Signature verification method, device and system
A signature verification and equipment technology, applied in the field of communications, can solve the problems of inability to use high-performance processing hardware, consume CPU running time, and not have digital signatures, so as to ensure authenticity and integrity, improve security, and improve reliability. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
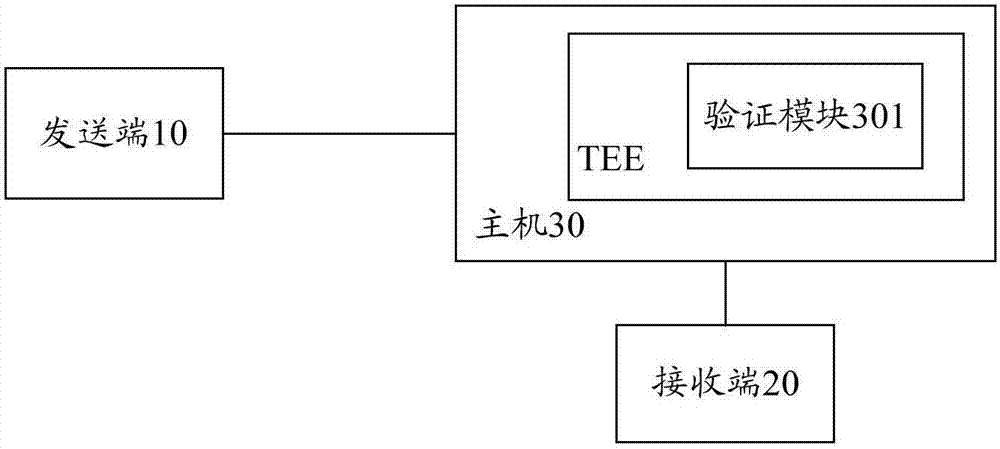
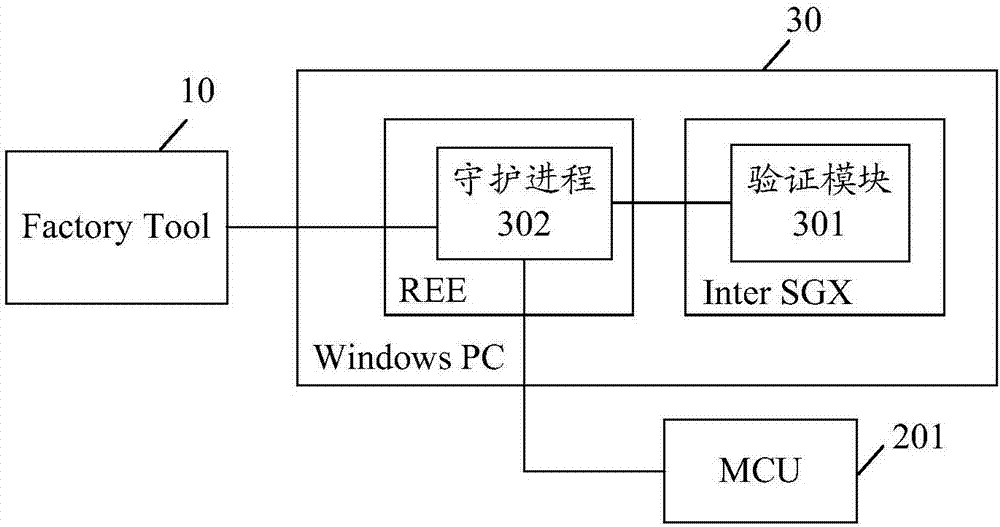
Image
Examples
Embodiment Construction
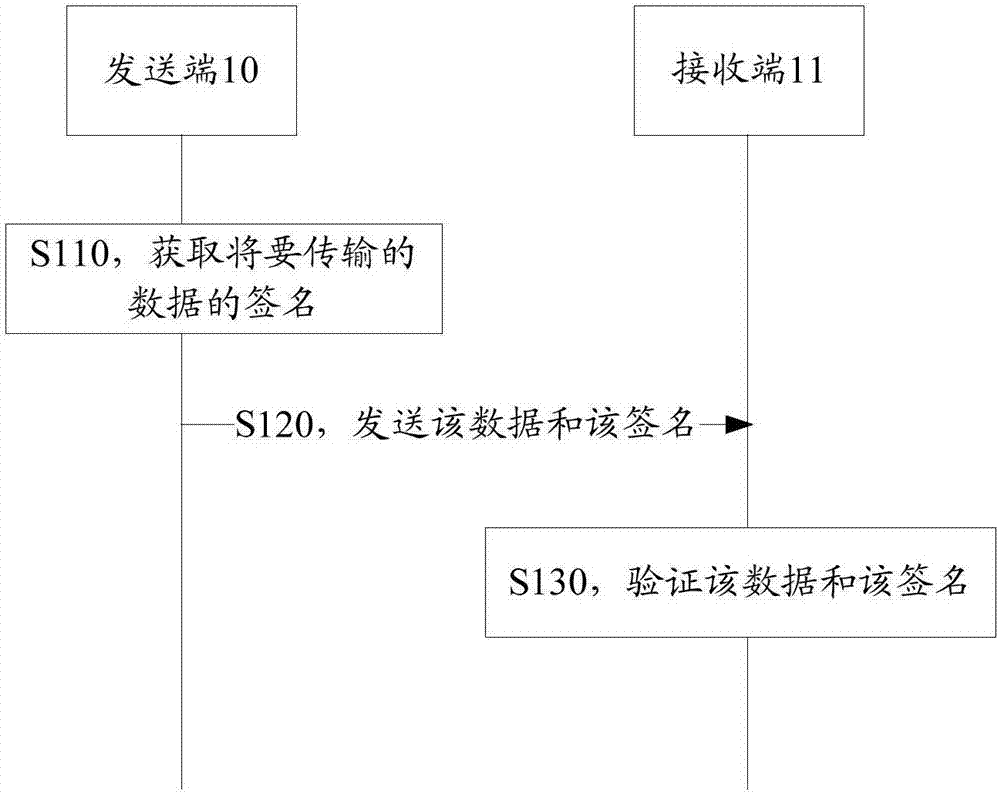
[0042] figure 1 A schematic flowchart of data transmission through digital signature technology is shown. figure 1 The digital signature algorithm used in the method of transmitting data is the RSA public key cryptography algorithm. In this method, both the sending end 10 and the receiving end 11 have the capability of digital signature, including:
[0043] S110, the sender 10 acquires the signature Sig of the data M to be transmitted M .
[0044] S120, the sending end 10 sends the data M and the signature Sig to the receiving end 11 M .
[0045] S130, the receiver 11 verifies the signature Sig M and data M.
[0046] Specifically, take Alice and Bob respectively using the sending end and the receiving end to perform identity authentication as an example for illustration. When Alice needs to send data M to Bob, she uses her own private key (SK) to sign the data M to get Sig M . Wherein, the data M is plaintext data. It should be noted that only Alice owns Alice's priv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com