Technology type hardware Trojan virus monitoring method and apparatus
A hardware Trojan horse and monitoring device technology, applied in the direction of measuring devices, measuring electricity, measuring electrical variables, etc., can solve problems such as low monitoring efficiency and inaccurate monitoring results, and achieve efficient and accurate monitoring
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
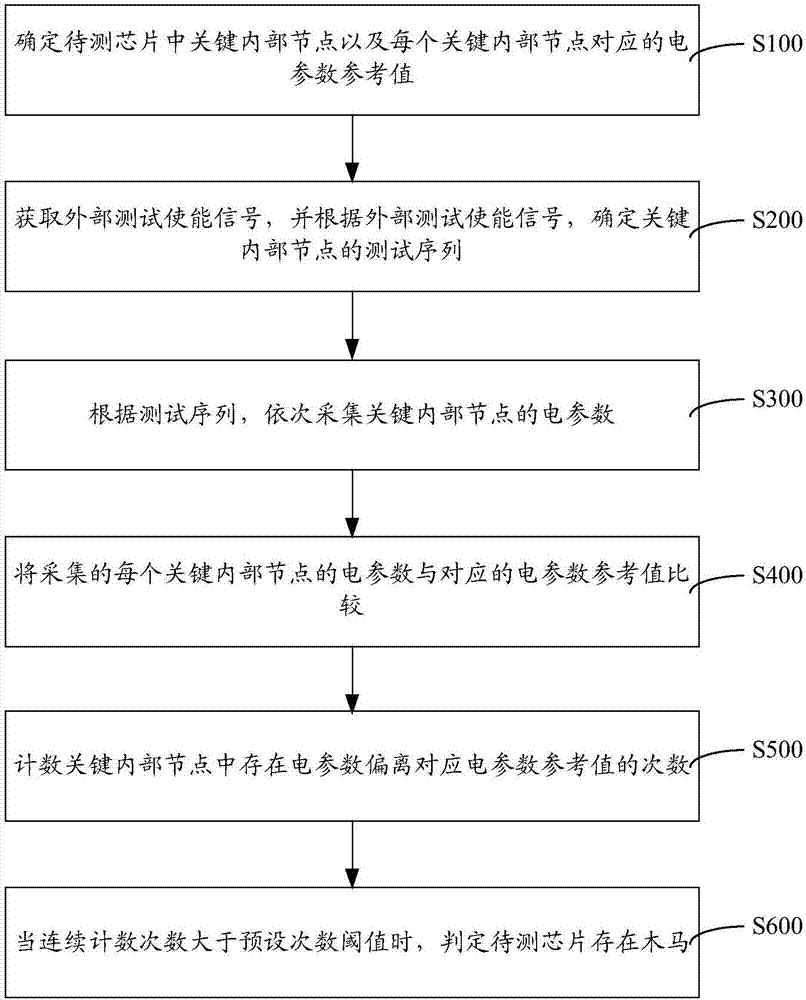
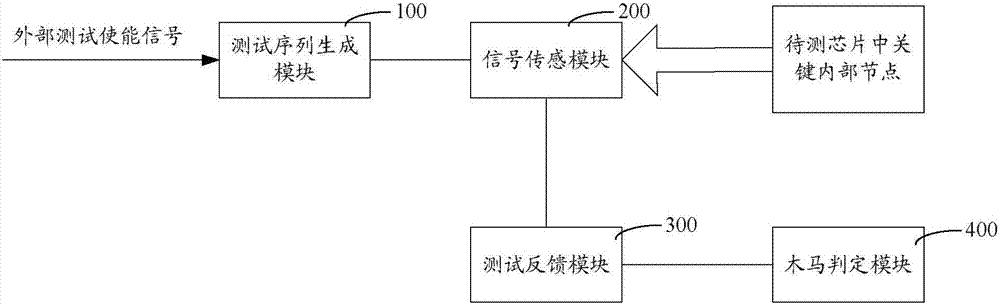
[0021] Such as figure 1 Shown, a kind of technology type hardware Trojan horse monitoring method comprises steps:
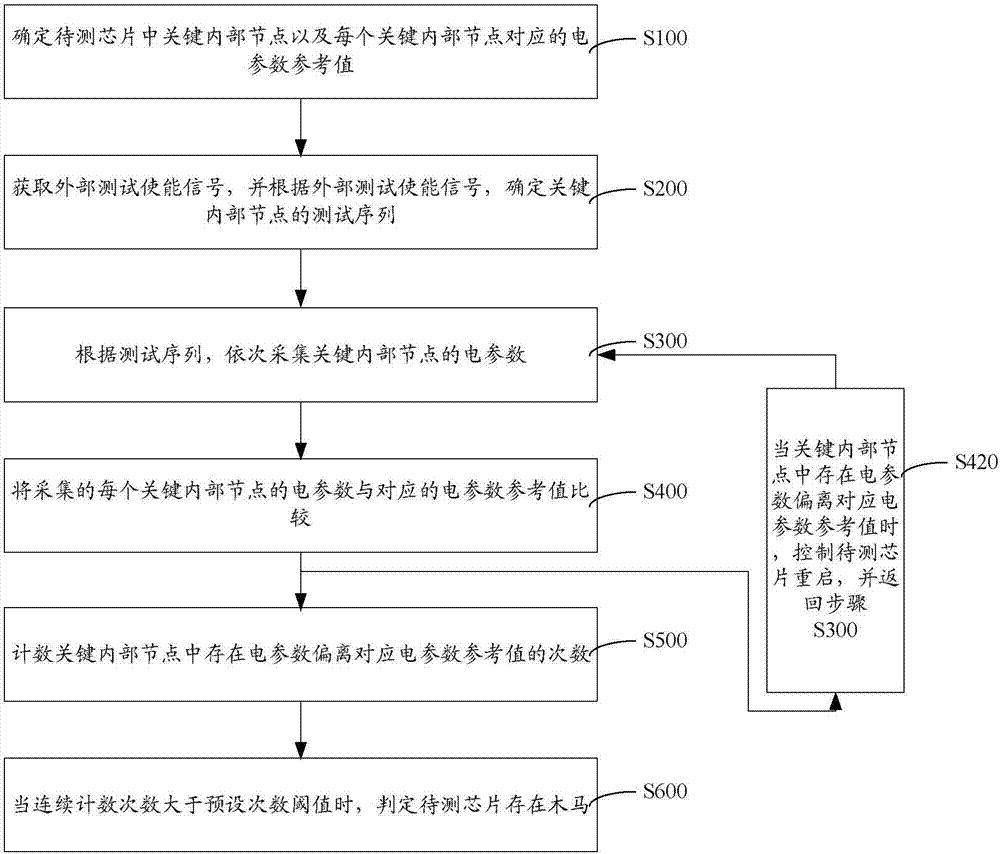
[0022] S100: Determine key internal nodes in the chip to be tested and electrical parameter reference values corresponding to each key internal node.
[0023] First of all, it is necessary to understand the attribute parameters of the chip to be tested and determine the key internal nodes in the chip to be tested. The key internal nodes in the chip under test refer to circuit nodes related to the overall function, performance or reliability of the chip under test. The step of determining the key internal nodes in the chip to be tested includes traversing the chip to be tested, searching for circuit nodes related to the overall function, performance or reliability of the chip to be tested, and using the found circuit nodes as key internal nodes in the chip to be tested. To put it simply, it is to conduct some routine research and testing on the chip to be test...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com