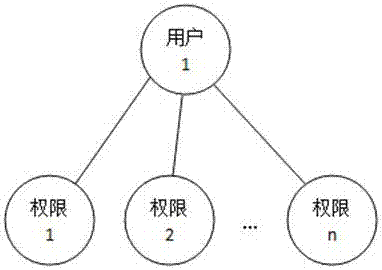
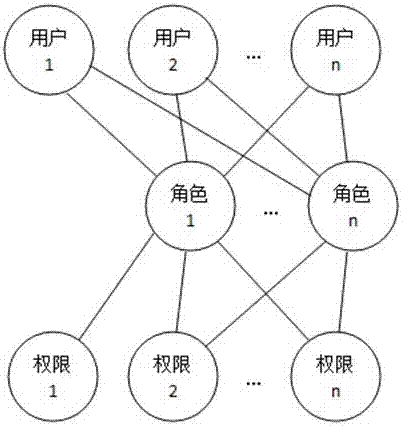
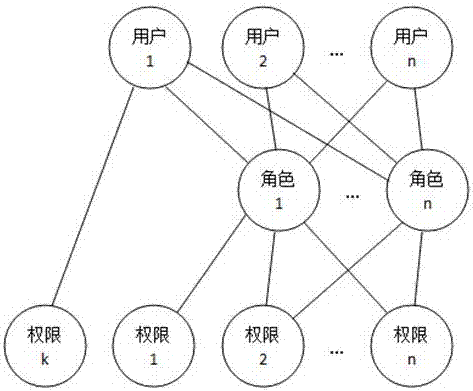
One-to-one authority authorization method and system on user based on roles
An authorization system and role technology, applied in user identity/authority verification, transmission systems, instruments, etc., can solve problems such as loss of system users, increase of authorization, cumbersome and troublesome operations of users, etc., to reduce the probability of authorization errors, The effect of improving efficiency and reliability, and improving the efficiency of authority management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
[0072] [Example 2] A one-to-one authority authorization method for users based on roles, including the following sequential steps:
[0073] S1: Establish roles, each role is an independent individual, not a group / class;
[0074] S2: Associate users with roles, where a role can only be associated with a unique user at the same time period, and a user is associated with one or more roles;
[0075] S3: Authorize the roles established by S1 respectively.
[0076] [Embodiment 3] In order to realize the above authority authorization method, the role-based one-to-one authority authorization system for users should at least include a role establishment unit, a role authorization unit and a user-role association unit;
[0077] The role establishment unit is used to perform role layout according to positions and establish system roles, each role is an independent individual, not a group / category; the composition of the system role is: position name + post number; for example: workshop ...
Embodiment 4
[0080] [Example 4] The following example shows that after employee Zhang San enters a company, the relationship among employees, users and roles is as follows:
[0081] 1. New entry: For new employees, just select the corresponding position number / position number role for the user (employee) to associate, for example: Zhang San joins the company (the company assigns a Zhang San user to Zhang San) , the job content is in the sales department, responsible for the sales of refrigerator products in the Beijing area (the corresponding role is the role of "Sales Engineer 5" under the sales department), then user Zhang San can directly select the role of "Sales Engineer 5" to associate .
[0082] 2. Increase positions: After Zhang San worked for a period of time, the company also arranged for Zhang San to be responsible for the sales of TV products in the Beijing area (the corresponding role is the role of "Sales Engineer 8" under the first sales department) and concurrently as the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com