Method for realizing security storage of mobile terminal in mobile internet based on TrustZone technology
A mobile Internet and mobile terminal technology, applied in the field of mobile terminal security storage, can solve the problems of long development cycle of software isolation technology, difficult research and development, and many defects, so as to improve reliability and security, reduce research and development difficulty, and solve the problems of software isolation technology. Effects of security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
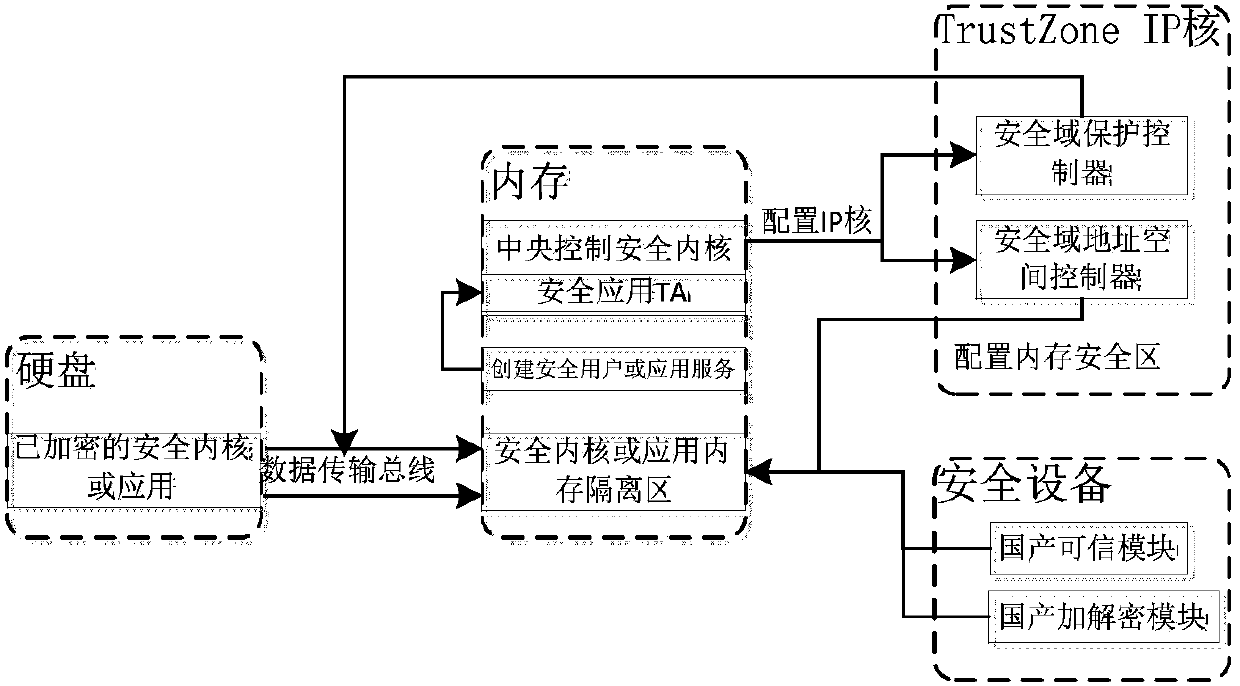
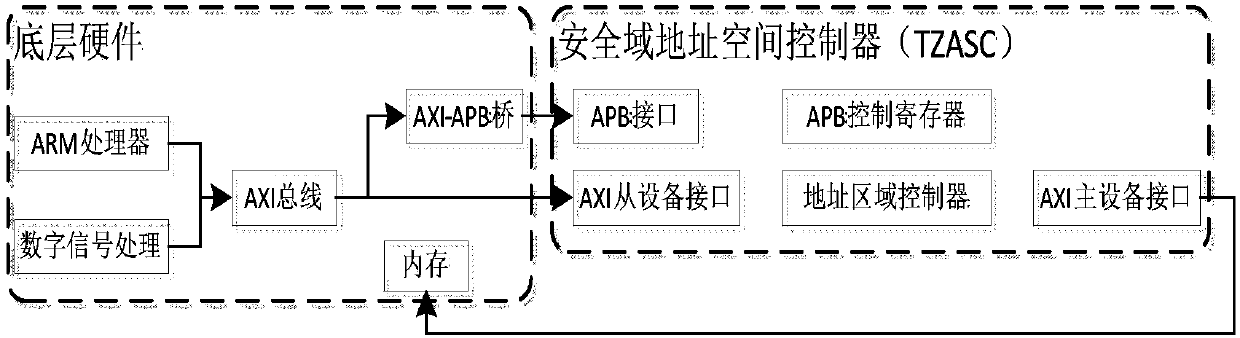
[0038] like Figure 1-2 shown.
[0039] A method for realizing secure storage of a mobile terminal under the mobile Internet based on the TrustZone technology, comprising the following steps:
[0040] 1) The normal world user invokes the application service of the security application in the normal world; after authorization verification, the session is opened, and the data and information of creating the security user / application are passed to the kernel security application;
[0041] 2) The kernel safety application applies to the central control kernel to configure the TrustZone IP core, and the state of the data transmission bus is switched to a safe state through the TrustZoneIP core; the memory is opened up in the memory according to the data and information of the safe user / application through the TrustZone IP core quarantine area;
[0042] 3) loading the encrypted kernel security application into the memory isolation area, and calling the encryption and decryption modu...
Embodiment 2
[0046] As described in embodiment 1, based on TrustZone technology to realize the method for safe storage of mobile terminals under the mobile Internet, the difference is that the encrypted kernel security application in the step 3) is set in the hard disk; the encrypted kernel security application is passed through The data transfer bus is loaded into the memory enclave.
Embodiment 3
[0048] As described in Embodiment 1, the method for implementing secure storage of a mobile terminal under the mobile Internet based on the TrustZone technology is different in that the kernel security application in step 1) runs in the security zone where the central control kernel is located. As the name implies, the security zone is a security zone physically isolated from the normal world allocated in memory by the TrustZone IP core TZASC (TrustZone Address Controller) to run and store programs or information in the security world.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com