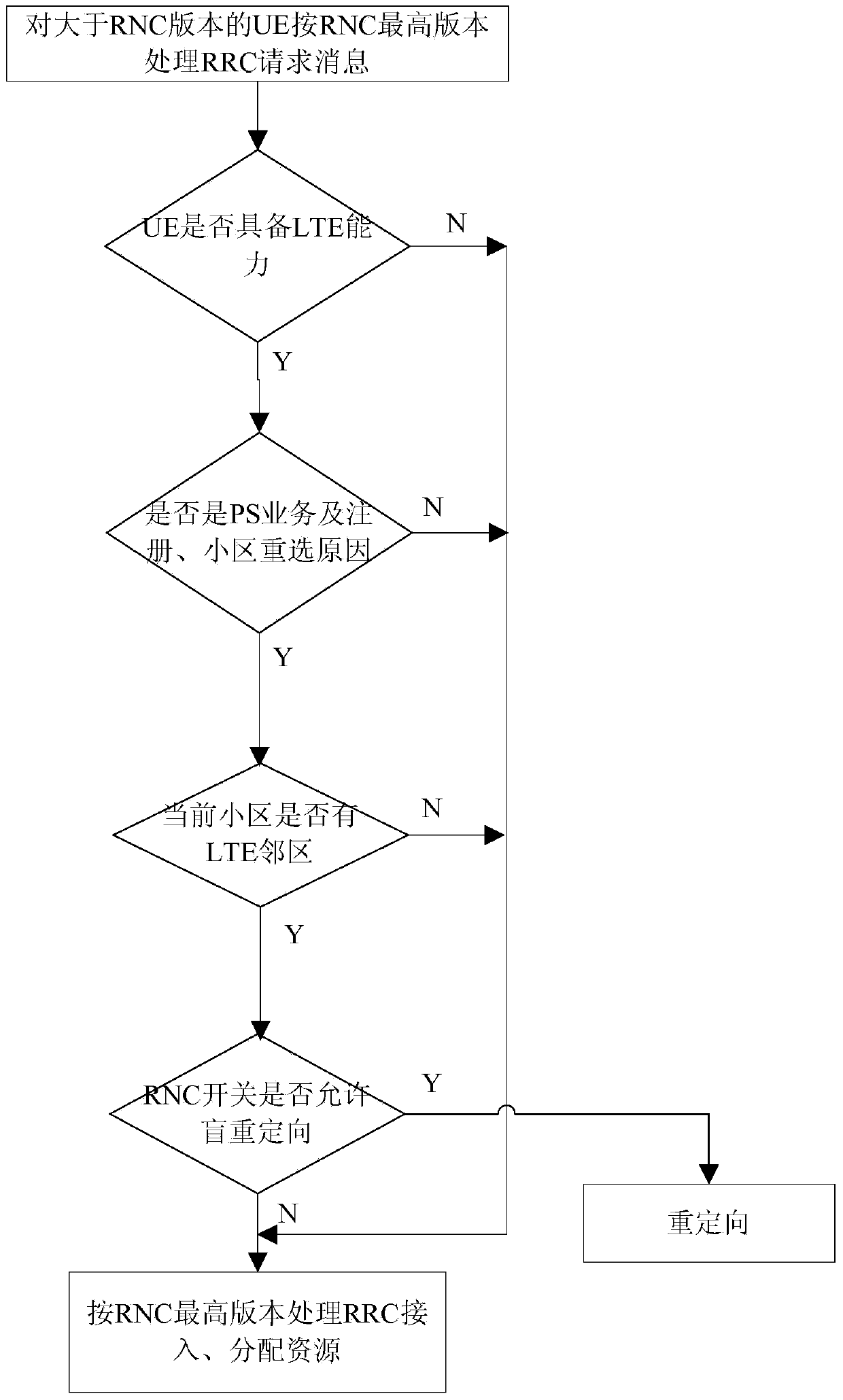
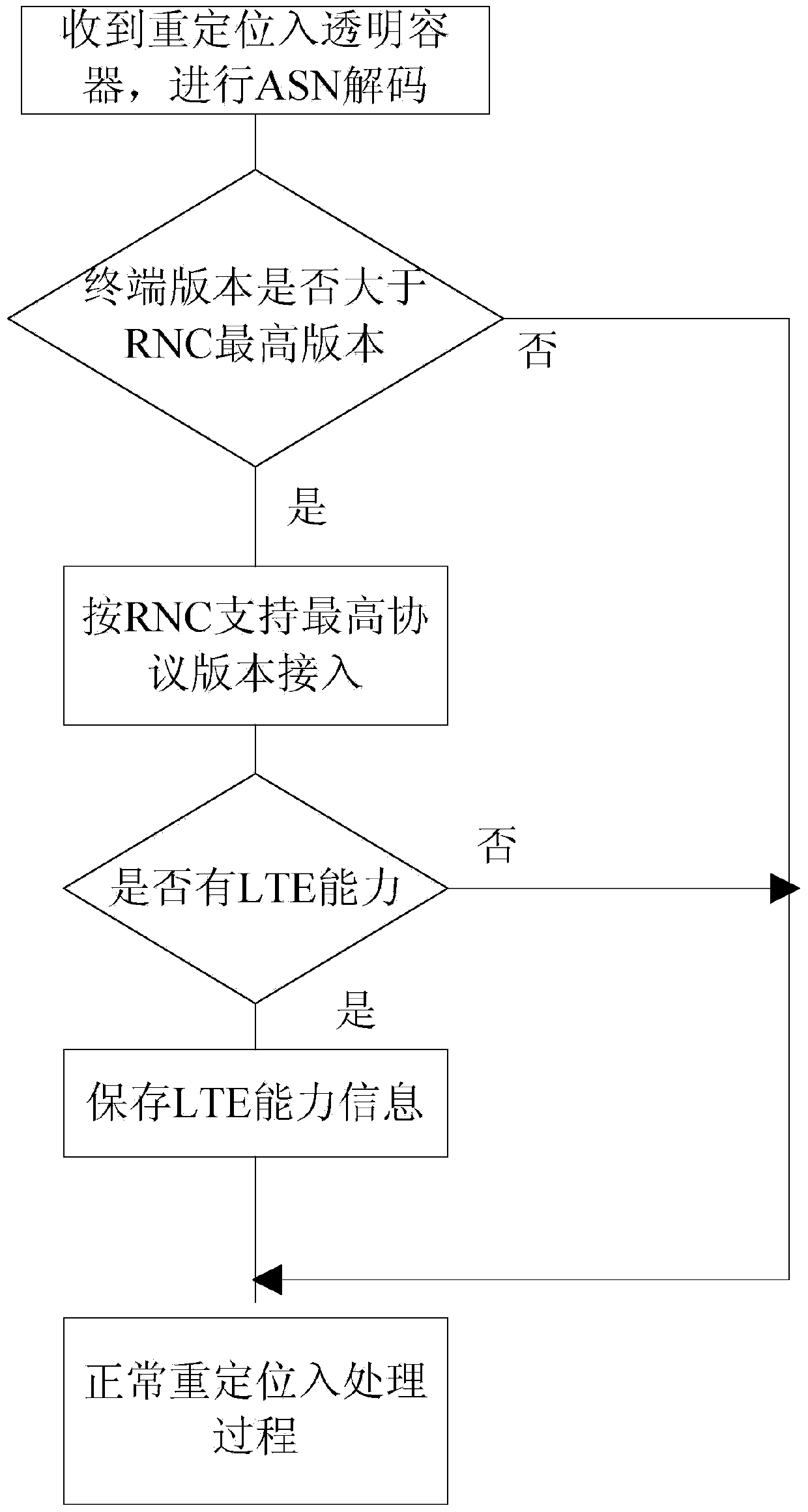
Terminal UE access control method and device
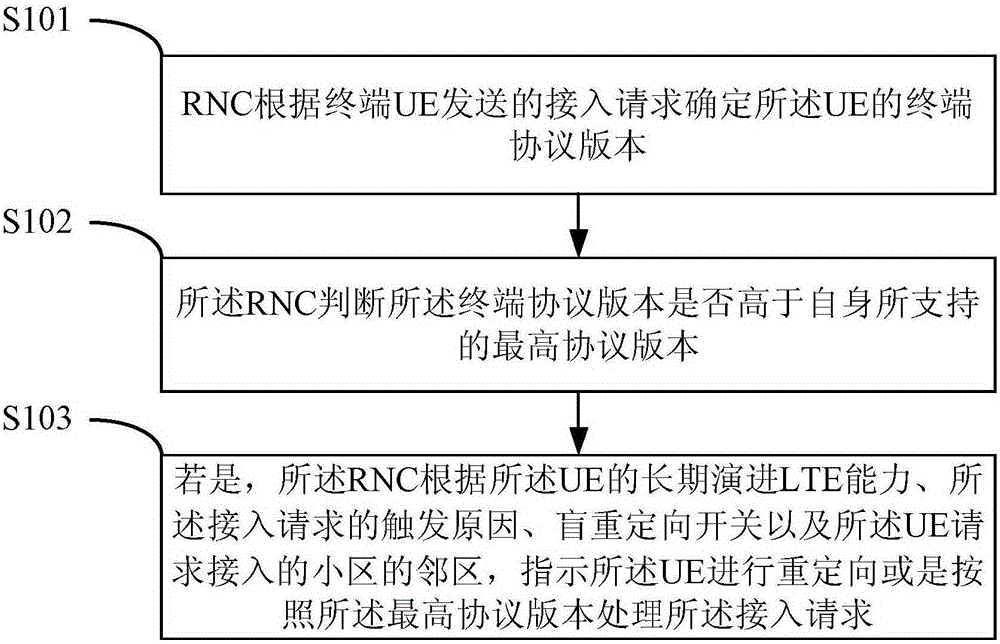
ActiveCN106550413AImprove access success rateGuarantee perceptionWireless communicationUser perceptionUsers perceptions
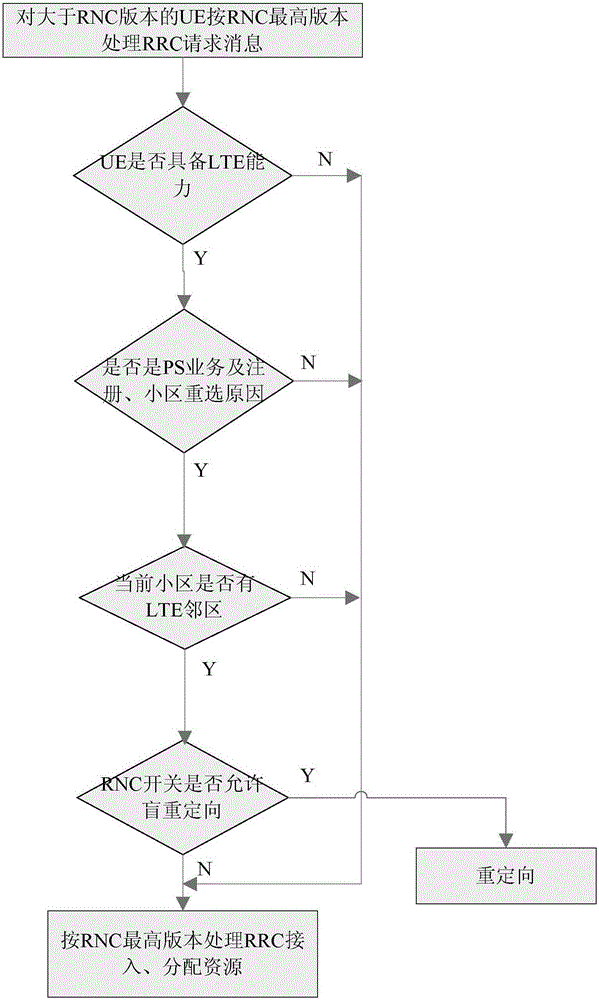
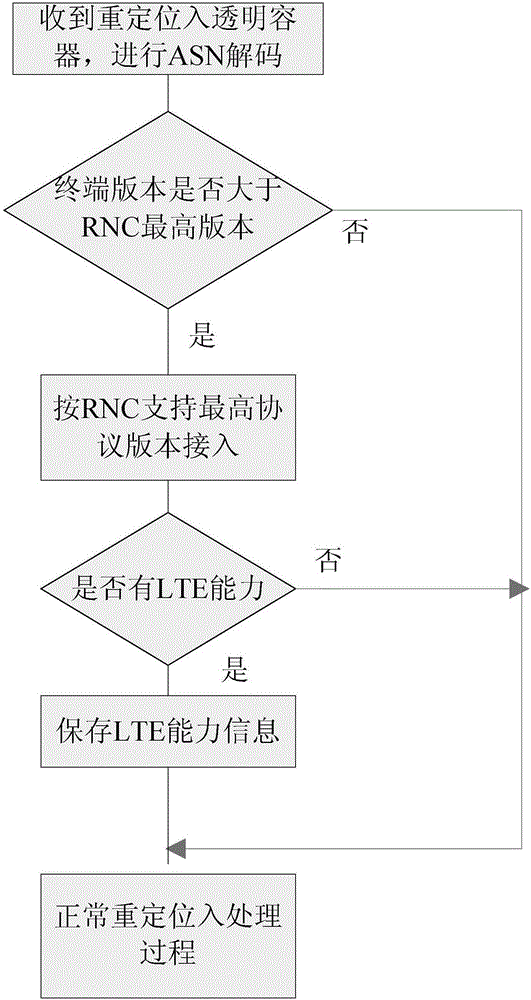
The application discloses a terminal UE access control method. After determining the terminal protocol version of terminal UE according to an access request sent by the terminal UE, an RNC (Radio Network Controller) judges whether the terminal protocol version is higher than the highest protocol version supported. If the terminal protocol version is higher than the highest protocol version supported, the UE is redirected under instruction according to the LTE capacity of the UE, the reason why the access request is triggered, a blind redirection switch and the neighborhood of a cell which the UE requests to access, or the access request is processed in accordance with the highest protocol version. The success rate of RRC access and the success rate of relocation are improved, user perception is ensured, and the investment of operators is protected.
Owner:DATANG MOBILE COMM EQUIP CO LTD
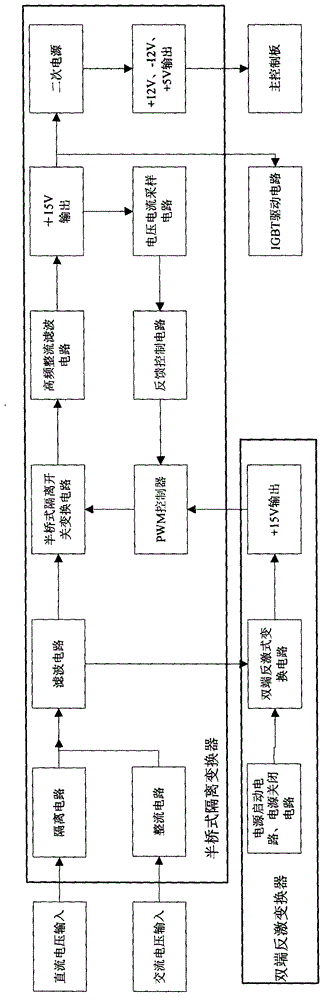
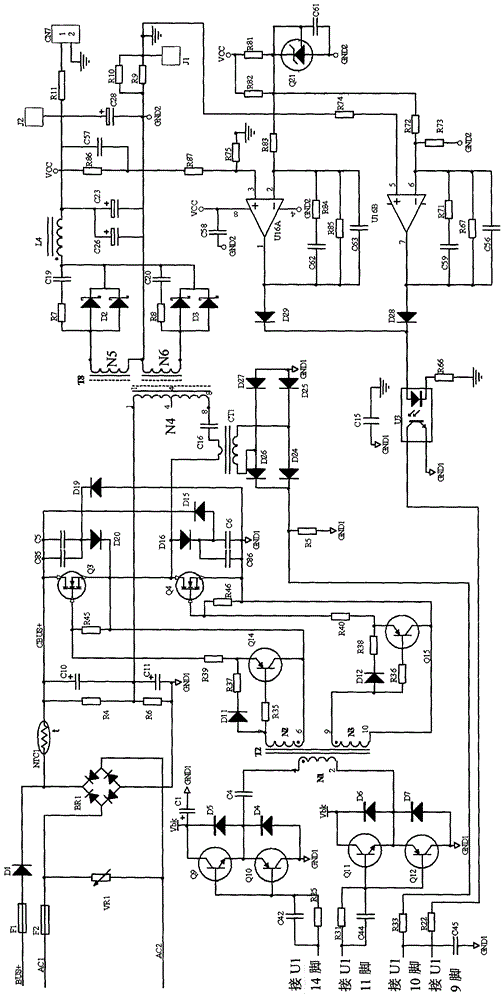
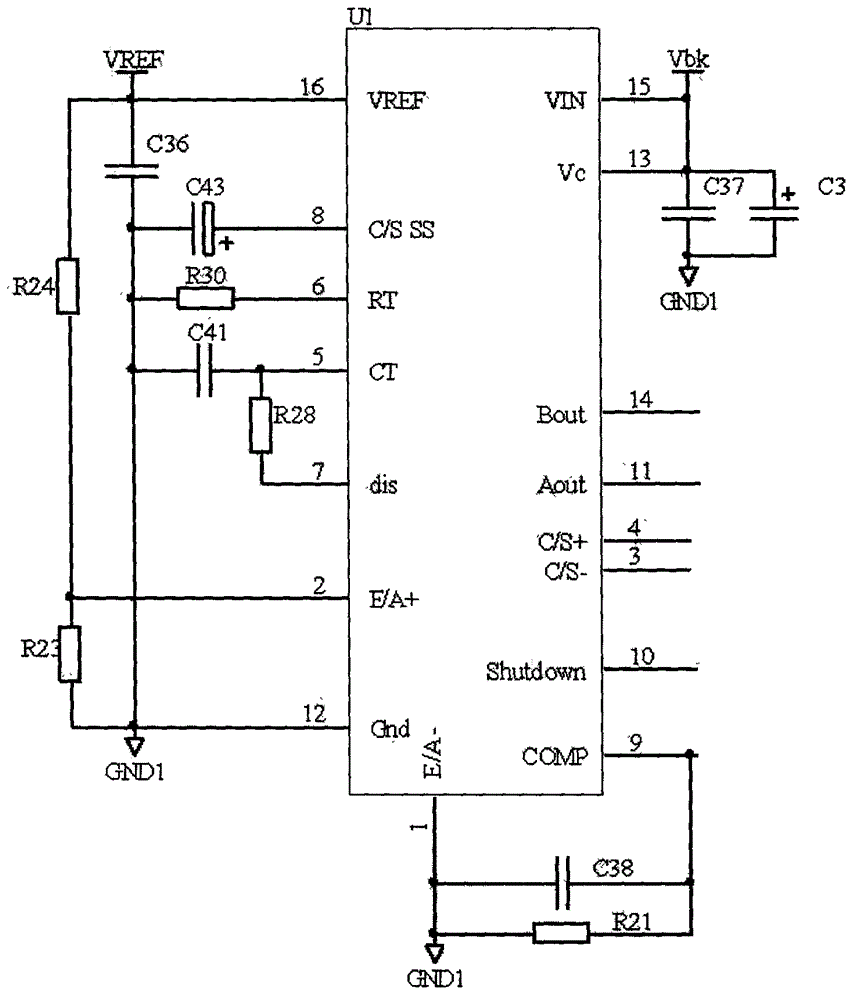
Auxiliary power supply of high-power UPS (uninterrupted power supply)
ActiveCN102832694AAvoid current stressStable jobEmergency power supply arrangementsEngineeringFly back converter
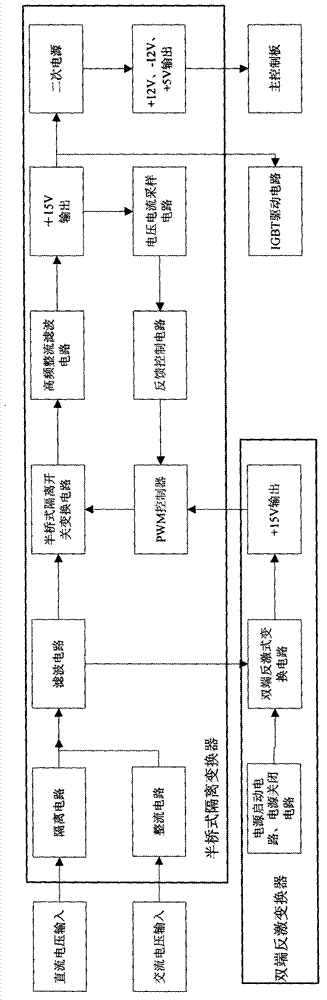
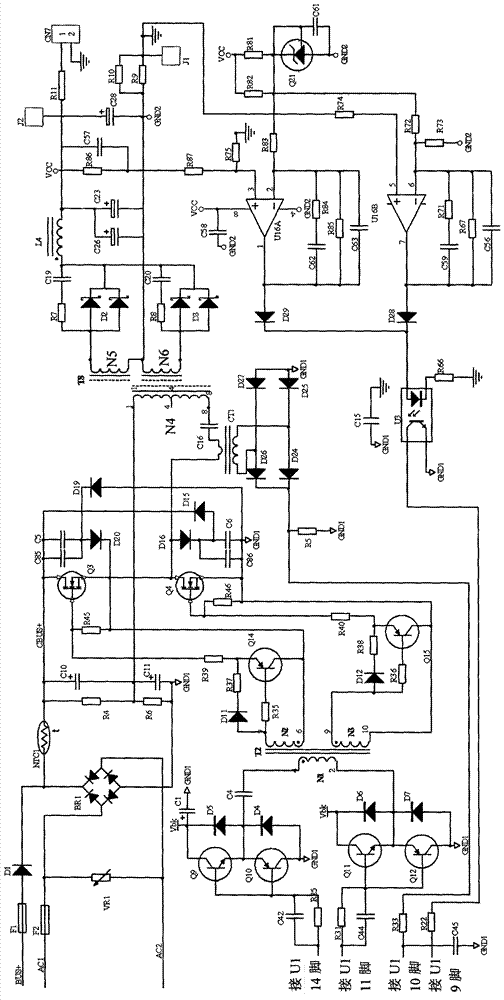
The invention discloses an auxiliary power supply of a high-power UPS (uninterrupted power supply). The auxiliary power supply comprises a direct-current voltage input, an alternating-current voltage input, an isolating circuit for preventing reverse-filling of current, a rectification circuit, a filter circuit, a half-bridge isolating switch conversion circuit, a high-frequency rectification filter circuit, a voltage and current sampling circuit, a feedback control circuit, a PWM (pulse width modulation) controller and a double-end fly-back converter. The direct-current voltage input is sequentially isolated and filtered via the isolating circuit and the filter circuit, is converted into high-frequency PWM alternating-current voltage by the half-bridge isolating switch conversion circuit, and is isolated, coupled, rectified and filtered by the high-frequency rectification filter circuit, and then direct-current voltage is output. The half-bridge isolating switch conversion circuit is controlled by the PWM controller to output stabilized direct-current voltage. An input end of the double-end fly-back converter is connected with an output end of the filter circuit so that the double-end fly-back converter can access to a power source, and the double-end fly-back converter supplies power to the PWM controller. The auxiliary power supply of the high-power UPS can supply reliable and stable direct-current voltage output to the UPS.
Owner:FOSHAN BAYKEE NEW ENERGY TECH INC
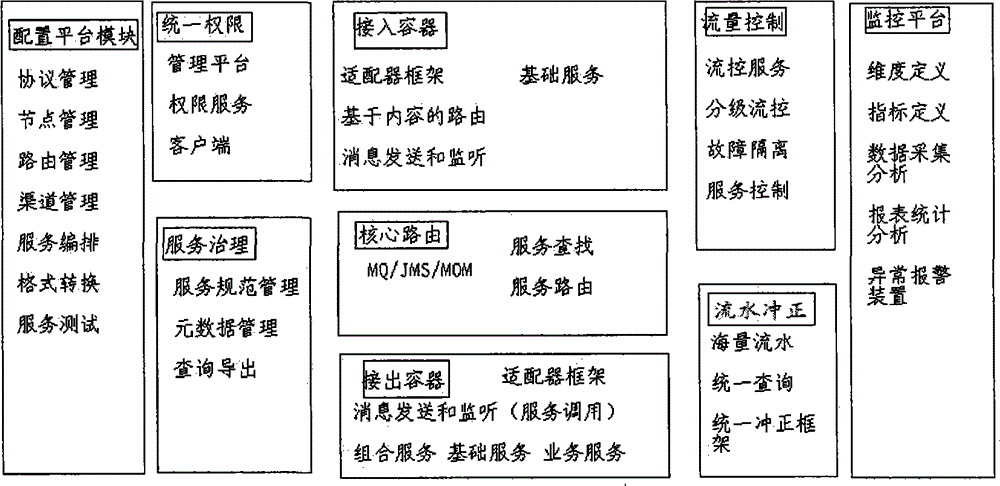
Basic information interaction system
InactiveCN104158721AGuaranteed normal executionGuaranteed uptimeData switching networksInteraction systemsStatistical analysis
The invention discloses a basic information interaction system. The basic information interaction system comprises a configuration platform module, a unified authority management module, a service governing module, a reception container module, an outlet container module, a core route module, a flow rate control module, a flowing water reversing module and a monitor platform module, wherein the service governing module is used for service standard management, metadata management and enquiry export; the core route module is used for service search and route service, supports various communication protocols, and supports extension of a communication protocol; the monitor platform is used for dimension defining, index defining, data acquisition analysis, statement statistical analysis and warning mechanism; the system further comprises a load balancing device. The system utilizes the separation function and the channel detection function of the load balancing device to realize separation of system failure; the service standard management comprises establishment of service specification and technical specification of a bank; the service governing module is further used for realizing management of whole life cycle of bank services.
Owner:神州数码融信软件有限公司
Securing data in a networked environment
ActiveUS8341756B2Protection inputProgram control using stored programsDigital data processing detailsSafe handlingData channel
Apparatus for securing data, comprising: an isolated processing environment having a boundary across which data cannot cross and a channel for allowing data to cross the boundary. A filter restricts data passage across the channel. Protected data is initially located in a secure area and is only released to such a secure processing environment so that access for authorized users to the secure data is available, but subsequent release of the secure data by the authorized users to the outside world is controlled.
Owner:MICROSOFT TECH LICENSING LLC
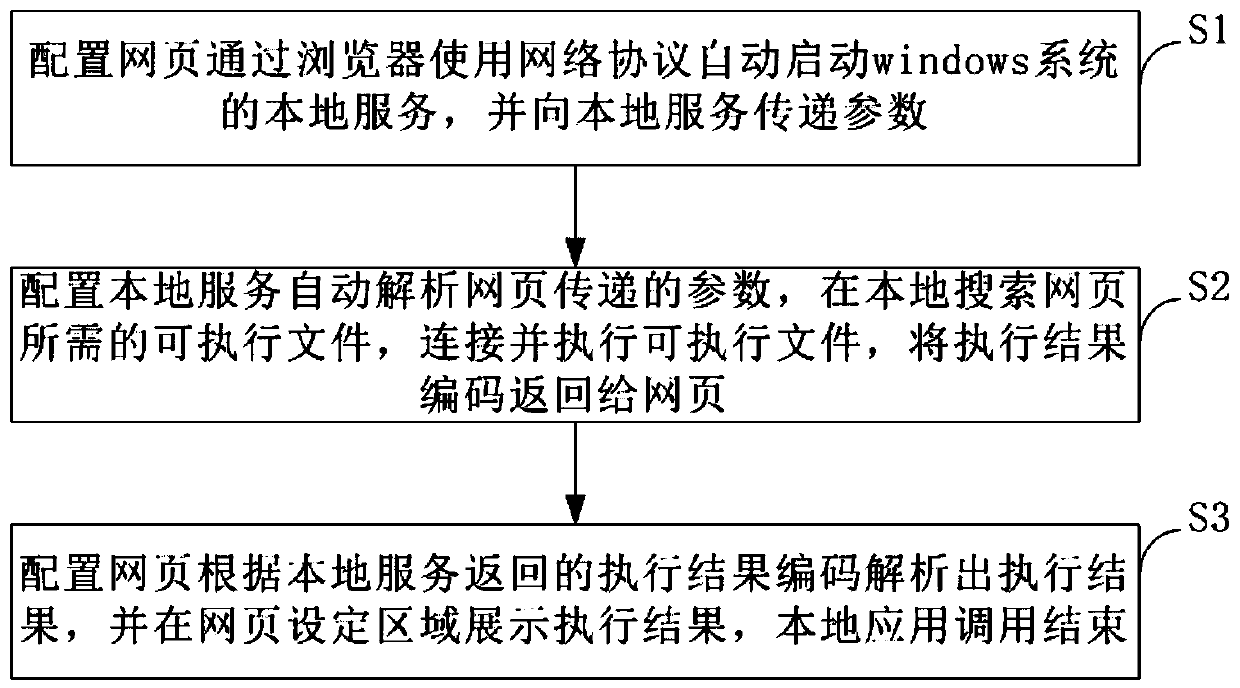
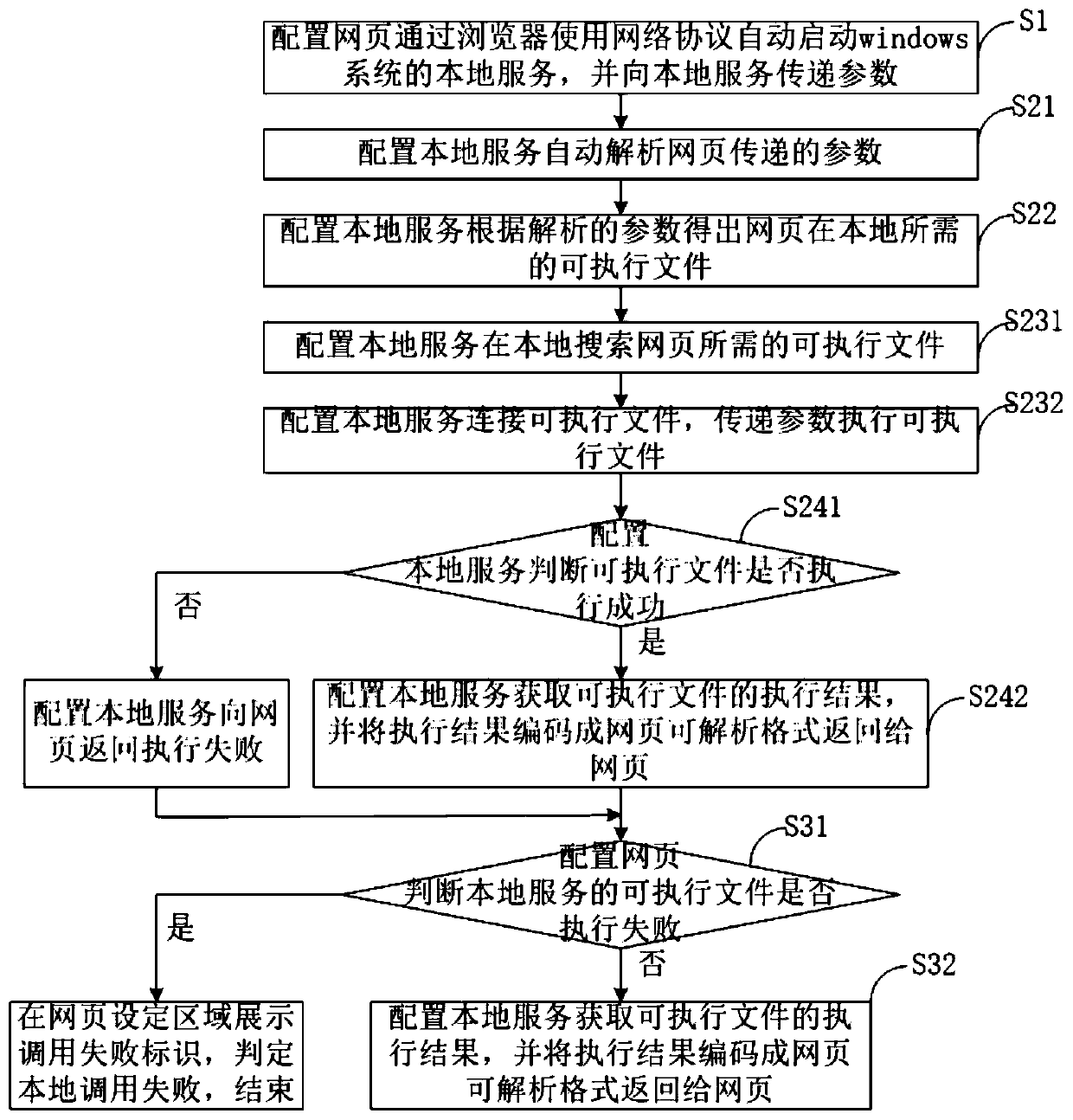
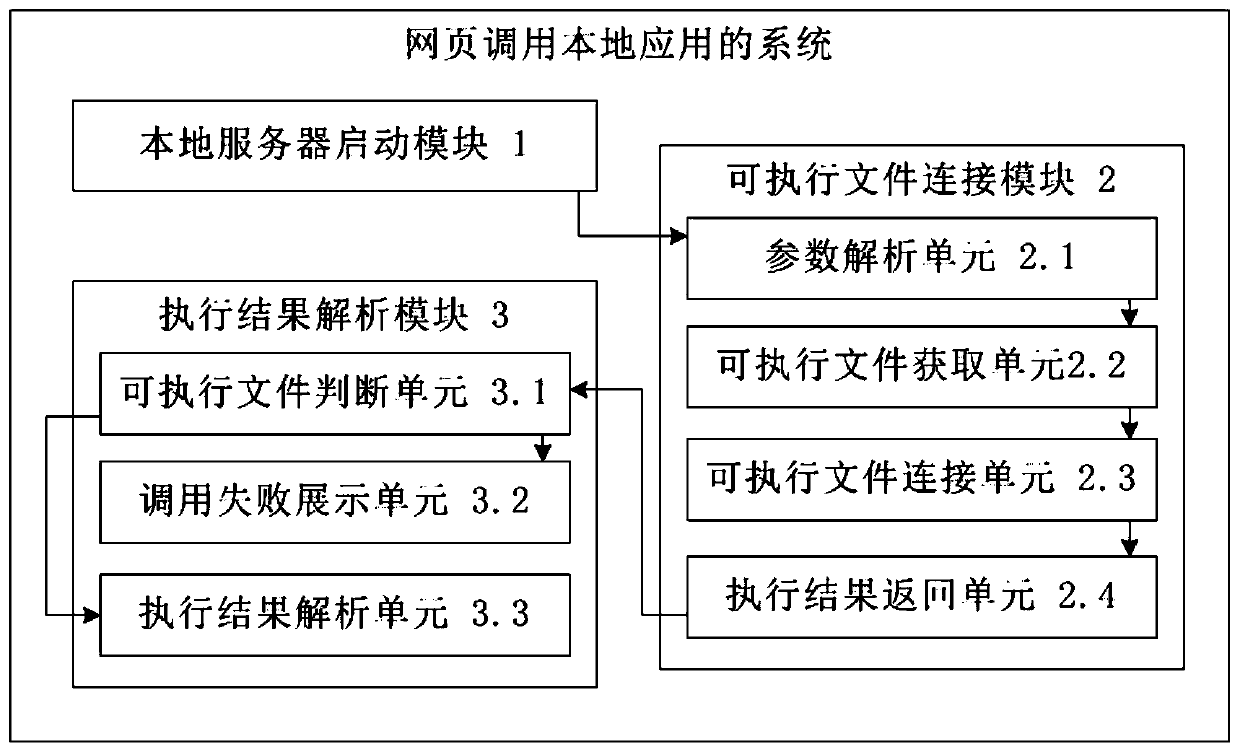
Method and system for calling local application by webpage
InactiveCN111338707AProtection inputImprove investment utilizationProgram loading/initiatingNetworking protocolApplication procedure
The invention provides a method and system for calling a local application by a webpage, and the method comprises the following steps: S1, configuring the webpage, automatically starting a local service of a windows system through a browser by using a network protocol, and transmitting parameters to the local service; S2, configuring a local service to automatically analyze parameters transmittedby the webpage, locally searching an executable file required by the webpage, connecting and executing the executable file, and returning an execution result code to the webpage; S3, enabling the configuration webpage to analyze an execution result according to the execution result code returned by the local service, displaying the execution result in a webpage setting area, and ending local application calling, wherein the system comprises a local server starting module, an executable file connection module and an execution result analysis module. According to the invention, the original control or the local application program used as the local application does not need to be modified, and the effect that the webpage directly calls the control or the local application program is achievedby adding the local service.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
Rectangular band-pass filter having recesses of less than one-quarter wavelength depth formed therein for fitting a dielectric insert with a superconductive film within the recesses
Owner:INST OF PHYSICS - CHINESE ACAD OF SCI +3
Phased array antenna system
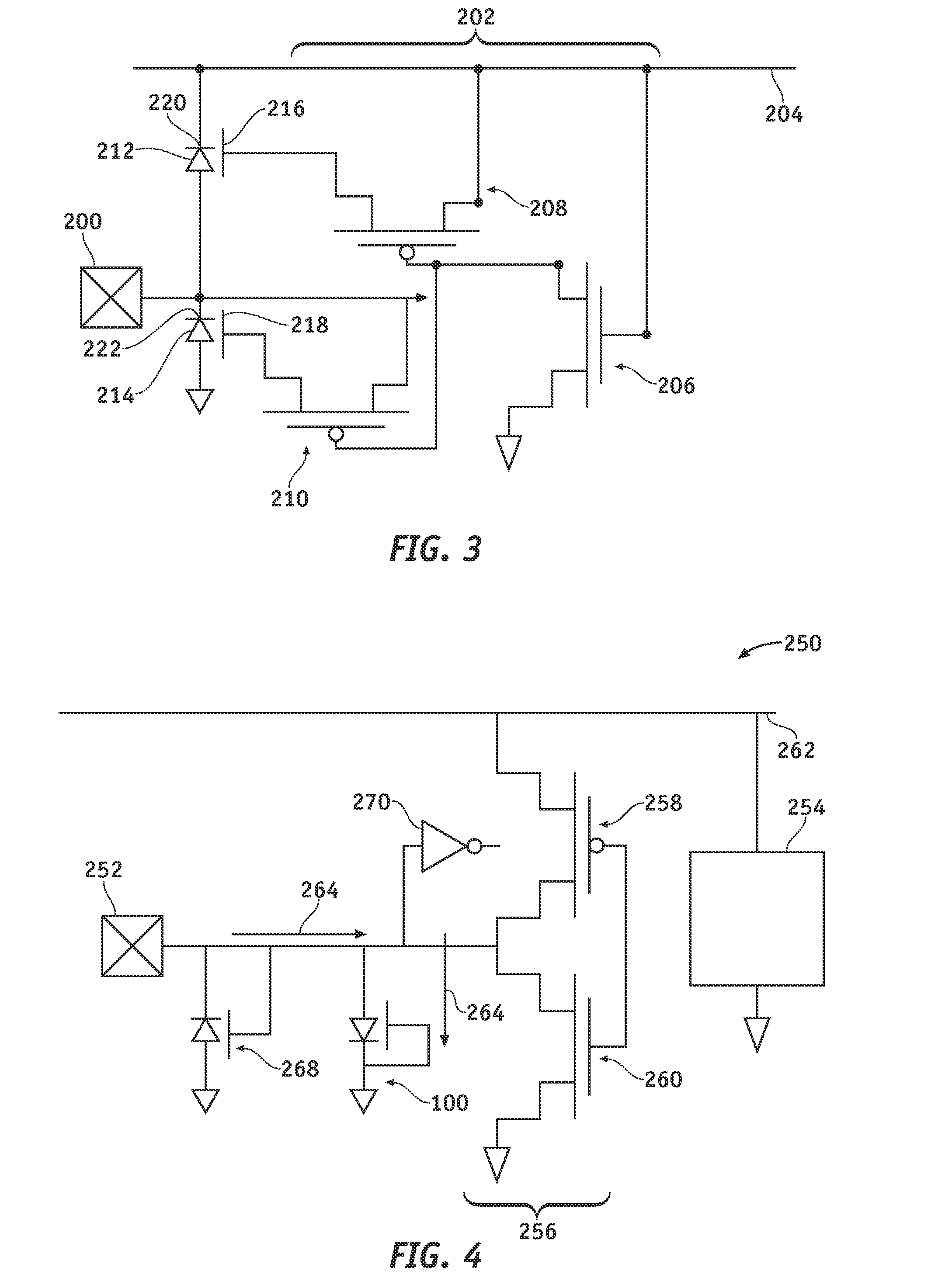
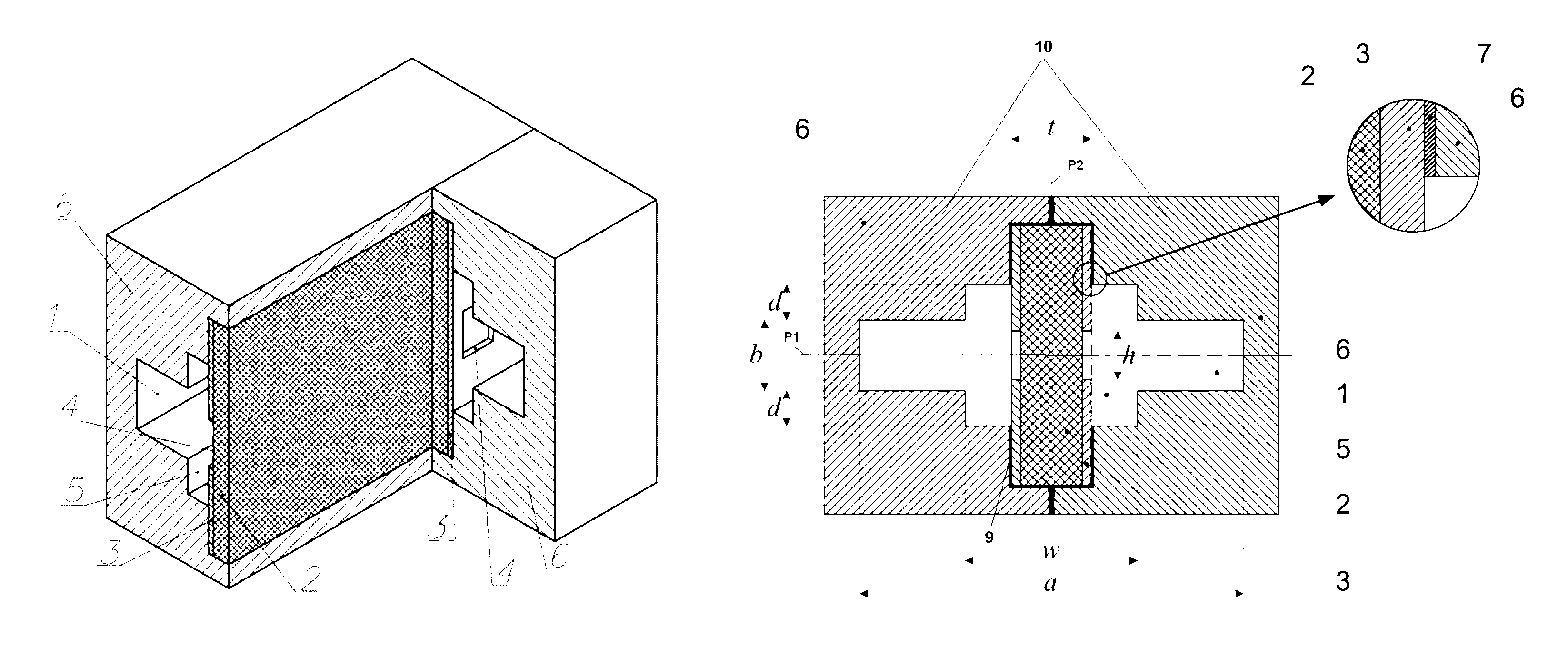
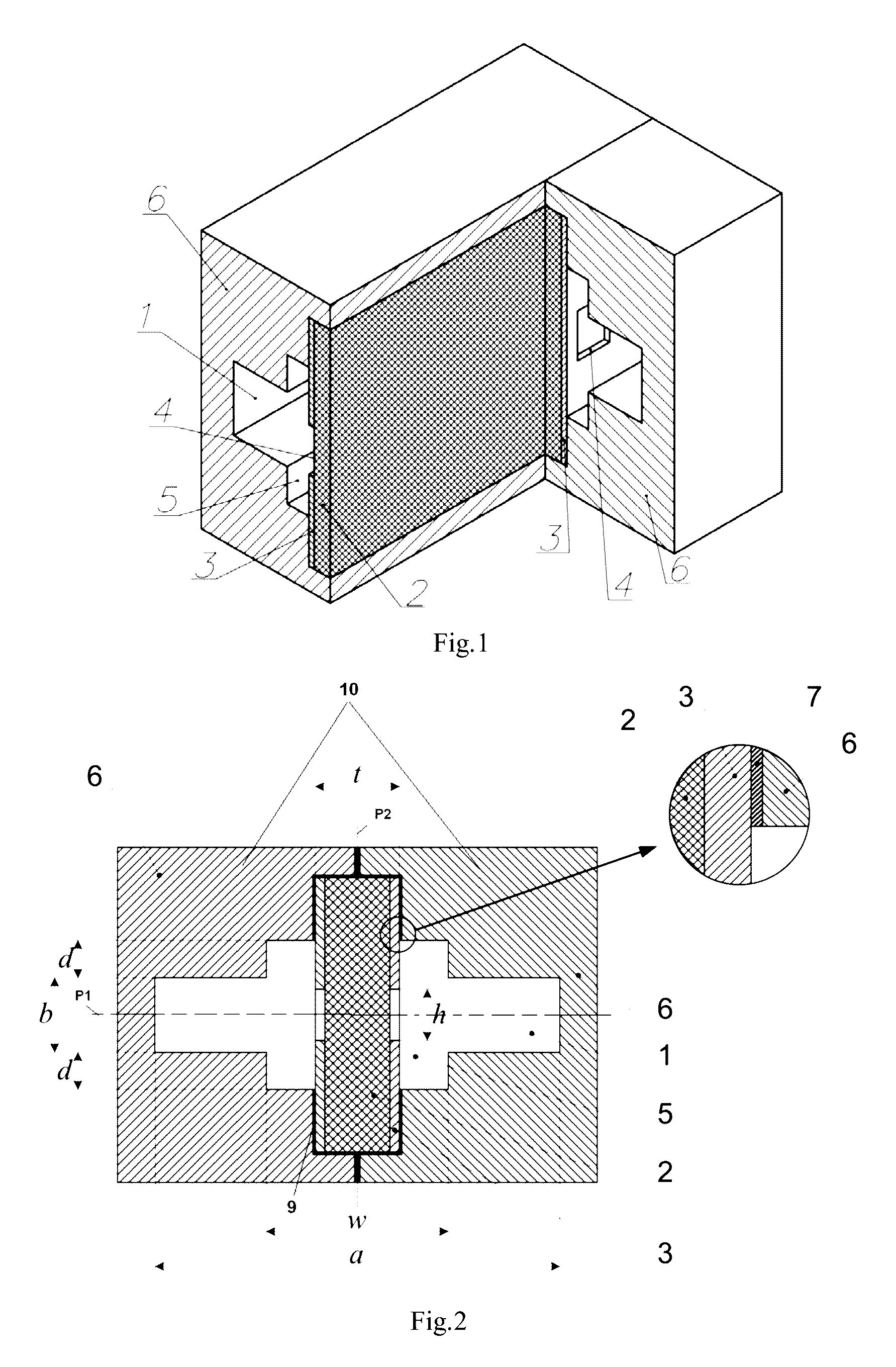
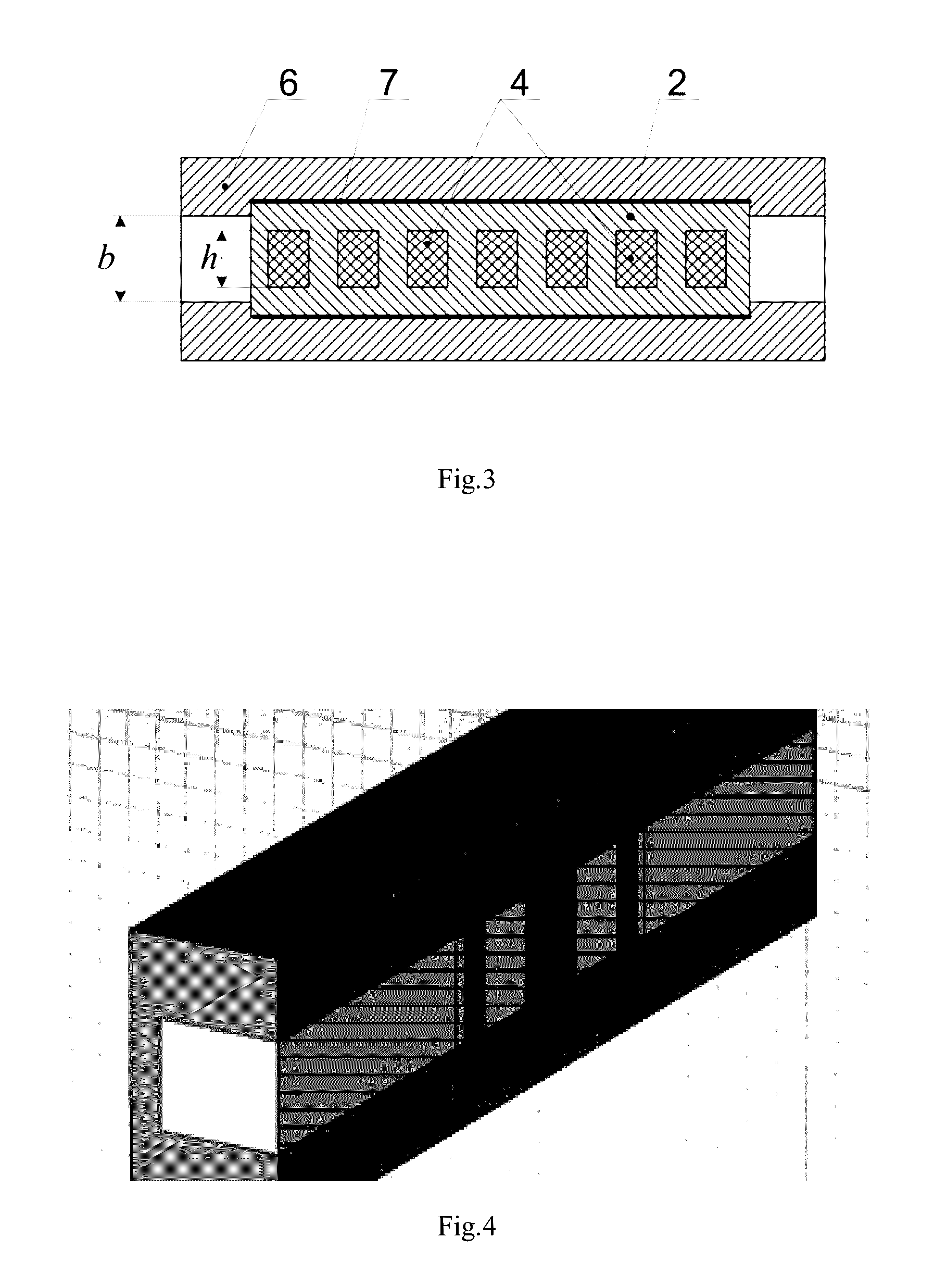
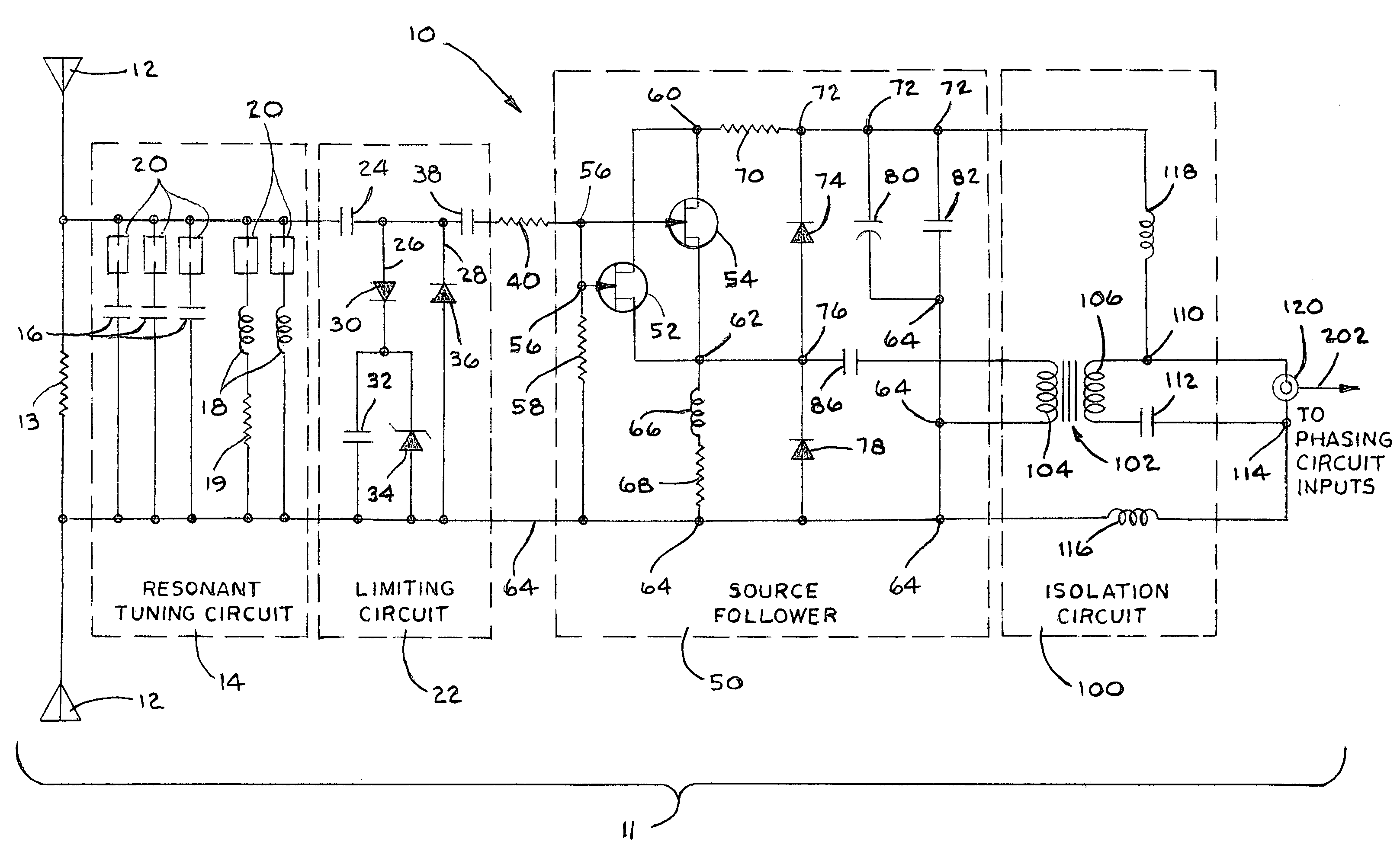
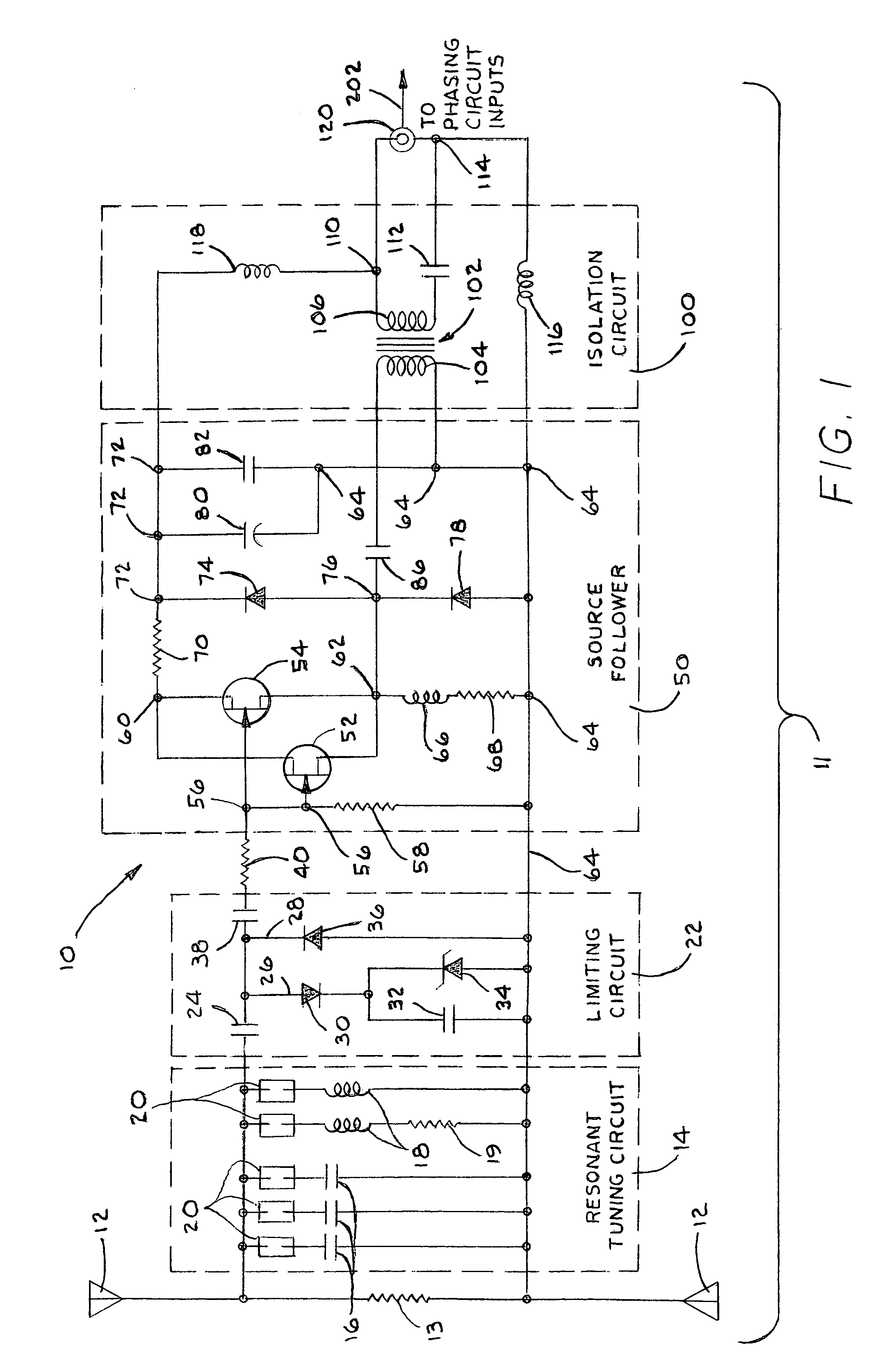
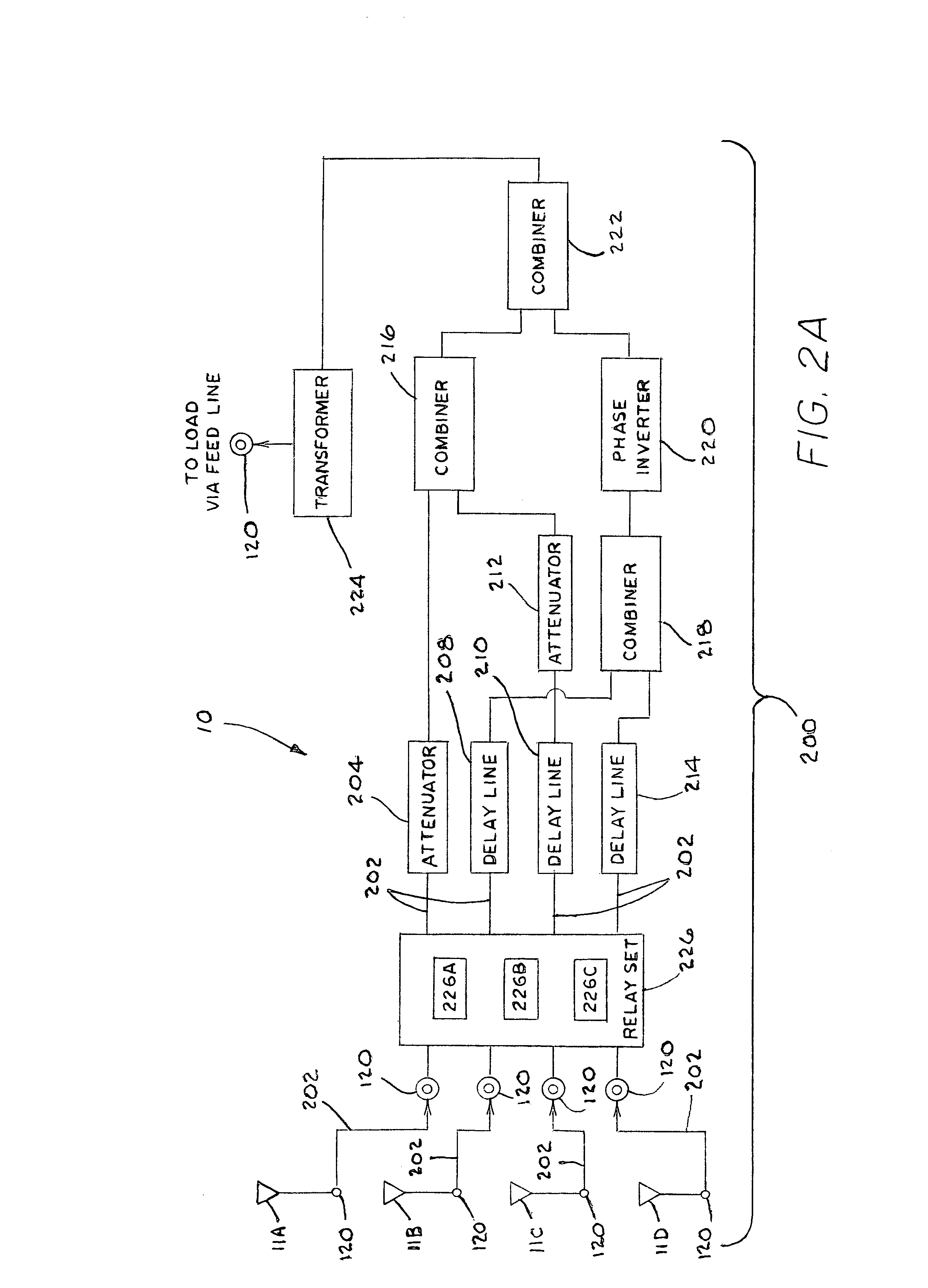
ActiveUS7423588B1Protection inputSolve narrow bandwidthRadio wave direction/deviation determination systemsAntennasElectricityZener diode
The present antenna system includes a phased array antenna system comprising a limiting circuit, an isolation circuit, and a phasing circuit. The limiting circuit includes a system of fast signal diodes coupled with a zener diode, which provides sharp limiting and increased limiting thresholds to received signals. In addition, the isolation circuit prevents a cable coupled to the output of the antenna unit from becoming electrically coupled with the antenna element itself. Furthermore, the phasing circuit allows the present antenna system to provide a null in a fixed direction over a wide bandwidth of signal receiving frequencies.
Owner:PDS ELECTRONICS
Method for user behavior analysis under https environment and system thereof
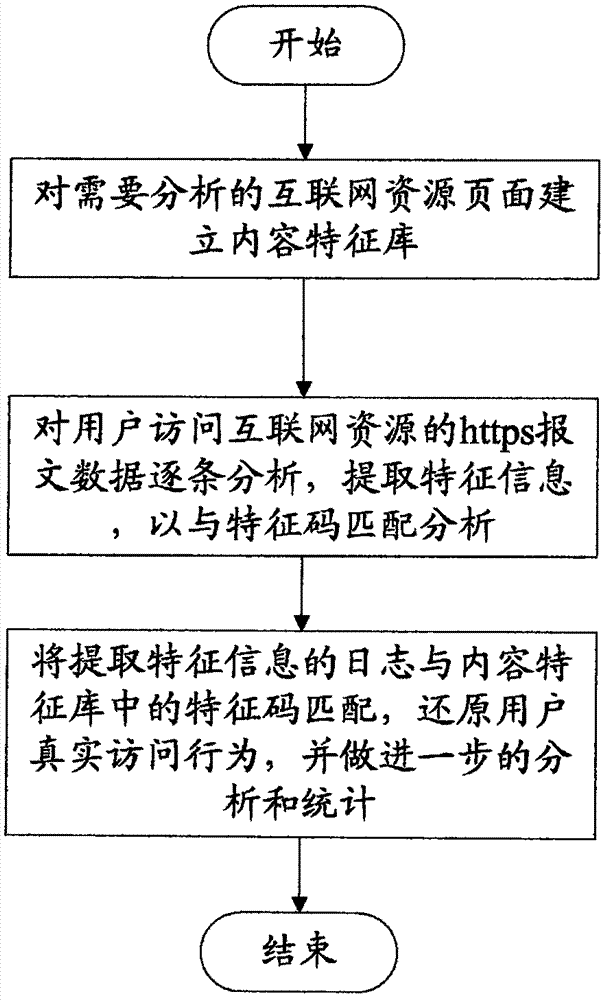
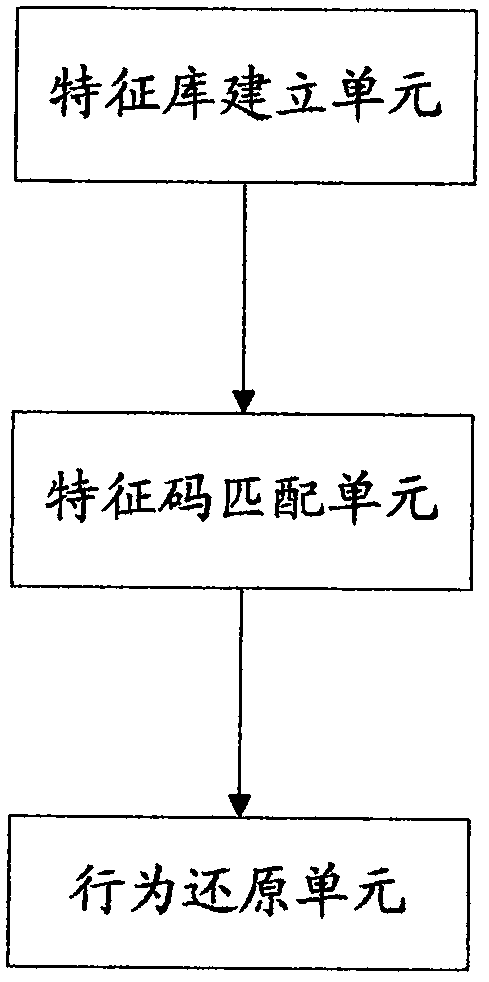
InactiveCN106878438AChange structureNo additional investment requiredWeb data indexingTransmissionBehavioral analyticsDynamic resource
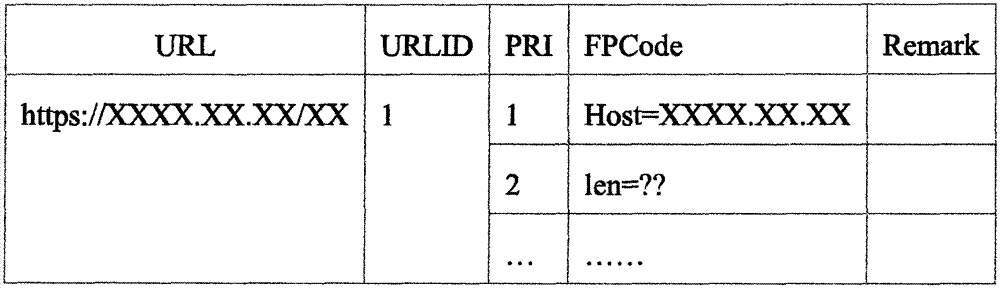
The invention discloses a method for user behavior analysis under the https environment and a system thereof. The method comprises the steps that step 1) a content feature library is established for an internet resource page requiring analysis, the feature library is composed of multiple feature codes, and the feature codes include one or combination of the Host of https request URL, the page size, the resource content included in the page, the size of the resource content, dynamic resource information and the embedded URLs and number; step 2) the https message data of user access internet resources are analyzed one by one, and feature information is extracted so as to be matched with the feature codes for analysis; and step 3) the log of feature information extraction is matched with the feature codes in the content feature library, the real access behavior of the user is restored and further analysis and statistics are performed.
Owner:JIUYUAN QIANCHANG BEIJING TECH SERVICE CO LTD
Semiconductor device
InactiveUS20040113172A1Erroneous operationNot easy to spreadTransistorSolid-state devicesMOSFETPower semiconductor device
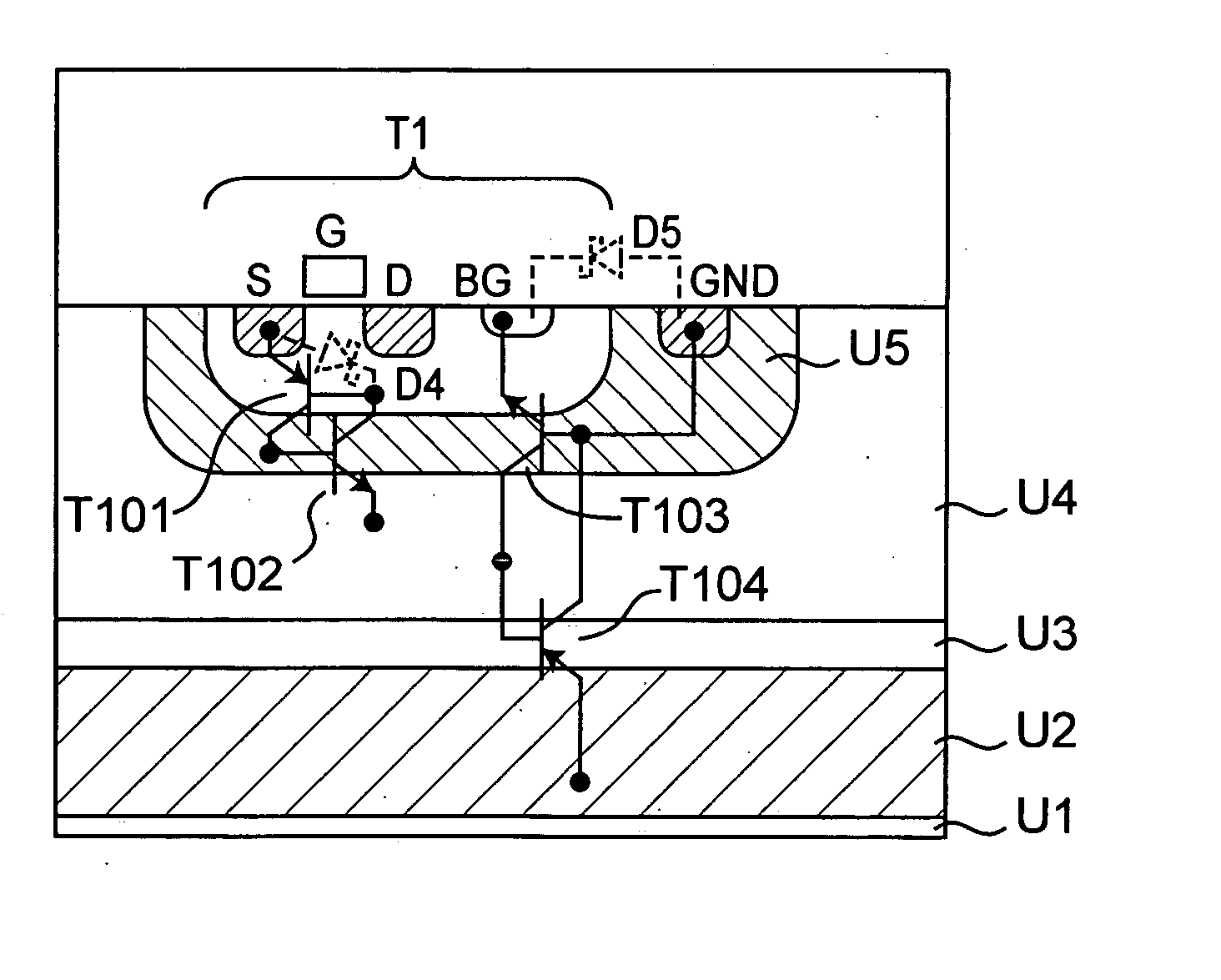
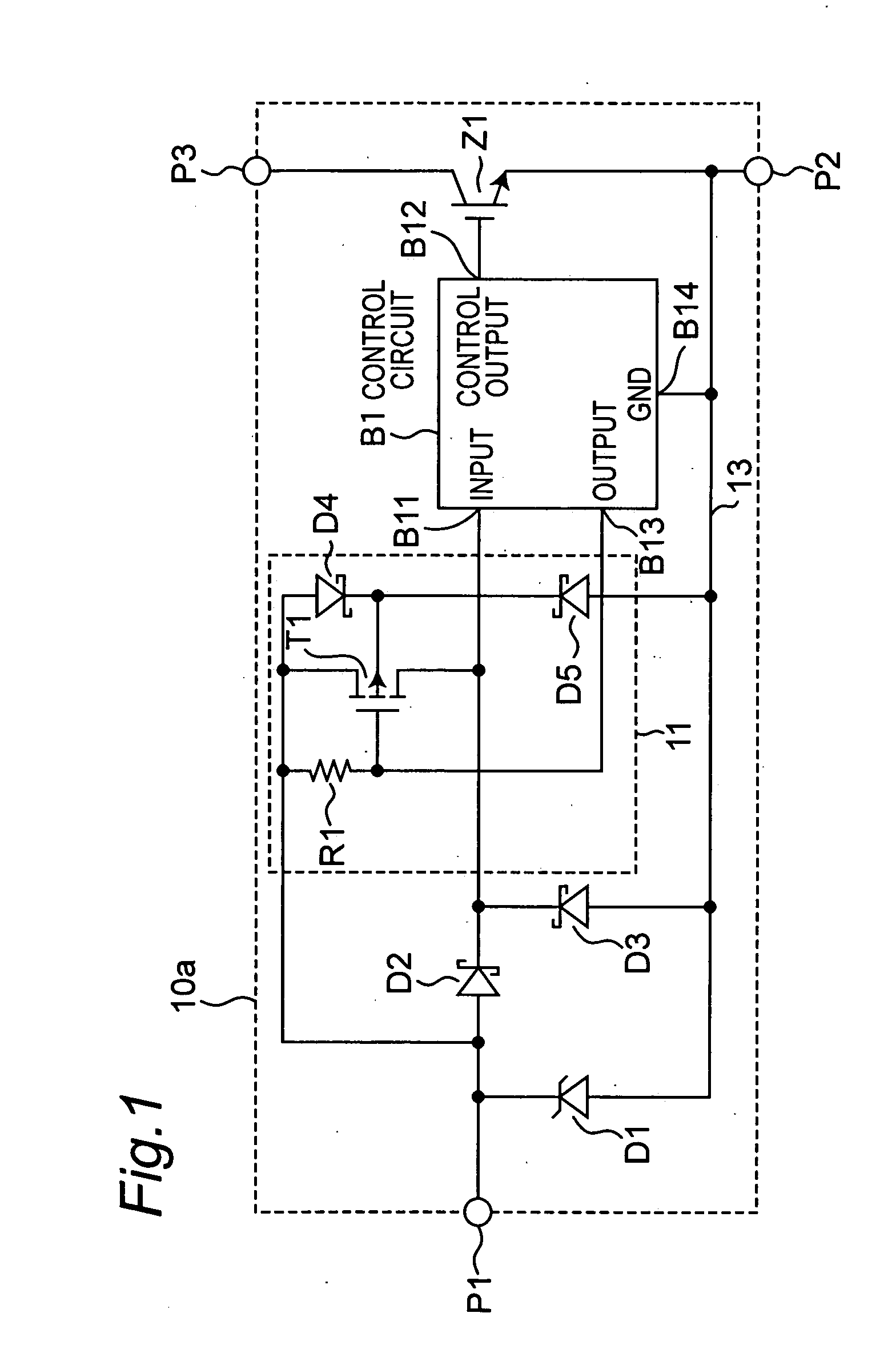
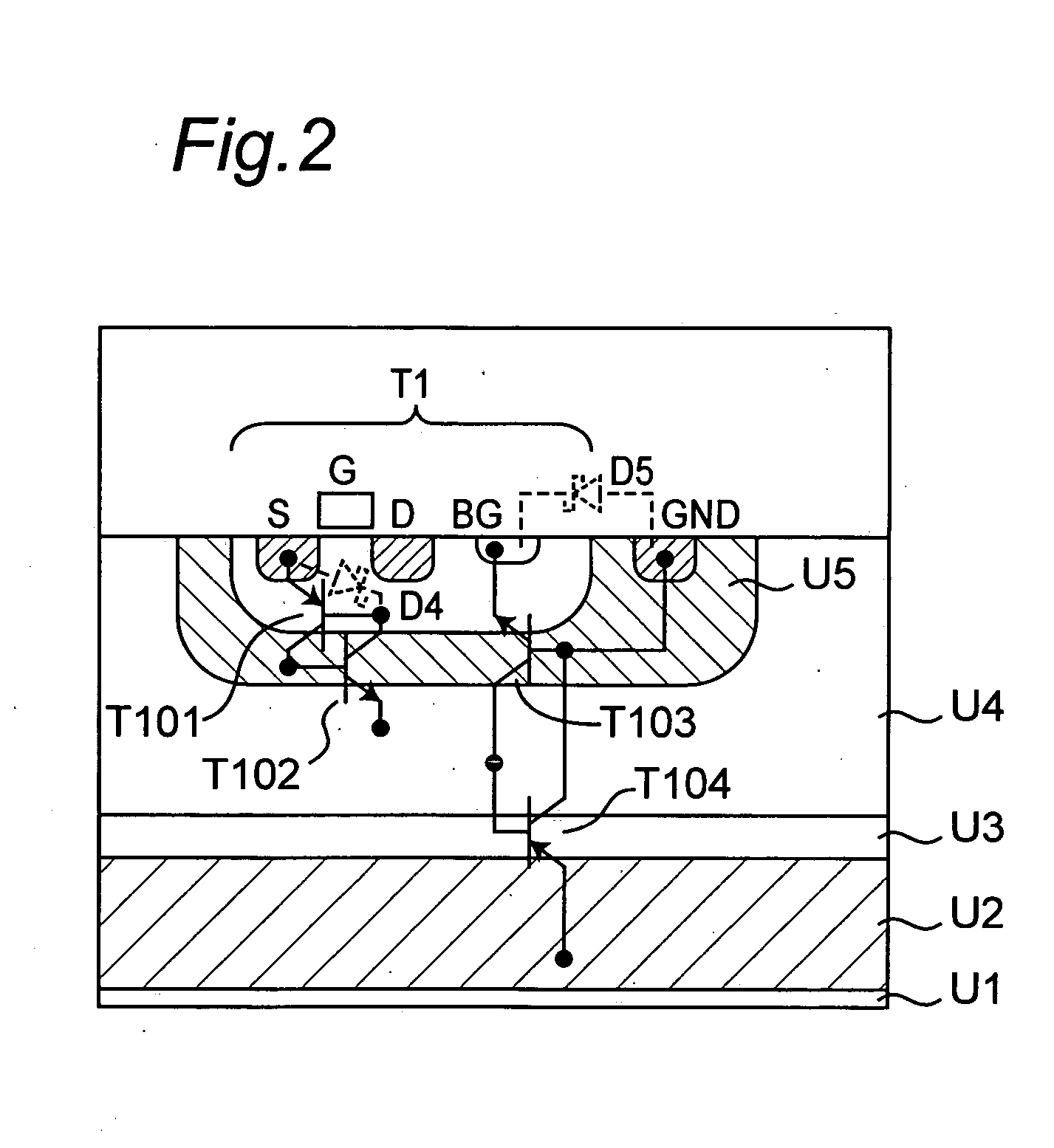
A semiconductor device which IGBT (Z1) and a control circuit (B1) for driving the IGBT (Z1) are formed on the same semiconductor substrate by using a junction isolation technology, includes an input terminal (P1) for inputting a drive signal of the IGBT (Z1), a Schottky barrier diode (D2) having an anode connected to the input terminal (P1) and a cathode connected to an input terminal (B11) of the control circuit (B1), and a p-channel MOSFET (T1) for shorting both ends of the Schottky barrier diode (D2) when the voltage of the drive signal input to the input terminal (P1) is higher than a predetermined voltage, thereby latch-up of the parasitic element is prevented and a transmission loss of the input signal can be reduced.
Owner:MITSUBISHI ELECTRIC CORP
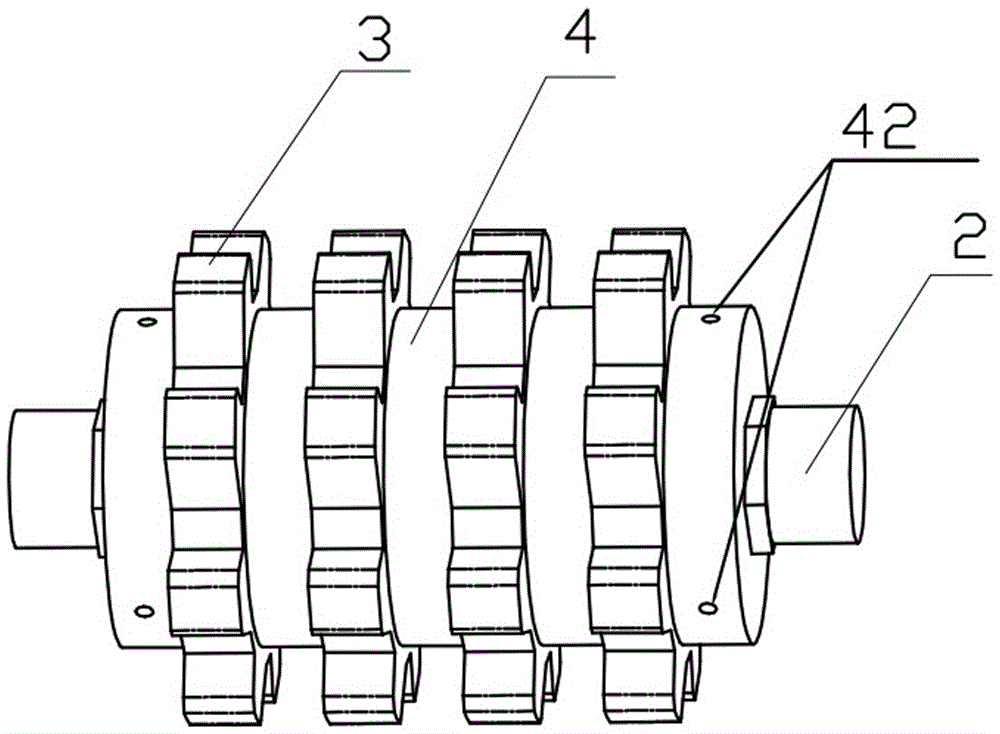
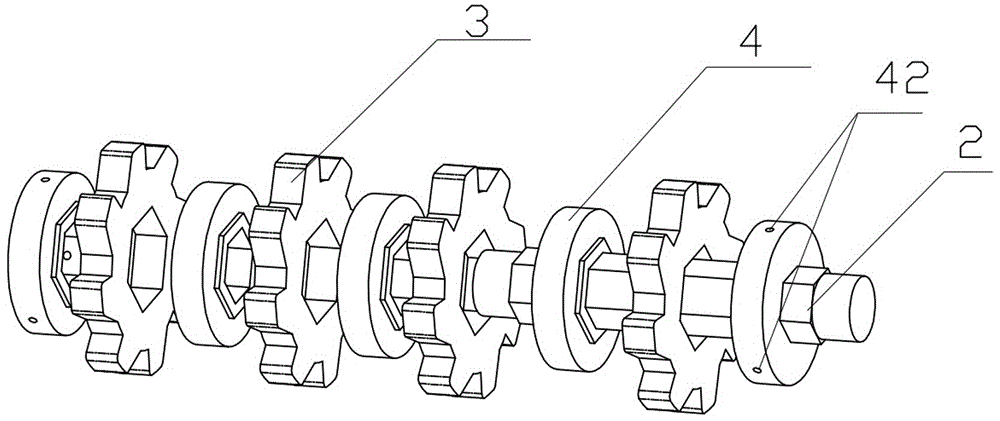
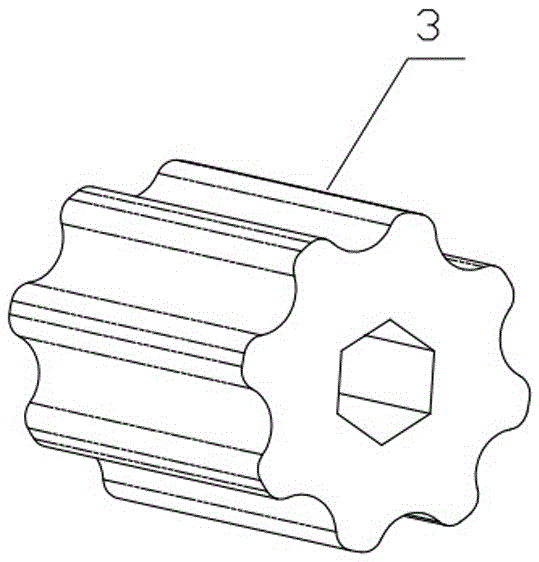
Ceramic roller for crushing lithium battery raw material and ceramic twin-roller machine
The invention discloses a ceramic roller for crushing a lithium battery raw material. The ceramic roller comprises a roller shaft, the roller shaft is provided with a plurality of detachable embossing rollers, and a detachable round roller is arranged between every two adjacent embossing rollers; the surfaces of the embossing rollers are pro vided with a plurality of convex teeth; the surfaces of the round rollers are smooth surfaces; and the maximum external diameter of each round roller is larger than that of each embossing roller. A ceramic twin-roller machine produced by using the ceramic roller comprises at least one embossing roller and ceramic roller group produced by using the ceramic roller, and each embossing roller and ceramic roller group is arranged in a staggered way that the embossing rollers correspond to the round rollers. The ceramic roller formed by assembling the embossing rollers and the round rollers at intervals is large in size, convenient to replace when being damaged, low in maintenance cost and high in crushing efficiency.
Owner:SUZHOU XIRAN IND EQUIP
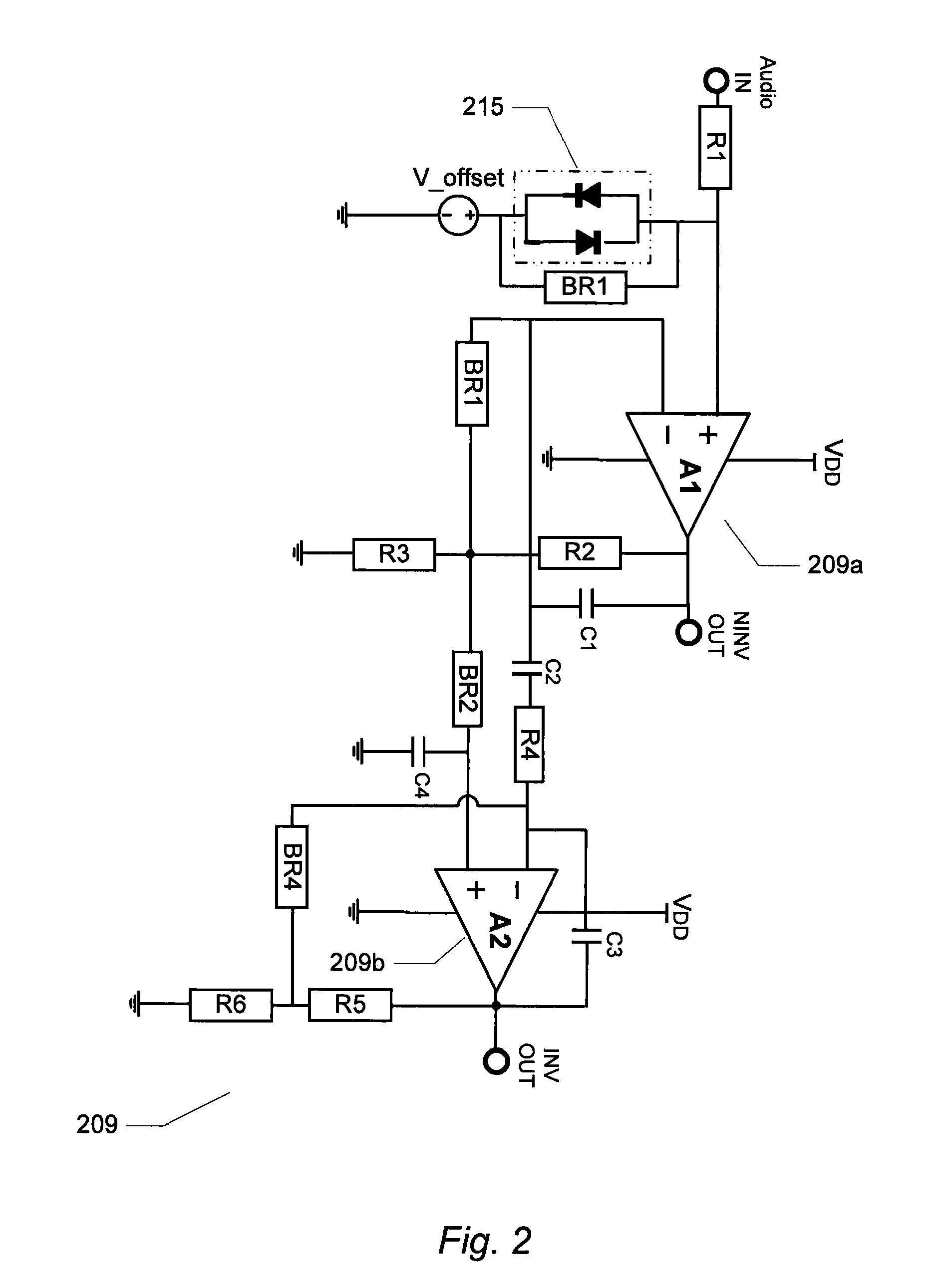
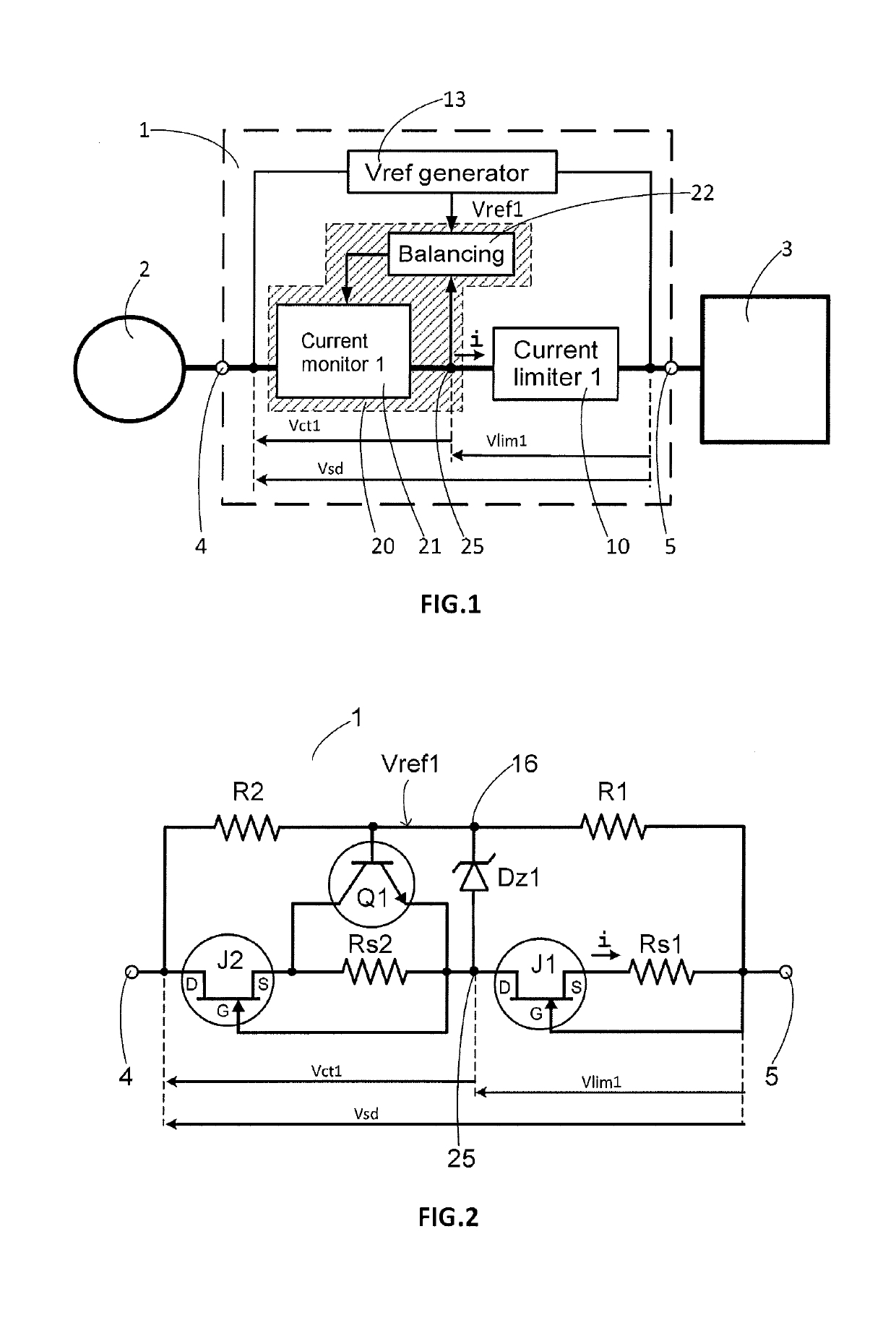
Overvoltage protection circuit and electrical device including such a protection circuit
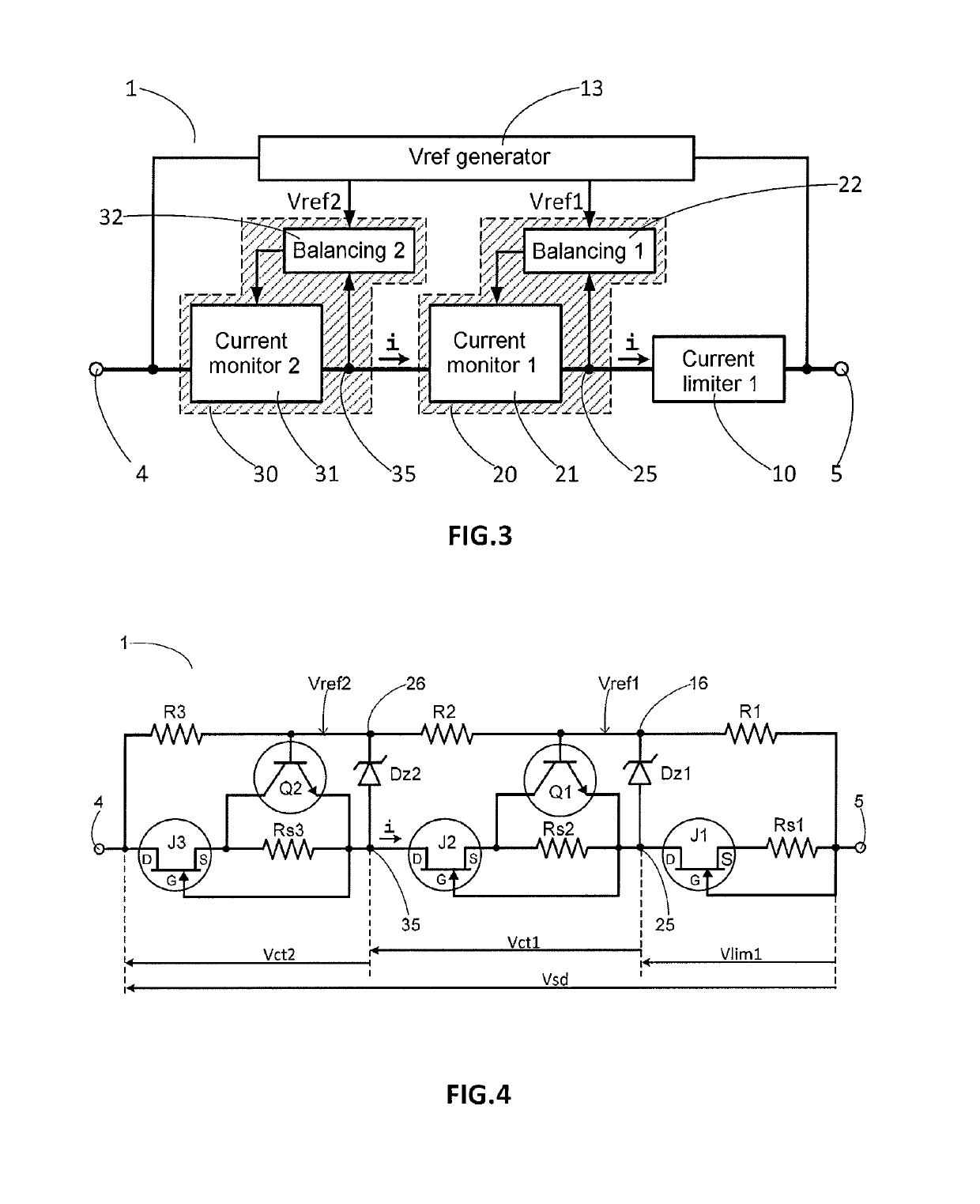
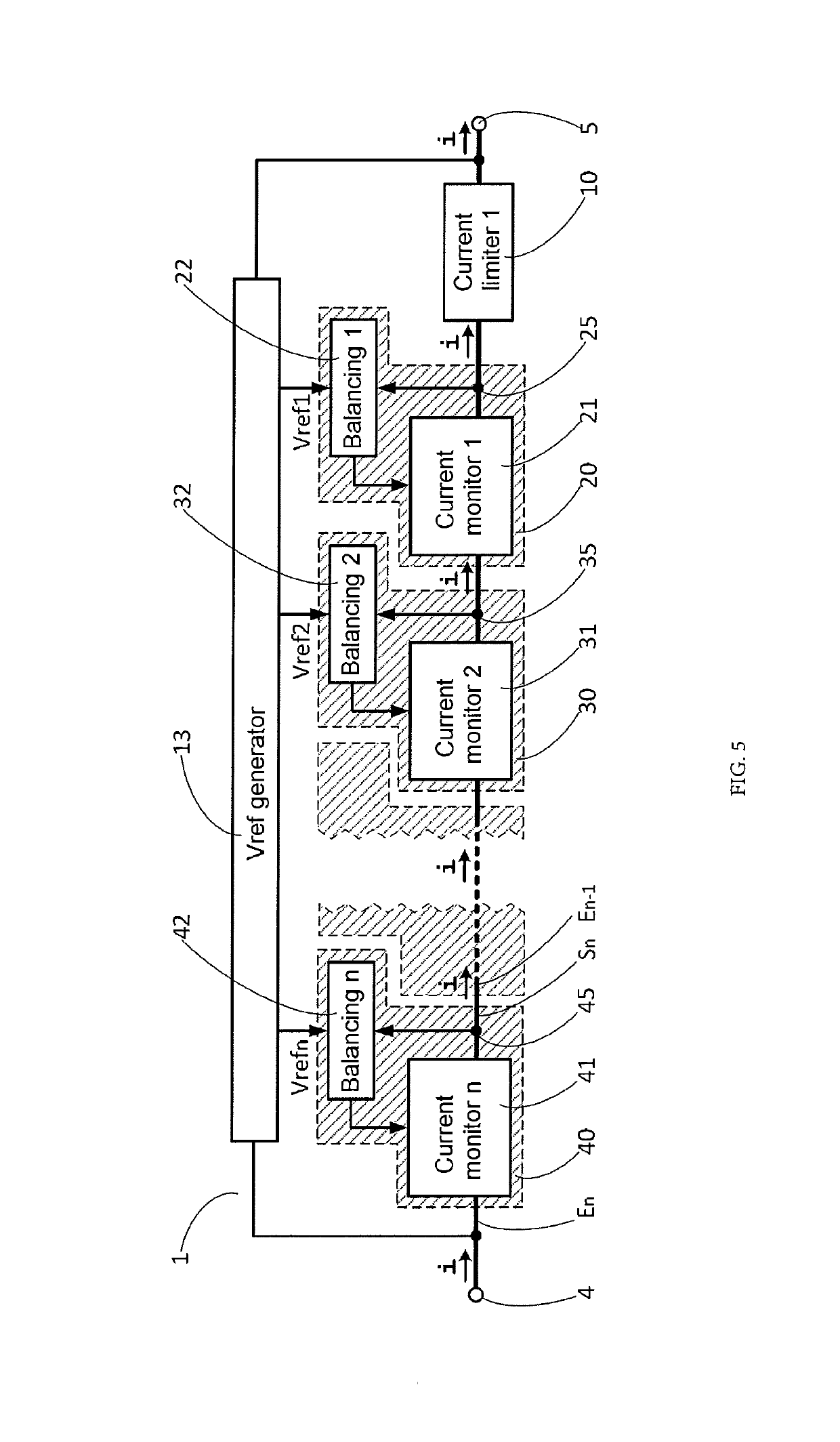
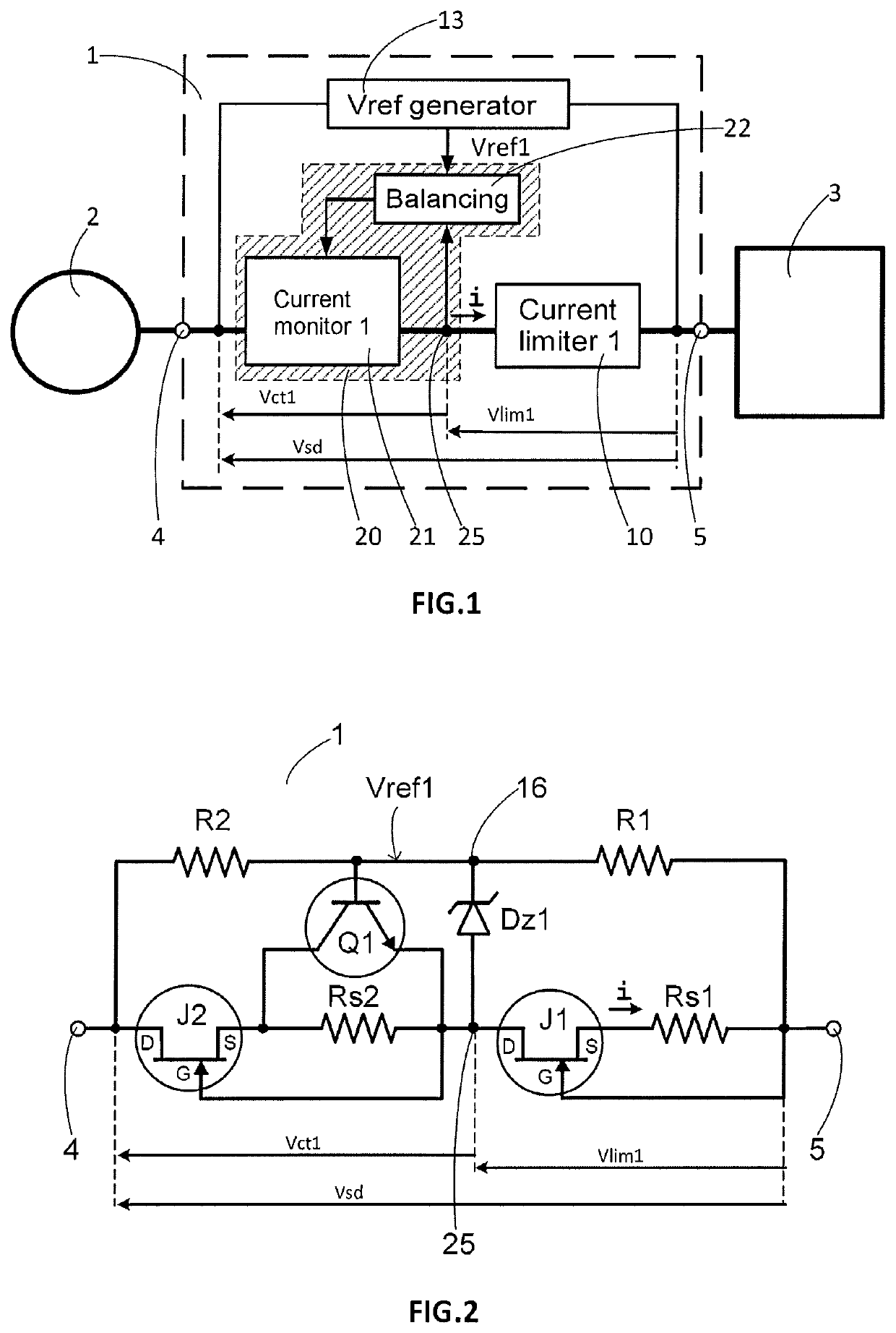
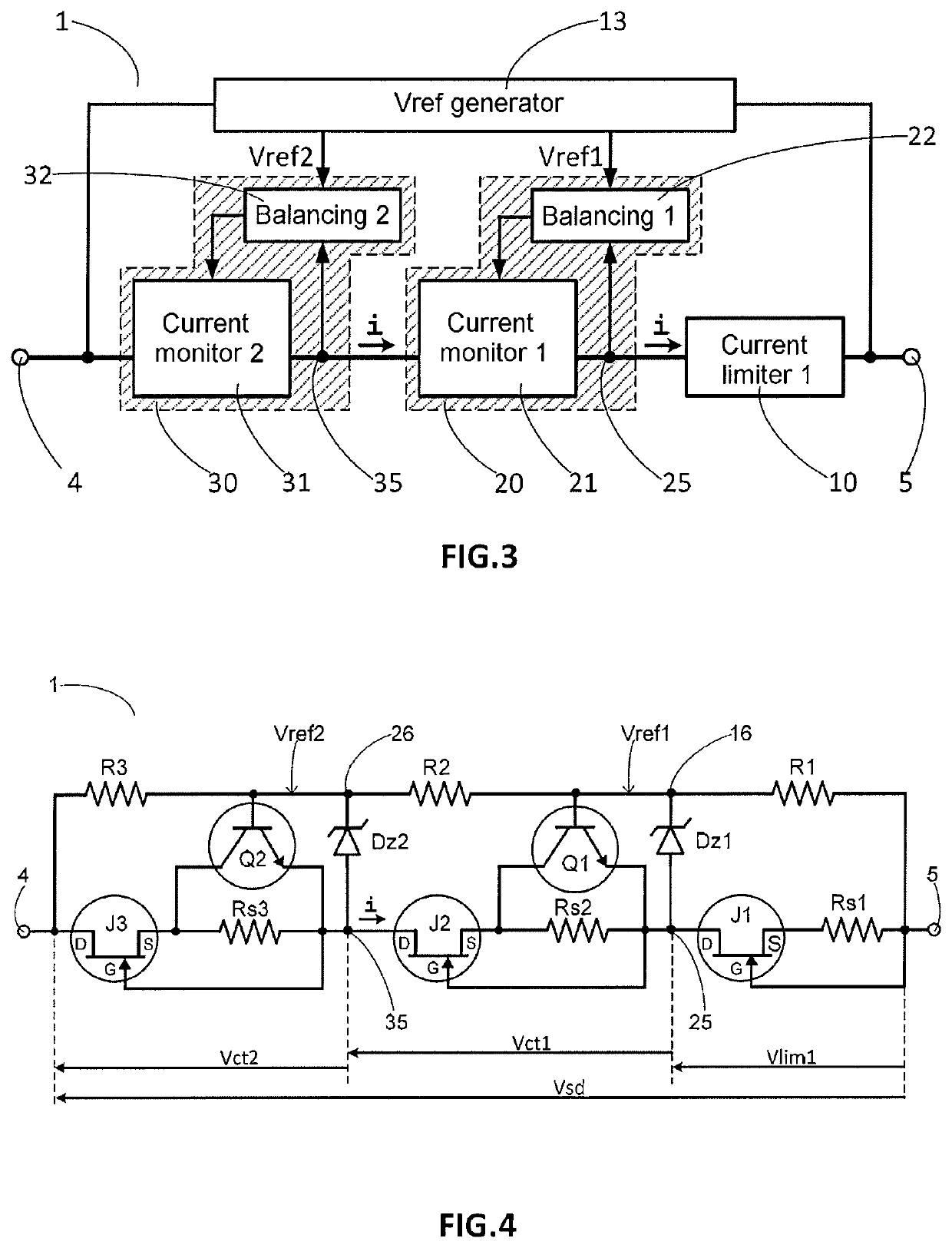
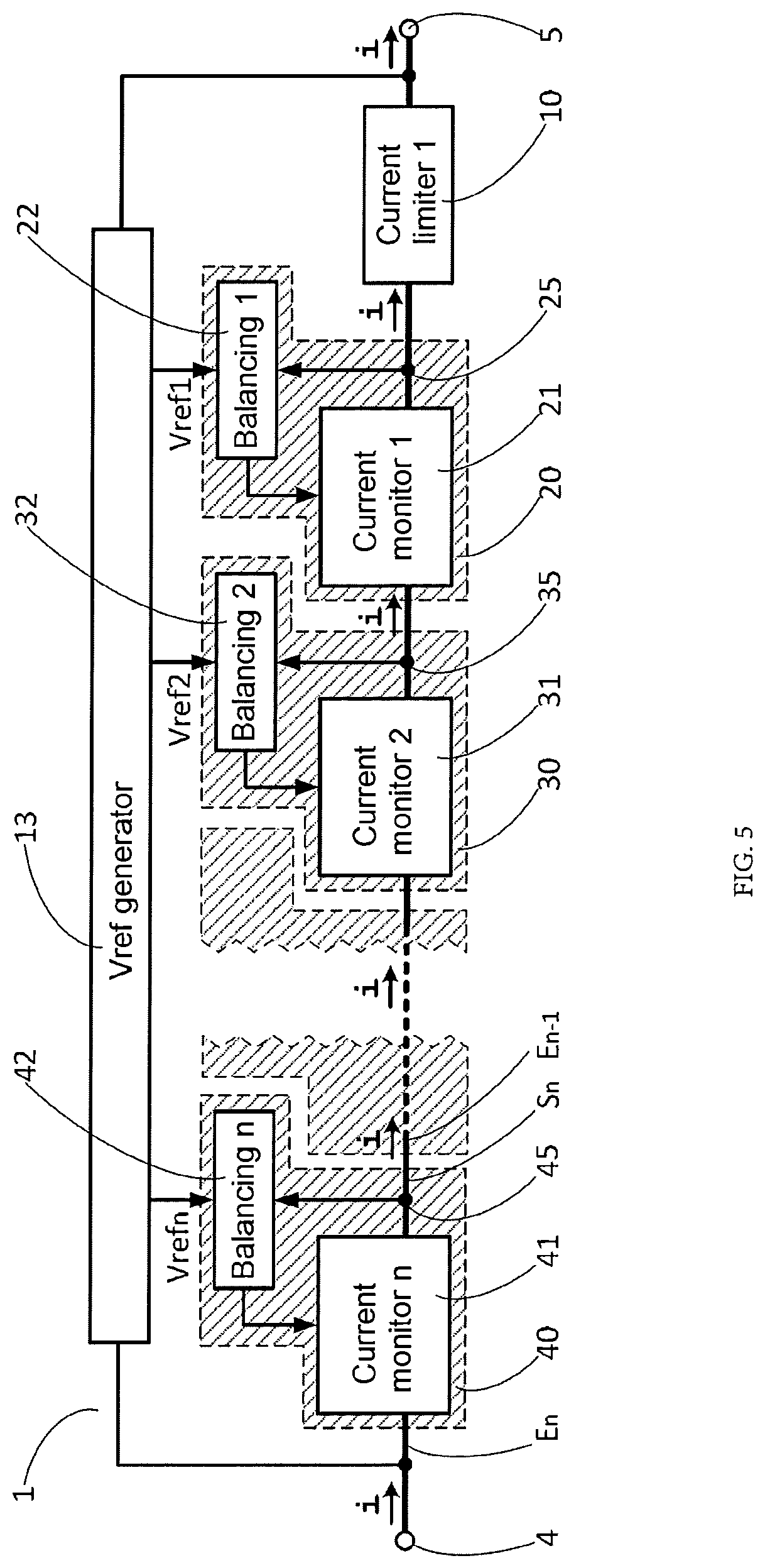
ActiveUS20190273378A1Easy to adaptAvoid disadvantagesEmergency protection detectionEmergency protective arrangements for limiting excess voltage/currentOvervoltageVoltage generator
A protection circuit intended to be connected between an electrical energy source and an overvoltage-sensitive device. A current limiting circuit and a current monitoring circuit are connected in series, a reference voltage generator circuit delivering a reference voltage, and a balancing circuit is intended to control the current monitoring circuit so that the voltage at a point of connection between the current limiting circuit and the current monitoring circuit is substantially equal to the reference voltage. An electrical measurement or power supply device including at least one such overvoltage protection circuit.
Owner:SCHNEIDER ELECTRIC IND SAS
Two-D bar code reading method and apparatus thereof
ActiveCN1275182CLiteracy realizationReduce manufacturing costCharacter and pattern recognitionSensing record carriersComputer terminalInterface circuits
A kind of 2D bar reader includes image reading head, terminal of computing device. The said image reading head through control interface circuit is connected to terminal of computing device with engine software for reading and recognizing bar code being installed on. The said terminal of computing device is one of desktop computer, server, palm computer, embedded type system or handset possible to install engine software for reading and recognizing bar code. It is initiation of the invention that recognition function is transferred to terminal of computing device connected. Thus, the image reading head possesses features of simple feature, easy of manufacture, high processing capacity, good recognition effect.
Owner:BEIJING INSPIRY XINCHUANG TECH
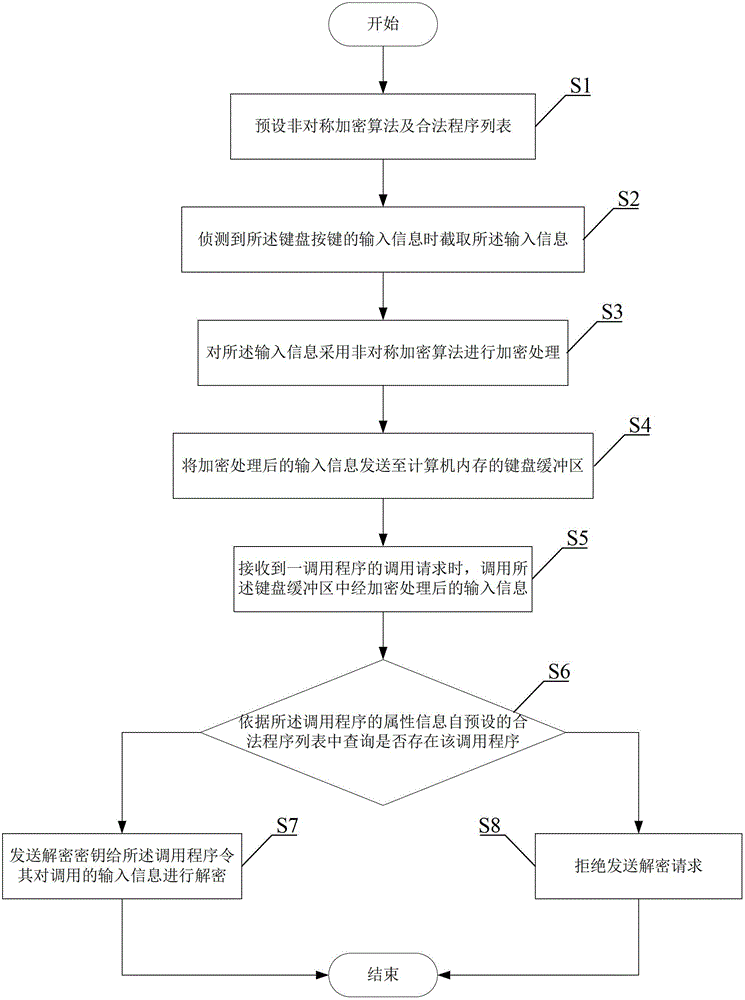
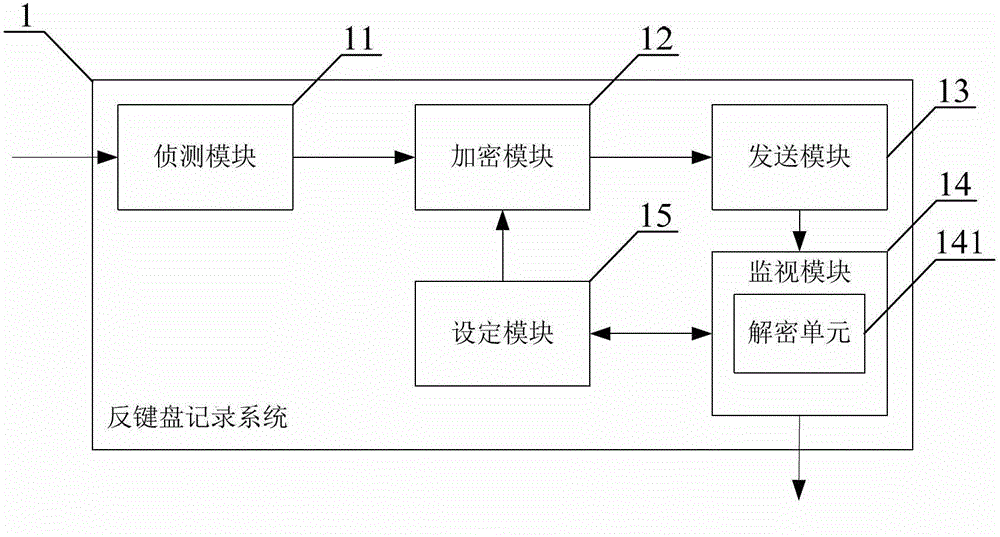
Anti-keylogging method and system
The invention provides a key-defending recording method and a key-defending recording system which are applied to a computer with a keyboard. The method comprises the following steps of: when input information of keys of a keyboard is detected, intercepting the input information; encrypting the input information by adopting an asymmetric cryptographic algorithm; sending the encrypted input information to a keyboard buffer area of a computer memory; calling the encrypted input information in the keyboard buffer area, monitoring and analyzing the keyboard buffer area to judge whether the calling is legal or not; and when the calling is judged to be legal, decrypting the called input information, and when the calling is judged to be abnormal, refusing to send a decryption request. Therefore, by the method and the system, the aim of protecting keyboard input is fulfilled, so that the safety of the keyboard input for users can be ensured to a large extent.
Owner:江苏华御威盾网络科技有限公司
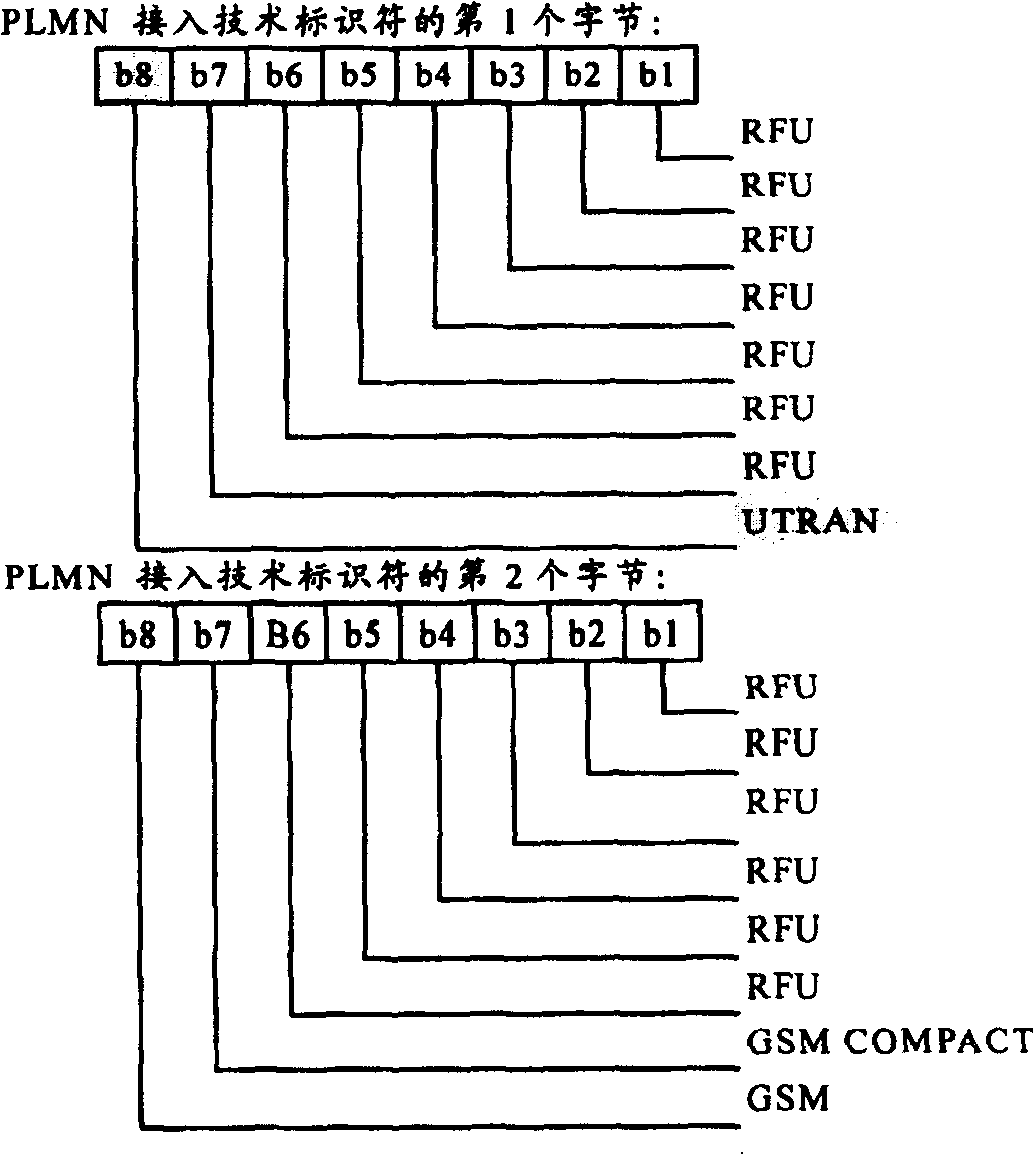
Method for increasing multiple mode terminal searching public land mobile net speed
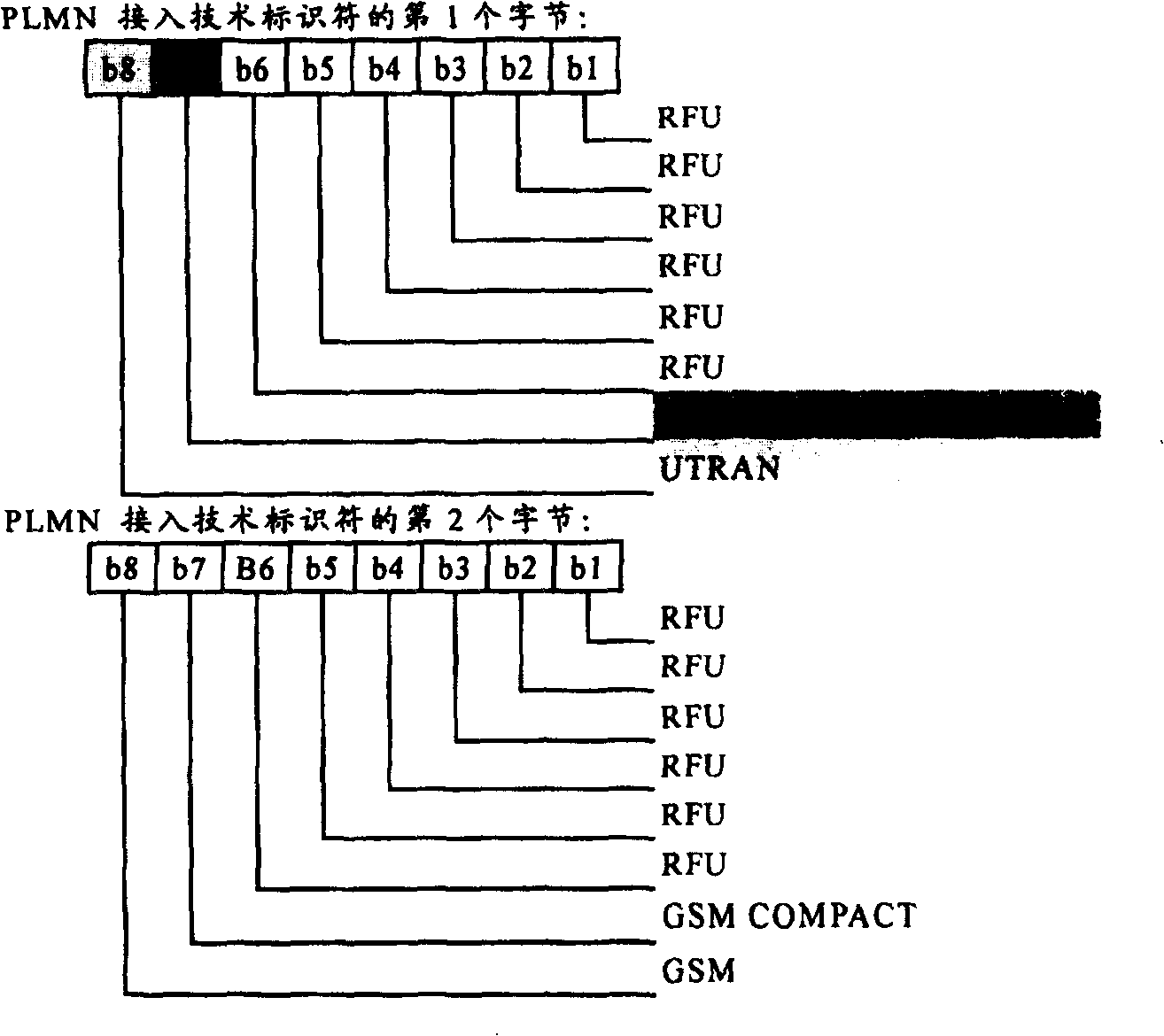
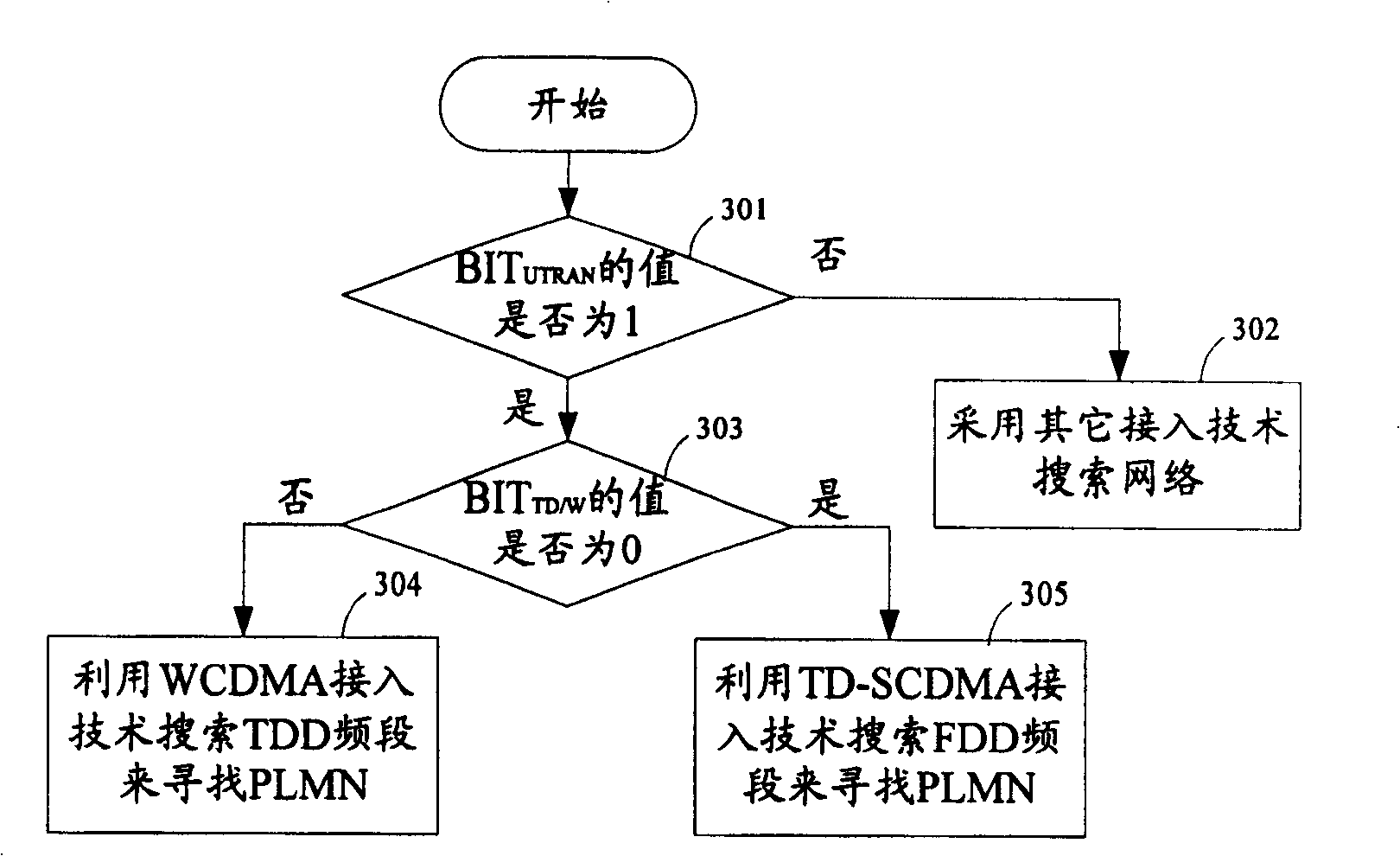
ActiveCN100431383CImprove the speed of searching PLMNShorten the timeAssess restrictionRadio/inductive link selection arrangementsPublic land mobile networkAccess technology
Present invention discloses a method for raising multiple mold terminals searching public land mobile network speed. It contains setting UTRAN wireless accessing technology type expressed by at least one preserving bit value in PLMN accessing technology identifier, when multiple mold terminal making PLMN searching, if determining selecting UTRAN wireless accessing technology then judging specific accessing technology type according to said preserving bit value, according to judgement result searching PLMN in said specific accessing technology corresponding frequency range by said determined specific accessing technology. Said invention can shorten terminal searching network average time, raising multiple mold terminal user satisfaction and systematical paging success ratio.
Owner:LEADCORE TECH
Logic circuit device comprising at least one digital input
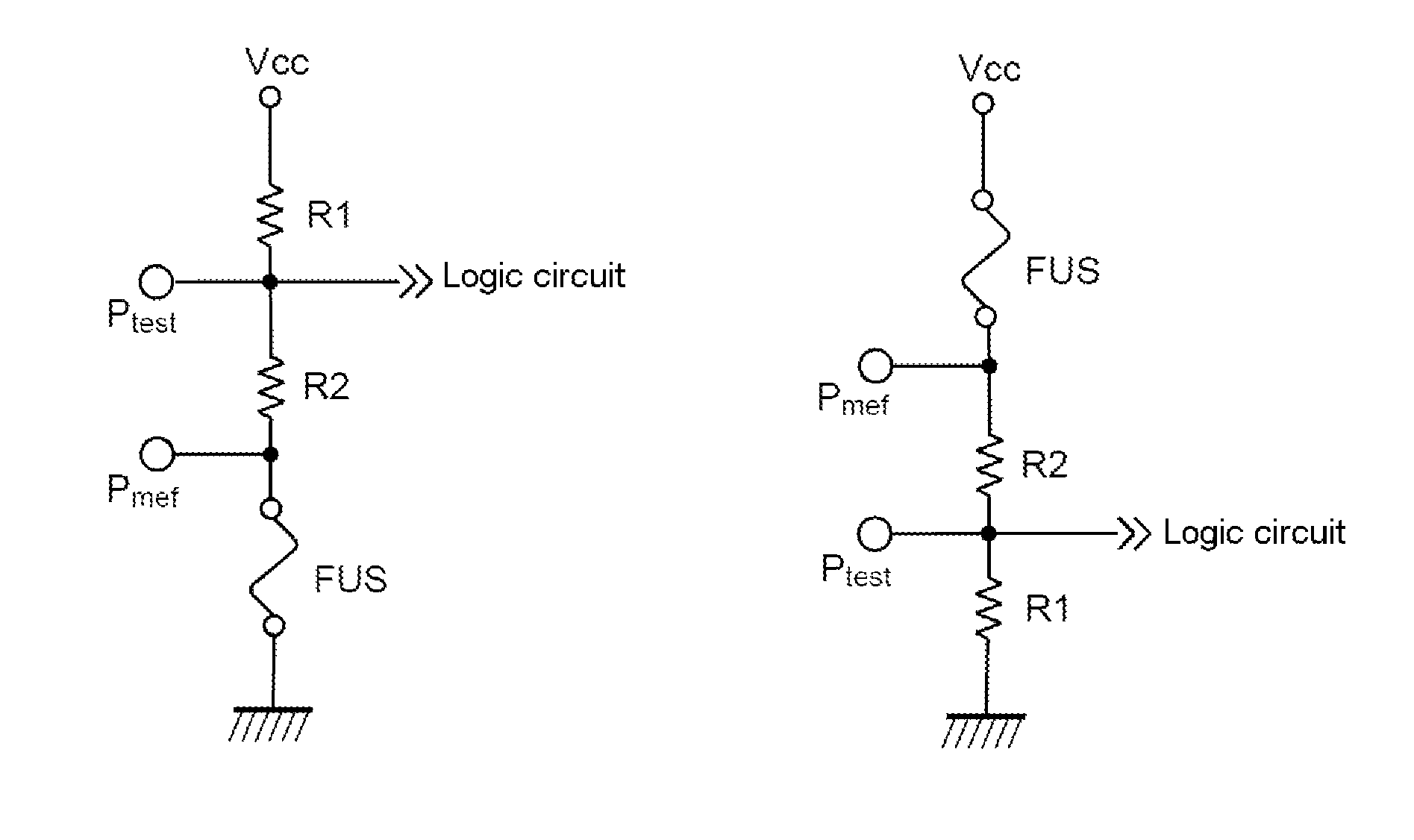
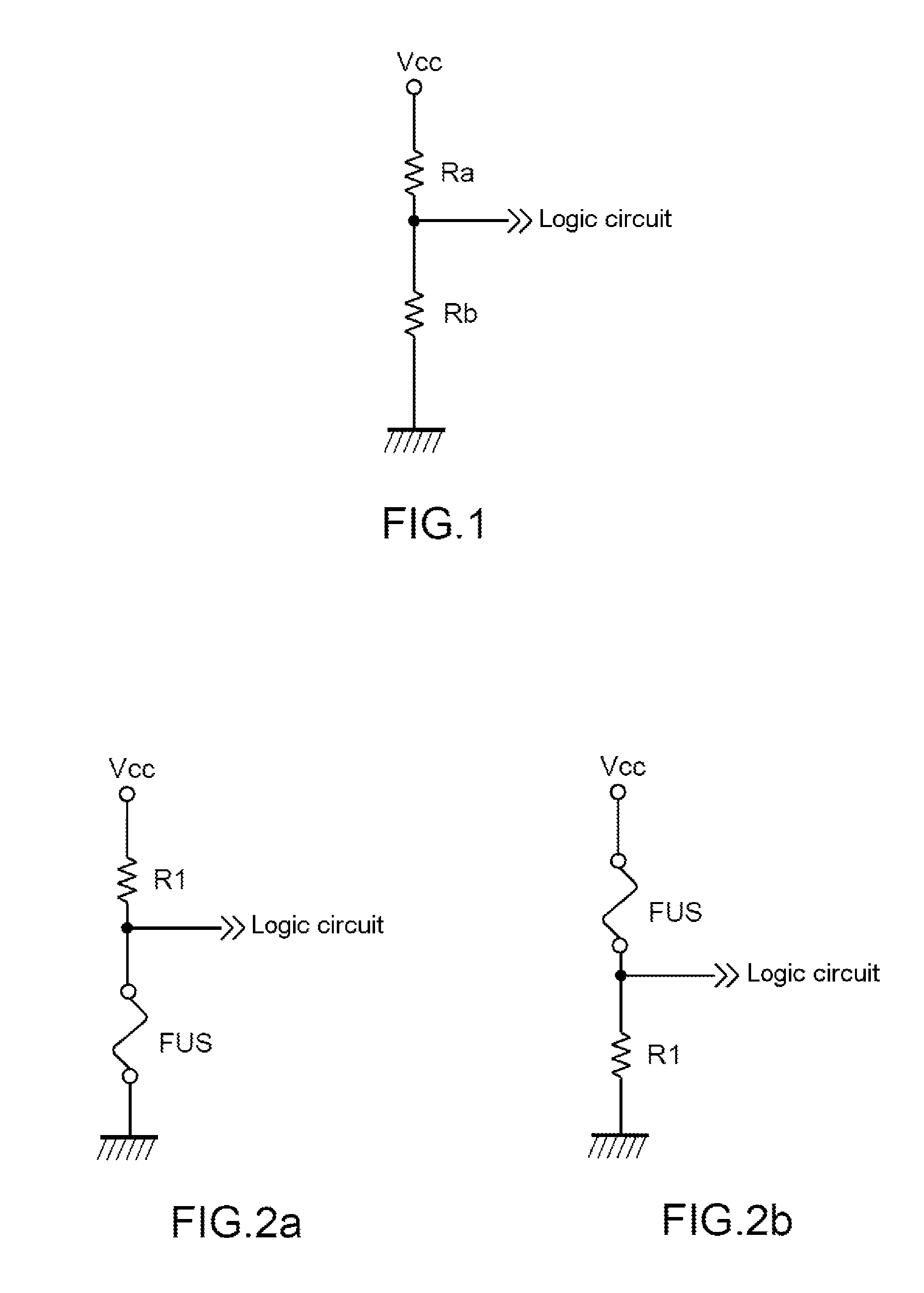
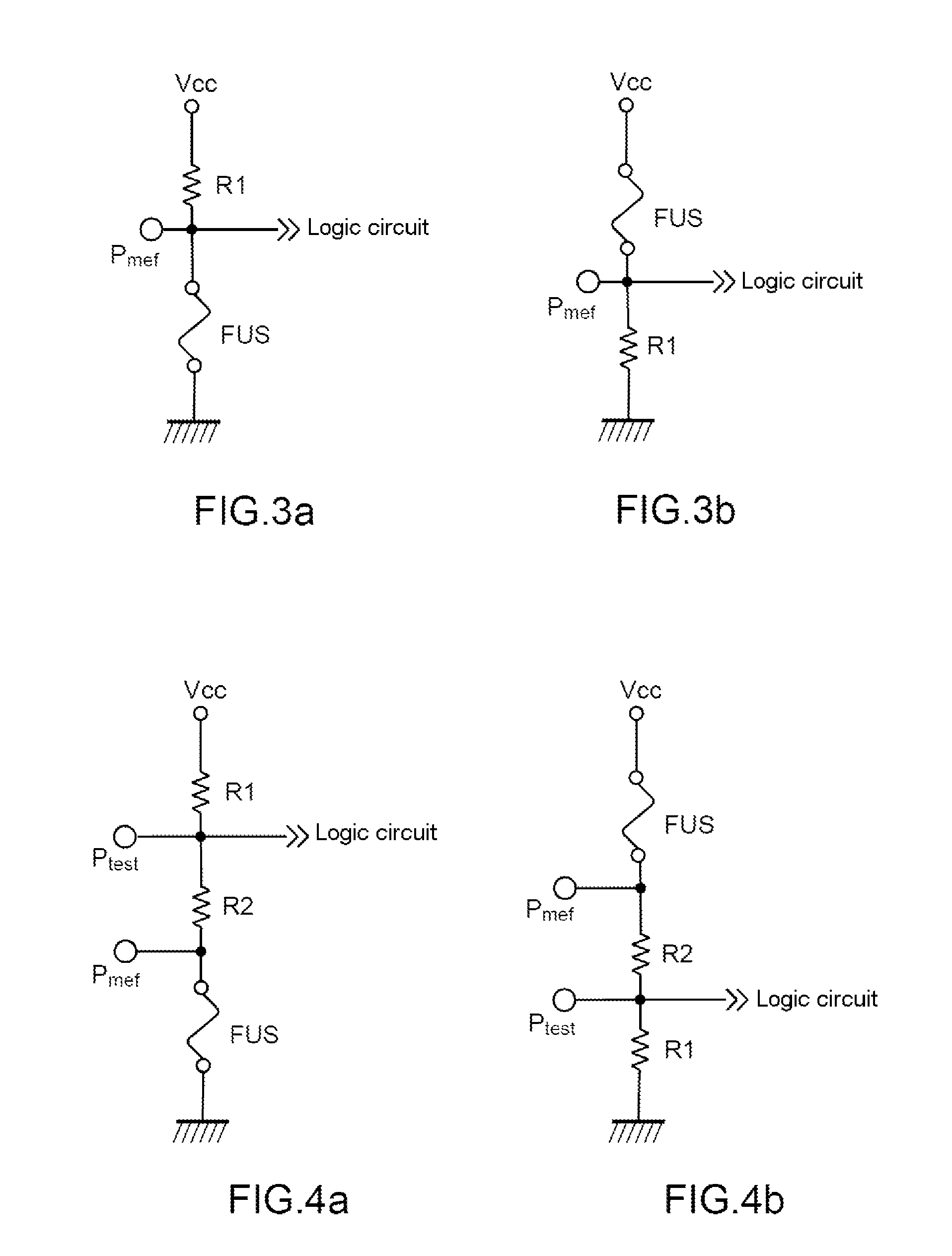
InactiveUS8941436B2Easy to implementLess expensiveHeating/cooling contact switchesVoltage/current interference eliminationLogic stateThreshold current
The invention pertains to a logic circuit device comprising at least one digital input furnished with a fuse (FUS) being, in the closed state, suitable for applying an electrical input voltage of the logic circuit corresponding to a first logic state from among the logic states 0 and 1, and, in the definitive open state, suitable for applying an electrical input voltage of the logic circuit corresponding to the second logic state from among the logic states 0 and 1, said fuse (FUS) being suitable for being placed definitively in the second logic state by injection of a current greater than a threshold current (CS).
Owner:THALES SA
Method for improving service building success rate in mobile communication system
ActiveCN100415048CIncrease success rateLower the bandwidth valueConnection managementRadio/inductive link selection arrangementsNon real timeMobile communication systems
The invention relates to a method for improving the service building success in the mobile communication system, wherein, when the wireless network controller (RNC) receives the distribute request of building service, and judges out the bandwidth needed by present processed service is over the maximum bandwidth reported by the user terminal (UE), check if the present service contains the non real-time service; if contains, decrease the bandwidth needed by the non real-time service, and using said decreased bandwidth to distribute or redistribute the bandwidth transmission signal channel of said non real-time service. The invention can use present bandwidth resource of mobile communication system to improve the success rate of service building without improve the bandwidth ability of UE.
Owner:SHANGHAI HUAWEI TECH CO LTD
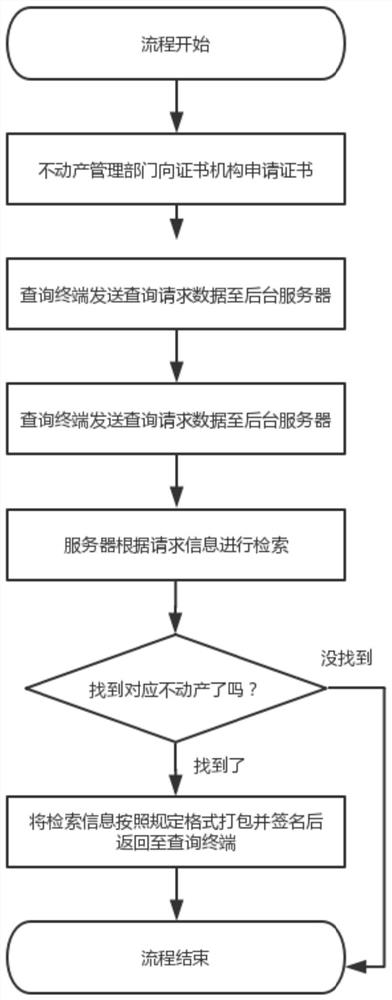
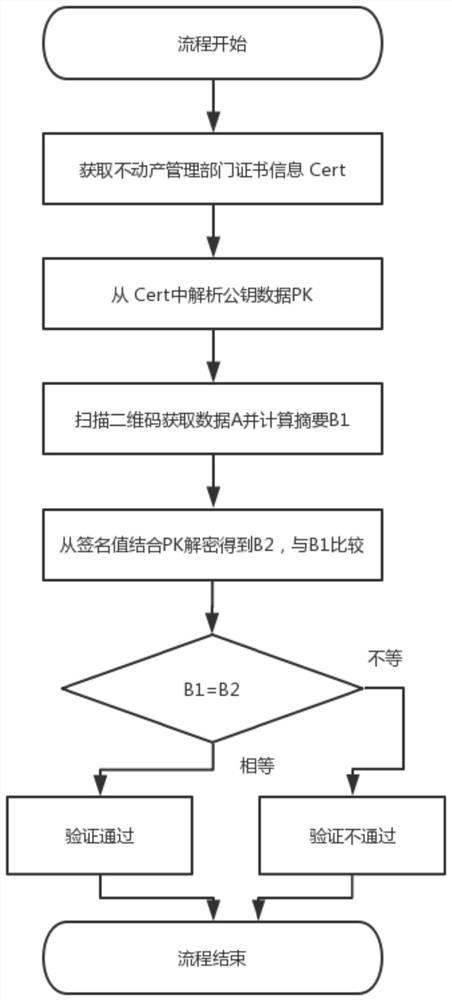
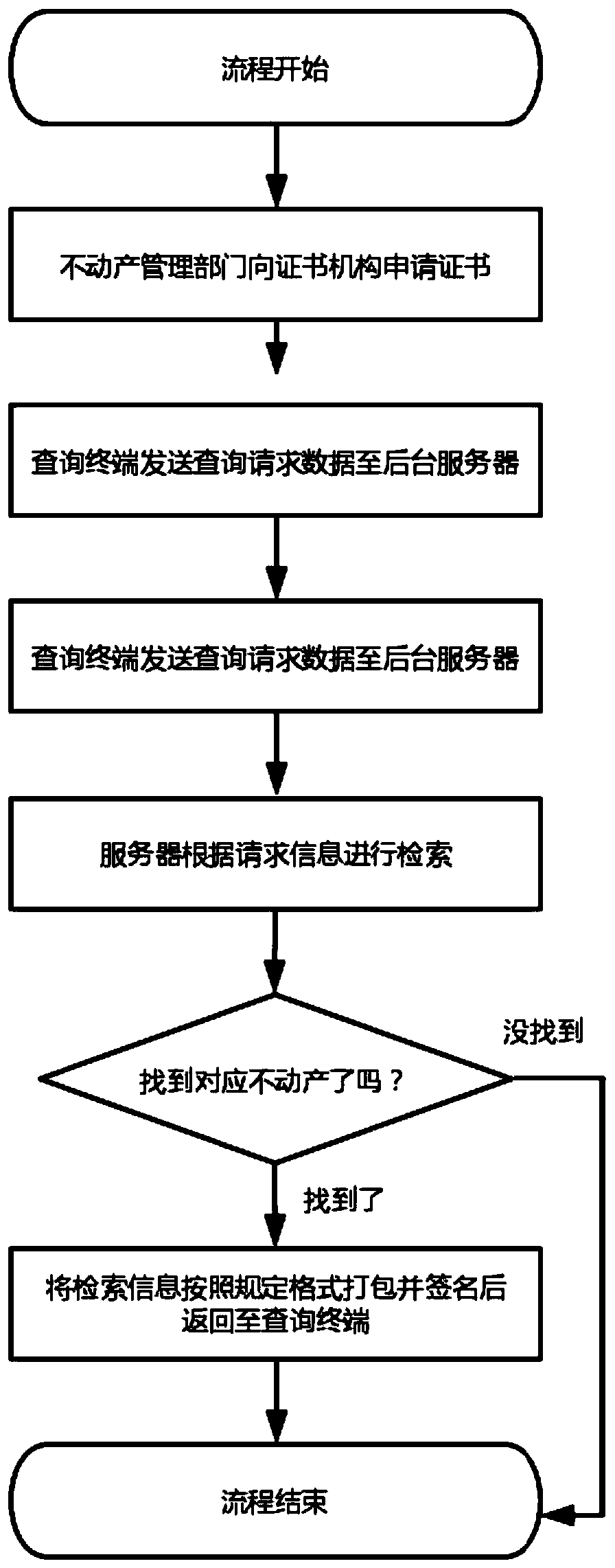
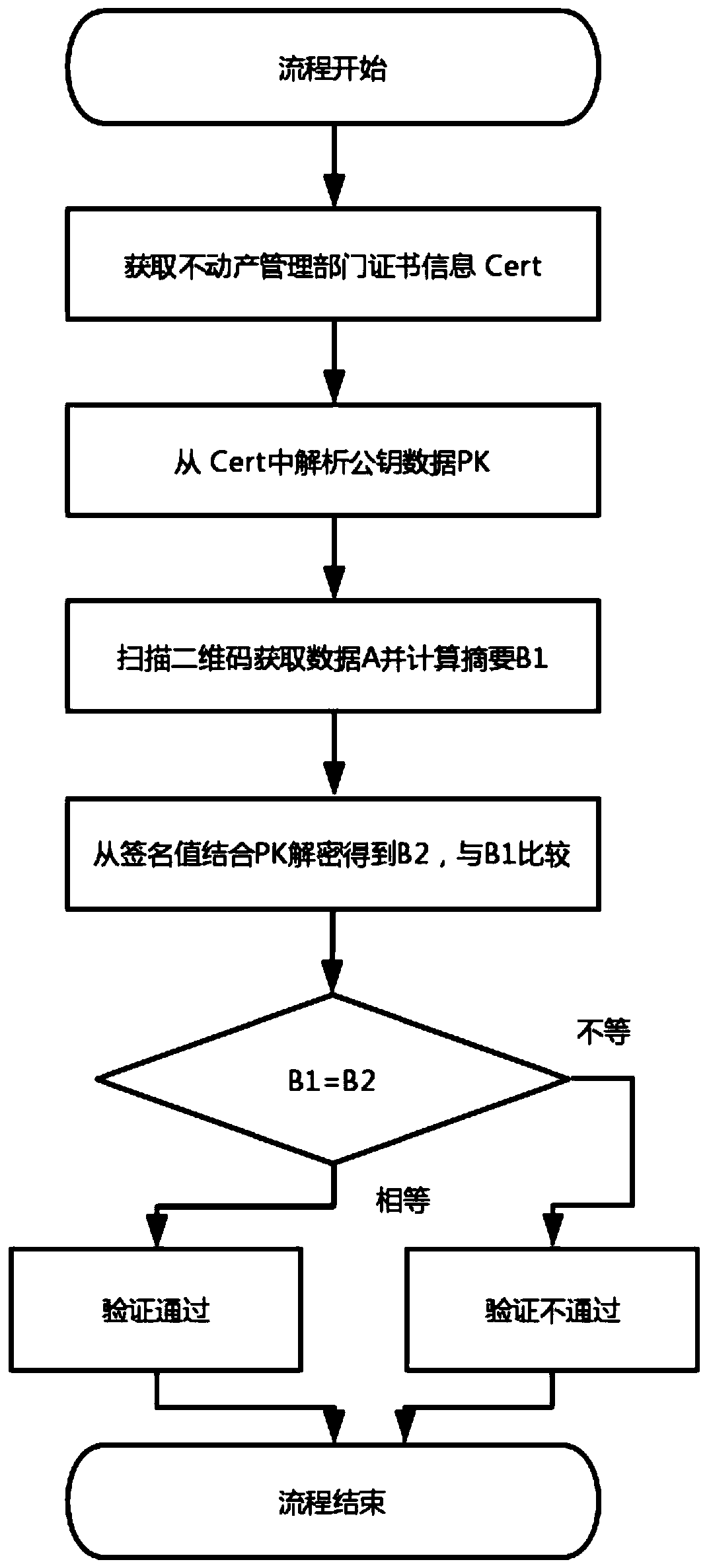
A Verification Method of Real Estate Information Based on Asymmetric Algorithm
ActiveCN111260528BNo sense of operationProtection inputData processing applicationsDigital data information retrievalAlgorithmThe Internet
The invention discloses a real estate information verification method based on an asymmetric algorithm, which belongs to the field of information security. The invention applies the concept of data signature, so that the key data of real estate can be protected and can not be tampered with, cannot be denied, and can not destroy the effect of integrity . The verification procedure is convenient and quick, and any smartphone can verify the authenticity of real estate information without connecting to the Internet after installing the APP, which effectively improves the efficiency of real estate-related businesses and reduces the trust cost of stakeholders.
Owner:赵智
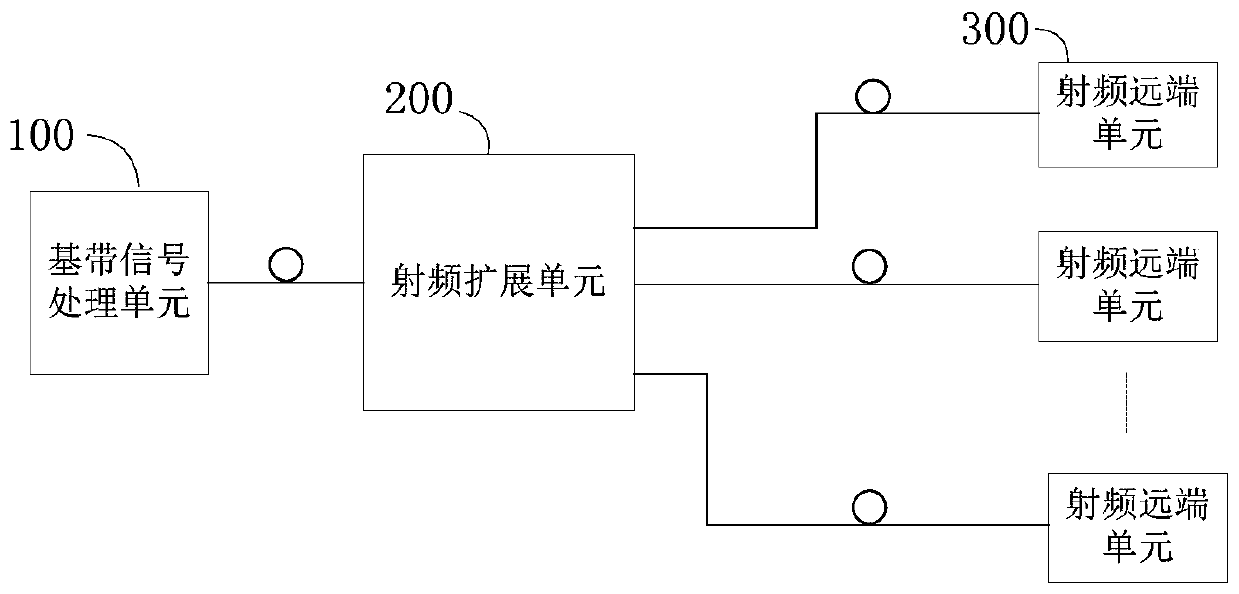
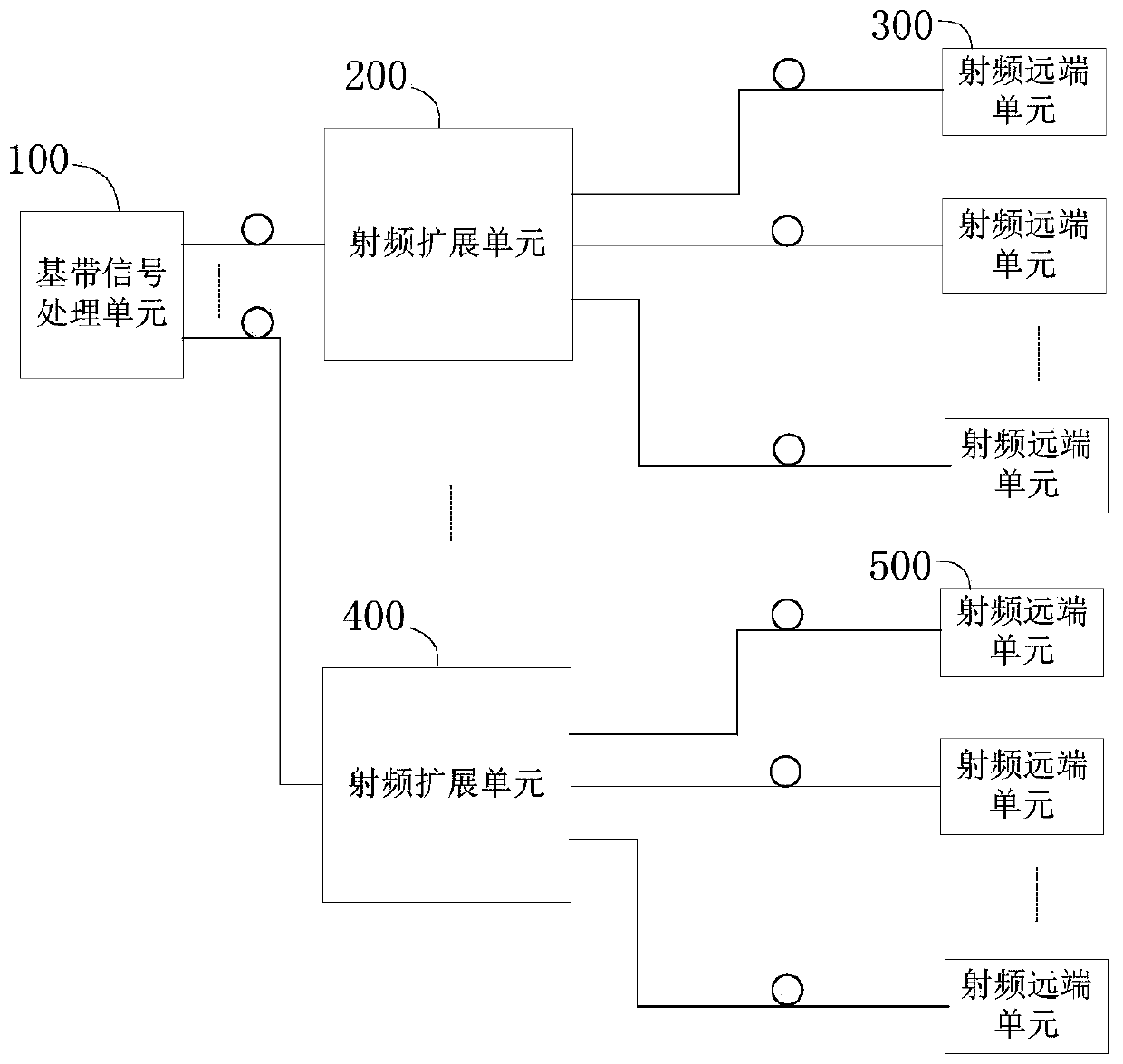
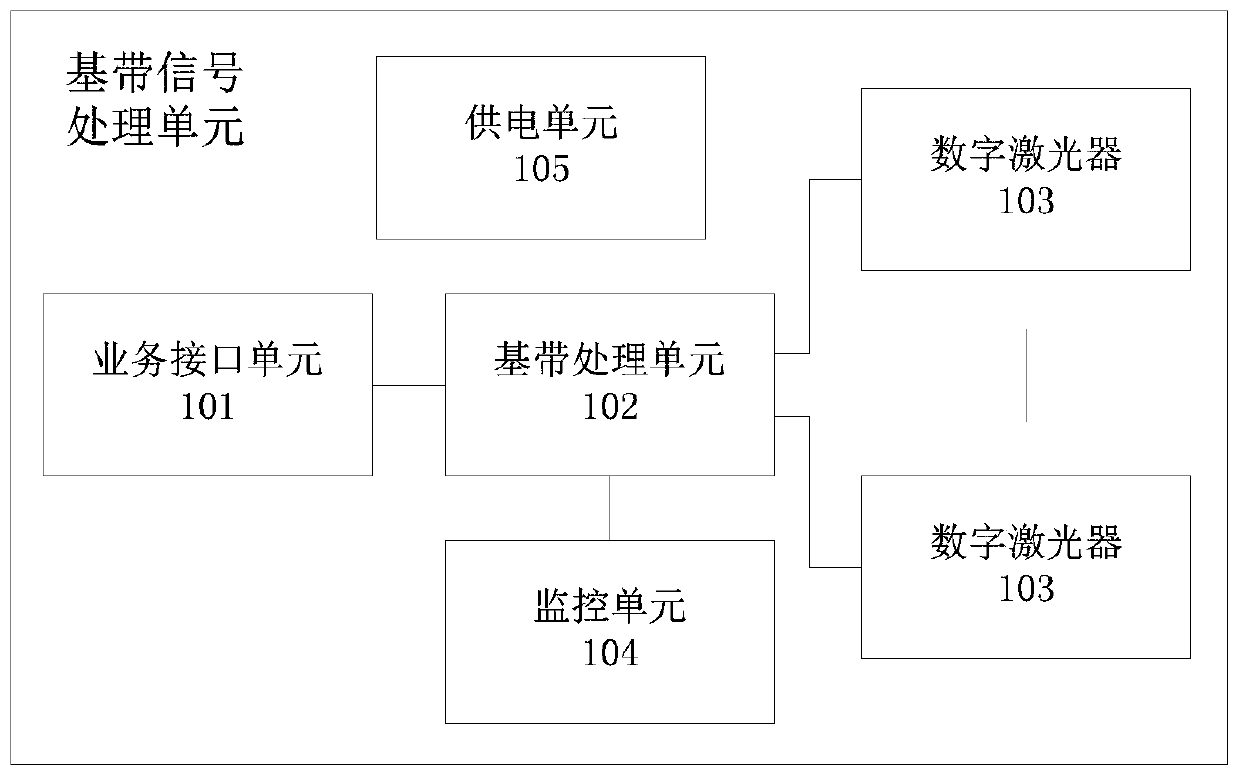
A distributed wireless signal coverage system
ActiveCN106712851BNo power lossNo electromagnetic radiationRadio-over-fibreRadio frequencyLow power dissipation
Owner:WUHAN HONGXIN TELECOMM TECH CO LTD
A terminal UE access control method and device
ActiveCN106550413BImprove access success rateGuarantee perceptionWireless communicationUser perceptionComputer terminal
The application discloses a terminal UE access control method. After determining the terminal protocol version of terminal UE according to an access request sent by the terminal UE, an RNC (Radio Network Controller) judges whether the terminal protocol version is higher than the highest protocol version supported. If the terminal protocol version is higher than the highest protocol version supported, the UE is redirected under instruction according to the LTE capacity of the UE, the reason why the access request is triggered, a blind redirection switch and the neighborhood of a cell which the UE requests to access, or the access request is processed in accordance with the highest protocol version. The success rate of RRC access and the success rate of relocation are improved, user perception is ensured, and the investment of operators is protected.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Method for reducing grinding belt fault
InactiveCN104495284AChange the signal transmission methodAvoid damageConveyorsControl devices for conveyorsDistributed control systemEngineering
The invention discloses a method for reducing the grinding belt fault. The method comprises the following steps: a, shaping an iron sheet to be designed on the belt roller site, processing and mounting a new induction iron sheet, and ensuring that the effective induction time is above a standard valve, namely 0.2 second; b, additionally arranging an isolation circuit on a DCS (Distributed Control System) cabinet and protecting an FM136 input module terminal; c, selecting sensors with alarm setup functions in the control cabinet and on the site, changing a signal transmission mode of the sensor, reducing the damage of an FM136 module and the sensors. According to the method for reducing the grinding belt fault, disclosed by the invention, the defects of short effective induction time, low reliability, too high flash frequency and the like in the prior art can be overcome so as to realize the advantages of long effective induction time, high reliability and low flash frequency.
Owner:GUANGXI YUFENG CEMENT
Overvoltage protection circuit and electrical device including such a protection circuit
ActiveUS11018503B2Easy to adaptAvoid disadvantagesEmergency protection detectionEmergency protective arrangements for limiting excess voltage/currentOvervoltageVoltage generator
Owner:SCHNEIDER ELECTRIC IND SAS
Real estate information verification method based on asymmetric algorithm
ActiveCN111260528ANo sense of operationProtection inputData processing applicationsDigital data information retrievalAlgorithmData mining
The invention discloses a real estate information verification method based on an asymmetric algorithm, belongs to the field of information security, and applies a data signature concept, so that theeffects of no tampering, no repudiation and no damage to integrity can be realized after real estate key data is protected. A verification program is convenient and fast, the authenticity of the realestate information can be verified without networking after any smart phone is installed with an APP, the efficiency of real estate related services is effectively improved, and the trust cost of a benefit related party is reduced.
Owner:赵智
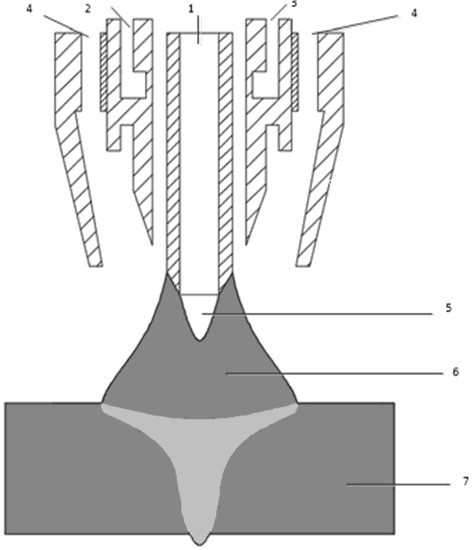
A method for welding thick plates of hollow tungsten extremely deep penetration tig welding
ActiveCN109454314BProtection inputQuality improvementArc welding apparatusWelding/cutting media/materialsThick plateShielding gas
The invention relates to a method for welding thick plates of hollow tungsten extremely deep penetration TIG welding, which comprises the following steps: step 1: fixing the workpiece to be welded on the welding fixture; -1000A, starting arc current is 350-1100A, slightly higher than welding current, cut-off current is 200-300A, starting time is 0.4-0.6s, transition time is 0.5-0.8s, falling time is 2-3s, ionized gas The flow rate is 4‑6L / min, the shielding gas flow rate is 15‑20L / min, the gas supply time is 3‑5s in advance, the inner hole of the hollow tungsten electrode is filled with argon gas, the gas flow rate is 3‑5L / min, and the shielding gas on the weld Both the shielding gas and the lower shielding gas are argon, the gas flow rate is 18-20L / min, the gas delay after welding is 15-40s, the workpiece gap is 0.2-0.5mm, and the welding speed is 200-500mm / min; Step 3: Pass Press the welding preparation and welding start buttons on the welding machine to start welding thick plates. The invention realizes the one-time penetration of the thick plate, and ensures the high quality of the welding seam while realizing the high-speed welding of the thick plate.
Owner:JIANGSU UNIV OF SCI & TECH
Auxiliary power supply for high power ups
ActiveCN102832694BAvoid current stressStable jobEmergency power supply arrangementsEngineeringFly back converter
The invention discloses an auxiliary power supply of a high-power UPS (uninterrupted power supply). The auxiliary power supply comprises a direct-current voltage input, an alternating-current voltage input, an isolating circuit for preventing reverse-filling of current, a rectification circuit, a filter circuit, a half-bridge isolating switch conversion circuit, a high-frequency rectification filter circuit, a voltage and current sampling circuit, a feedback control circuit, a PWM (pulse width modulation) controller and a double-end fly-back converter. The direct-current voltage input is sequentially isolated and filtered via the isolating circuit and the filter circuit, is converted into high-frequency PWM alternating-current voltage by the half-bridge isolating switch conversion circuit, and is isolated, coupled, rectified and filtered by the high-frequency rectification filter circuit, and then direct-current voltage is output. The half-bridge isolating switch conversion circuit is controlled by the PWM controller to output stabilized direct-current voltage. An input end of the double-end fly-back converter is connected with an output end of the filter circuit so that the double-end fly-back converter can access to a power source, and the double-end fly-back converter supplies power to the PWM controller. The auxiliary power supply of the high-power UPS can supply reliable and stable direct-current voltage output to the UPS.
Owner:FOSHAN BAYKEE NEW ENERGY TECH INC
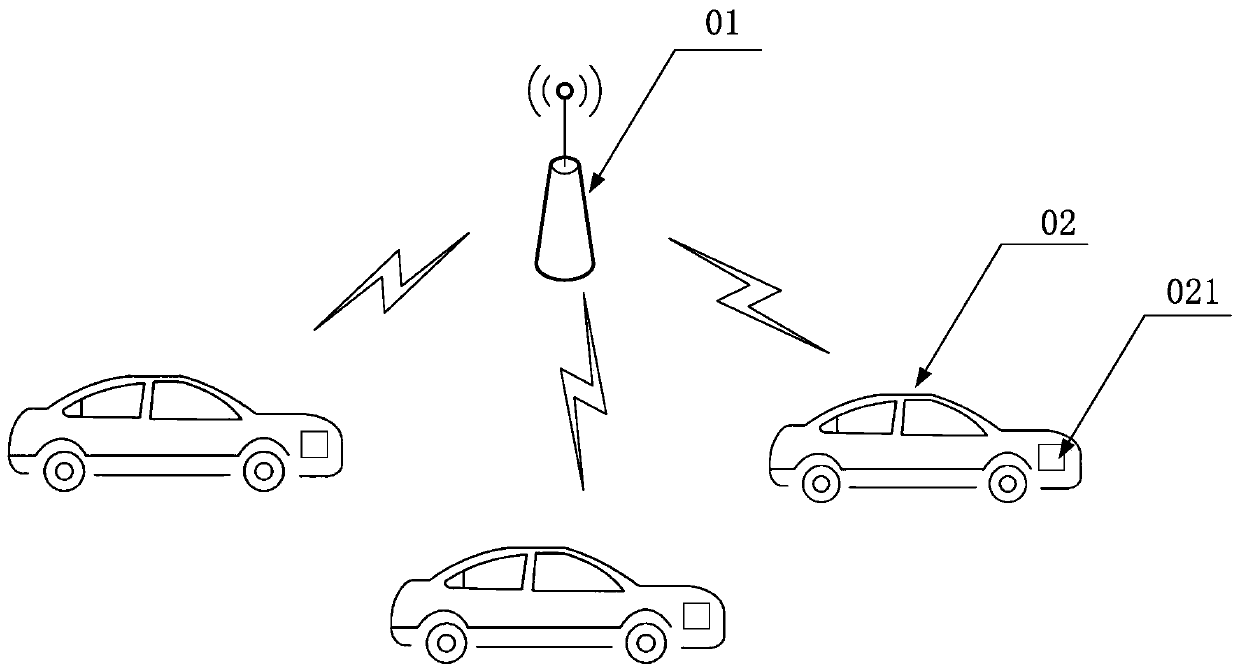
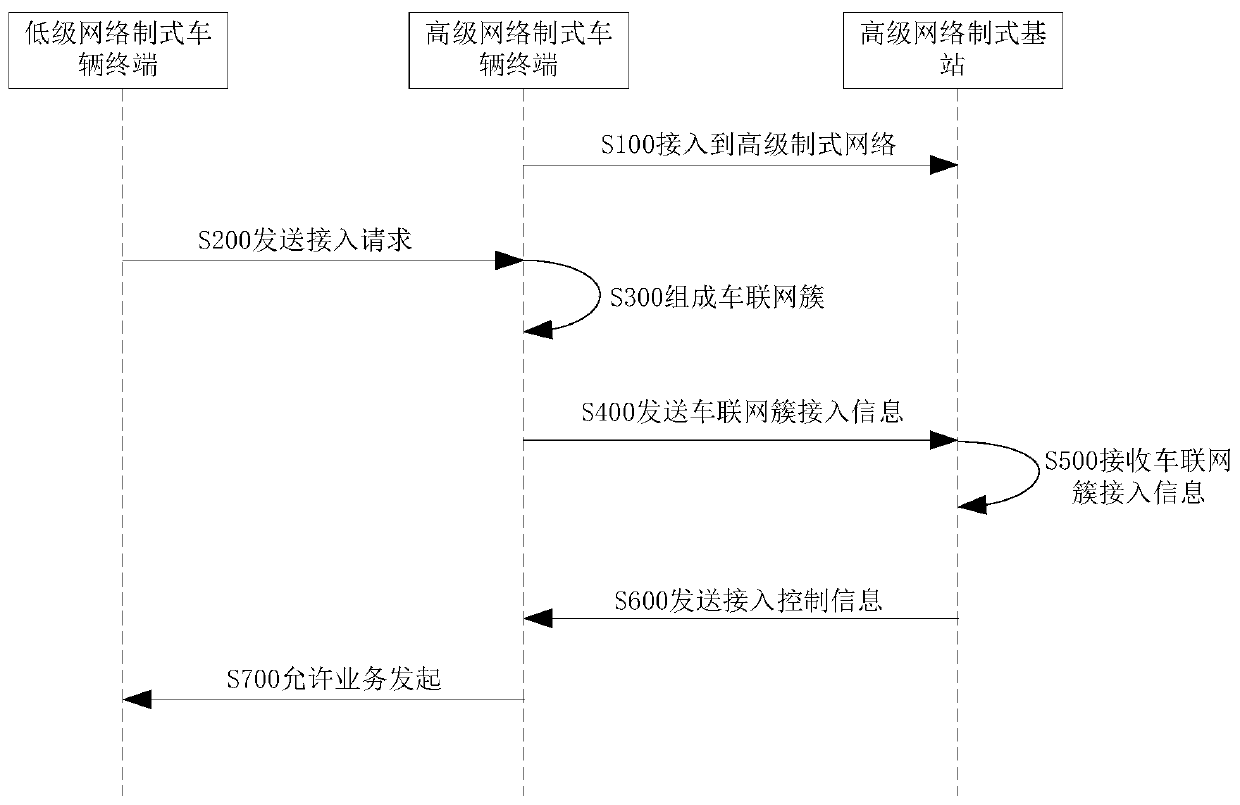
Networking method and device for a vehicle networking system, and a vehicle networking system
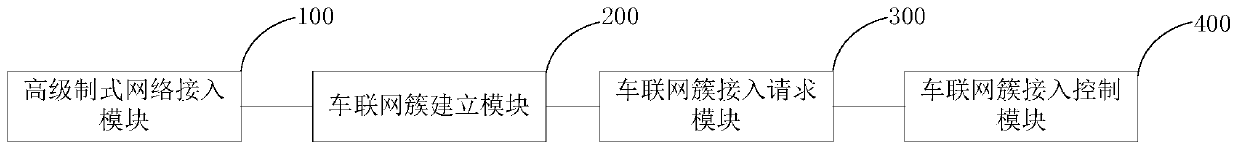
ActiveCN106162806BReduce shockProtection inputAssess restrictionNetwork topologiesThe InternetReal-time computing
The invention relates to an Internet-of-Vehicles system networking method applied to a high-level network type vehicle terminal. The method comprises the steps that access is made to a high-level type network through a high-level network type base station; an access request from a low-level network type vehicle terminal is received, and a corresponding Internet-of-Vehicles cluster is formed with the low-level network type vehicle terminal according to the access request; Internet-of-Vehicles cluster access information is sent to the high-level network type base station, wherein the Internet-of-Vehicles cluster access information comprises identification information of the Internet-of-Vehicles cluster; access control information returned by the high-level network type base station and corresponding to the identification information of the Internet-of-Vehicles cluster is received, and a communication message from the high-level network type base station is sent to the low-level network type vehicle terminal in the Internet-of-Vehicles cluster according to the access control information, or a communication message from the low-level network type vehicle terminal is sent to the high-level network type base station. The method enables the low-level network type vehicle terminal to have access to a high-level type network through application service so that the low-level network type vehicle terminal can use high-level type network resources.
Owner:上海工业控制安全创新科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com