Suspicious mobile phone short message identification system and using method thereof
A technology for identifying systems and text messages, applied in the field of information security, can solve problems such as ineffective protection of users, inability to update in time, inability to obtain fraudulent information, etc., and achieve the effects of faster training model, high scalability, and improved performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
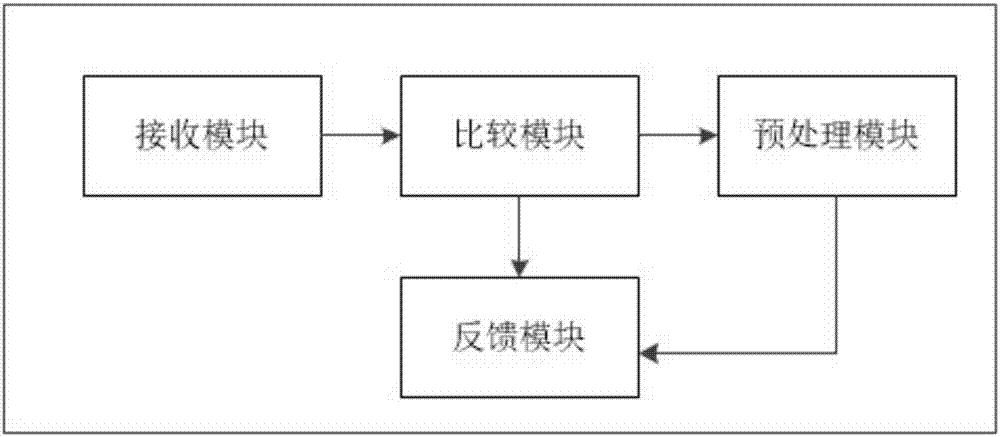
[0023] like figure 1 As shown, an identification system for suspicious mobile phone short messages includes a receiving module, a preprocessing module, a comparison module and a feedback module. The receiving module passes the received short messages to the preprocessing module for preprocessing, and the preprocessing module preprocesses the short messages and Passed to the comparison module, the comparison module compares the text features of the received short message and the number of the sent short message with the deep learning model and sends the comparison result to the feedback module, and the feedback module gives feedback to the user according to the comparison result of the comparison module, wherein, SMS messages include SMS text and / or URLs.
[0024] The preprocessing of the short message by the preprocessing module includes extracting the number for sending the short message, extracting the text and / or URL of the short message and generating a feature vector.
...
Embodiment 2
[0028] like figure 2 As shown, a method for identifying a suspicious mobile phone text message includes:
[0029] Step 100, receive a short message, the short message includes short message text and / or URL, and enter step S110;
[0030] Step S110, locally judge whether the text message is a suspicious text message on the mobile phone, if the local judgment text message is a suspicious text message, then enter step S400; if the local judgment is a normal text message, then enter step S300;
[0031] Step S400, uploading suspicious text messages to the cloud for further judgment and feedback to the user, wherein the cloud updates the sample set according to the uploaded suspicious text messages, and the cloud uses the Spark algorithm;
[0032] Step S300, no feedback, silently waiting for the next text message.
Embodiment 3
[0034] like image 3 As shown, a method for identifying a suspicious mobile phone text message includes:
[0035] Step 100, receive a short message, the short message includes a short message text, and enter step 200;
[0036] Step 200, extracting the text features of the short message and the number for sending the short message, and entering step 300;
[0037] Step 300, first compare the number of sending text messages with the suspicious samples of the local deep learning model, then compare the text of the text message with the suspicious samples of the local deep learning model, if the comparison result is yes, it is determined that the text message is a suspicious text message, then enter step 500; if If the judgment result is no, then enter step 400;
[0038] Step 400, no feedback content, no feedback to the user;
[0039] Step 500, upload suspicious text messages to the cloud, and enter step 600;
[0040] Step 600, compare the text features of the short message wit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com