Method for detecting suspected online water armies for microblog
A discovery method and microblogging technology, applied in other database retrieval, network data retrieval, instruments, etc., can solve problems such as inability to discover groups, achieve full utilization, strong modularity, and reduce complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention is described in detail below in conjunction with accompanying drawing and embodiment:
[0031] Take a Sina Weibo user as an example:
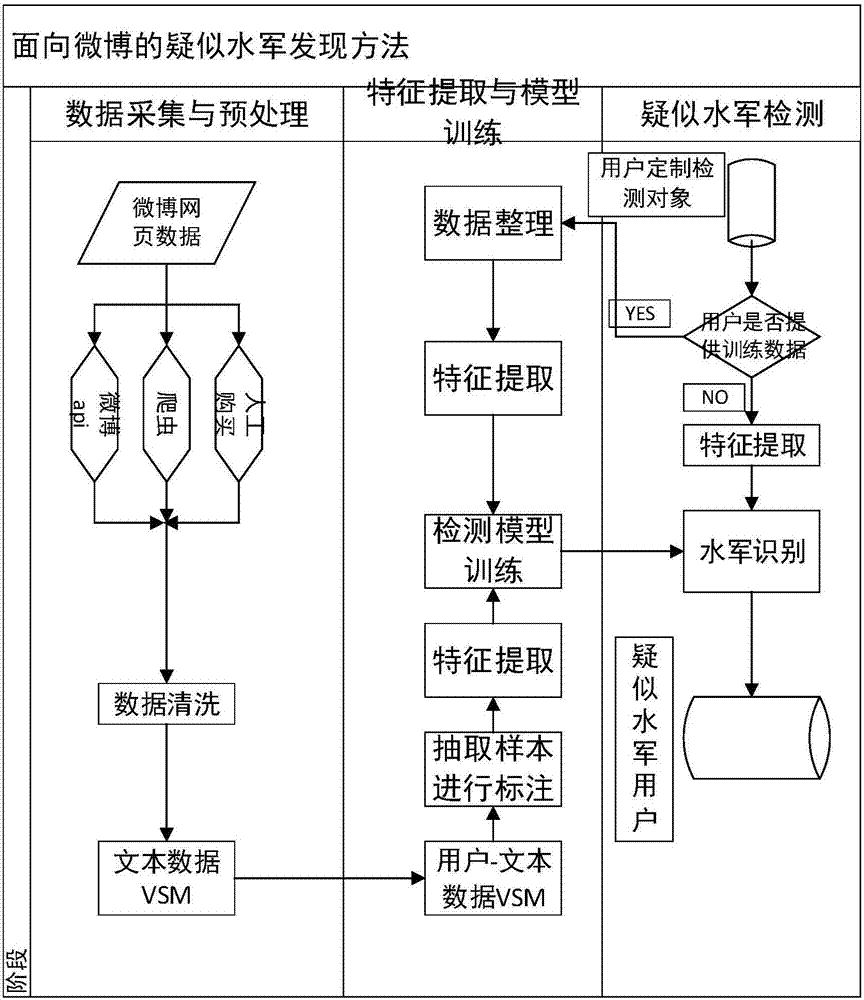
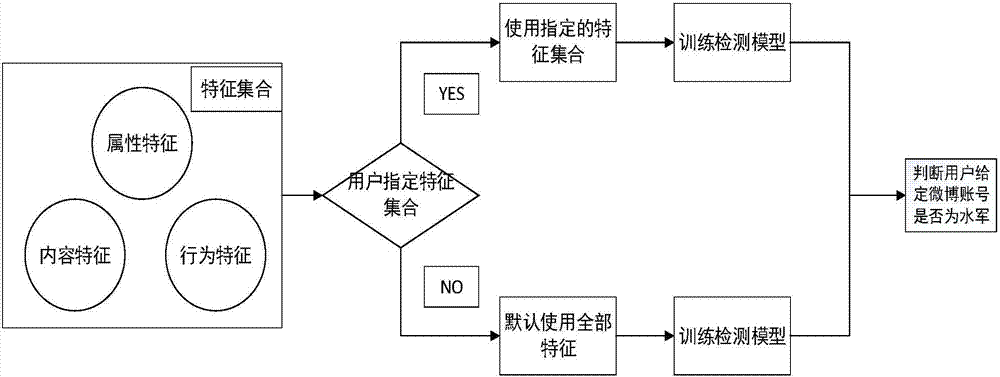
[0032]The user ID is 5364402211. When it is necessary to judge whether this microblog account is a navy account, only the user ID of user 5364402211 needs to be given, and the method of the present invention can collect and analyze relevant data according to the user ID, and finally determine whether this account is a navy account. The navy gives the prediction result. Specific process such as figure 1 shown in detail below.
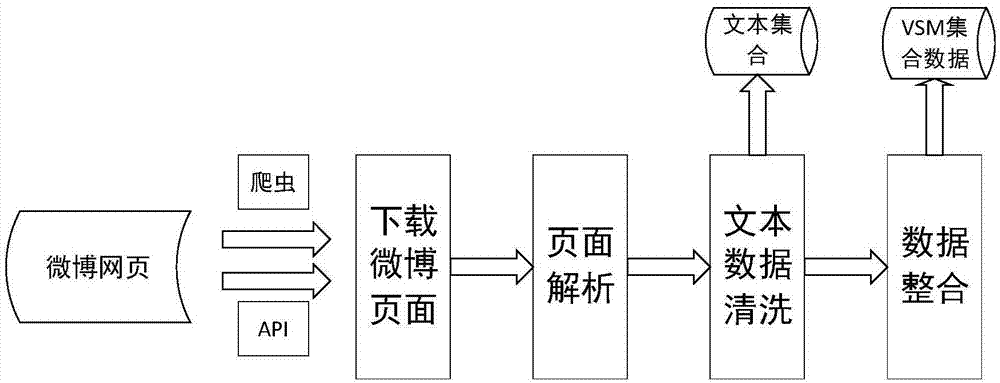
[0033] Collect relevant microblog data according to step 1:
[0034] Collect the Sina Weibo data we want to study or directly obtain the public data provided by Weibo. The data is collected by establishing a buffer URL queue, using the breadth-first search algorithm (BFS) to search for webpage links, scanning and downloading each node webpage, and parsing the page to remove irrelevant noi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com