A kind of active defense method and device
An active defense and versioning technology, applied in the direction of program code conversion, code compilation, program/content distribution protection, etc., to increase the cost of detection and attack, increase uncertainty, and reduce the time window of opportunity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] In order to facilitate the understanding of those skilled in the art, the present invention will be further described below in conjunction with the accompanying drawings, which cannot be used to limit the protection scope of the present invention. It should be noted that, in the case of no conflict, the embodiments in the present application and various manners in the embodiments can be combined with each other.
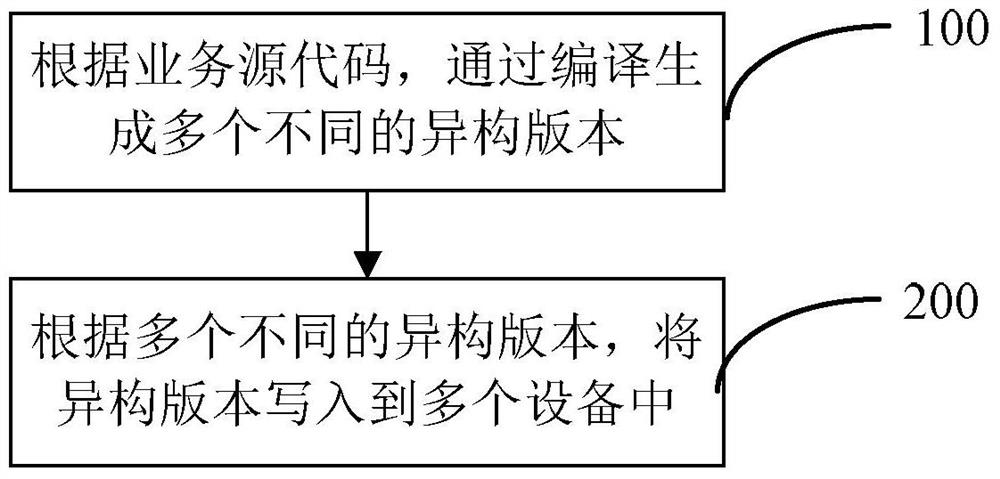
[0053] see Figure 1A , the present invention proposes a kind of active defense method, described method comprises:
[0054] Step 100, generate multiple different heterogeneous versions by compiling according to the business source code;
[0055] Step 200, write the heterogeneous versions into multiple devices according to the multiple different heterogeneous versions.
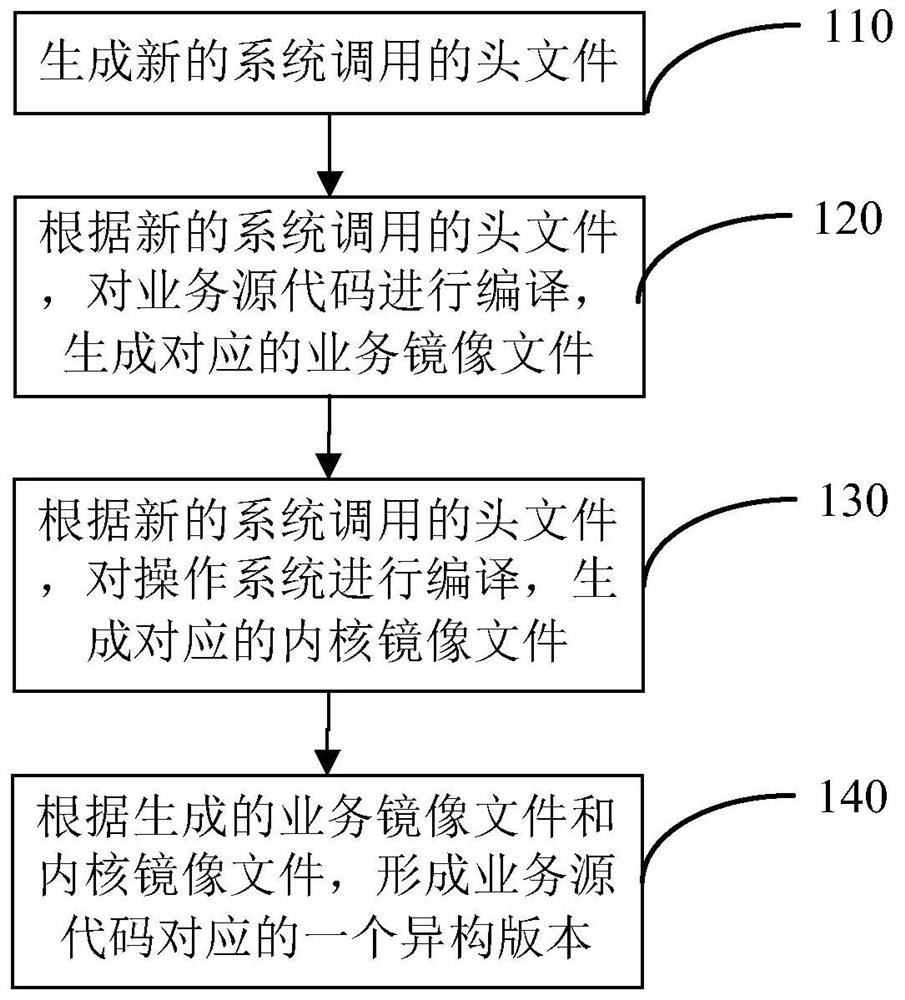
[0056] Among them, see Figure 1B , step 100 includes:
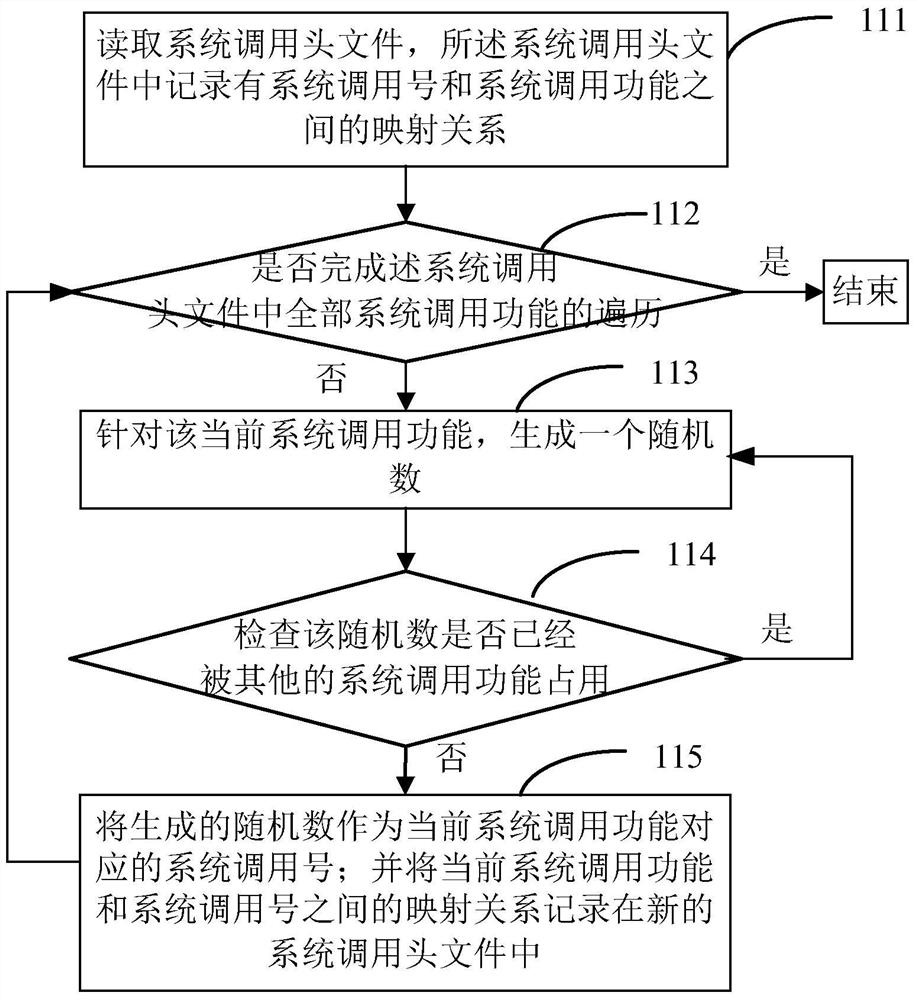
[0057] Step 110, generating a header file for a new system call;
[0058] Step 120, compile the business source code according to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com