Privacy protection hierarchical clustering method based on vector homomorphic encryption
A technology of homomorphic encryption and privacy protection, applied in the field of vector clustering, it can solve problems such as data privacy leakage, and achieve the effect of expanding the scope of application, ensuring the reliability of data privacy, and efficiently and accurately clustering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
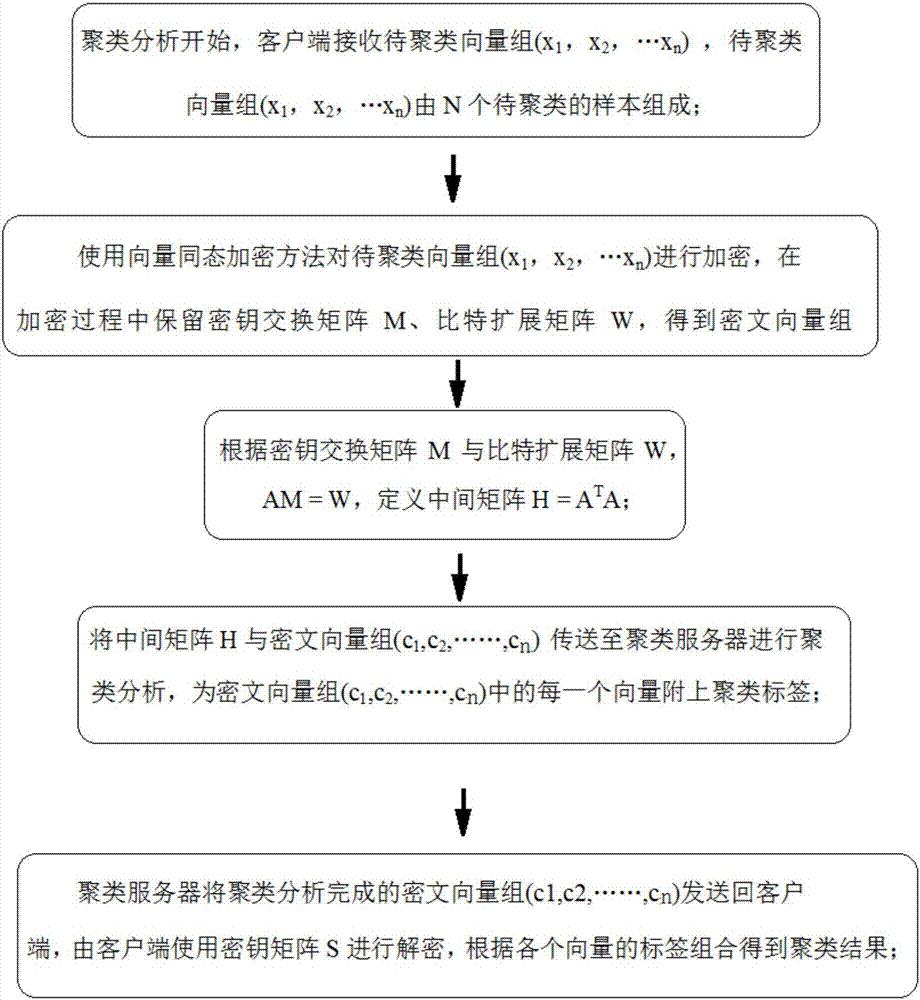
[0038] This embodiment provides a privacy-preserving hierarchical clustering method based on vector homomorphic encryption, such as figure 1 , the method includes:
[0039] (1) The clustering analysis starts, and the client receives the vector group to be clustered (x 1 , x 2 ,...x n ), the vector group to be clustered (x 1 , x 2 ,...x n ) consists of N samples to be clustered;
[0040] (2) Use the vector homomorphic encryption method to treat the clustering vector group (x 1 , x 2 ,...x n ) for encryption, the key exchange matrix N and the bit expansion matrix W are retained during the encryption process, and the ciphertext vector group (c 1 ,c 2 ,...,c n );
[0041] (3) According to key exchange matrix N and bit extension matrix W, calculate matrix A, make AN=W, define intermediate matrix H=A T A;
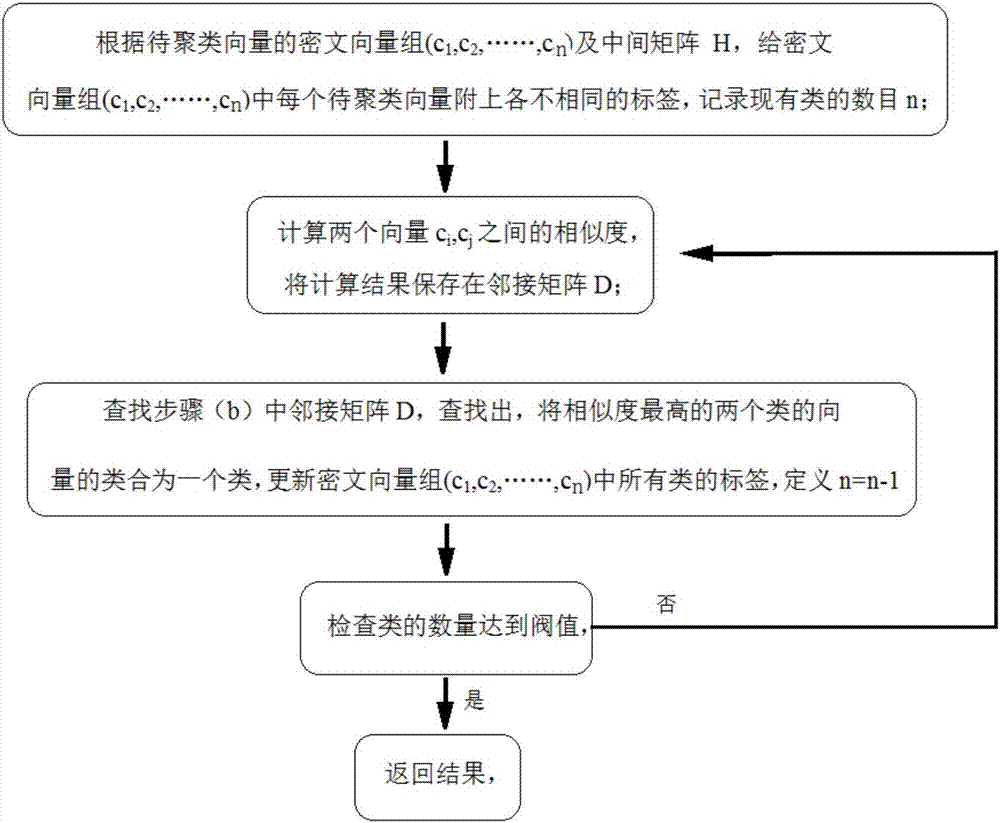
[0042] (4) Combine the intermediate matrix H with the ciphertext vector group (c 1 ,c 2 ,...,c n ) to the clustering server for clustering analysis, which is the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com