Patents
Literature
63results about How to "Address security risks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Wide-angle projection optical system
ActiveCN104698574AAddress security risksLarge field cornerOptical elementsOptical propertyMangin mirror
The invention relates to a wide-angle projection optical system between an object side and an image side. The wide-angle projection optical system comprises a first optical system and a second optical system. The first optical system comprises a first lens unit and a second lens unit. The second optical system comprises a Mangin mirror. The first lens unit with positive effective optical power comprises an aperture diaphragm, provides the optical feature matching projection light rays of the object side and collects the light rays onto the aperture diaphragm. The second lens unit behind the first lens unit has the positive effective optical power. Relative to the first lens unit, the aperture diaphragm and the second lens unit, the Mangin mirror is closer to the image side. The first lens unit and the second lens unit form distortion real images at the front of the Mangin mirror which is provided with a penetration face and a reflection face, in this way, the light rays are subjected to the secondary refraction and the primary reflection, so that an image distortionless after zooming is generated on a screen and thinned, with aberration thereof reduced.
Owner:DELTA ELECTRONICS INC
Safe and environment-friendly initiating explosive substituent and preparation method thereof
The invention discloses a safe and environment-friendly initiating explosive substituent and a preparation method thereof. In a microstructure, the initiating explosive substituent takes fine particle high explosive as a core, takes an additive which burns at a high speed as a housing; and the initiating explosive substituent is quick in combustion and deflagration to detonation transition capability due to the special microstructure. The explosive substituent disclosed by the invention can be taken as a safe and environment-friendly initiating explosive, to replace the existing conventional explosives which are poor in safety, contains heavy metal or generates a mass of wastewater in the process of preparation, such as GTG, lead azide, DDNP (dinitrodiazophenol), lead trinitroresorcinate and BNCP. According to the invention, the problems of security risk and environment occur when the exciting initiating explosive for a detonating cap is prepared can be solved, and the normal size and the low cost of the detonating cap can be kept simultaneously.
Owner:INST OF CHEM MATERIAL CHINA ACADEMY OF ENG PHYSICS
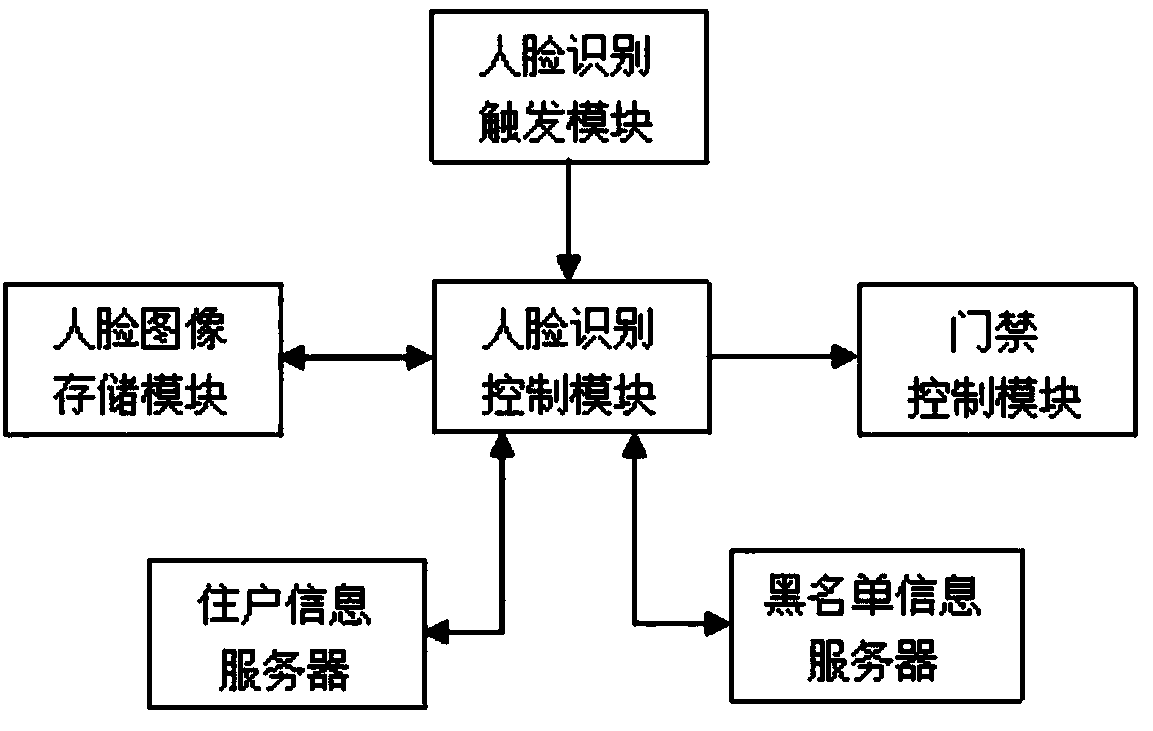
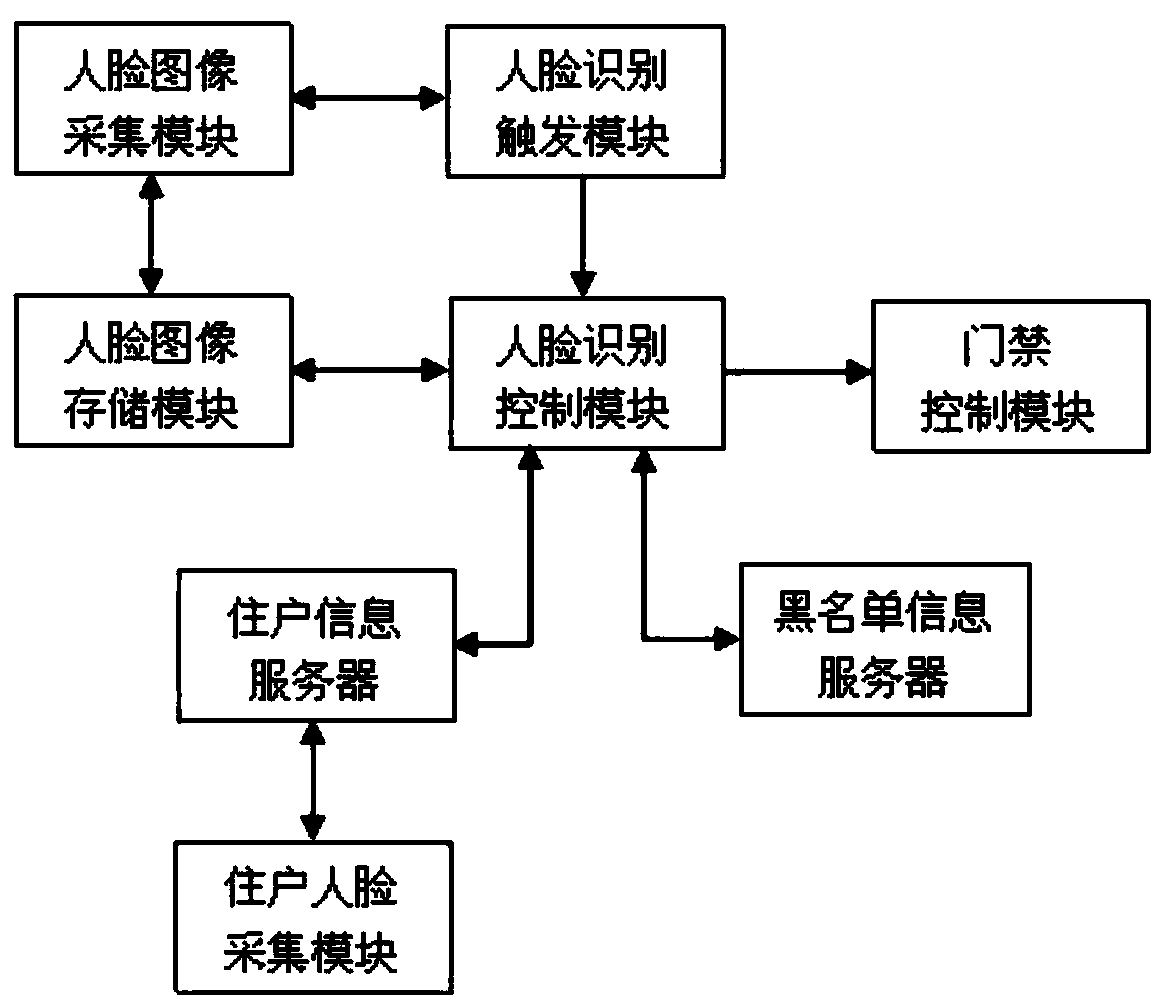
Face recognition unit entrance guard system and face recognition unit entrance guard control method
InactiveCN107730672ASolve the inconvenience of opening the access controlAddress security risksIndividual entry/exit registersPattern recognitionImage storage
The invention relates to the technical field of security, and concretely discloses a face recognition unit entrance guard system and a face recognition unit entrance guard control method. The system includes a face recognition triggering module, a face image storage module, a face recognition control module, an inhabitant information server, a blacklist information server and an entrance guard module. The face recognition triggering module starts a face recognition function, the face recognition control module compares the current face image with inhabitant face images stored in the inhabitantinformation server, outputs a door opening signal to the entrance guard control module if matching is successful, matches the current face image with blacklist face images stored in the blacklist information server, and outputs an alarm signal if the matching is successful. The system solves a problem that existing entrance guard systems are inconvenient for opening the entrance guard and have security risks, can open the entrance guard through automatic face recognition to provide convenience for inhabitants, and can automatically give an alarm when recognizing criminal offenders through theautomatic face recognition in order to guarantee the property safety of the inhabitants.
Owner:SICHUAN IDAO TECH
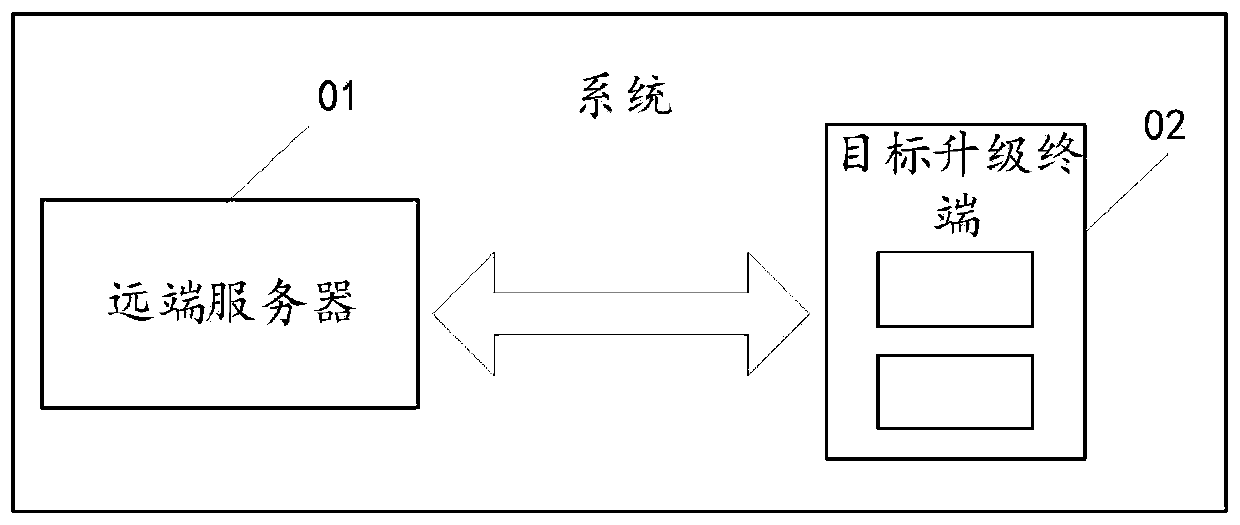
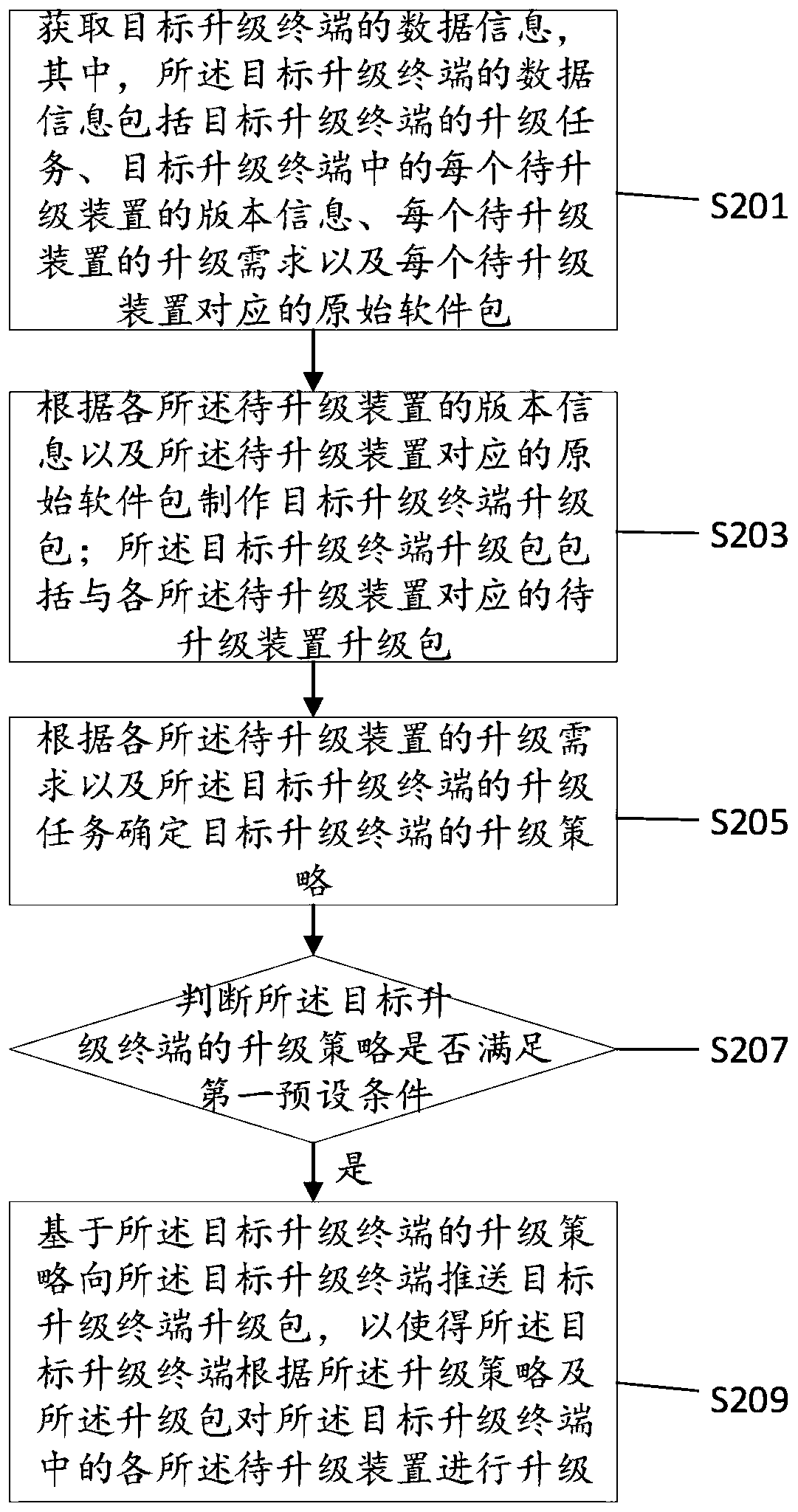
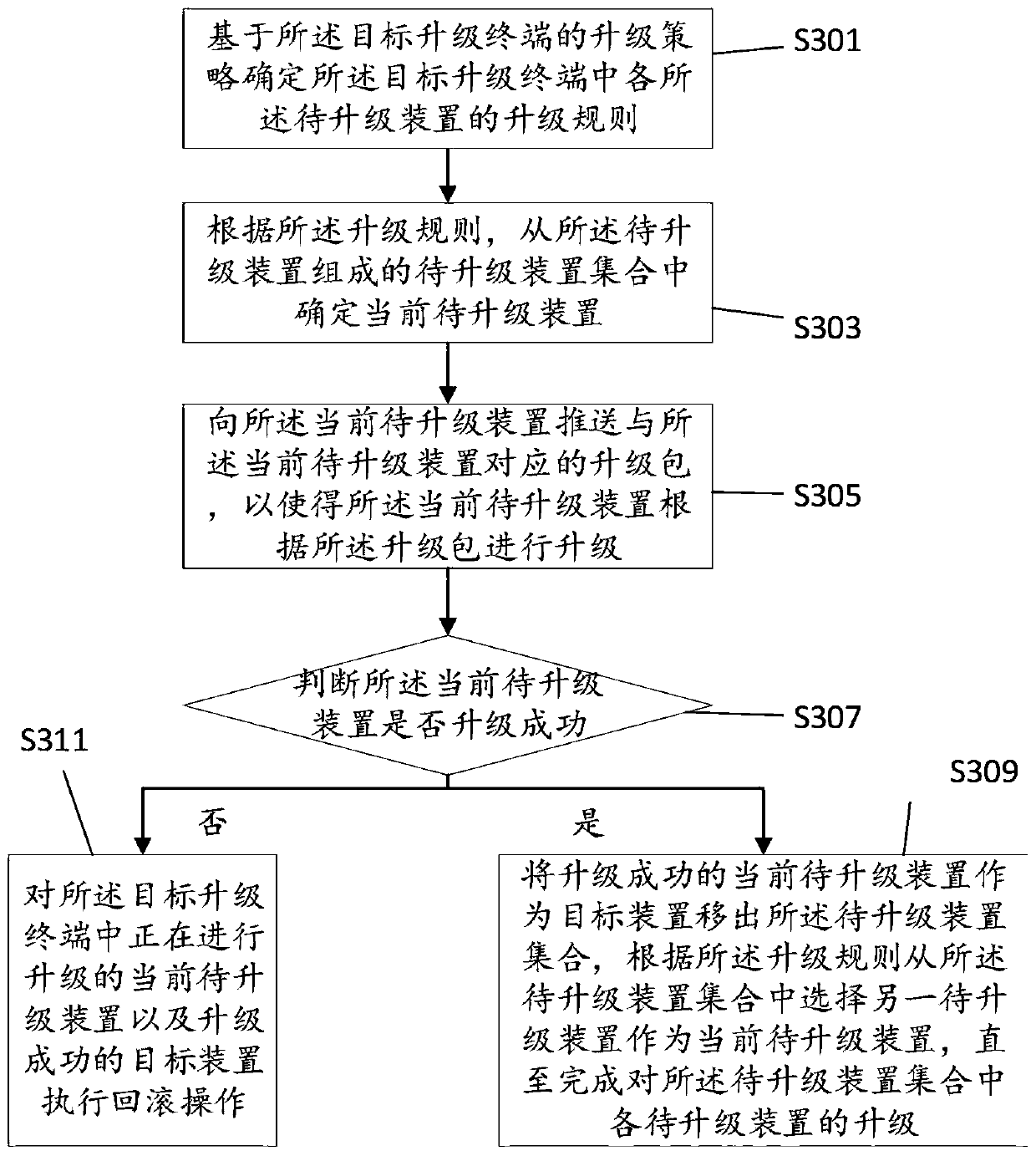
Terminal upgrading method and device, terminal and storage medium
The invention discloses a terminal upgrading method and device, a terminal and a storage medium. The method comprises: obtaining an upgrading task of a target upgrading terminal, version information of each to-be-upgraded device in the target upgrading terminal, an upgrading demand of each to-be-upgraded device and an original software package corresponding to each to-be-upgraded device; making atarget upgrading terminal upgrading package according to the version information of each to-be-upgraded device and the original software package corresponding to the to-be-upgraded device; determiningan upgrading strategy of the target upgrading terminal according to the upgrading requirement of each to-be-upgraded device and the upgrading task of the target upgrading terminal; and when the upgrading strategy of the target upgrading terminal meets a first preset condition, pushing the target upgrade terminal upgrade package to the target upgrade terminal based on the upgrade strategy of the target upgrade terminal, so that the target upgrade terminal upgrades each to-be-upgraded device in the target upgrade terminal according to the upgrade strategy and the upgrade package, and the security risk and vulnerability of the target upgrade device information can be quickly solved from the far end.
Owner:ZHEJIANG GEELY NEW ENERGY COMML VEHICLES CO LTD +3
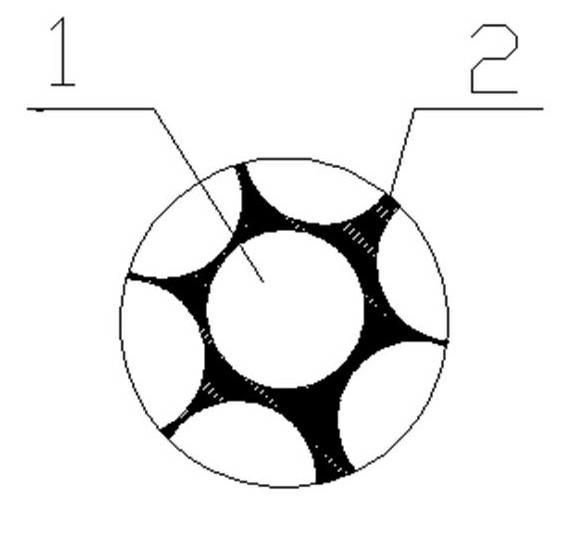
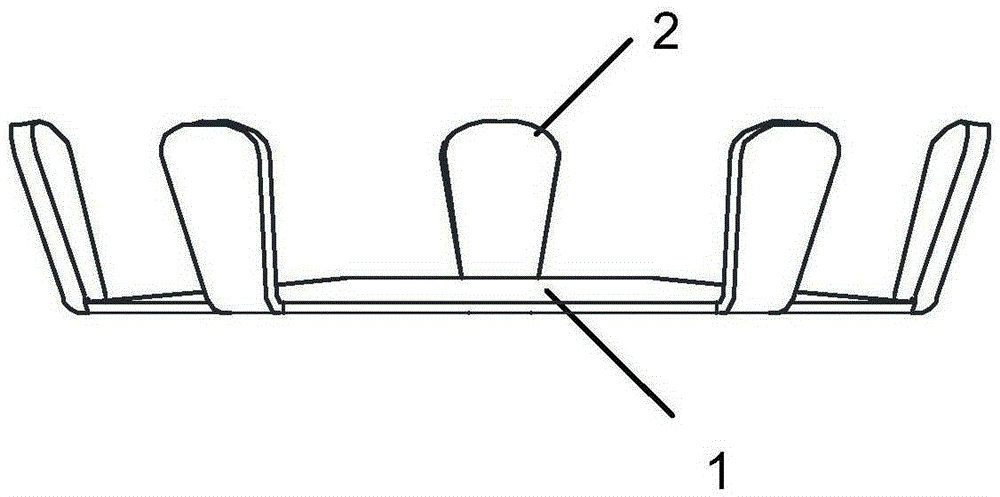
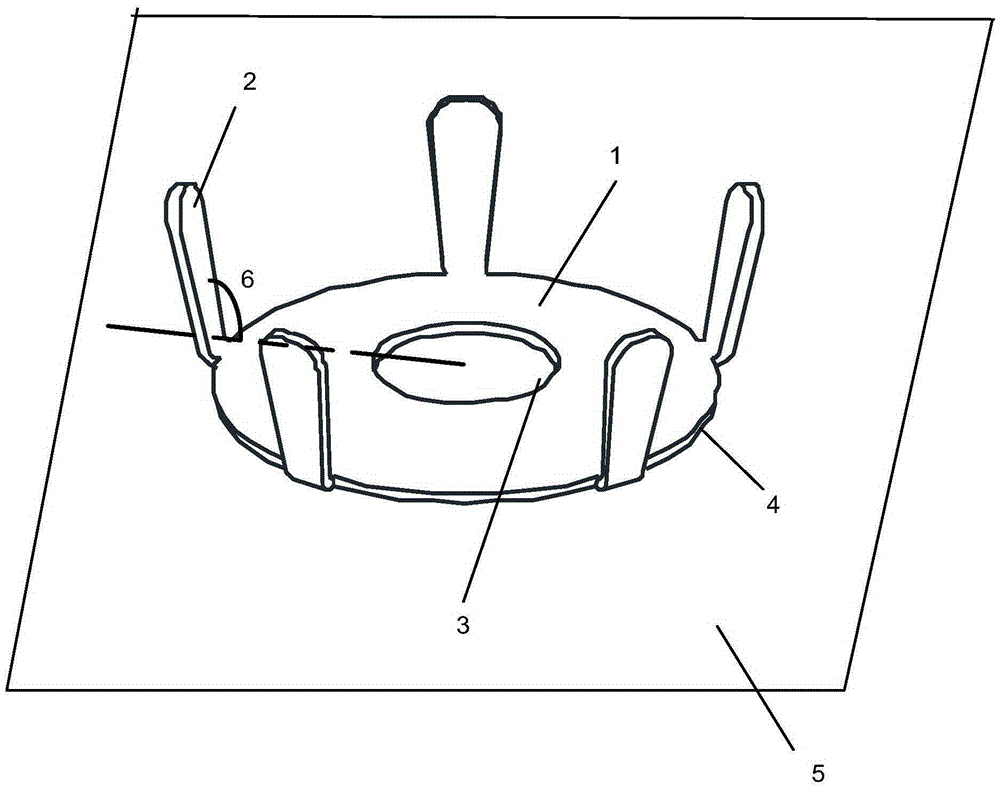
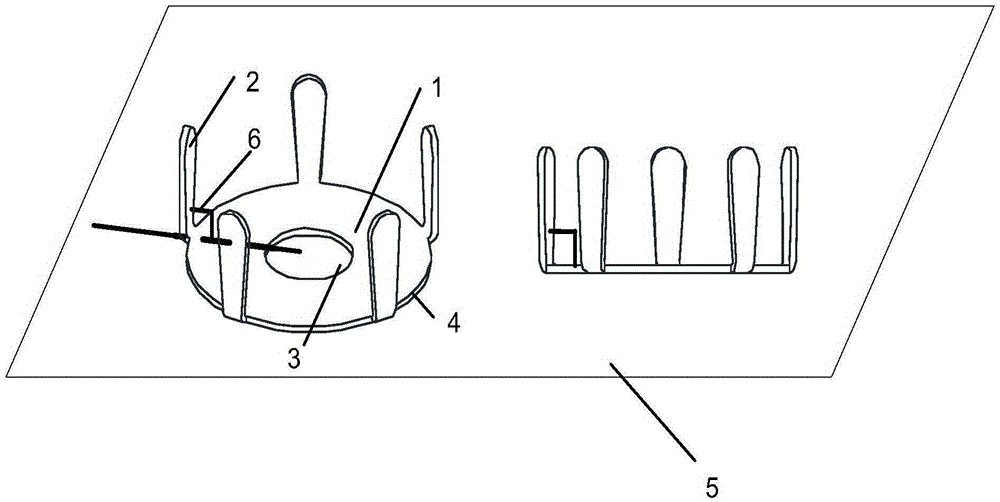
Spring washer fastener
ActiveCN105370702AShow fasteningAddress security risksWashersLoad modified fastenersConvex sideEngineering
The invention provides a spring washer fastener characterized by comprising a spring washer (1) and one or more tongue pieces (2), wherein the spring washer (1) is a sheet with an inner hole (3), one side of the spring washer (1) is a convex surface, the other side is a concave surface, the tongue pieces (2) are arranged on the outer edge of the spring washer and on the side of the convex surface, the angle formed by each tongue piece (2) and a plane (4) where the outer edge of the spring washer is located is a first angle (5), and when the convex surface of the spring washer is under pressure, the first angle (5) is in negative correlation with the pressure borne by the spring washer (1).
Owner:HUAWEI DIGITAL POWER TECH CO LTD
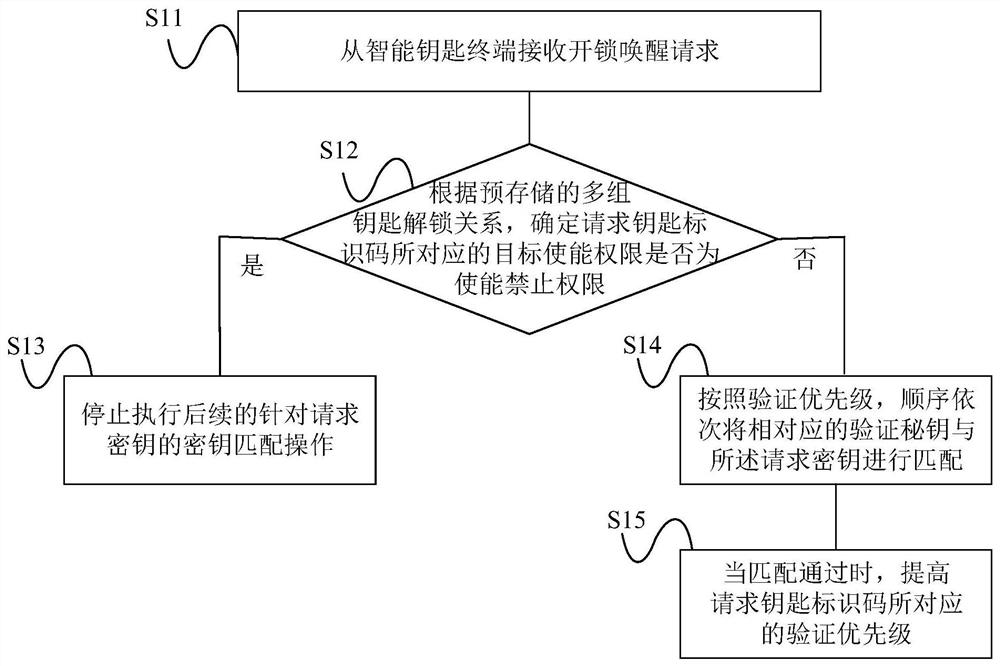
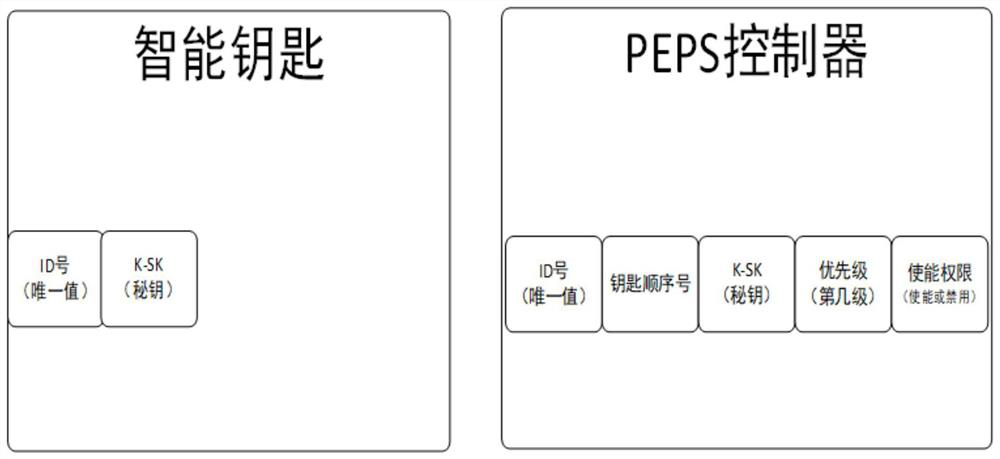
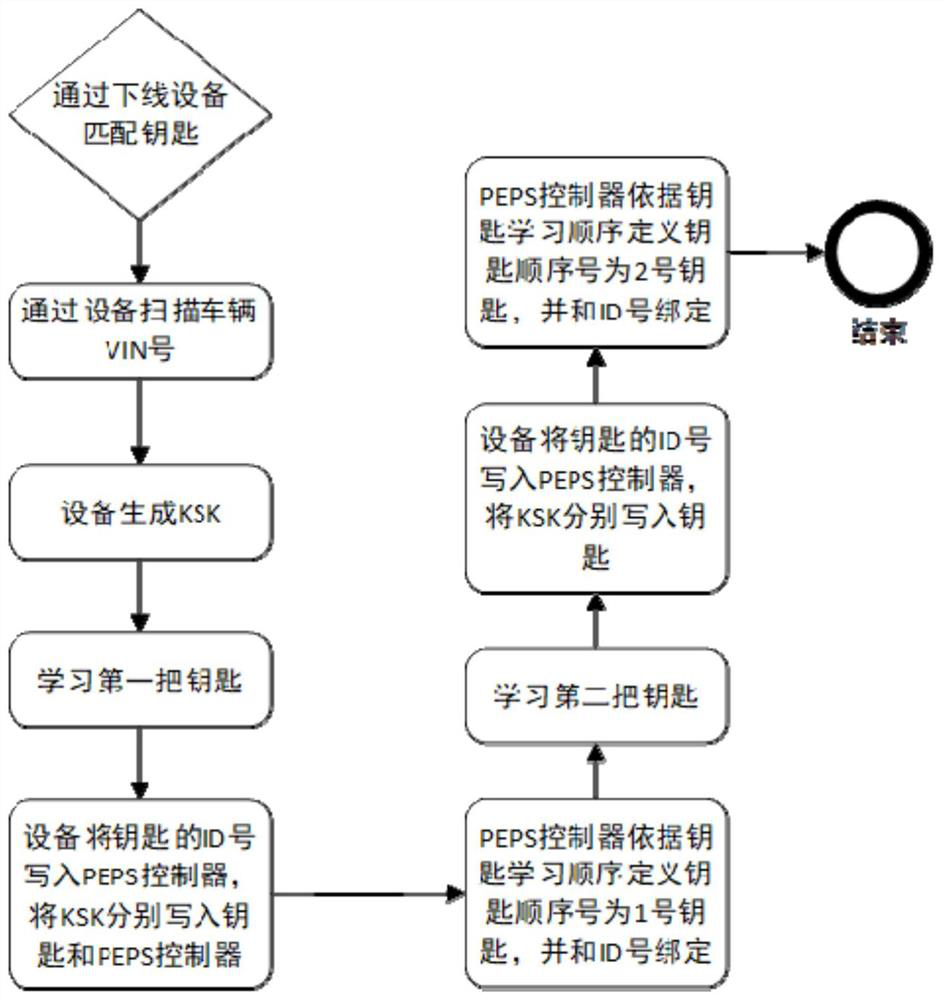
Vehicle intelligent key management method and vehicle control unit
InactiveCN111762126AAdvantages of management methodsImprove securityAnti-theft devicesKeysOperating systemVehicle control
The invention relates to the technical field of vehicle keys and provides a vehicle intelligent key management method and a vehicle control unit. The vehicle intelligent key management method comprises the steps that an unlocking awakening request is received from an intelligent key terminal, the unlocking awakening request includes a request key identification code and a request secret key, multiple sets of key unlocking relations are pre-stored in the vehicle, and each key unlocking relation includes a corresponding key identification code, a verification secret key and enabling permission;target enabling permission corresponding to the request key identification code is determined according to the pre-stored multiple groups of key unlocking relations; and when the target enabling permission indicates enabling prohibition permission, subsequent key matching operation for the request key is stopped to execute. Therefore, authority management of forgetting a standby key or illegally stealing the key is realized, an illegal person is prevented from starting the vehicle by using the keys, and safety performance of the vehicle is improved.
Owner:GREAT WALL MOTOR CO LTD
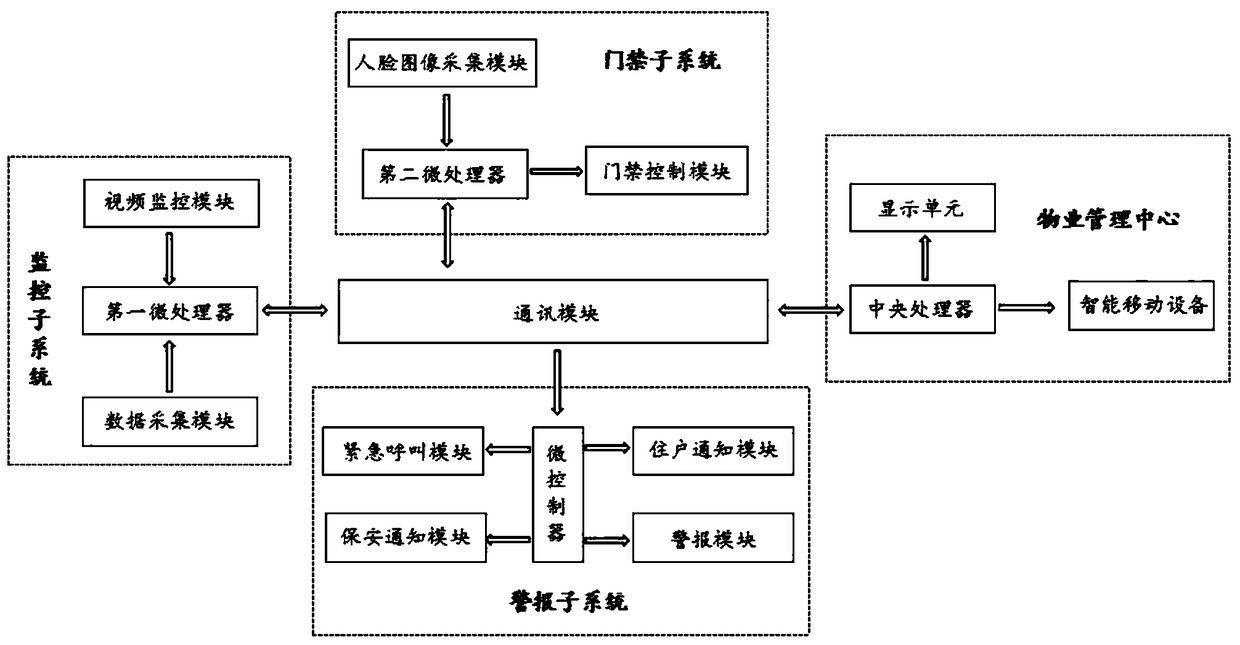
Urban community security protection system based on Internet of Things
InactiveCN108665661AEnsure safetySolve the inconvenience of opening the access controlIndividual entry/exit registersBurglar alarmInformation transmissionThe Internet
The invention discloses an urban community security protection system based on the Internet of Things. The system comprises a property management center, an access control subsystem, a monitoring subsystem, an alarm subsystem and a communication module, wherein the access control subsystem and the monitoring subsystem are both linked to the property management center through a wireless communication module, and the property management center is connected to a signal input end of the alarm subsystem through the communication module. The access control subsystem obtains a current face image, matches the current face image with stored resident face images and then opens a door, so that the problem are solved that doors of existing access control systems are inconvenient to open and there arepotential security hazards. The door is opened through automatic face recognition, so that convenience is provided for residents, and the safety of the residents is guaranteed from entering the door.Situations of a community are monitored in real time through the monitoring subsystem, image information is transmitted to the property management center, and on-duty personnel monitors real-time images of the community on a remote monitoring platform in real time, so that the effect of security protection is achieved.
Owner:ANHUI XINHUA UNIV
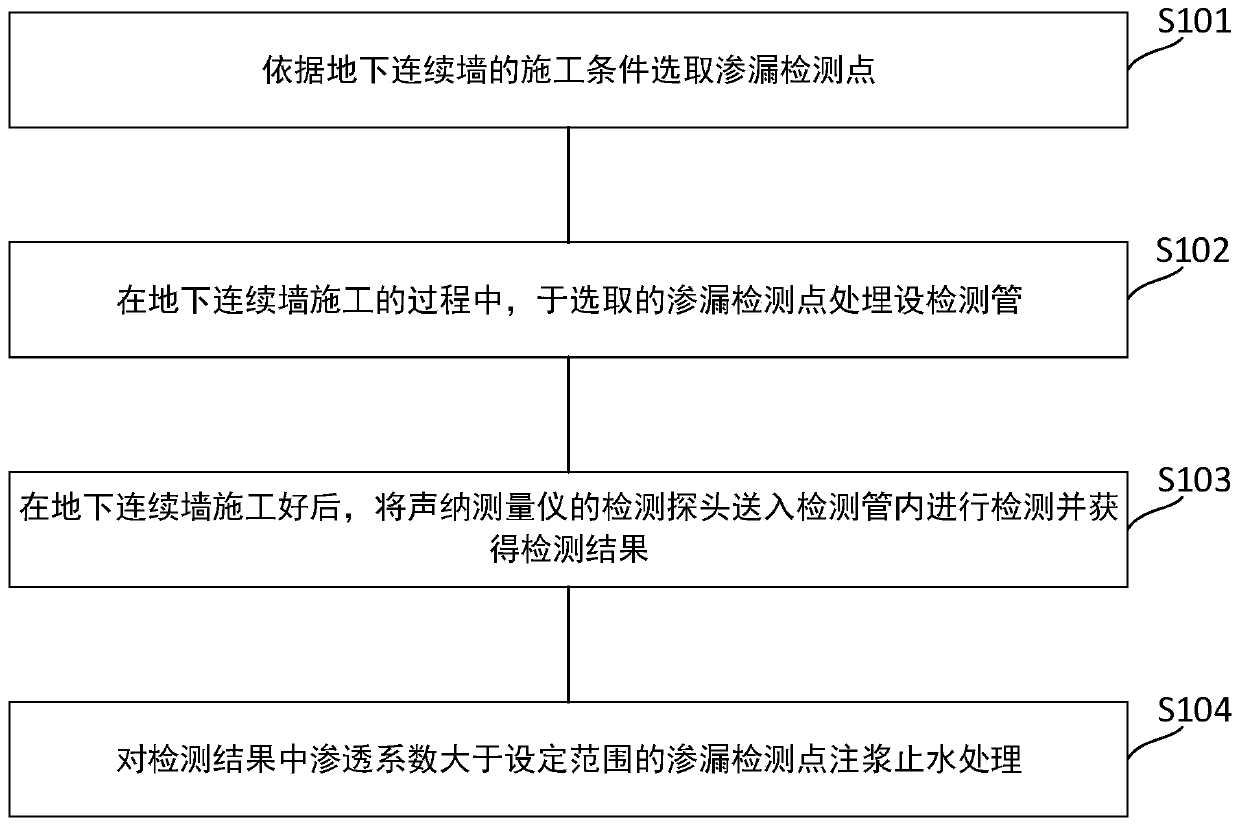
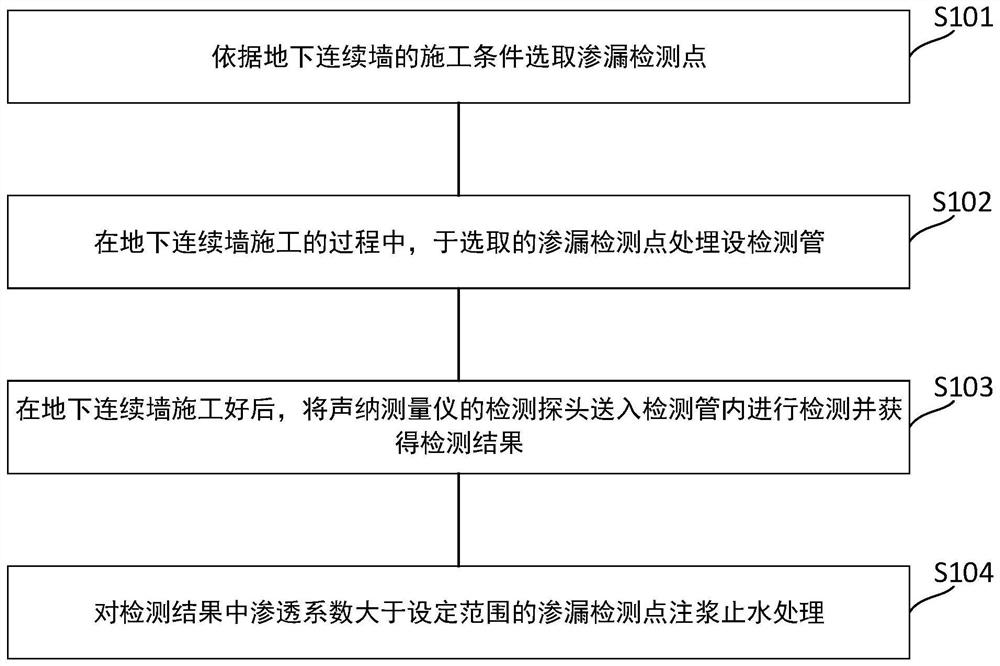
Construction method for seepage anticipation and treatment of underground continuous wall
ActiveCN110258658AAvoid the risk of water and sand gushingSolve the hidden danger of water seepageDetection of fluid at leakage pointProtective foundationSlurry wallMeasuring instrument
The invention relates to a construction method for seepage anticipation and treatment of an underground continuous wall. The construction method includes the following steps that according to the construction condition of the underground continuous wall, a seepage detection point is selected; during construction of underground continuous wall, a detection pipe is buried at the selected seepage detection point; after the construction of the underground continuous wall is finished, a detection probe of a sonar measuring instrument is sent into the detection pipe for detecting, and a detection result is obtained; and grouting water stop treatment is conducted on the leakage detection point which the seepage coefficient is larger than the set range in the detection result. According to the construction method, whether the underground continuous wall has seepage hidden danger or not is detected in advance to ensure safety of foundation pit excavation, if yes, grouting water stop treatment is conducted timely, the risk of water and sand gushing during foundation pit excavation is avoided, probability of seepage of the underground continuous wall is decreased, and construction safety of a foundation pit is improved.
Owner:CHINA CONSTR EIGHT ENG DIV CORP LTD
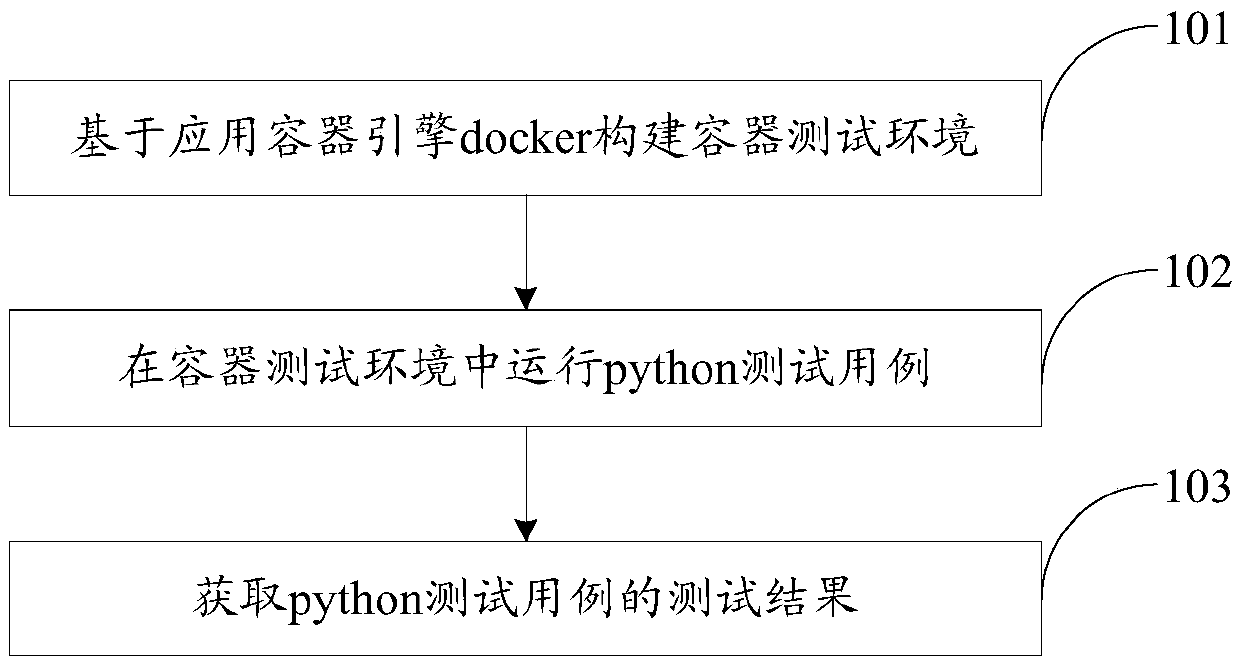
Docker-based test method and device
InactiveCN109656829AAddress open sourceAddress security risksSoftware testing/debuggingPlatform integrity maintainanceThird partyOpen source
The invention provides a docker-based test method and device, relates to the technical field of computer security, and can solve the problem of security risk caused by code open source of a third-party library. The specific technical scheme is as follows: constructing a container test environment based on an application container engine docker; Operating a python test case in the container test environment; And obtaining a test result of the python test case.
Owner:XIAN SECLOVER INFORMATION TECH CO LTD
Radio access network notification area updating method and device, terminal and base station
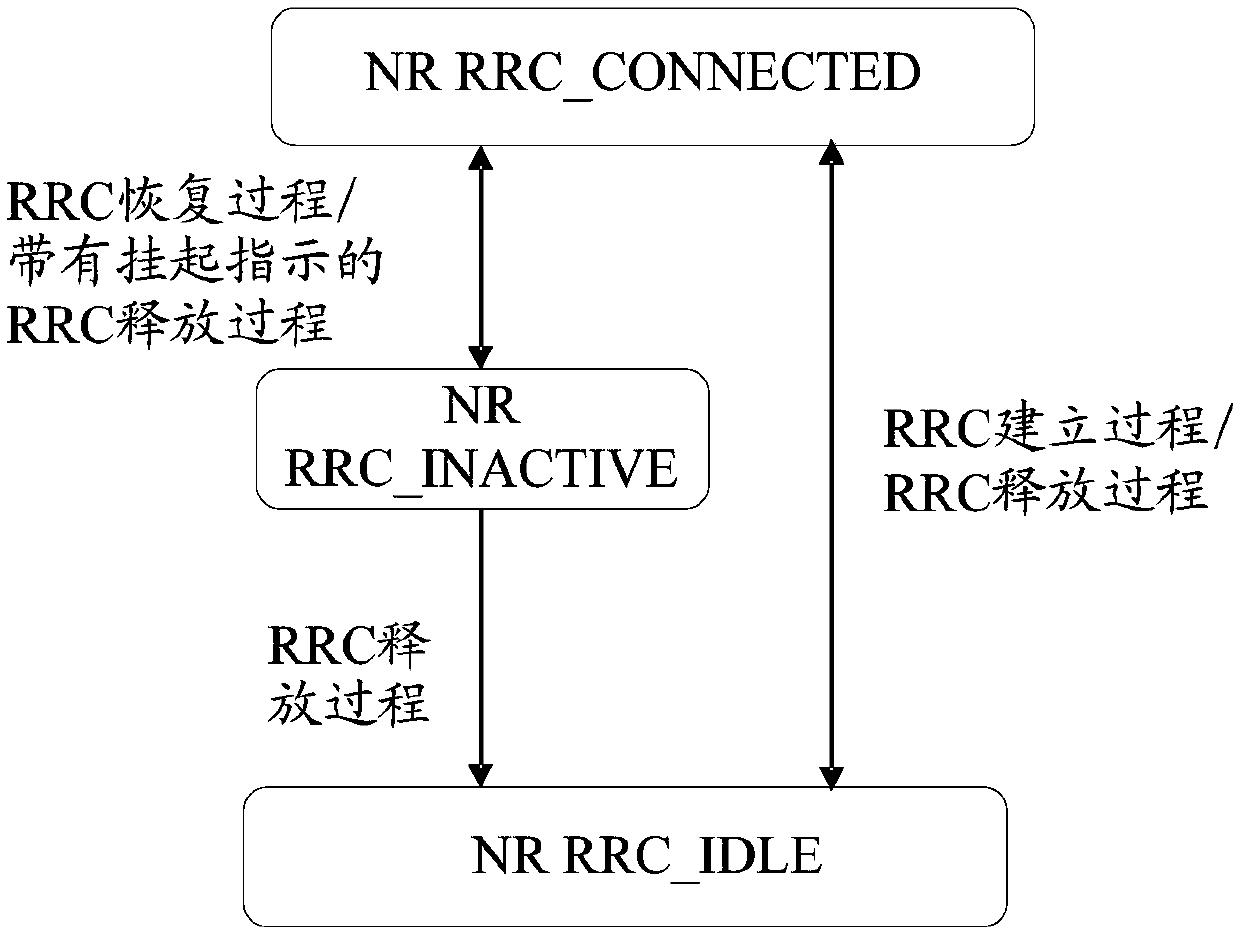
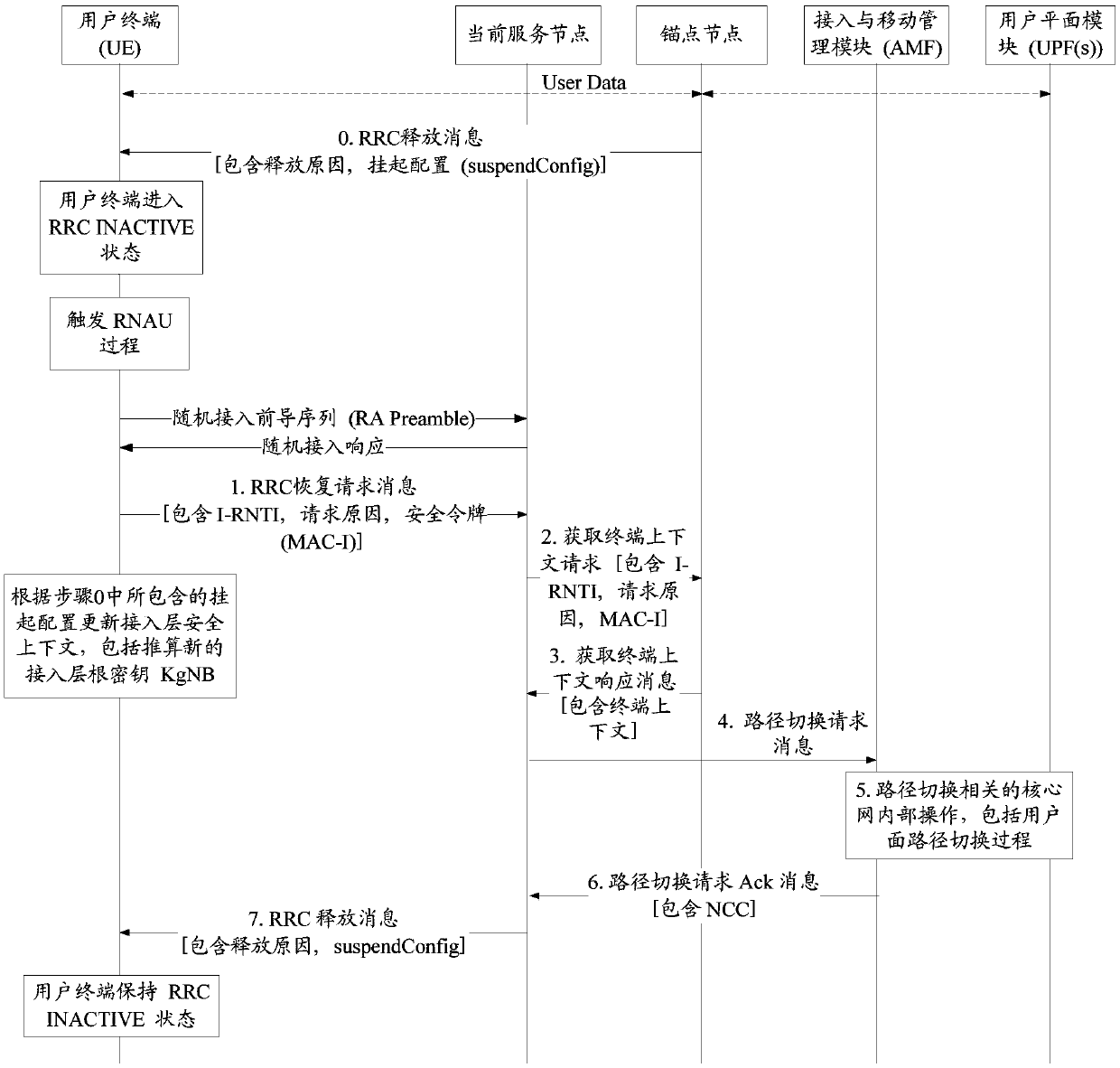
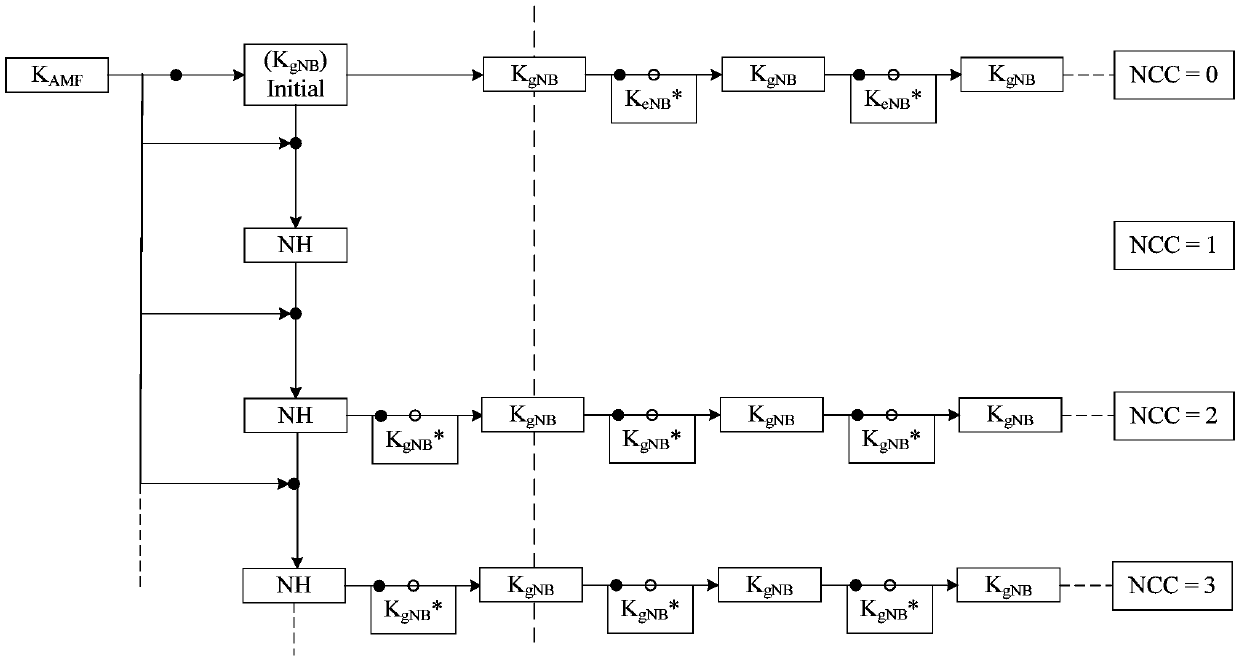
ActiveCN110636499AAddress security risksEnsure safetyConnection managementSecurity arrangementAccess networkRadio access network
The invention provides a wireless access network notification area updating method and device, a terminal and a base station. The radio access network notification area updating method comprises the following steps: when a terminal is in an RRC inactive state, sending an RRC recovery request to a base station, and if an RRC message fed back by the base station is received, comparing whether a first NCC value and a second NCC value are the same or not; if the first NCC value is the same as the second NCC value, deleting an access layer root key generated according to the first NCC value and other keys and security tokens generated by using the root key, and recovering a security context held before sending the RRC recovery request message to the base station; wherein the first NCC value isan NCC value in a first RRC release message received most recently before the RRC recovery request message is sent to the base station, the second NCC value is an NCC value in an RRC message fed backby the base station, and the RRC message comprises an RRC recovery message or an RRC release message. According to the scheme, the problem that in the prior art, safety risks exist in the RNAU processwithout executing anchor point transfer is solved.
Owner:DATANG MOBILE COMM EQUIP CO LTD
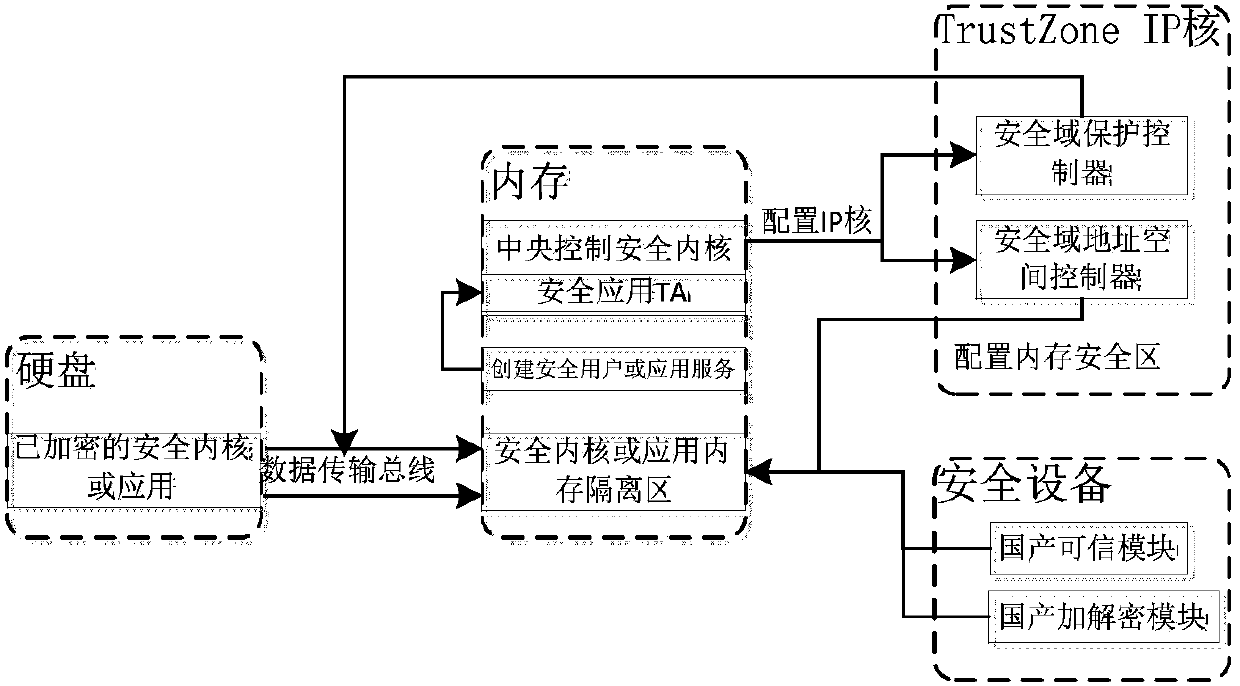
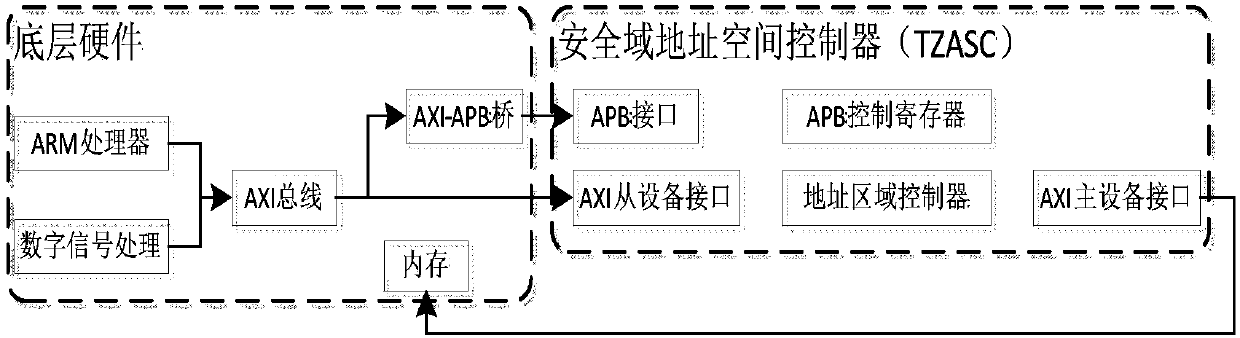
Method for realizing security storage of mobile terminal in mobile internet based on TrustZone technology
InactiveCN107609412AImprove security and reliabilityAddress security risksDigital data protectionInternal/peripheral component protectionTrusted applicationSecurity kernel
The invention relates to a method for realizing security storage of a mobile terminal in a mobile internet based on a TrustZone technology. Private applications and data in the mobile terminal are loaded to a hardware isolation security region of the mobile terminal, and an access request of a non security region is refused, so that information security is ensured. The core is to self-develop a TrustZone IP kernel driver and a trusted application; a security kernel of a security world is accessed through a client of an ordinary world of the trusted application; the corresponding trusted application is started; a specific memory region is subjected to hardware isolation through the IP kernel driver; data and codes encrypted through a homemade encryption / decryption module and stored in an external storage device are loaded to an isolation region of a memory; and the encrypted data and codes are decoded by calling a TCM chip after being loaded, so that dynamic storage security of information is guaranteed finally.
Owner:SHANDONG UNIV
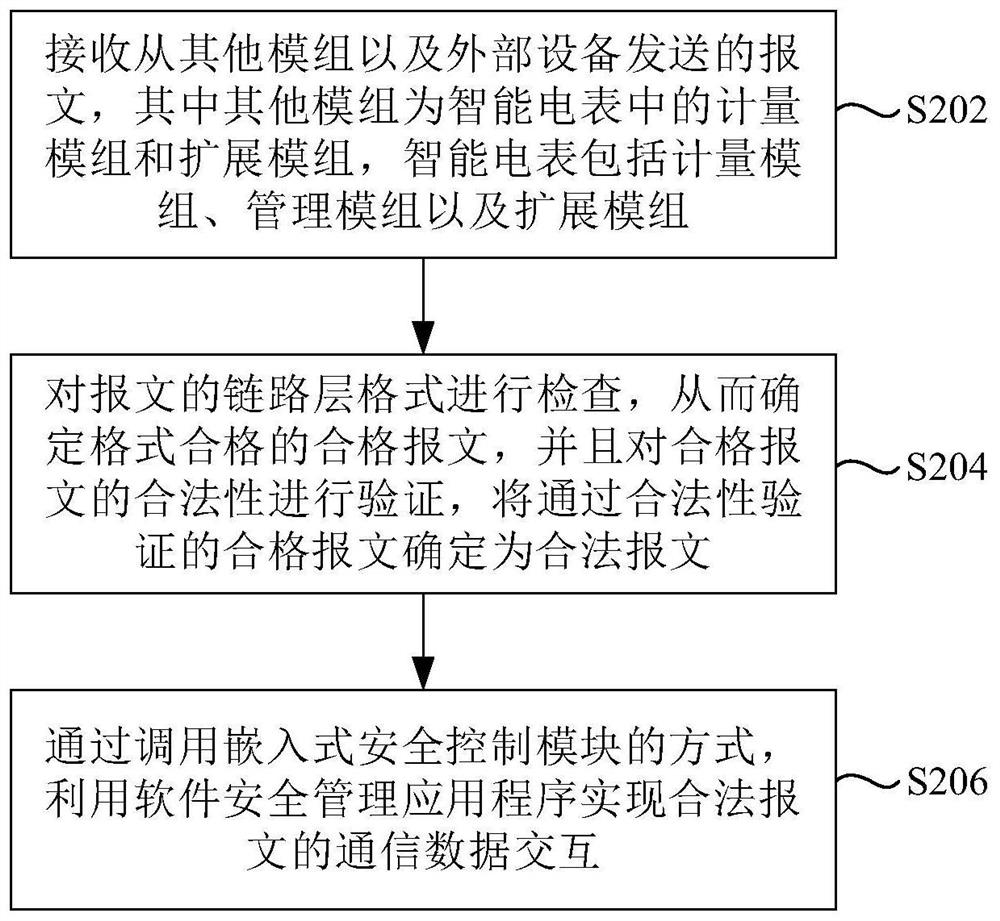
Method and device for managing communication security of intelligent electric meter
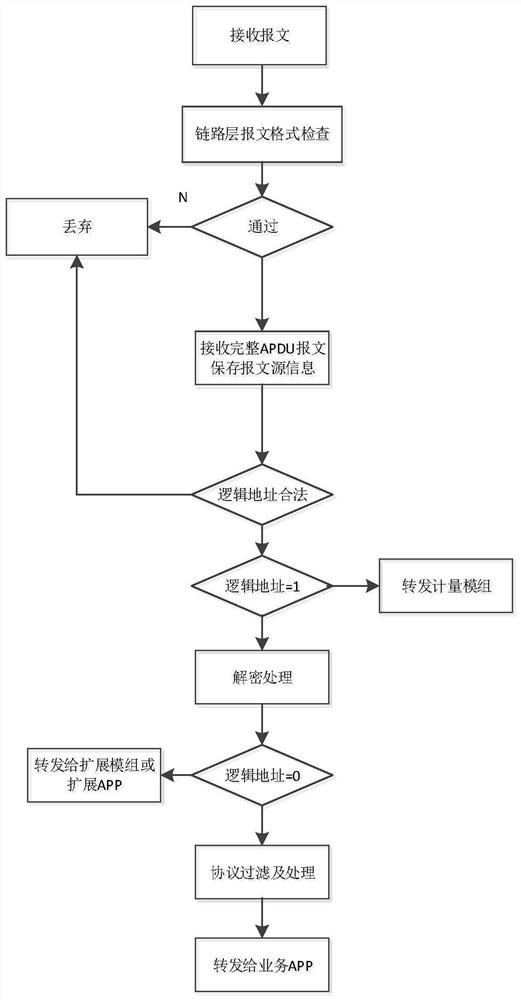
ActiveCN112217795AImplement filteringRealize communication data interactionTransmissionInformation technology support systemCommunications securityEmbedded security
The invention discloses a method and device for managing communication security of an intelligent electric meter. The method comprises steps that messages sent by other modules and external equipmentare received, the other modules are a metering module and an extension module in the intelligent electric meter, and the intelligent electric meter comprises a metering module, a management module andan extension module; the link layer format of the message is checked so as to determine a qualified message with a qualified format, legality of the qualified message is verified, and the qualified message passing the legality verification is determined as a legal message; and communication data interaction of legal messages is realized by utilizing a software security management application program in a manner of calling the embedded security control module.
Owner:STATE GRID CORP OF CHINA +1
Border gateway routing updating method based on block chain
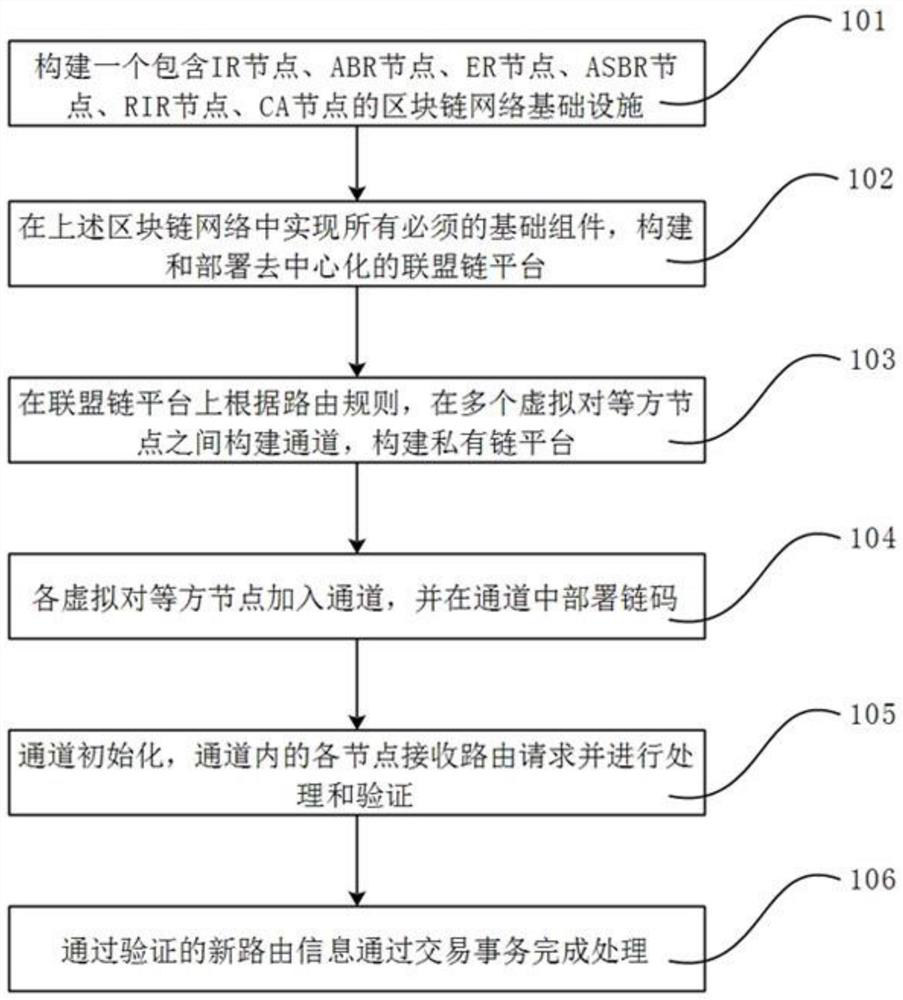
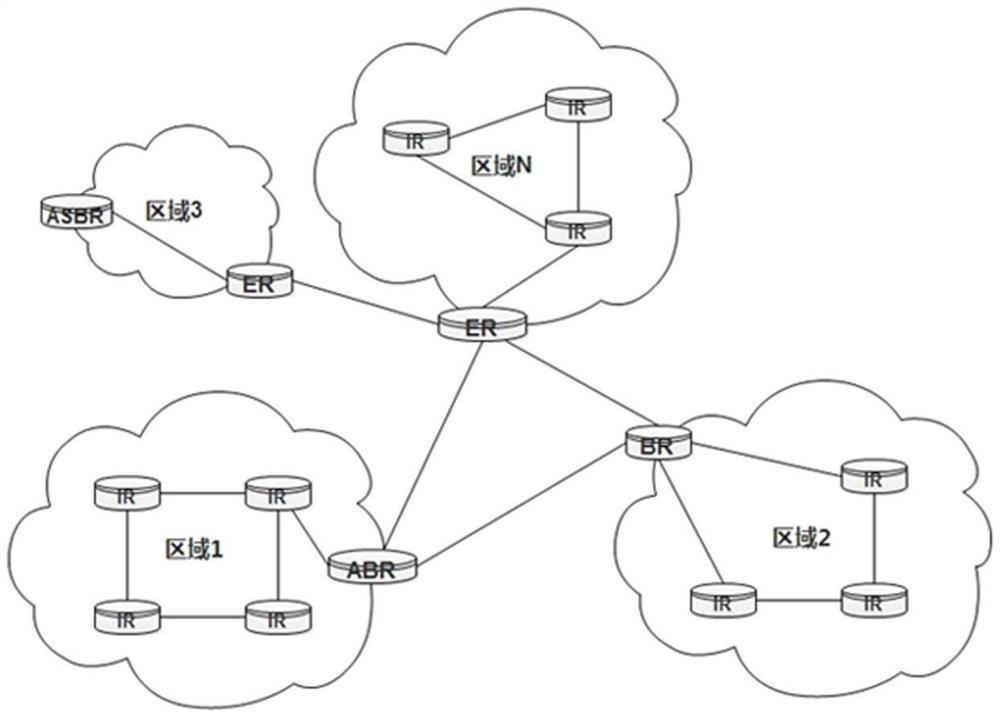
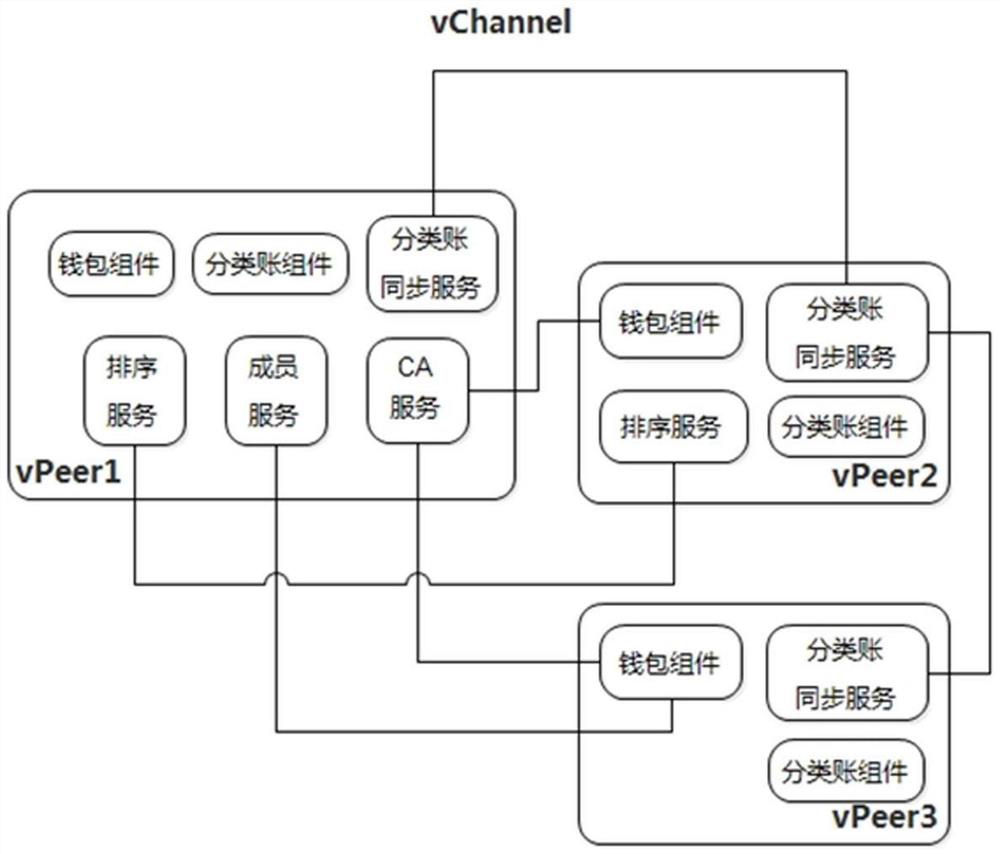
ActiveCN113726665AReduce security risksNo attenuation and lossUser identity/authority verificationData switching networksChain networkBlockchain
The invention discloses a border gateway routing updating method based on a block chain. The method comprises the following steps: constructing a block chain network infrastructure comprising an IR node, an ABR node, an ER node, an ASBR node, an RIR node and a CA node; realizing a basic component in a block chain network infrastructure, and constructing and deploying a decentralized alliance chain platform; constructing channels among the plurality of virtual peer nodes on the alliance chain platform according to a routing rule, and constructing a private chain platform; adding each virtual peer node into a channel and deploying a chain code in the channel; initializing a channel, wherein each node in the channel receives the routing request and performs routing verification; and forwarding the new routing information passing the routing verification and submitting a transaction to a channel. According to the method, the decentralized invariant database based on the consensus of the participating autonomous system (AS) is created to construct the block chain, and verification is performed according to the content of the block chain distributed database when the update of each border gateway route is received, so that the security risk is reduced.
Owner:四川启睿克科技有限公司
Pipeline connector device
InactiveCN106931255ASolve problems that present greater security risksAddress security risksSleeve/socket jointsNon-disconnectible pipe-jointsMechanical engineeringEngineering
The invention provides a pipeline connector device. The pipeline connector device comprises a pair of fixing slips. The pair of fixing slips is composed of multiple slips plates which are sequentially spliced in the circumferential direction of the fixing slips. Each slips plate is wrapped around a first pipe body and a second pipe body to be connected. At least one slips plate is provided with a first locating piece used for being inserted into a first locating hole of the first pipe body for locating. At least one slips plate is provided with a second locating piece used for being inserted into a second locating hole of the second pipe body for locating. The pipeline connector device solves the problem that in the prior art, large safety risk exists when a hot work joint manner is adopted.
Owner:PETROCHINA CO LTD
Cable crane main cable dismantling construction method
ActiveCN110065888AAddress security risksAddress safety risks of working at heightsCable carsLoad-engaging elementsCross channelEngineering
The invention discloses a cable crane main cable dismantling construction method. The cable crane main cable dismantling construction method comprises the steps of laying a main cable ground channel,relaxing a main cable for the first time, dropping the main cable for the second time, dropping the main cable on the main cable ground channel, feeding the main cable to a main cable reel to be recovered, and dismantling the main cable ground channel. As for laying of the main cable ground channel, the steps include that carrier roller devices and guiding ground anchors are arranged on the groundbelow the cable crane main cable; and the carrier roller devices are arranged on the ground along a main cable recovery moving route at intervals, and the guiding ground anchors are arranged on all turning positions of the main cable during ground recovering and moving. According to the construction method, an air main cable crossing channel is optimized to form a ground channel on a dam surfaceof a hydropower station dam, auxiliary facilities such as carrier roller sets and the guiding ground anchors are adopted on the dam surface to arrange the main cable ground channel, temporary bearingcable erection and dismantling and temporary bearing code installation and dismantling are omitted, main cable demolition high-altitude work is optimized into ground work, and the main cable high-altitude work safety risks are completely solved.
Owner:SINOHYDRO BUREAU 7 CO LTD
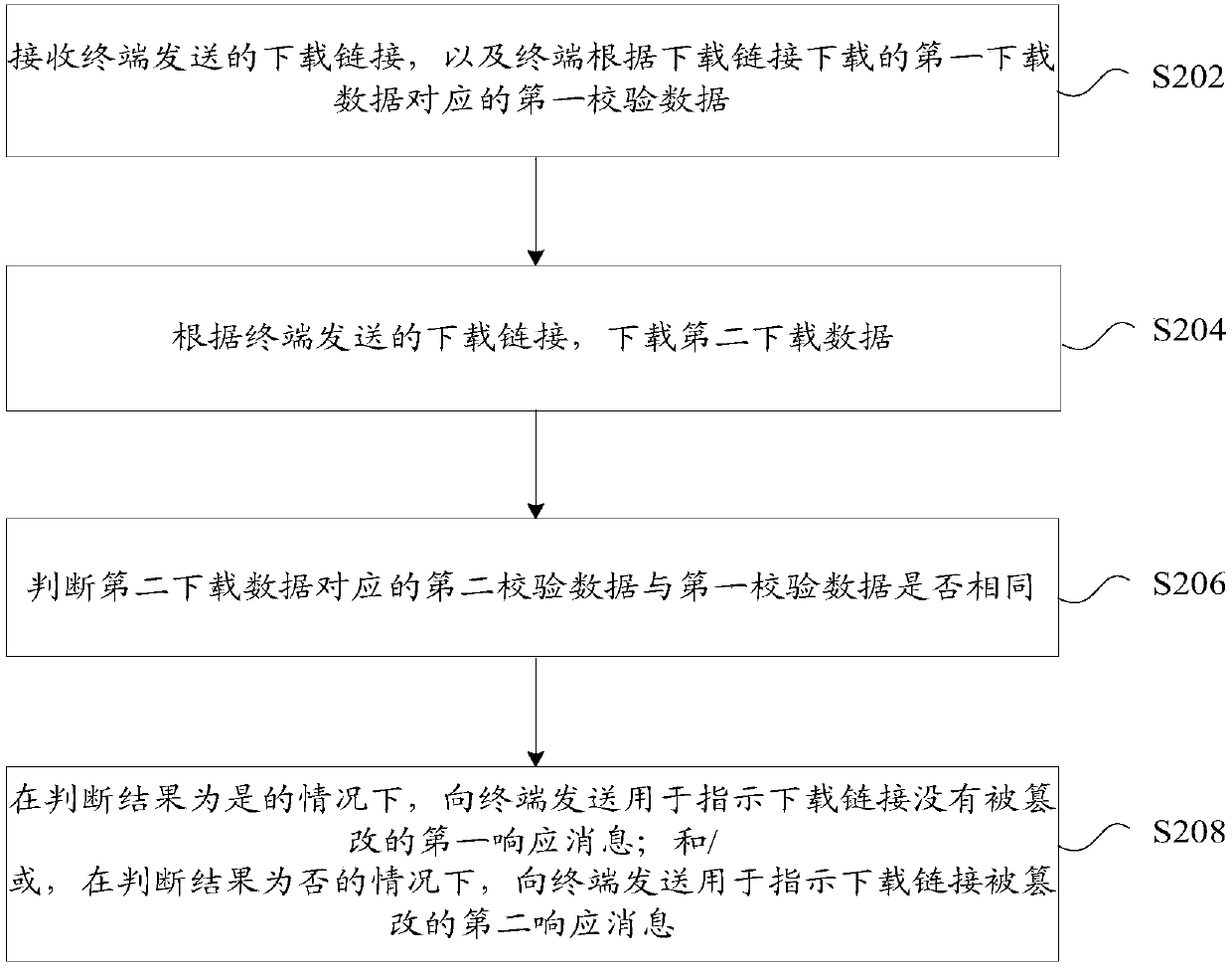
Data processing method and device, server, and terminal
InactiveCN107770213AAddress security risksEnsure safetyTransmissionComputer terminalReal-time computing
The invention provides a data processing method and device, a server, and a terminal. The method comprises the steps: receiving a downloading link transmitted by the terminal and first verification data corresponding to first downloading data downloaded by the terminal according to the downloading link; downloading second downloading data according to the downloading link transmitted by the terminal; judging whether second verification data corresponding to the second downloading data is the same as the first verification data or not; transmitting a first response message which is used for indicating that the downloading link is not tampered to the terminal under the condition that the judgment result is that the second verification data corresponding to the second downloading data is thesame as the first verification data; and / or transmitting a second response message which is used for indicating that the downloading link is tampered to the terminal under the condition that the judgment result is that the second verification data corresponding to the second downloading data is not the same as the first verification data. According to the invention, the method solves a problem inrelated technologies that the tampering of the downloading link causes the safety risks of the terminal, and achieves an effect of guaranteeing the data safety of the terminal.
Owner:ZTE CORP
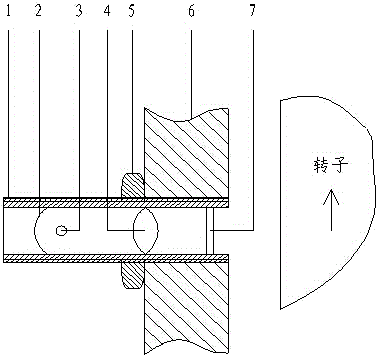
Online motor rotor temperature measuring probe
ActiveCN104390727AAccurate measurementImprove securityTemperature measurement of moving solidsHeat lossesLight filter
The invention discloses an online motor rotor temperature measuring probe which comprises a reflector, an infrared light source, a focusing mirror, a receiving element, a light filter and a heat insulation sleeve. The probe is integrally protected by the heat insulation sleeve, screwed on a shell or an end cover and different from a common infrared temperature measuring probe, the probe effectively overcomes the shortcomings of unstable reflection and polarized light of a rotor surface caused by rotation by the aid of the light filter, a measuring element is mounted in the heat insulation protection sleeve, heat shock of heat conduction on a photoelectric element is relieved, and mechanical shock of body vibration on the elements is decreased when a motor runs. The probe has the advantages that the probe is accurate in measurement and fine in safety, the effect on the structure of the motor is low and the like, the probe can be conveniently and rapidly mounted on the end cover of the motor, the temperature of the end face of the rotating rotor is continuously measured in real time, and the probe effectively solves the problems that heat loss and safety risks caused by a window formed in the end cover in the past, temperature measuring test paper is pasted on the surface of a rotor, the highest temperature can only be inspected in a split manner, and the temperature change process cannot be reflected.
Owner:CSR ZHUZHOU ELECTRIC CO LTD
Composite profile made from waste dry film and preparation method thereof
The invention provides a composite profile made from a waste dry film and a preparation method thereof. The composite profile comprises, by weight, 25-35 parts of dry film fines, 35-45 parts of wastecircuit board resin powder, 5-20 parts of polyethylene plastic and / or dry wood powder, 5-10 parts of waste glass fiber reinforced plastic, and 10-15 parts of an auxiliary agent, wherein the dry film fines is obtained from alkali treatment on a waste dry film and contains no more than 3% by mass of colloid. Through resource utilization of the waste dry film, waste circuit board resin powder and waste glass fiber reinforced plastic, a composite profile with excellent mechanical properties is obtained. The composite profile has significant economic and social benefit.
Owner:常州厚德再生资源科技有限公司
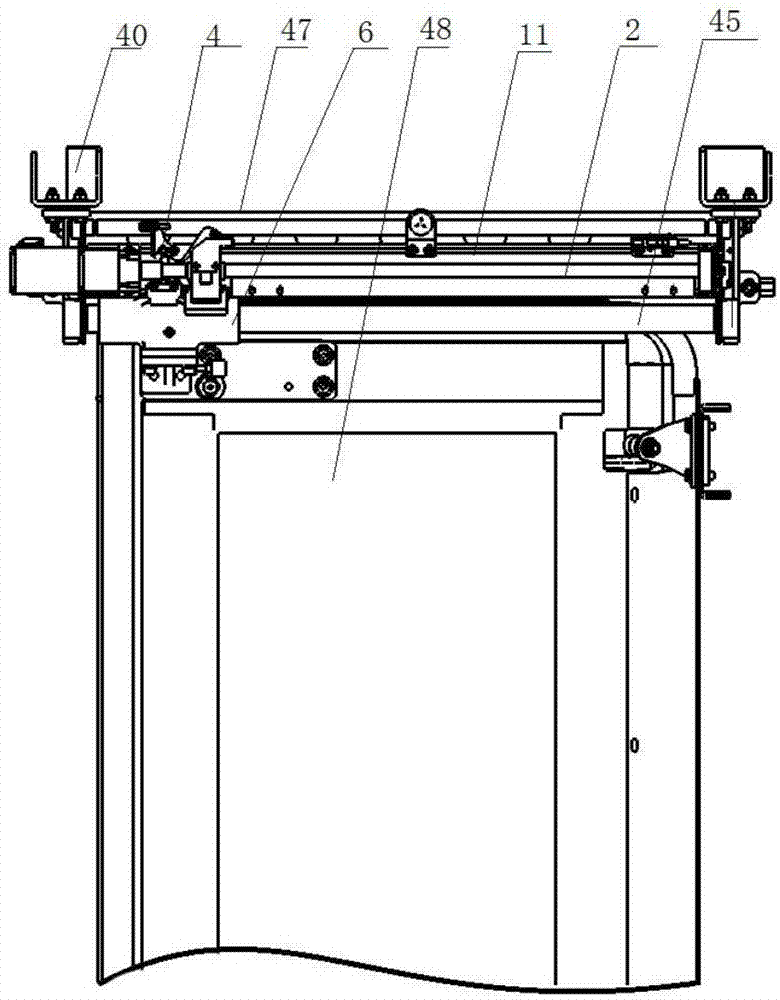
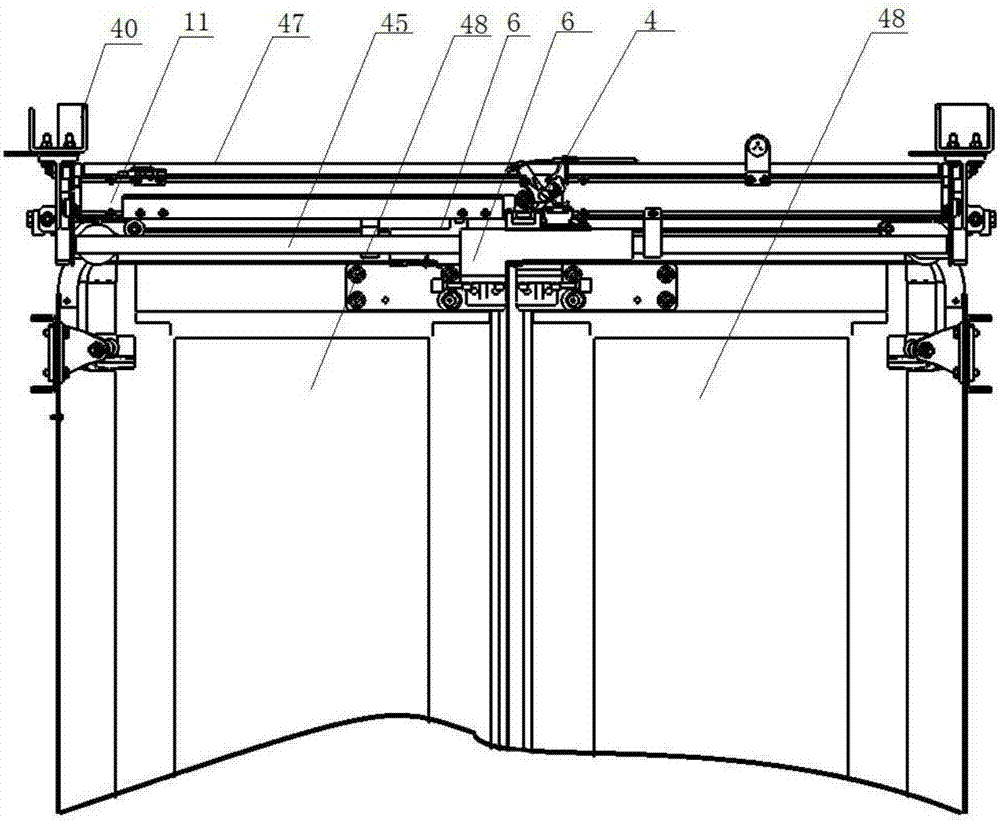
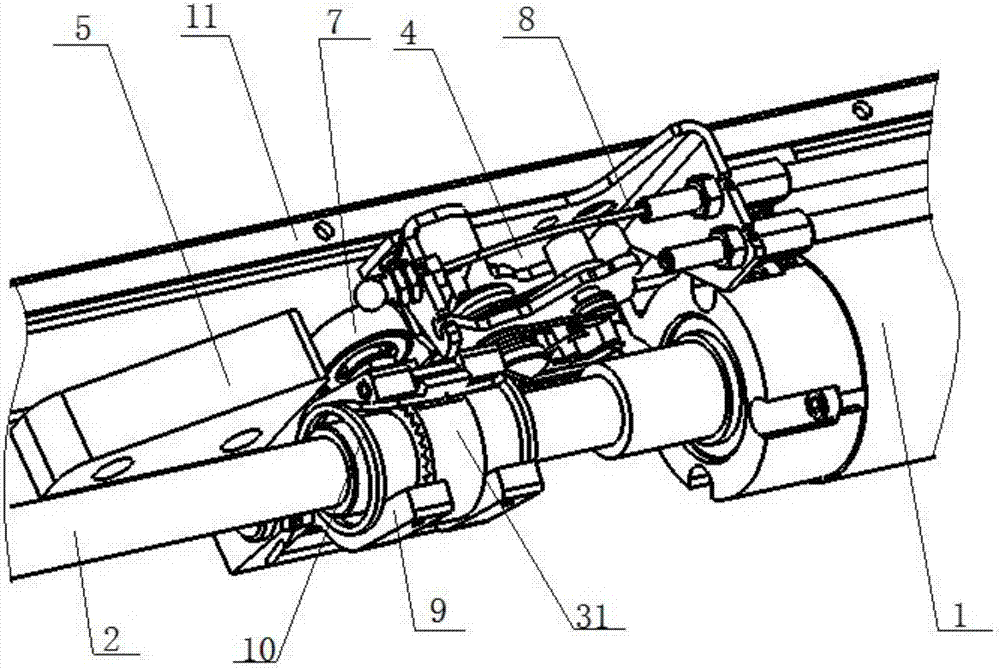
Automatic sliding door system
ActiveCN105545139BAddress security risksReduce in quantityPower-operated mechanismReciprocating motionElectric machinery
The invention discloses an automatic door sliding system. The automatic door sliding system comprises a cross beam, a driving mechanism arranged on the cross beam and a limiting mechanism; the driving mechanism is connected with a sleeve component; a door leaf is connected through a door carrying frame; a guide locking block is arranged on the cross beam; the driving mechanism includes a lead screw driven by a motor and a nut component; the nut component includes a transmission frame, a nut coating the lead screw, and a followup part fixed on the nut; the nut is mounted in the transmission frame; the transmission frame is connected with the sleeve component; the lead screw drives the nut component to perform a reciprocating motion in the axial direction of the lead screw; in forward rotating process of the lead screw, when the followup part is contacted with the guide locking block, the followup part moves to the limiting mechanism under the guidance of the upper surface of the guide locking block and is stopped by the limiting mechanism; the followup part rotates along with the lead screw to enter a space between the side surface of the guide locking block and the limiting mechanism to be locked; and when the lead screw reversely rotates, the followup part reversely rotates along with the lead screw to deviate from the limitation of the guide locking block to be unlocked, and moves in the axial direction of the lead screw.
Owner:NANJING KANGNI MECHANICAL & ELECTRICAL
Data transmission method, device and system
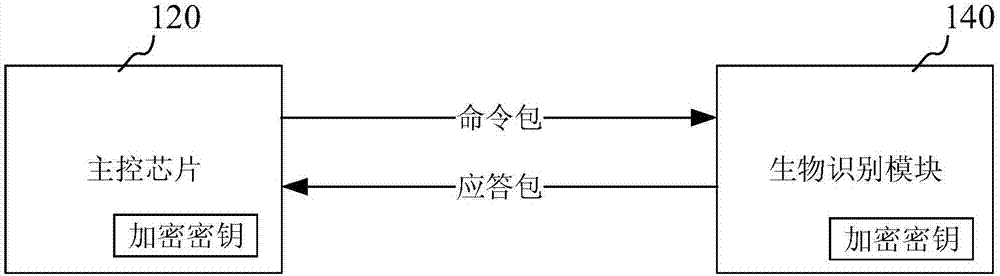
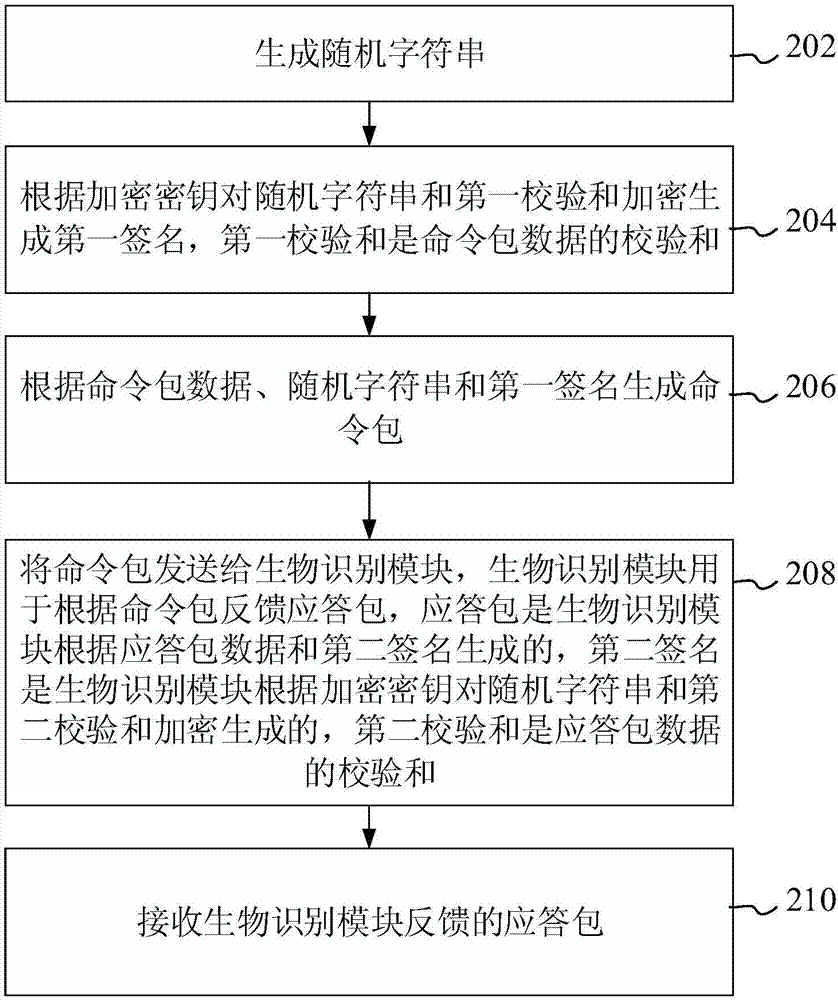
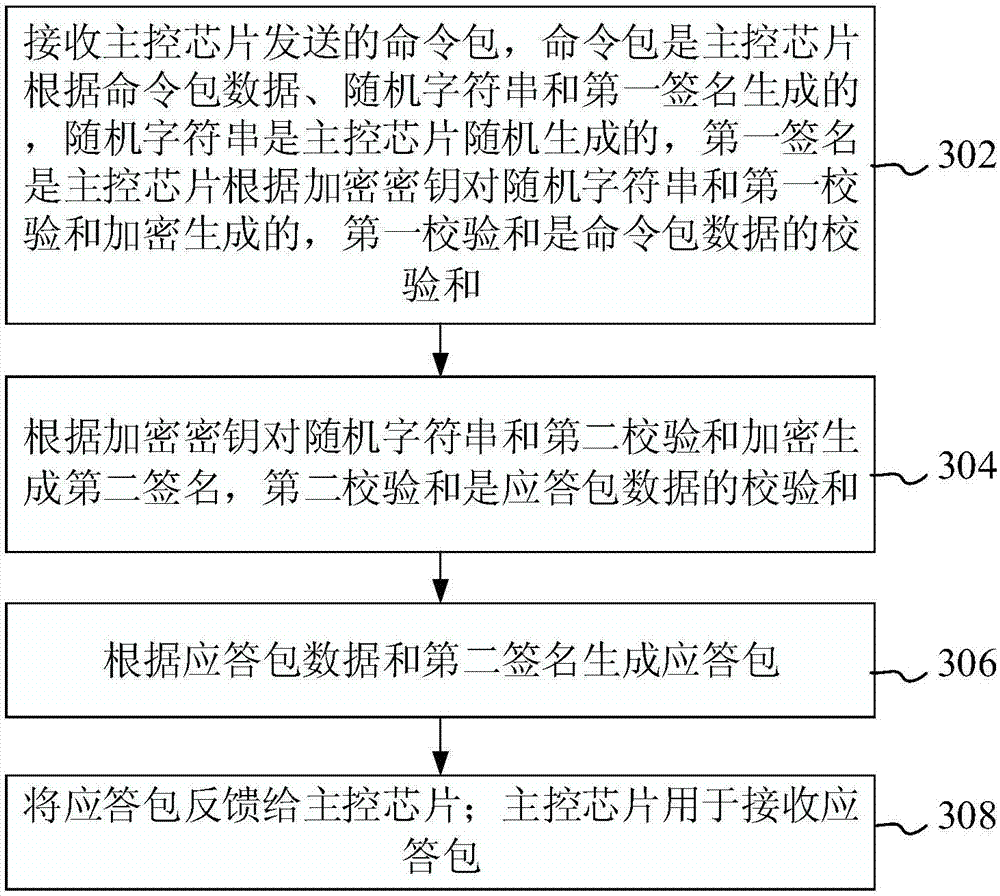
InactiveCN107395340AAddress security risksReduce hardware costsKey distribution for secure communicationError detection/correctionComputer hardwarePlaintext
The invention discloses a data transmission method, device and system, belonging to the technical field of biometric identification. The method comprises the steps of generating a random character string; encrypting the random character string and a first checksum according to an encryption key so as to generate a first signature, wherein the first checksum is a checksum of command packet data; generating a command packet according to the command packet data, the random character string and the first signature; sending the command packet to a biometric identification module, wherein the biometric identification module is used for feeding back a reply packet according to the command packet; and receiving the reply packet fed back by the biometric identification module. When a master control chip cannot execute complex RSA, DES or MD5 algorithms due to poor performance, most communication protocols use plaintext, and data transmission has security risk. The invention solves the above problem. The safe communication algorithm is realized at extremely low hardware cost, bidirectional identity identification, anti-replay and anti-tamper functions are realized, only an encryption module is used and a decryption module is not used, and the data transmission risk is lowered.
Owner:YUNDING NETWORK TECH BEIJING
Protection device used for electric transmission line tower climbing operation
InactiveCN107497073AGuaranteed safe operationEliminate psychological fearSafety beltsTowerBuilding construction
The invention relates to a protection device used for electric transmission line tower climbing operation, is particularly suitable for being used in overhead transmission line construction, interruption maintenance, operation with power uninterrupted and other tower climbing operation and belongs to the technical field of electric transmission line pole and tower field operation tools. The protection device comprises a safety rope with one end being hung on the human body, a plurality of short tying ropes which are arranged at intervals in the height direction of an electric transmission line pole and tower, and a differential speed blocking device which is used for clamping the safety rope which rapidly rotates anticlockwise. The differential speed blocking device is provided with a wire inlet which is used for penetrating the safety rope, a wire outlet and a clamping mechanism. The protection device is simple in structure, convenient to use, safe, reliable, wide in application range and high in operation efficiency.
Owner:YANTAI POWER SUPPLY COMPANY OF STATE GRID SHANDONG ELECTRIC POWER +1
Lifting-following rotary-type self-balancing tower crane
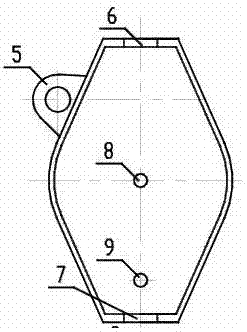
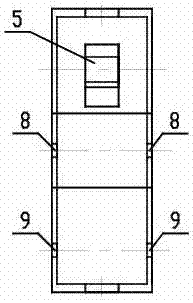
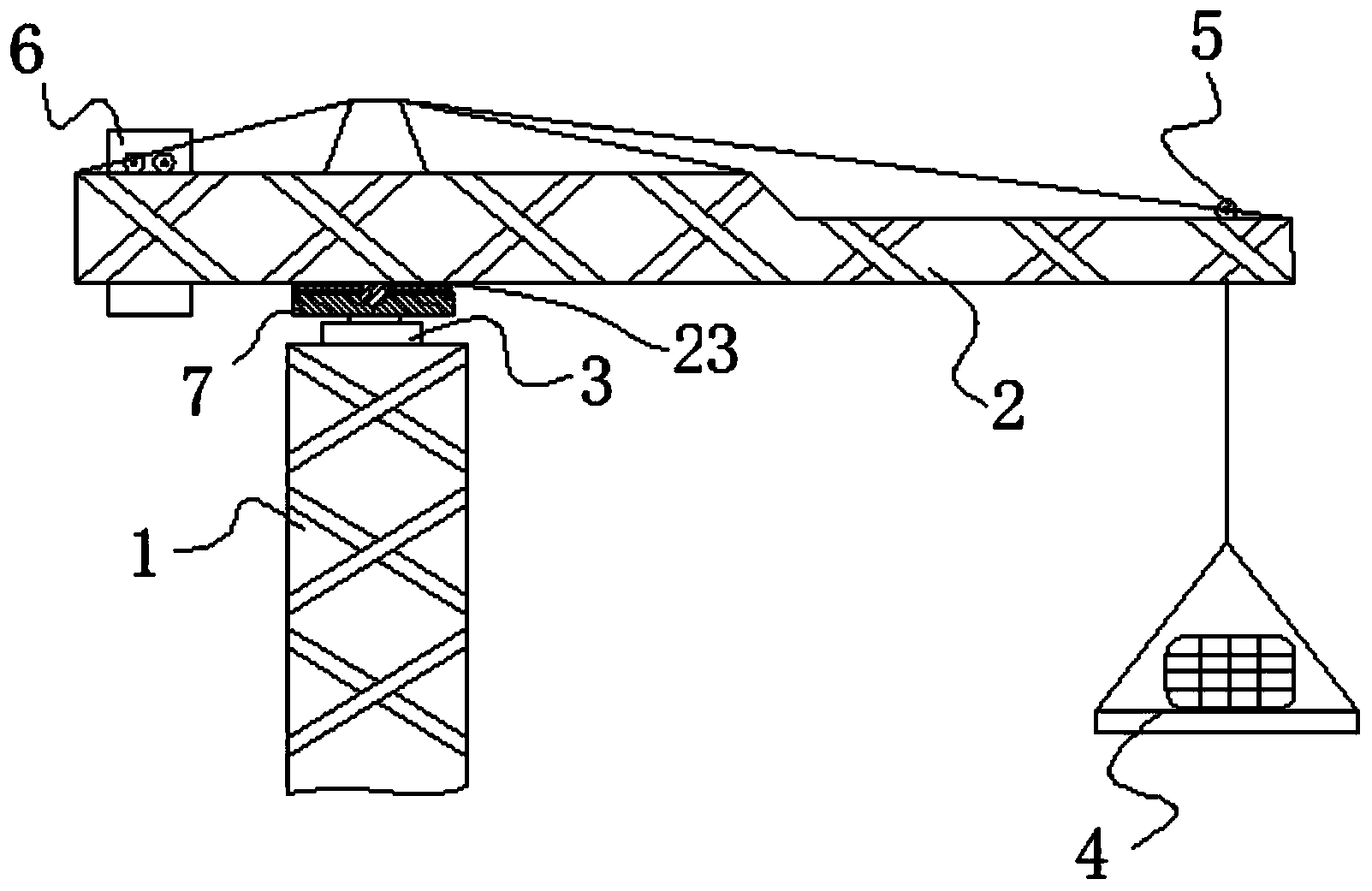
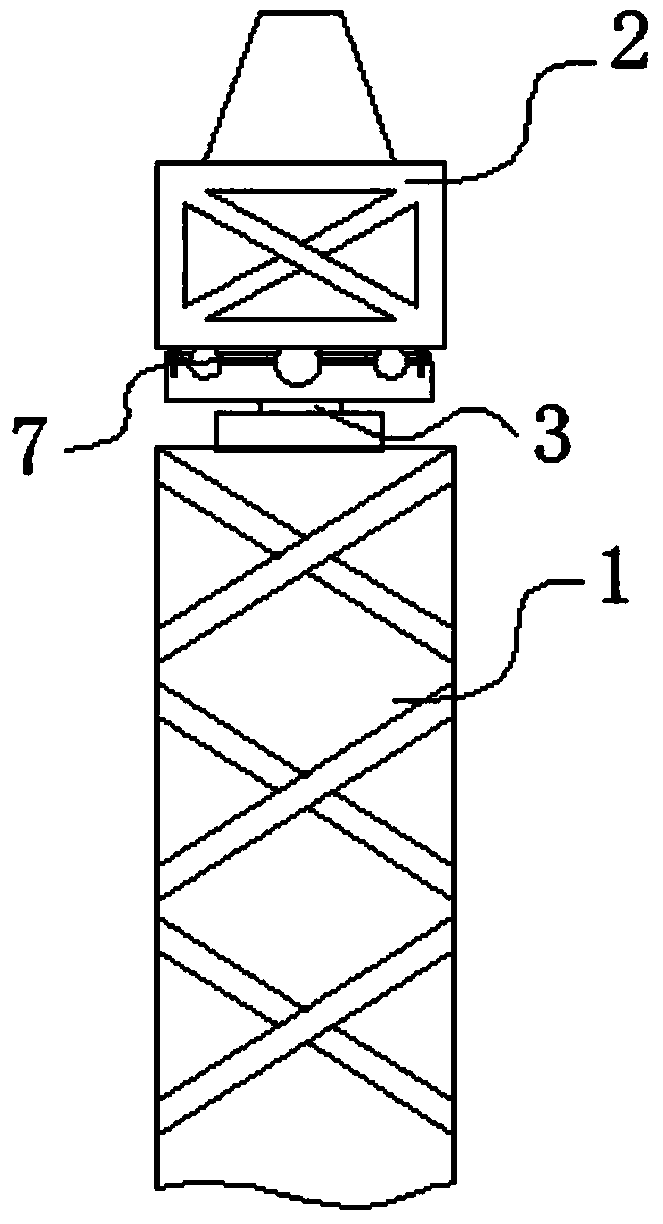
ActiveCN103508340AEffective protectionImprove anti-overturn performanceLoad-engaging elementsCranesTower craneCantilever
The invention discloses a lifting-following rotary-type self-balancing tower crane and aims to provide a tower crane design capable of effectively protecting the tower frame body, improve the anti-overturning capacity of the tower crane, increase the counter weight and the bearing capability of the tower crane, and enable the tower crane to be suitable for transporting and hoisting large-scale materials and components of buildings, equipment and facilities. The lifting-following rotary-type self-balancing tower crane comprises a tower frame, a luffing trolley, a clump weight, a rotary mechanism, a luffing cantilever and a tower frame protection structure. The invention worthily illustrates that in a conventional tower crane structure, the cantilever is also called a big arm and is connected to the front and rear sides of a cone pillar at the upper end of a rotary mechanism, one side of the connection point of the cantilever is provided with a balance arm or a counter weight arm and the other side of the connection point is provided with a suspension arm. In the invention, the basic structure of the luffing cantilever is basically the same as the existing cantilever structure and only the connecting manner of the cantilever and the rotary mechanism is changed as shown below. Therefore, the cantilever of the lifting-following rotary-type self-balancing tower crane can luff, so that the cantilever is named the luffing cantilever to be distinguished from the cantilever in the prior art.
Owner:重庆亚颖机电科技有限公司
On-board electronic equipment having steering wheel sound inputting and video displaying functions
InactiveCN103770722ASupport touch control functionSolve the inconvenienceHand wheelsElectric/fluid circuitSteering wheelOn board
The invention relates to on-board electronic equipment, in particular to on-board electronic equipment having sound inputting and video displaying functions. Steering wheel centralized-control on-board electronic equipment having steering wheel sound inputting and video displaying functions is provided to effectively eliminate inconvenience in driving and operating and safety risk due to sound inputting and video displaying of the on-board electronic equipment far away from an automobile driver. By enabling or disenabling sound inputting of a steering wheel and video displaying on the steering wheel, interference with driving of the automobile driver can be avoided, and the driving safety is ensured. Meanwhile, the sound inputting and video displaying of the steering wheel are independent of each other, and can be used separately and together, and a touch screen can be taken as a video display unit on the steering wheel to support touch control function.
Owner:洪国林
Concrete prepared by utilizing abandoned dry film and preparation method thereof
ActiveCN108117330AExcellent overall performanceGood mechanical propertiesSolid waste managementSlagNatural sand
The invention provides concrete prepared by utilizing an abandoned dry film and a preparation method thereof. The concrete comprises the following components in parts by weight: 5-15 parts of dry filmfine, 5-15 parts of magnesium reducing slag, 10-20 parts of cement, 20-30 parts of natural sand, 20-30 parts of stones, 10-15 parts of water and 5-10 parts of a water reducing agent, wherein the dryfilm fine is obtained by carrying out alkali treatment on the abandoned dry film, and mass content of a colloid component in the dry film fine is less than or equal to 3%. According to the invention,the abandoned dry film and magnesium reducing slag are recycled, and the concrete with excellent mechanical properties is obtained.
Owner:常州厚德再生资源科技有限公司
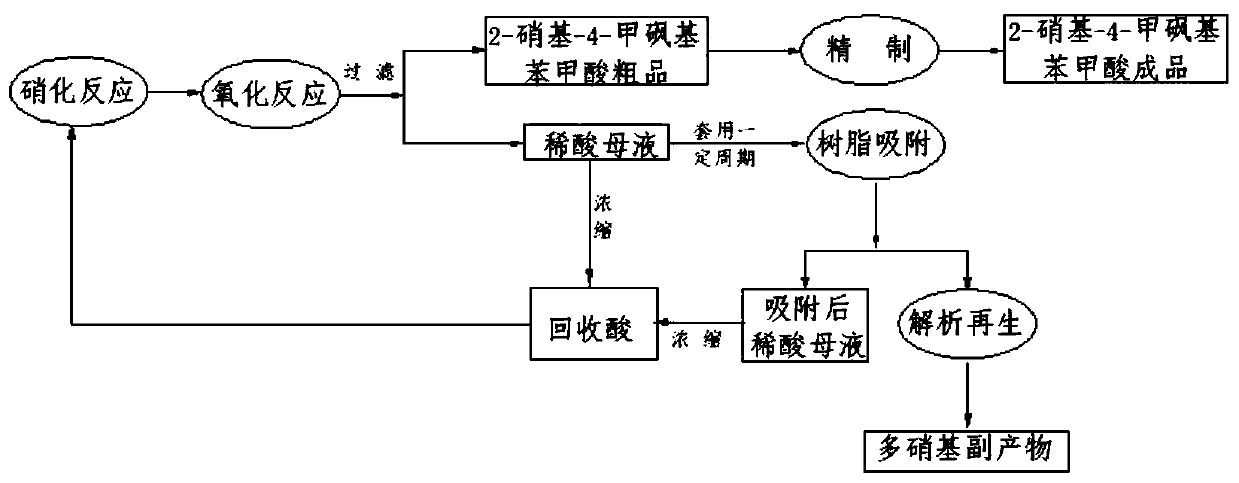
Method for recycling acid in synthesis of 2-nitro-4-methylsulfonylbenzoic acid
ActiveCN111302984AReduce unit consumptionSolve processing problemsOrganic chemistryOrganic compound preparationBenzoic acidNitro compound
The invention relates to a method for recycling acid in synthesis of 2-nitro-4-methylsulfonylbenzoic acid, which comprises the following steps of 1) by using 4-methylsulfonyltoluene as a raw material,carrying out nitration reaction and oxidation reaction in a concentrated sulfuric acid medium, filtering dilute acid mother liquor obtained after the 2-nitro-4-methylsulfonylbenzoic acid crude product, and concentrating to obtain recycled acid, 2) recycling the recovered acid, and removing the reaction by-product polynitro compound from the dilute acid mother liquor by adopting a resin adsorptionmethod, so that the content of the polynitro compound in the dilute acid mother liquor after adsorption is less than 200 ppm, 3) concentrating the adsorbed dilute acid mother liquor, applying the concentrated dilute acid mother liquor to the nitration reaction, and supplementing the required catalyst to continue the oxidation reaction after the nitration reaction is finished, and 4) desorbing andregenerating the adsorbed resin through solvent desorption, concentrating, filtering and washing to recover the reaction by-product, thereby avoiding the safety and environmental protection risks caused by continuous accumulation of the by-product concentration in the synthesis process, and being safe, practical, green and environment-friendly, and suitable for industrial implementation.
Owner:利民化学有限责任公司
Rotary disk type measuring cup carrier mechanism and use method thereof
ActiveCN108169309AAddress security risksSolve the resultMaterial electrochemical variablesTrace elementEngineering
The invention discloses a rotary disk type measuring cup carrier mechanism and a use method thereof and relates to the technical field of trace element detection. The rotary disk type measuring cup carrier mechanism mainly comprises a fixed disk body, a rotating disk body, a lifting cleaning table, a detecting electrode, a plurality of liquid suction needles, a plurality of liquid feeding needles,a wiping device, a plurality of detection liquid outlet needles, a sample liquid outlet needle and a stirring device. The rotary disk type measuring cup carrier mechanism can keep a fixing state of the electrode in detection and an electrode movement mechanism is avoided so that the problems of safe risk of the electrode movement and measuring errors caused by the electrode movement are solved. The detection electrode can be cleaned in detection so that the complex manual cleaning process is avoided and the detection efficiency is improved.
Owner:北京新九陆生物科技发展有限责任公司
Online high-temperature corrosive powder sampling device and method
InactiveCN110672370AAvoid pollutionAvoid security issuesWithdrawing sample devicesChemical industryEngineering
The invention discloses an online high-temperature corrosive powder sampling device and method, relates to the field of chemical industry, and solves the problems of high environmental pollution and high safety risk due to online sampling of high-temperature, fine-granularity and strong-corrosivity powder in a conventional sampling mode. According to the technical scheme, the online high-temperature corrosive powder sampling device comprises a high-temperature material bin; a sampling hole is formed in the bottom of the high-temperature material bin; the sampling hole is connected with a discharging pipe; and at least two valves are arranged on a discharging pipe. According to the online high-temperature corrosive powder sampling method, before sampling, a valve, closest to the sampling hole, on the discharging pipe is closed; during sampling, a valve which is second closest to the sampling hole is closed, the valve closest to the sampling hole is opened, and materials enter the discharging pipe; and a valve of a pipe section containing the materials in the discharging pipe is closed, and a valve, close to one side of a discharging hole, of the pipe section is opened until the materials flow out of the discharging hole. The sampling device and method are suitable for online sampling the high-temperature corrosive powder.
Owner:PANZHIHUA IRON & STEEL RES INST OF PANGANG GROUP
An on-line temperature probe for motor rotor
ActiveCN104390727BAccurate measurementImprove securityTemperature measurement of moving solidsHeat lossesLight filter
The invention discloses an online motor rotor temperature measuring probe which comprises a reflector, an infrared light source, a focusing mirror, a receiving element, a light filter and a heat insulation sleeve. The probe is integrally protected by the heat insulation sleeve, screwed on a shell or an end cover and different from a common infrared temperature measuring probe, the probe effectively overcomes the shortcomings of unstable reflection and polarized light of a rotor surface caused by rotation by the aid of the light filter, a measuring element is mounted in the heat insulation protection sleeve, heat shock of heat conduction on a photoelectric element is relieved, and mechanical shock of body vibration on the elements is decreased when a motor runs. The probe has the advantages that the probe is accurate in measurement and fine in safety, the effect on the structure of the motor is low and the like, the probe can be conveniently and rapidly mounted on the end cover of the motor, the temperature of the end face of the rotating rotor is continuously measured in real time, and the probe effectively solves the problems that heat loss and safety risks caused by a window formed in the end cover in the past, temperature measuring test paper is pasted on the surface of a rotor, the highest temperature can only be inspected in a split manner, and the temperature change process cannot be reflected.
Owner:CSR ZHUZHOU ELECTRIC CO LTD
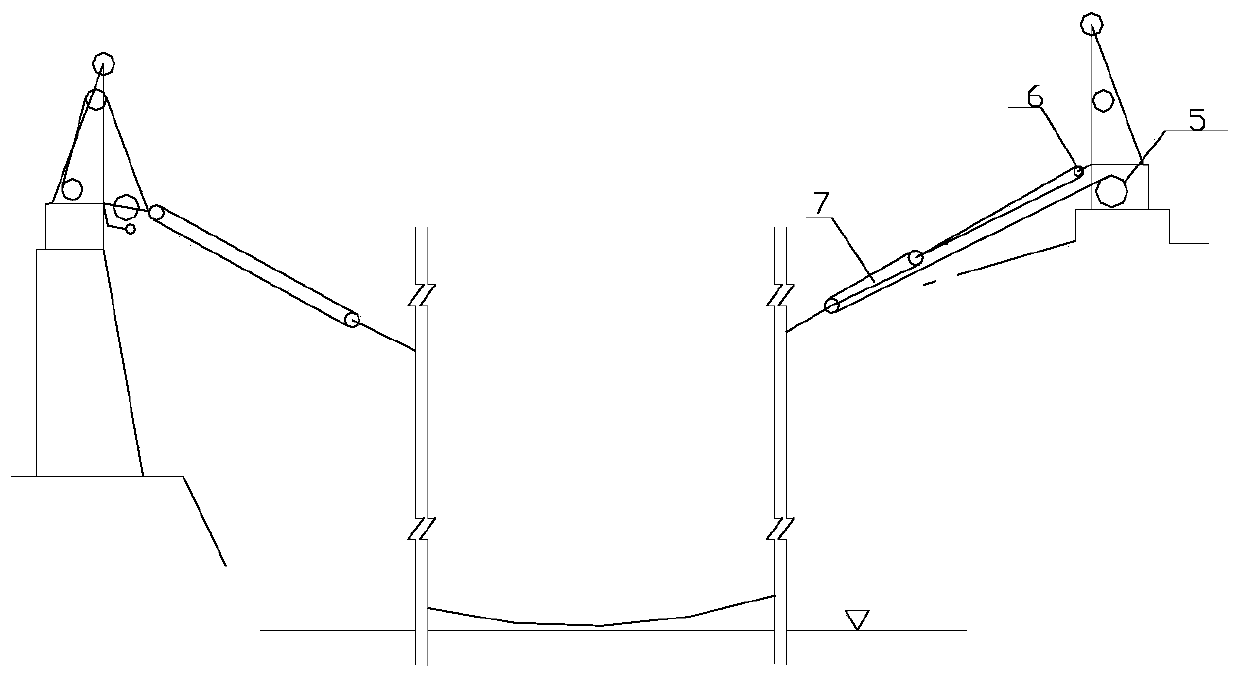
The Construction Method of Leakage Prediction and Treatment of Underground Diaphragm Wall
ActiveCN110258658BSolve the hidden danger of water seepageAddress security risksDetection of fluid at leakage pointProtective foundationSlurry wallSonar
The invention relates to a construction method for seepage anticipation and treatment of an underground continuous wall. The construction method includes the following steps that according to the construction condition of the underground continuous wall, a seepage detection point is selected; during construction of underground continuous wall, a detection pipe is buried at the selected seepage detection point; after the construction of the underground continuous wall is finished, a detection probe of a sonar measuring instrument is sent into the detection pipe for detecting, and a detection result is obtained; and grouting water stop treatment is conducted on the leakage detection point which the seepage coefficient is larger than the set range in the detection result. According to the construction method, whether the underground continuous wall has seepage hidden danger or not is detected in advance to ensure safety of foundation pit excavation, if yes, grouting water stop treatment is conducted timely, the risk of water and sand gushing during foundation pit excavation is avoided, probability of seepage of the underground continuous wall is decreased, and construction safety of a foundation pit is improved.
Owner:CHINA CONSTR EIGHT ENG DIV CORP LTD
Interface calling method and device, computer equipment and readable storage medium
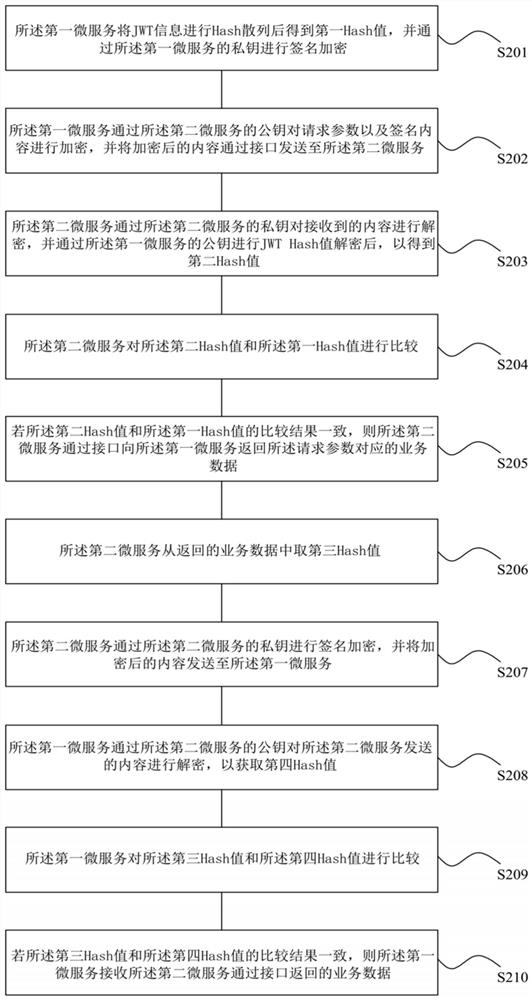
PendingCN112328415AReduce verification stepsCommunication securityInterprogram communicationDigital data protectionComputer engineeringComputer equipment
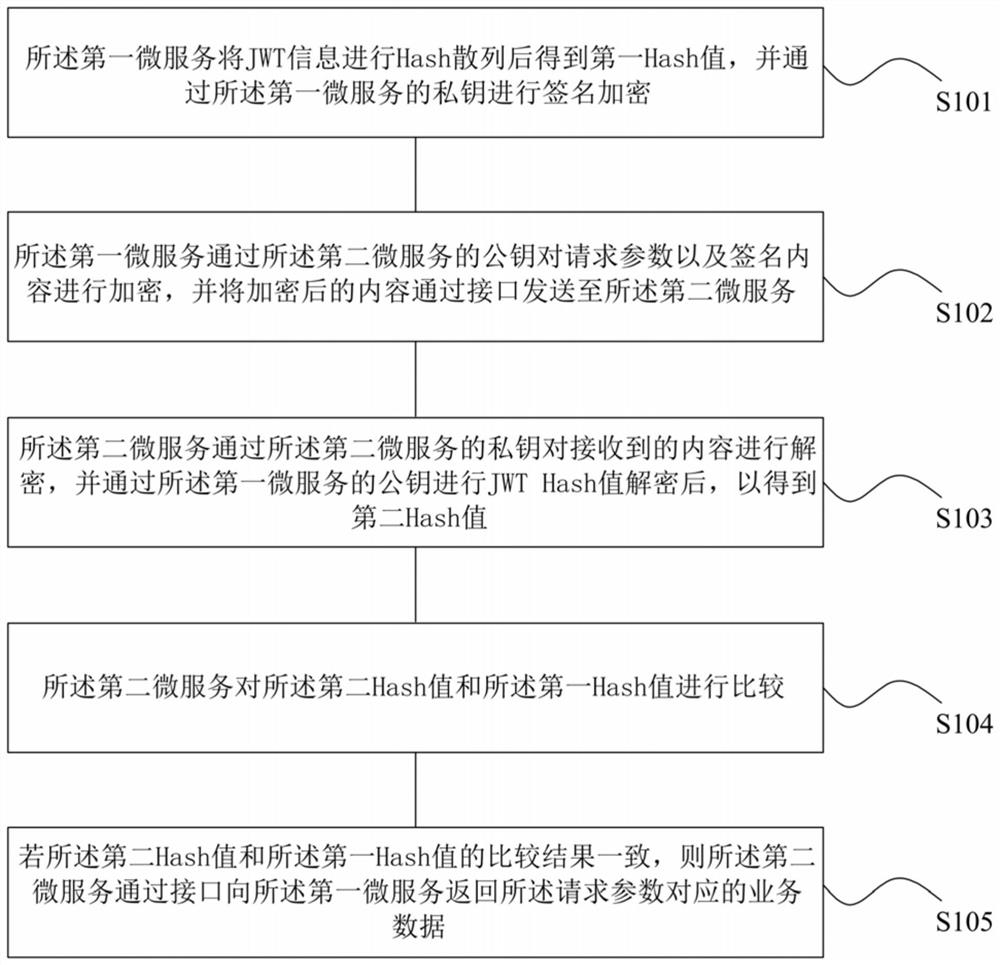
The invention relates to an interface calling method and device, computer equipment and a readable storage medium. The method comprises the steps that a first micro-service carries out the Hash of JWTinformation, obtains a first Hash value, and carries out the signature encryption through a private key of the first micro-service; the first micro-service encrypts the request parameter and the signature content through a public key of the second micro-service, and sends the encrypted content to the second micro-service through an interface; the second micro-service decrypts the received contentthrough a private key of the second micro-service, and performs JWT Hash value decryption through a public key of the first micro-service to obtain a second Hash value; the second micro-service compares the second Hash value with the first Hash value; and if the comparison result of the second Hash value and the first Hash value is consistent, the second micro-service returns service data corresponding to the request parameter to the first micro-service through the interface. According to the invention, the problems of tedious verification steps and security risks in the prior art are solved,and security and effectiveness of information interface calling among multiple platforms are realized.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com