Mobile application information security system for power system and transmission method thereof
An information security system and mobile application technology, applied in the field of smart grid, can solve problems such as hidden dangers of data security, and achieve the effect of ensuring confidentiality and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
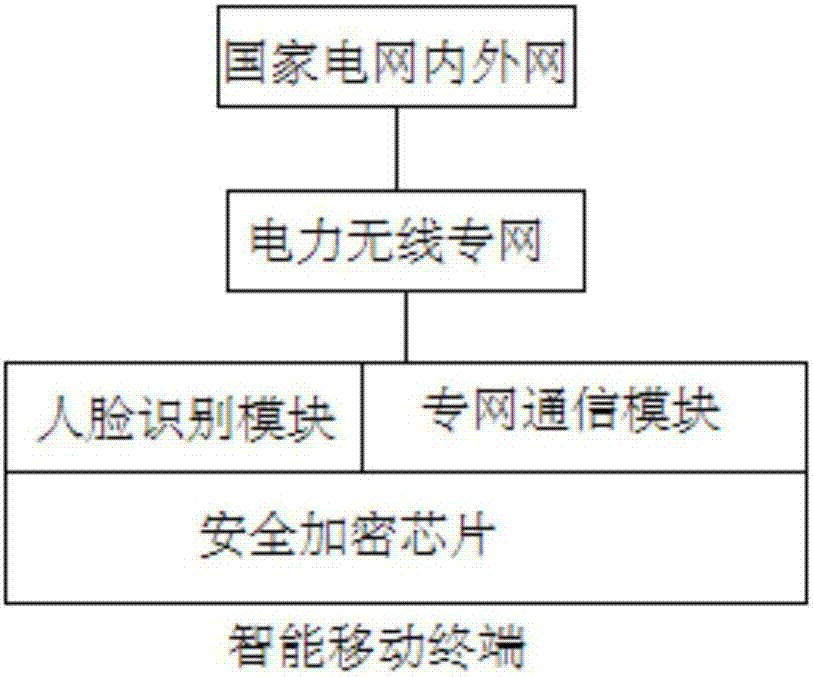
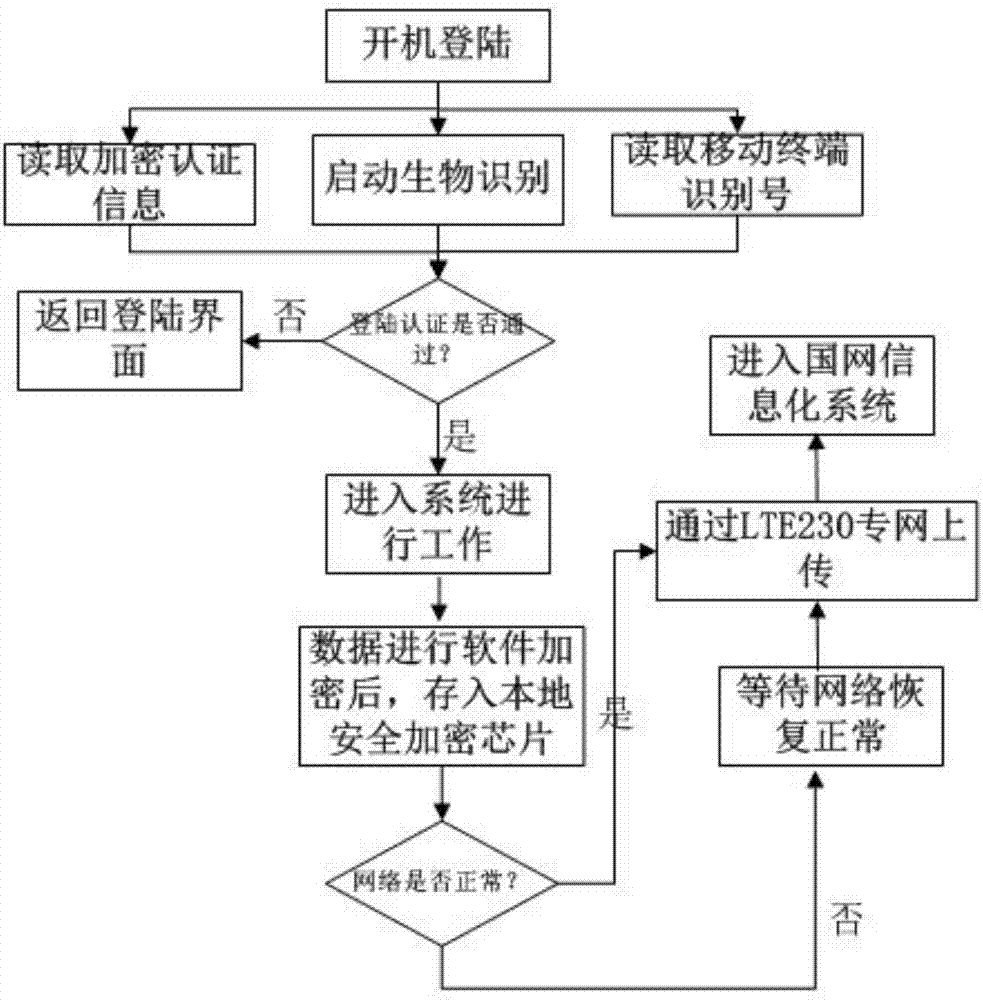
[0032] A power system mobile application information security system (see attached figure 1 ), including the internal and external network of the State Grid, the electric power wireless private network and the intelligent mobile terminal, the intelligent mobile terminal communicates with the internal and external network of the State Grid through the electric power wireless private network, and the intelligent mobile terminal includes a security encryption chip, a face recognition module and A private network communication module, the private network communication module and the face recognition module are both connected to the security encryption chip, and the private network communication module is connected to the electric power wireless private network. The electric power wireless private network is a dedicated two-way transmission network for data, voice and video. The internal and external networks of the State Grid include external network security protection devices, the...
Embodiment 2
[0046] This embodiment is basically the same as Embodiment 1, except that the voltage detection circuit is equipped with a capacitive element for detection, and the upper plate of the capacitive element is fixedly connected to the inner surface of the upper part of the smart mobile terminal. The lower plate of the element is fixedly connected to the inner surface of the lower part of the intelligent mobile terminal; the voltage detection circuit changes according to the charge of the capacitive element used for detection, and the self-pressurization circuit directly destroys the data of the security chip.
Embodiment 3
[0048] This embodiment is basically the same as Embodiment 2, except that the upper part and the lower part of the smart mobile terminal are connected by a connecting column, the lower end of the upper connecting column of the smart mobile terminal is an inclined plane, the upper end of the lower connecting column of the intelligent mobile terminal is an inclined plane, and the smart mobile terminal The upper connecting column of the mobile terminal abuts against the lower connecting column of the smart mobile terminal.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com