WEB abnormal traffic monitoring method based on integrated learning
An integrated learning and abnormal traffic technology, applied in the field of machine learning, can solve problems such as noise data interference, denial of service attacks, manual update of feature database, etc., and achieve high precision, integrity and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The technical solutions in the embodiments of the present invention will be described clearly and in detail below with reference to the drawings in the embodiments of the present invention. The described embodiments are only some of the embodiments of the invention.
[0047] The technical scheme that the present invention solves the problems of the technologies described above is:
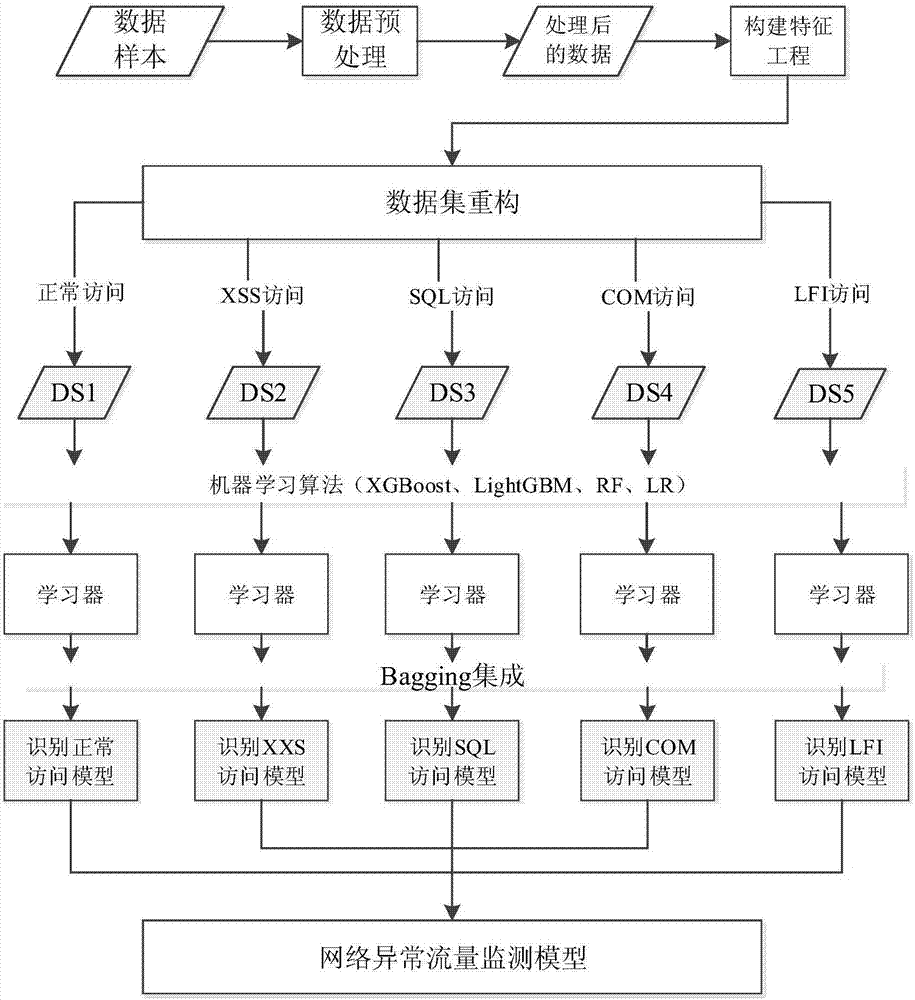
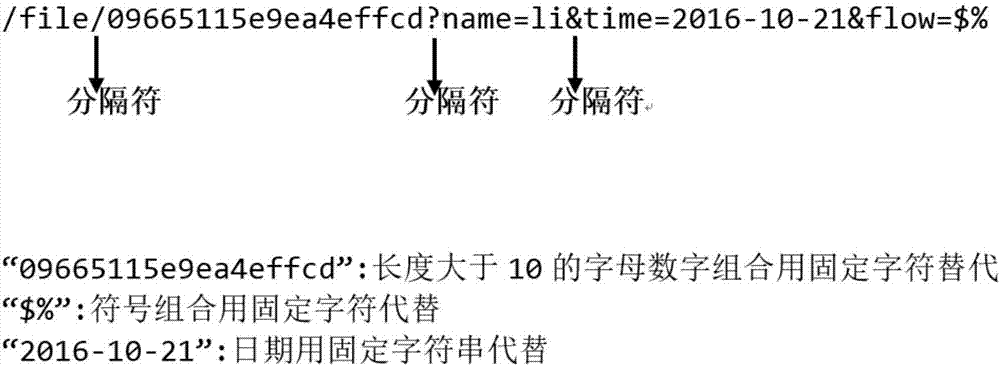
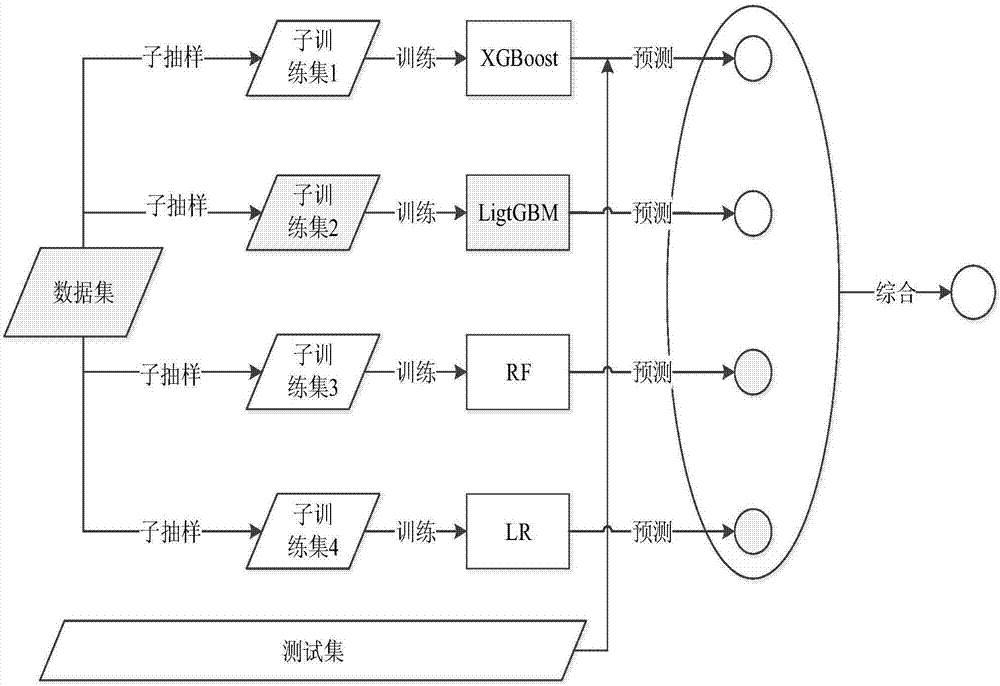
[0048] The present invention proposes a model for solving abnormal traffic monitoring. figure 1 Shown is a flowchart of the entire model. Preprocess the data set, such as segmenting symbols such as "&" and "=", and extract valid information in URLs to improve processing efficiency. figure 2 Cutting examples for URLs. The processed data are feature extracted by statistical methods such as mutual information and information entropy. After the construction of the feature engineering, according to the different nature of the visit, the data sets with different characteristics are constructed ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com