Content audit system based on active defense mechanism and content audit method thereof
An active defense and content auditing technology, applied in the field of network security, can solve problems such as the abuse of power by managers, the reduction of damage to industrial network equipment, and improper operations by executives.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
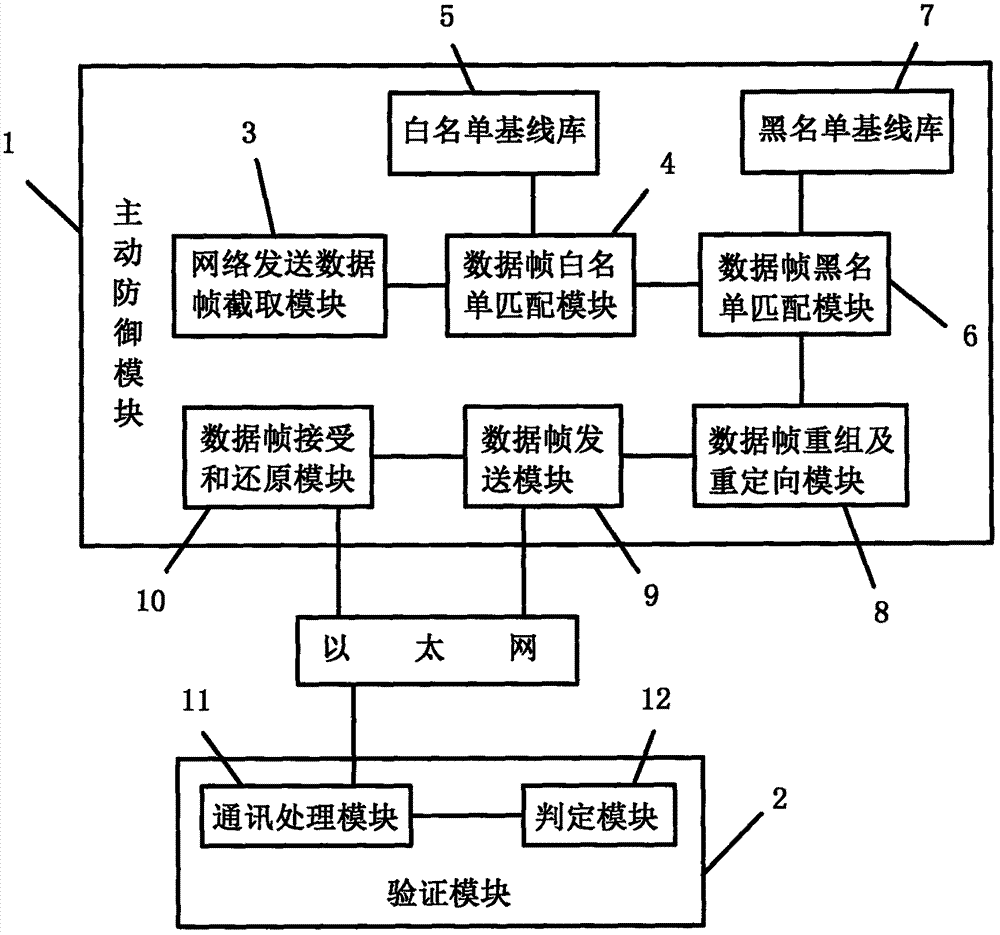
[0039] refer to Figure 1-6 , a specific embodiment of the present invention includes an active defense module 1 and a verification module 2, and the active defense module 1 and the verification module 2 are connected through Ethernet communication;
[0040] Active Defense Module 1 includes,
[0041] The data frame interception module 3 sent by the network is used to intercept the data frame;
[0042]The data frame whitelist matching module 4 is used to carry out source-destination MAC, source-destination IP, transport layer protocol, source-destination port and other data of the intercepted network transmission data frame with each whitelist data in the whitelist baseline library 5. Compare and match data such as destination MAC, source and destination IP, transport layer protocol, and source and destination ports;
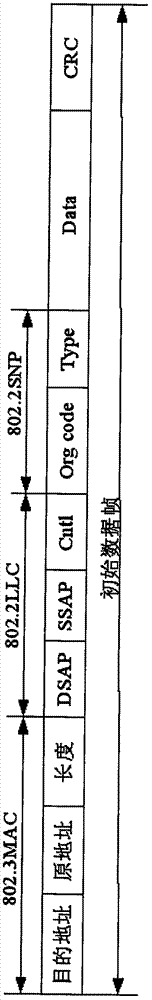
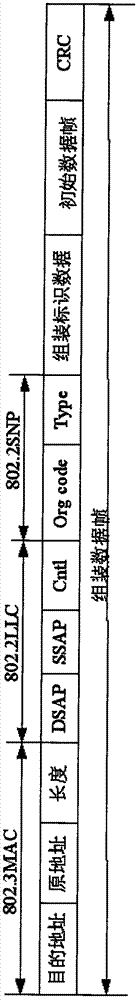
[0043] The data frame blacklist matching module 6 is used for data such as source destination MAC, source destination IP, transport layer protocol, source dest...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com