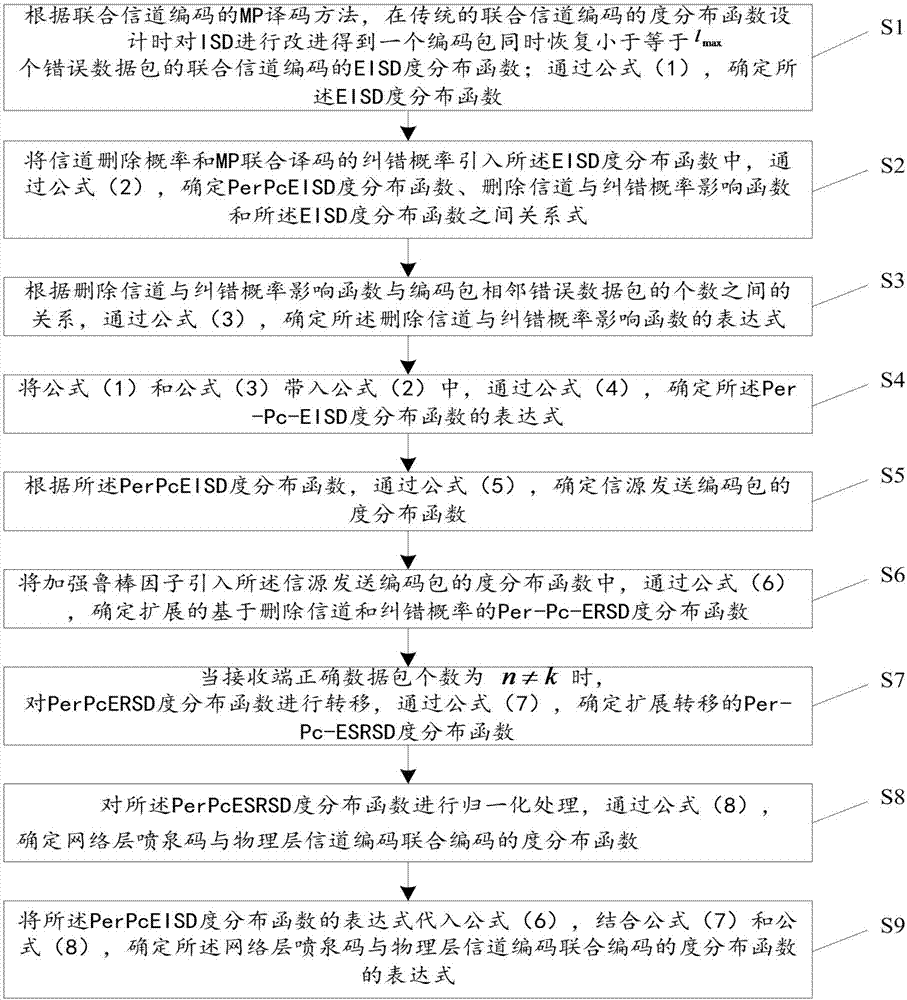
Degree distribution function design method of network layer fountain code and channel joint encoding
A technology of joint coding and design method, which is applied in the field of wireless transmission information security, and can solve problems such as inapplicability of degree distribution functions.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
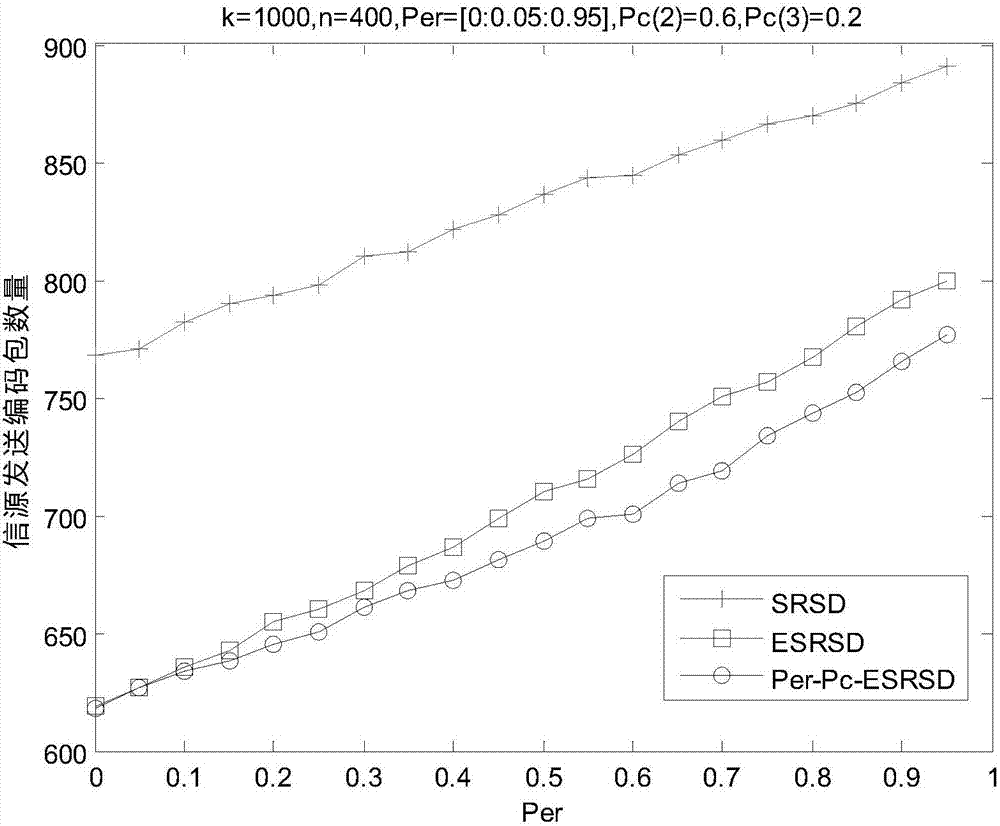
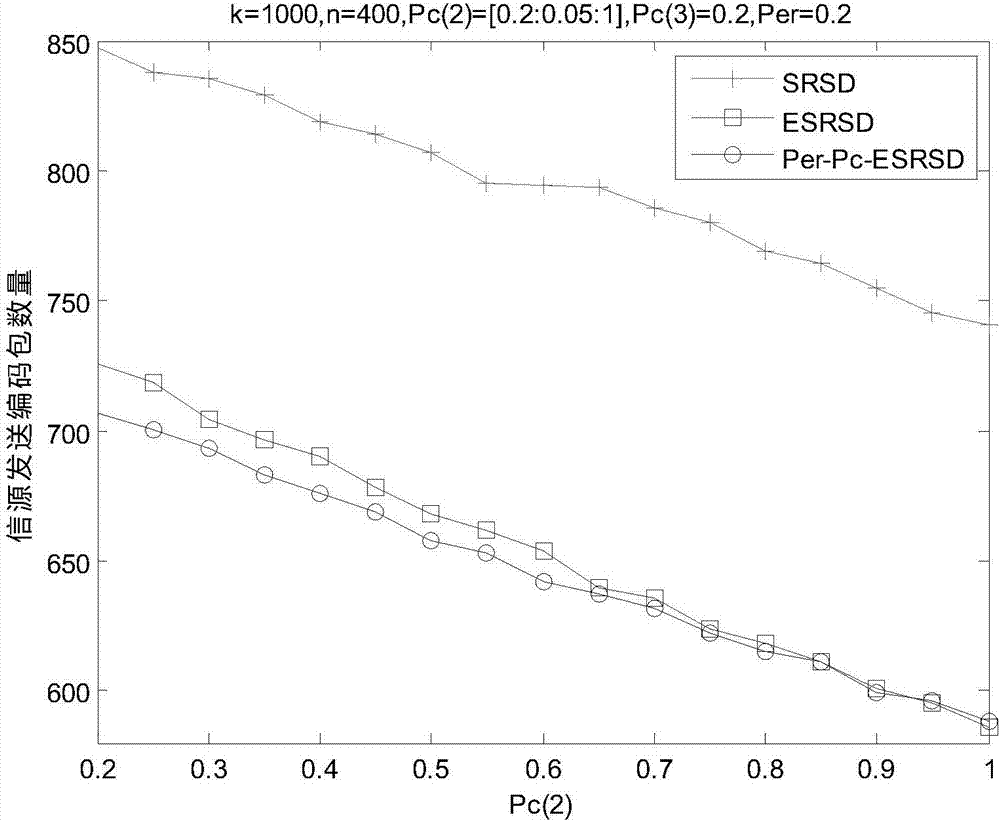
[0100] Assume that the source has sent k=1000 data packets, and is disturbed by channel noise, etc., and n=400 correct data packets are received, and the rest are all erroneous data packets. choose l max = 3, that is, 1 coded packet is adjacent to 2 error packets or 3 error packets can be adjacent with probability p c(2) or p c(3) Recover the error data packet to achieve the purpose of error correction. Parameters in the degree distribution function c=0.03, δ=0.5. Matlab is used for simulation, and the number of simulations is 2000.
[0101] The influence of channel erasure probability changes on the number of encoded packets required for decoding:
[0102] Channel deletion probability p er The change range is 0~0.95, and the step size is 0.05, and the probability p of the two error data packets adjacent to the encoded packet is restored at the same time c(2) =0.6, the probability of recovering 3 error packets p c(3) =0.2, the simulation results are as follows figure ...
Embodiment 2
[0111] Joint coding and decoding method of fountain code at network layer and channel coding at physical layer:
[0112] Assuming that the source needs to transmit k groups of data packets with verification functions, the fountain code is used to encode them at the network layer, and the fountain code at the network layer is jointly decoded with the physical layer, and l max ≤3. Its implementation method is as follows:
[0113] 1) The source sends a set of information to estimate the channel, and the channel deletion probability P is measured er and the probability P of encoding packets to recover multiple erroneous packets c(2) P c(3) .
[0114] 2) Send k groups of original data packets with error detection function to the receiving end, and the receiving end will perform error detection on the received original data packets to determine whether the data packets are correct, and count the number n of correct data packets.
[0115] 3) If n=k, then send an ACK to the sourc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com