Payment verification method, system, mobile device, and security authentication device
A technology of security authentication equipment and mobile equipment, applied in the direction of payment system, payment system structure, protocol authorization, etc., can solve the problem of not being able to take into account both security and user experience at the same time, achieve both security and user experience, and overcome security and user experience , good user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
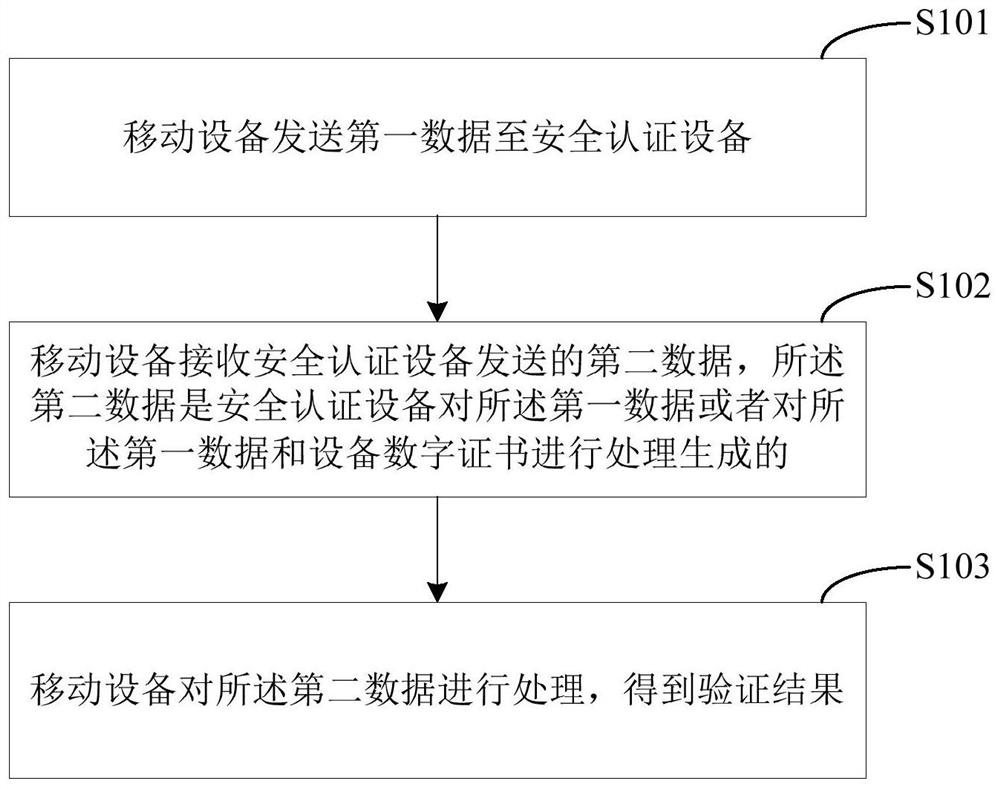
[0068] see figure 1 , is a schematic flow chart of the payment verification method provided in Embodiment 1 of the present invention, and is illustrated by taking the mobile device side as an example. As shown in the figure, the method may include the following steps:
[0069] In step S101, a mobile device sends first data to a security authentication device.
[0070] In the embodiment of the present invention, the security authentication device may be a Bluetooth security authentication device, or may be a WiFi security authentication device.
[0071] The bluetooth security authentication device may be a bluetooth card shield, a bluetooth smart bracelet, a bluetooth smart watch, etc., which is not limited here.
[0072] The first data may be a plain text of a random number, and may also be an instruction for the mobile device to request the security authentication device to provide a device digital certificate.
[0073] When the mobile device needs to conduct a transaction,...
Embodiment 2
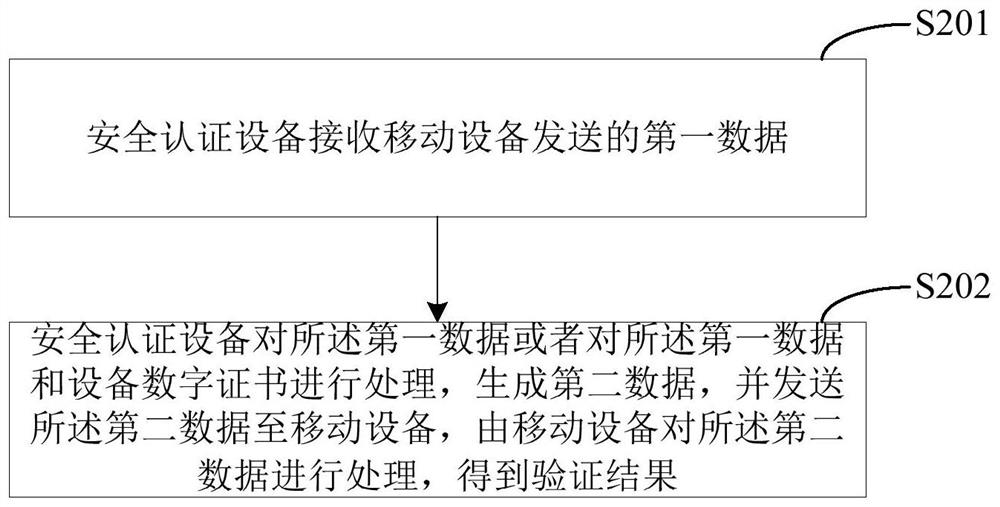
[0100] see figure 2 , is a schematic flow chart of the payment verification method provided in Embodiment 2 of the present invention, and is illustrated by taking the security authentication device side as an example. As shown in the figure, the method may include the following steps:
[0101] In step S201, the security authentication device receives first data sent by the mobile device.
[0102] Step S202, the security authentication device processes the first data or the first data and the device digital certificate, generates second data, and sends the second data to the mobile device, and the mobile device processes the second data The data is processed and the verification results are obtained.
[0103] In the embodiment of the present invention, if the first data is random number plaintext and the second data is random number ciphertext, the security authentication device processing the first data includes the following steps:
[0104] Step 1. The security authenticat...
Embodiment 3
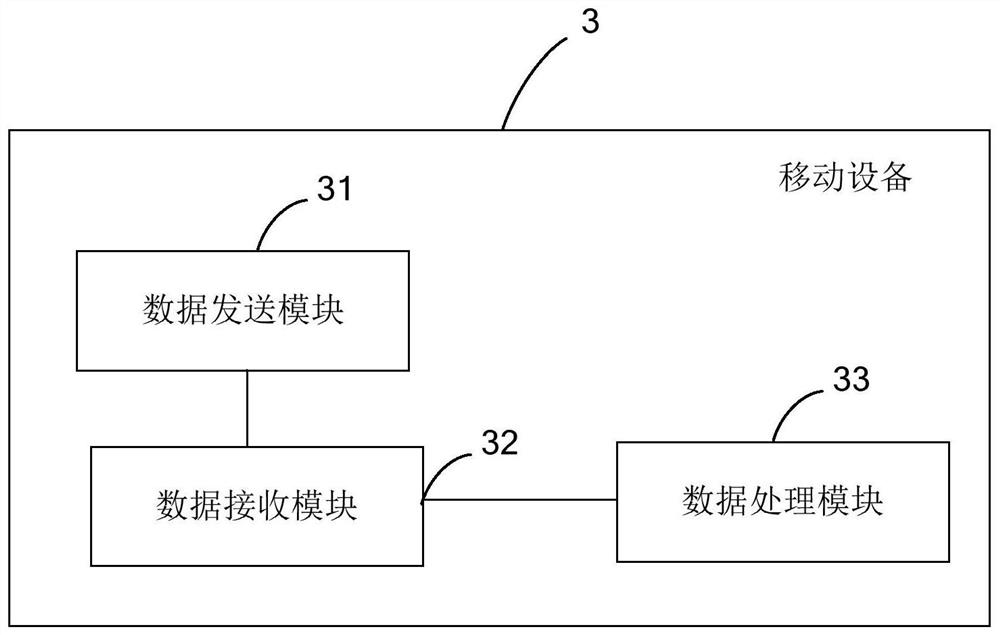
[0115] image 3 A schematic block diagram of the mobile device 3 provided by Embodiment 2 of the present invention is shown, and for convenience of description, only parts related to the embodiment of the present invention are shown. The mobile device 3 includes: a data sending module 31 , a data receiving module 32 and a data processing module 33 .
[0116] Wherein, the data sending module 31 is used to send the first data to the security authentication device;
[0117] The data receiving module 32 is configured to receive second data sent by the security authentication device, the second data is generated by the security authentication device by processing the first data or the first data and the device digital certificate;
[0118] The data processing module 33 is configured to process the second data to obtain a verification result.
[0119] Specifically, the first data is random number plaintext, the second data is random number ciphertext, and the random number ciphert...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com