Disk decoding method and device of electronic equipment
A technology of electronic equipment and disk, applied in the protection of internal/peripheral computer components, digital data authentication, etc., can solve the problems of cumbersome disk decryption process, achieve the effect of ensuring safety and simplifying manual operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
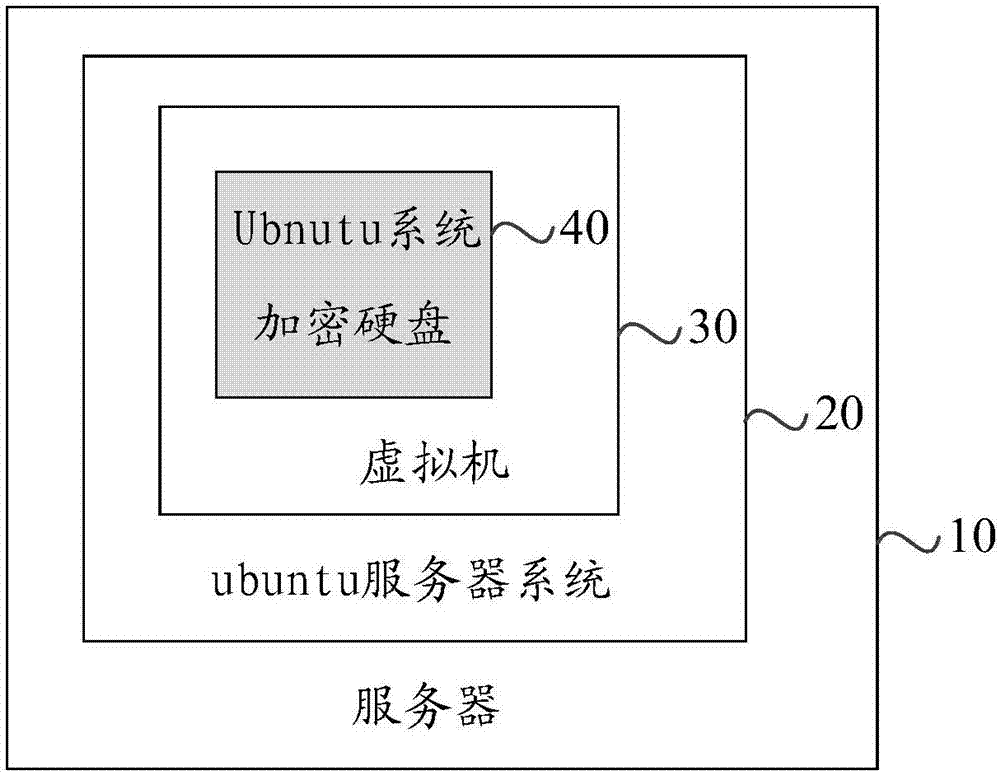
[0047] In order to describe in detail the disk decryption method of the electronic device provided in Embodiment 1, a specific implementation example will be described below. The electronic device in this embodiment is specifically a server, and an applicable scenario of the present application is briefly introduced below. Such as figure 2 as shown, figure 2 The outermost among them is server 10, and Ubuntu server system 20 is installed on server 10, can simulate a plurality of virtual machines 30 (Virtual Box) on above-mentioned server 10 usually, promptly on the disk of this server 10, for every virtual machine 30 divides a section of disk storage space, and the Ubuntu system 40 is also running in the virtual machine 30. Generally, a service program (not shown) is running in the Ubuntu system 40. These service programs can respond to the operation of the client (not shown), Provide services to clients. In addition, a ukey device (not shown) can be connected to the above...
Embodiment 1
[0069] The disk decryption method provided in Embodiment 1 is executed in the electronic device, and the disk decryption scheme is also executed on the side of the ukey device. Based on this, this embodiment 3 provides a disk decryption method of the electronic device, which is applied to the ukey device, such as image 3 As shown, it specifically includes the following steps:
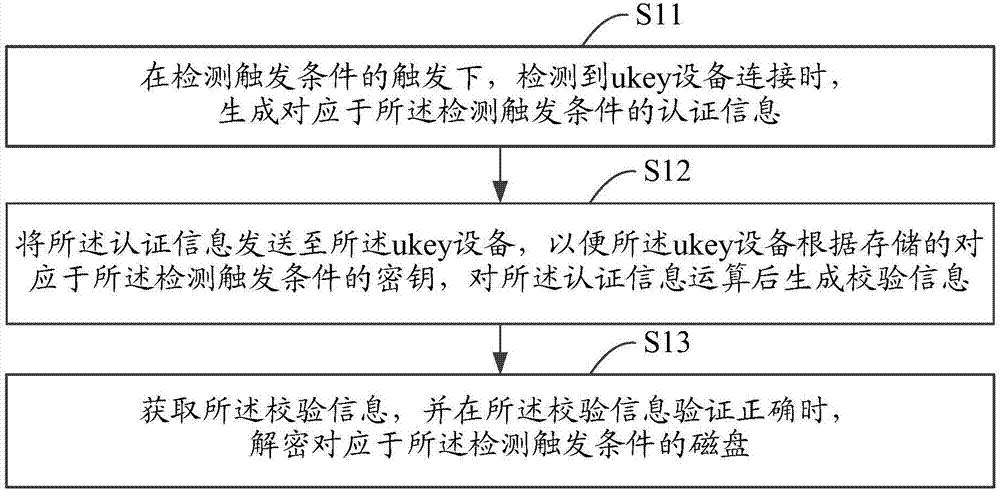
[0070] Step S31: Receive the authentication information sent by the electronic device, wherein the received authentication information is generated by the electronic device after detecting that the ukey device is connected under the trigger of the detection trigger condition, and the generated authentication information corresponds to the detection trigger condition .
[0071] The detection trigger condition in this step includes: a first detection trigger condition and a second detection trigger condition; the ukey device stores: a first key corresponding to the first detection trigger condition, and,...
Embodiment 4
[0077] Corresponding to the disk decryption method for electronic equipment provided in Embodiment 1, the present application also provides a disk decryption device, which can be applied on the electronic equipment side, and is used to simplify the manual work required for disk decryption under the premise of ensuring the safety of the electronic equipment. Operation, the device may include:
[0078] An authentication information generating module, configured to generate authentication information corresponding to the detection trigger condition when the ukey device is detected to be connected under the trigger of the detection trigger condition;
[0079] An authentication information sending module, configured to send the authentication information to the ukey device, so that the ukey device generates verification information after calculating the authentication information according to the stored key corresponding to the detection trigger condition;
[0080] The verification...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com